In 2026, most organizations still take weeks to detect threats that later turn into breaches, even when the indicators were there from day one. That is not a minor issue. It is a signal that something in our security practice is broken.
Today, you are swimming in tools, alerts, and feeds, but you are starving for insights because there’s little to nothing that tells you what to do next. According to Aikido’s State of AI Security Development 2026 report, around 15% of engineering time is lost to triaging alerts, time that should be spent building, fixing, and shipping software.
Instead, teams push cards around Kanban boards and hire more analysts just to keep up. That looks less like security at scale and more like crisis management on repeat.
As such, threat intelligence should be the thing that cuts through the chaos, points to the real risks, and helps you decide confidently what to fix now and what can wait. Most tools today give you more data, but not the right context. That leaves you in an endless loop of chasing ghosts.
In this article, we are going to do three things. First, we will break down what threat intelligence actually means today and why it matters. Then we will examine the strengths and weaknesses of the top 7 threat intelligence tools and platforms. Finally, we will show you how to choose the right one.
Let us get into it, however, before that, here’s an overview of the top 7 threat intelligence tools:
- Aikido Security
- Recorded Future
- CrowdStrike
- Mandiant
- Palo Alto Networks Unit 42
- Anomali
- ThreatConnect
TL;DR:
Among the threat intelligence tools we reviewed, Aikido Security stands out as a unified security platform built for modern development teams.
Rather than siloed point tools, Aikido brings code security, dependency analysis, infrastructure and cloud posture management, dynamic testing, and runtime protection into one seamless system that works with the tools developers already use. This unified approach reduces noise and false positives, so security teams and developers can focus on real risks and accelerate remediation.
The platform uses AI-driven features like AutoTriage and AI Autofix to automatically prioritize alerts and even generate fixes that can be merged through pull requests, cutting down manual work and alert fatigue. Aikido’s scanning capabilities span static application security testing (SAST), open-source dependency analysis (SCA), secrets and misconfiguration detection, and container and cloud risk assessment.
Aikido also includes advanced threat testing and runtime defense, with authenticated DAST, API fuzzing, AI-assisted pentesting, and real-time protections that block attacks before they impact production. This breadth of functionality helps teams find and fix vulnerabilities earlier, enforce security continuously, and test defenses just like attackers would.
Finally, Aikido integrates with numerous development, cloud, and collaboration tools and supports compliance automation for standards like SOC 2 and ISO 27001, enabling scalable security governance without disrupting developer workflows. Its focus on actionable insights, contextualized alerting, and developer-friendly automation makes it a comprehensive platform for threat intelligence.
Aikido can also help make threat modelling practical for developers.
What Is Threat Intelligence?
Threat intelligence is the ability to understand which security risks actually matter to your environment, and why they matter right now.
Threat intelligence used to mean feeds: lists of IPs, domains, hashes, and CVEs pulled from somewhere else and dropped into your tooling. If you have been in security long enough, you have probably watched those feeds grow while their usefulness quietly shrank.
But today, threat intelligence means decision support.
Threat intelligence is about understanding which risks are relevant to your environment, your code, and your cloud setup, not what is theoretically dangerous somewhere on the internet. Without context, intelligence is just data and malware signatures, and neither will help you ship securely or sleep better at night.
Modern threat intelligence tools should answer practical questions:
- Is this vulnerability reachable in production?
- Is this package actually used in a critical path?
- Does this exposure matter, given how the service is deployed?
If it cannot help you answer those questions quickly, it is background noise.
Why Are Threat Intelligence Tools Important?
The way we build and run software has changed and is continuously changing, and security isn’t getting any simpler. As such, you need a threat detection tool that simplifies building and maintaining your applications.
You need a threat detection tool when you are dealing with:
- Cloud infrastructure that changes daily
- Dependencies you did not write
- Pipelines that deploy automatically, and
- Environments that scale on demand.
Attackers understand this speed and exploit it. They do not need zero days all the time; they thrive on known issues that never get prioritized. This is where threat intelligence becomes critical.
At its core, threat intelligence tools matter because they:
- Help teams focus on real risk, not theoretical issues: By adding context around exploitability and exposure, threat intelligence helps teams prioritize vulnerabilities that are likely to be abused, instead of treating every finding as equally urgent.
- Reduce alert fatigue and wasted engineering time: Without intelligence, teams drown in raw findings. Good threat intelligence filters noise, which means fewer alerts, higher-confidence issues, and less time lost to manual triage.
- Improve detection speed and decision-making: Threat intelligence shortens the gap between when a threat appears and when teams understand its impact, enabling faster and more confident remediation.
- Provide context across modern, complex environments: Modern stacks span code, dependencies, cloud services, and runtime systems. Threat intelligence helps correlate signals across these layers so risks can be understood in context, not isolation.
- Allow security to scale without adding headcount: As environments grow, manual analysis does not scale. Threat intelligence automates prioritization and context, allowing teams to maintain strong security outcomes without constantly expanding teams.
A good threat detection tool helps restore focus. It helps teams move from reactive firefighting to informed prioritization.
Top 7 Threat Intelligence Tools
By now, one thing should be clear. Threat intelligence does not fail because teams lack data. It fails because most tools operate in isolation, each seeing a fragment of the risk while leaving you to connect the dots.
With that in mind, let us look at seven widely used threat detection tools and platforms.
Comparing The Top 7 Threat Intelligence Tools
1. Aikido Security
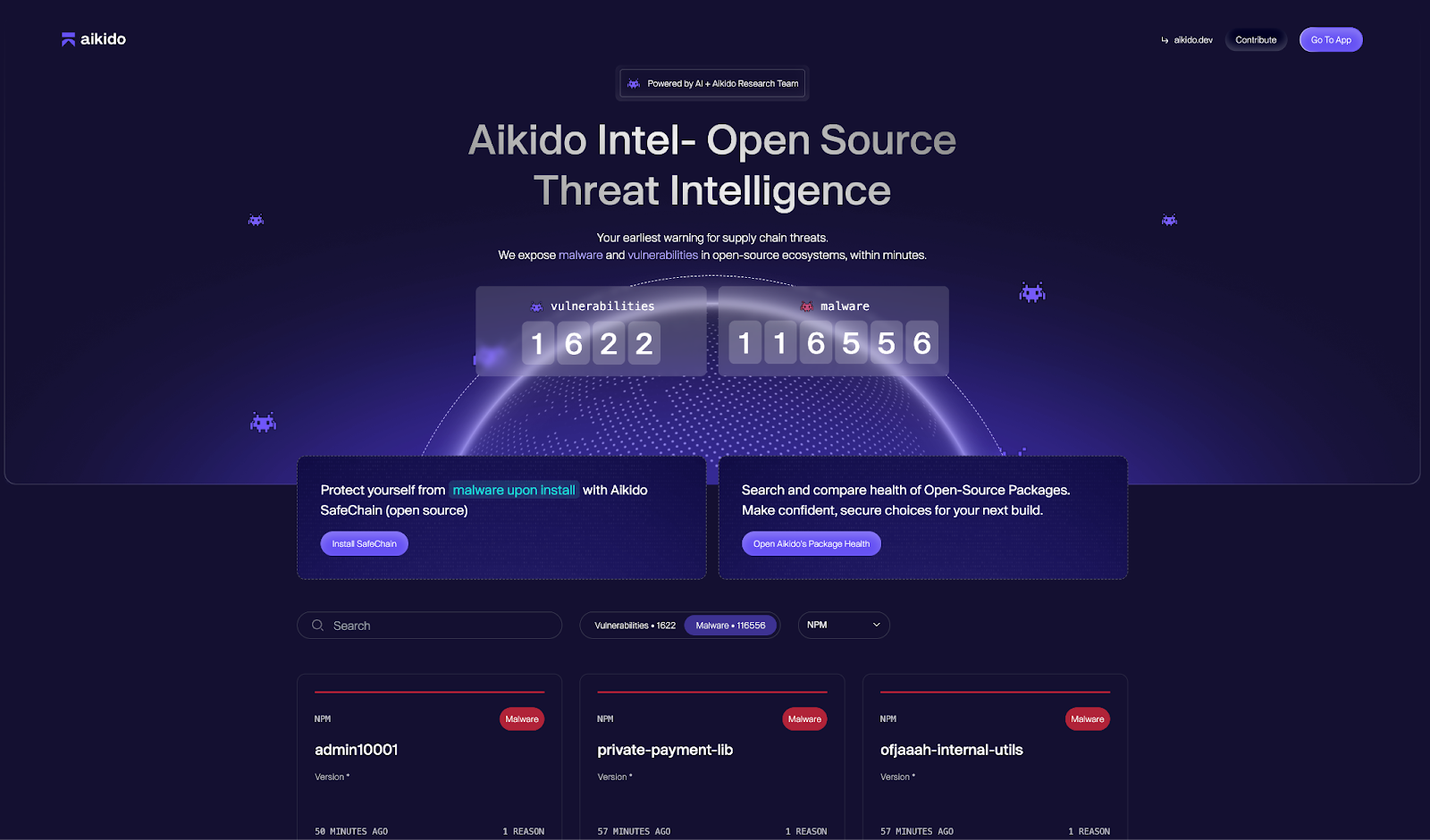
Aikido Security brings threat intelligence, code security, and runtime protection together in a single, unified platform designed to secure the entire software development lifecycle. It combines early visibility into emerging threats with automated scanning across code, dependencies, cloud, and infrastructure, helping teams detect vulnerabilities, misconfigurations, secrets, and malware before they become production issues.
At the intelligence layer, Aikido Intel continuously tracks vulnerabilities and malicious activity across open-source ecosystems, including issues that do not yet have CVEs. This intelligence feeds directly into Aikido’s broader security capabilities, such as software composition analysis, license compliance, malware detection, and supply chain protection. With features like SafeChain and package health insights, teams can make informed dependency decisions and block malicious packages at install time.
Beyond pre-production scanning, Aikido extends protection into production with Zen, its embedded runtime protection layer. Zen blocks common injection attacks, bot abuse, and zero-day exploits in real time, without external infrastructure or rule tuning. Because it runs inside the application, it provides accurate, low-noise protection while feeding runtime context back into vulnerability prioritization.
Together, these capabilities allow Aikido to connect threat intelligence with real-world exploitability. By unifying open-source intelligence, application and cloud security, and runtime defense into a single platform, Aikido reduces tool sprawl, improves signal quality, and helps teams focus on the risks that matter most across build, deploy, and runtime stages.
Key Features
- Unified security coverage: Aikido Security provides context-aware vulnerability detection across source code, open-source dependencies, cloud and infrastructure configurations, APIs, and runtime. This unified approach removes blind spots and ensures risks are identified consistently from build to production.
- Built-in threat intelligence: Aikido Intel continuously monitors open-source ecosystems for newly discovered vulnerabilities and malware, including issues without CVEs. This intelligence feeds directly into the platform, helping teams prioritize vulnerabilities based on exploitability and real-world risk, not just severity scores.
- Best-in-class application and cloud security testing: The platform delivers broad coverage for SAST, DAST, SCA, secrets detection, malware scanning, IaC and cloud security, and API discovery and testing. These layers work together to give teams a complete view of application and infrastructure risk without relying on multiple disconnected tools.
- Runtime protection with exploit-aware prioritization: With Aikido Zen, teams get embedded runtime protection that blocks common injection attacks, bot abuse, and zero-day exploits in real time. Runtime insights are fed back into Aikido’s risk scoring, helping teams focus remediation efforts on vulnerabilities that are actually reachable and exploitable.
- Low-noise, developer-friendly experience: Aikido automatically triages findings to reduce false positives and alert fatigue, surfacing only issues that matter. It integrates seamlessly with existing developer workflows and can be deployed quickly, enabling fast adoption without disrupting engineering teams or adding operational overhead.
Pros
- Strong signal-to-noise ratio that reduces alert fatigue
- Clear prioritization that helps teams focus on what matters now
- Designed to fit into real engineering workflows
- Consolidates multiple security categories without increasing operational overhead
- Early threat detection using proprietary intelligence, either at installation time or before the malware is assigned a CVE
- Runtime protection that blocks attacks in real time
- Automated remediation that considerably reduces fix time
- Built-in compliance and audit report
Pricing Model
Aikido offers flexible plans designed to scale with your team’s size and security needs.
- Free Tier (Developer): Ideal for getting started, and includes core scanners, PR security reviews, and analytics to help teams evaluate their Kubernetes security posture.
- Basic Plan: Best for small teams looking to expand coverage, offering AI-based protection, code-to-cloud visibility, and integrations with tools like Jira, Drata, and Vanta.
- Pro Plan: Suited for growing organizations, unlocking advanced capabilities such as custom SAST rules, on-prem scanning, API security testing, malware detection, and virtual machine scanning.
- Advanced Plan: Built for enterprises with complex environments, extending protection with hardened container images, extended library lifecycles, and EPSS-driven prioritization.
Pricing starts from the free tier, with higher tiers available based on scale and required features.
2. Recorded Future
Recorded Future is a threat intelligence platform that primarily focuses on aggregating and analysing external threat data at scale. It pulls intelligence from a wide range of sources, including the open web, dark web, and technical feeds, and presents this information through risk scores and reports.
Key Features
- Large-scale aggregation of external threat data
- Risk scoring for domains, IPs, and vulnerabilities
- Reporting focused on threat actors and campaigns
- Integrations with SIEM and SOAR tools
Pros
- Broad visibility into external threat activity
- Strong reporting for strategic and executive use
- Useful for monitoring emerging threat trends
Cons
- Intelligence is largely external and high-level, which makes it difficult to map findings
- Requires significant analyst interpretation to translate insight into concrete remediation actions
- Limited native context around modern software stacks, such as source code, CI/CD pipelines, and dependency graphs
- Weak integration into developer workflows, making it harder for engineering teams to act on findings quickly
- Often deployed alongside multiple other security tools to provide missing internal context
Pricing Model
Recorded Future uses a tiered, subscription-based pricing model, typically aligned with organization size and data access levels. Costs can increase as additional modules and integrations are added.
3. CrowdStrike
CrowdStrike Falcon Intelligence is the threat intelligence arm of the CrowdStrike ecosystem. It is tightly coupled with endpoint protection and focuses heavily on adversary tracking, malware analysis, and intrusion-related intelligence.
The platform is most effective in environments where CrowdStrike endpoint tooling is already central to security operations.
Key Features
- Adversary and campaign tracking
- Intelligence is tied closely to endpoint telemetry
- Reports focused on attacker behaviour and tactics
- Integration with Falcon platform components
Pros
- Strong linkage between endpoint activity and intelligence
- Useful for incident response and post-incident analysis
- Centralized within an existing CrowdStrike deployment
Cons
- Strongly coupled to the CrowdStrike ecosystem, which significantly reduces its value outside endpoint-centric environments.
- Intelligence impact drops sharply for organizations without broad CrowdStrike endpoint coverage
- Focuses primarily on adversary tracking and campaigns rather than day-to-day vulnerability prioritization
- Limited visibility into application-layer risks
- Minimal insight into dependency and supply chain risks that affect build and deployment pipelines
- Less effective for cloud-native and containerized workloads
Pricing Model
Falcon Intelligence is typically licensed as an add-on within the broader CrowdStrike platform, with pricing dependent on endpoint coverage and selected modules.
4. Mandiant
Mandiant Advantage is a threat intelligence platform built around incident response expertise and adversary research. It emphasizes understanding attacker behaviour, campaigns, and techniques based on real-world breach investigations.
Organizations that prioritize preparedness for advanced threats and post-incident learning commonly use the platform.
Key Features
- Intelligence grounded in incident response research
- Campaign and threat actor analysis
- Strategic reporting for security leadership
- Integration with selected security tools
Pros
- Deep insight into advanced threat activity
- Strong credibility in breach analysis
- Valuable for mature security teams
Cons
- Intelligence is largely strategic and post-incident focused, offering limited support for preventative or real-time security decisions
- Less focused on day-to-day vulnerability prioritization needed in active development environments
- Insights often remain high-level, requiring additional effort to translate into concrete remediation steps
- Requires experienced security teams to interpret intelligence effectively
- Relies on additional tools for enforcement and response, increasing operational complexity
- Less suitable for fast-moving engineering teams that need automated prioritization and immediate feedback
Pricing Model
Mandiant Advantage follows a subscription pricing model, typically positioned for mid to large organizations with established security operations.
5. Palo Alto Networks Unit 42
Unit 42 is Palo Alto Networks’ threat research and intelligence group. Its intelligence feeds into Palo Alto’s broader security ecosystem, supporting firewall, cloud, and endpoint products.
The focus is on research-driven insight rather than standalone threat intelligence consumption.
Key Features
- Threat research and analysis
- Intelligence tied to Palo Alto products
- Reporting on campaigns and vulnerabilities
- Support for network and cloud security tooling
Pros
- Useful within Palo Alto-centric environments
- Backed by extensive research resources
- Relevant for network-focused security teams
Cons
- Intelligence is primarily designed to support Palo Alto Networks products, which limits its usefulness as a standalone threat intelligence solution.
- Strong dependence on the Palo Alto ecosystem reduces value for organizations using mixed or non-Palo Alto tooling
- Research-driven insights often remain abstract and require manual translation
- Limited focus on application-layer, dependency, and supply chain risks
- Minimal alignment with developer workflows, like CI/CD pipelines and source control
- Better suited for research and advisory use than for day-to-day operational prioritization and automation
Pricing Model
Access to Unit 42 intelligence is generally bundled within Palo Alto Networks' product offerings rather than sold independently.
6. Anomali
Anomali is a threat intelligence platform focused more on the ingestion, normalization, and sharing of threat data. It is often used as a central hub for collecting intelligence from multiple sources and distributing it across security tools.
You are going to get more of interoperability than opinionated prioritization with Anomali.
Key Features
- Threat intelligence aggregation and normalization
- Support for multiple intelligence standards
- Sharing and collaboration capabilities
- Integrations with SIEM and SOAR platforms
Pros
- Flexible ingestion of diverse data sources
- Strong interoperability focus
- Useful for centralising feeds
Cons
- The overall value of the platform depends heavily on the quality and relevance of ingested feeds
- Limited built-in prioritization means teams must define and maintain their own scoring logic
- Requires significant setup, tuning, and ongoing management to remain effective over time
- High operational overhead makes it challenging for smaller teams without dedicated threat intelligence staff
- Intelligence is presented as aggregated data and requires manual analysis to translate into actionable remediation steps
- Less suited for teams seeking automation embedded directly into engineering workflows
Pricing Model
Anomali uses a modular subscription model, with pricing influenced by data volume, integrations, and feature selection.
7. ThreatConnect
Think of ThreatConnect positions as a threat intelligence and operations platform that combines intelligence management with a carefully orchestrated workflow. This is why security operations teams that manage large complex intelligence pipelines use it. The platform focuses on coordination rather than simplification.
Key Features
- Intelligence management and enrichment
- Workflow and case management
- Integration with security tooling
- Collaboration features for security teams
Pros
- Strong operational tooling for intelligence teams
- Flexible workflow configuration
- Designed for mature security operations
Cons
- Designed primarily for mature threat intelligence operations, which can be excessive for lean teams
- High operational overhead due to heavy emphasis on workflows and manual management
- Steep learning curve and significant setup required before teams see meaningful value
- Focus on structured intelligence workflows can slow down teams that need fast, automated decision-making
- Requires dedicated intelligence staff to operate effectively
- Less aligned with modern developer and CI/CD workflows
Pricing Model
ThreatConnect pricing is subscription-based and typically reflects platform scope, number of users, and enabled modules.
Best Practices for Choosing a Threat Intelligence Tool
When it comes down to choosing a threat intelligence, your focus shouldn’t be on which tool has the longest feature list, but which is compatible with your team’s workflow.
Here are the key principles in the decision.
1. Look Beyond Features and Focus on Outcomes: You can compare features, but not outcomes. Instead of asking what a platform can do, ask what it helps you stop doing. Does it reduce time spent triaging alerts? Does it help engineers fix the right issues faster? Does it lower the number of unresolved findings sitting in your backlog? If a threat detection tool creates more work for your security team, it is not doing its job.
2. Prioritize Compatibility With Your Existing Workflows: Great threat intelligence tools meet teams at the level they operate. This means that if a platform forces you to redesign workflows or introduce new processes, it will be harder to get everyone on the team on board. The best platforms integrate naturally with how your engineers build, deploy, and operate systems because they feel like part of the system.
3. Demand Coverage That Reflects Your Real Attack Surface: Modern environments consist of code, dependencies, cloud configuration, and runtime behaviour. A platform that sees only one slice of that picture will always leave gaps in your security makeup because you do not get to see how signals across layers connect and how risks interact.
4. Think Carefully About Scalability and Operational Load: What works for a small environment may collapse as you grow. Ask how the platform behaves as your organization scales. Does noise increase linearly, or does prioritization improve as more context becomes available? Does the platform require more analysts over time, or does it reduce dependence on manual effort? Scalability is more about human effort than data volume.
5. Be Honest About Cost Stability Over Time: \Some platforms appear affordable until you add required modules, integrations, or headcount to operate them effectively. Others remain predictable because they consolidate capabilities rather than fragment them. A good threat intelligence platform should help control long-term cost by reducing tool sprawl and operational complexity, not quietly increasing it.
Bring Threat Intelligence Back to Day-To-Day Security
By this point, one thing should be clear. Threat intelligence is only useful when it keeps pace with modern teams. If it lives in reports, separate dashboards, or weekly reviews, it will always arrive too late to change outcomes.
The teams getting the most value today are not chasing more data. They are choosing platforms that reduce friction, cut noise, and help engineers make better decisions without slowing delivery. That means looking beyond features and asking harder questions about fit, scalability, and operational effort.
This is where threat detection tools like Aikido Security stand out. By embedding threat intelligence directly into security workflows across code, cloud, and runtime, Aikido helps teams move from awareness to action faster, without adding more tools to manage or more alerts to triage.
See how Aikido Security helps teams bring threat intelligence back to day-to-day security, book a demo and explore the platform today.
FAQs
What makes Aikido Security different from traditional threat intelligence tools?
Most traditional threat intelligence tools focus on collecting and presenting external data, then rely on analysts to interpret it. Aikido Security embeds threat intelligence directly into a security platform that understands your applications, cloud environment, and runtime behaviour. The focus is not on showing more information, but on helping teams decide what to fix first with less effort.
Is Aikido Security a replacement for standalone threat intelligence feeds?
For many teams, yes. Aikido Security is designed to remove the need for separate threat intelligence feeds by providing prioritized, context-aware insight as part of its security capabilities. Instead of managing feeds and dashboards, teams get intelligence that is already mapped to real exposure in their environment.
How does Aikido Security reduce alert fatigue?
Aikido Security reduces noise by correlating findings with exploitability, reachability, and real-world risk. Rather than surfacing every possible issue, it highlights the ones that matter most, which helps teams spend less time triaging and more time fixing meaningful risks.
Who is Aikido Security best suited for?
Aikido Security works best for engineering-led teams that want strong security outcomes without heavy operational overhead. It is particularly well-suited for DevSecOps teams that need threat intelligence to fit naturally into development and cloud workflows, rather than living in a separate security silo.
Can Aikido Security scale as teams and environments grow?
Yes. Aikido Security is built to scale with modern, fast-changing environments by reducing dependency on manual analysis and tuning. As applications, dependencies, and cloud resources grow, the platform continues to automatically prioritize risk, without requiring proportional increases in tooling or headcount.
You Might Also Like:
- SAST vs SCA: Securing the Code You Write and the Code You Depend On
- The Top 13 Code Vulnerability Scanners in 2026
- OWASP Top 10 for Agentic Applications (2026): What Developers and Security Teams Need to Know
- Supply Chain Security: The Ultimate Guide to Software Composition Analysis (SCA) Tools
- What Is CSPM (and CNAPP)? Cloud Security Posture Management Explained

Secure your software now





.avif)
