Software Security for FinTech
From compliance-heavy banking APIs to high-speed crypto exchanges, Aikido helps FinTech teams ship fast, stay compliant, and safeguard their SDLC, without slowing development.
- Scanning of Code, Containers, Cloud, SBOMs and more
- Accelerate compliance (DORA, PCI, SOC 2, and more)
.avif)
These companies sleep better at night







.png)
Accelerate security, win client trust
FinTech moves fast, but security and compliance can’t be left behind.
Aikido keeps your release cycles secure and audit-ready for DORA, PCI DSS, and ISO 27001, proving your posture to customers, partners, and regulators.

All-in-one Security built for speed & credibility
In FinTech, credibility is currency. Aikido helps you meet the highest security standards without slowing delivery.
- Unify detection, monitoring, and remediation
- Fix issues before production
- Prove compliance with audit-ready reports
Hassle-free Compliance
From PCI DSS to DORA, ISO 27001, SOC 2, and NIS2, compliance is table stakes in FinTech. Aikido makes it easy to achieve and retain certification, with automated controls, clear reporting, and faster time-to-audit.
- Automate SBOMs, OSS license checks & NIS2-aligned reports
- Generate audit-ready evidence for DORA, PCI DSS, and more
- Deliver clear proof to partners, auditors & regulators
- Cut compliance overhead with built-in controls and reporting

Autonomous AI Pentesting
Security isn’t just about scanning, it’s about understanding how real adversaries move.
Our AI agents analyze your code and deployed web apps or APIs, simulate real attacker behavior, and deliver a verified SOC2- and ISO27001-ready report - all within hours.
- End-to-End Attack Paths: Map exploitable routes across code, cloud, and runtime.
- Exploit Simulations: Test against real-world techniques without risk to production.
- Prioritized Risk: Focus on the vulnerabilities attackers would actually exploit.
Crypto & Web3 ready
Crypto teams need proactive defense. Aikido adds in-app runtime protection to stop exploits in real time, and our Open Source Threat Feed surfaces risks others miss.
- Open Source Threat Feed: Human-verified intel, tens of thousands of vulns & malware packages uncovered (incl. gaps in NVD/GitHub)
- Runtime protection: block attacks as they happen inside your app
- Early warning on zero-days in critical open-source dependencies

Everything You Wish Security Tools Actually Did
Static Application Security Testing (SAST)
Scans your source code for security vulnerabilities such as SQL injection, XSS, buffer overflows and other security risks. Checks against popular CVE databases. It works out-of-the-box and supports all major languages.

Software Composition Analysis
Analyse third-party components such as libraries, frameworks, and dependencies for vulnerabilities. Aikido does reachability analysis, triages to filter out false positives, and provides clear remediation advice. Auto-fix vulnerabilities with one click.

Infrastructure as code (IaC)
Scans Terraform, CloudFormation & Kubernetes Helm charts for misconfigurations.
- Catch misconfigurations that expose your infrastructure to risk
- Identify vulnerabilities before they reach your main branch
- Integrates in your CI/CD Pipeline

Container Security
Scan your container operating system for packages with security issues.
- Checks if your containers have any vulnerabilities (Like CVEs)
- Highlights vulnerabilities based on container data sensitivity
- Auto-fix your container images with AI

DAST & API Security
Monitor your app and APIs to find vulnerabilities like SQL injection, XSS, and CSRF, both on the surface and with authenticated DAST.
Simulate real-world attacks and scan every API endpoint for common security threats.
.avif)
Cloud & K8s Security Posture Management (CSPM)
Detect cloud infrastructure risks across major cloud providers.
- Scans Virtual Machines (AWS EC2 instances) for vulnerabilities.
- Scan your cloud for misconfigurations and overly permissive user roles/access
- Automate security policies & compliance checks for SOC2, ISO27001, CIS & NIS2

Secrets detection
Check your code for leaked and exposed API keys, passwords, certificates, encryption keys, etc…

Malware detection
The npm ecosystem is susceptible to malicious packages being published because of its open nature. Aikido identifies malicious code that may be embedded within JavaScript files or npm packages. (Scans for backdoors, trojans, keyloggers, XSS, cryptojacking scripts and more.)

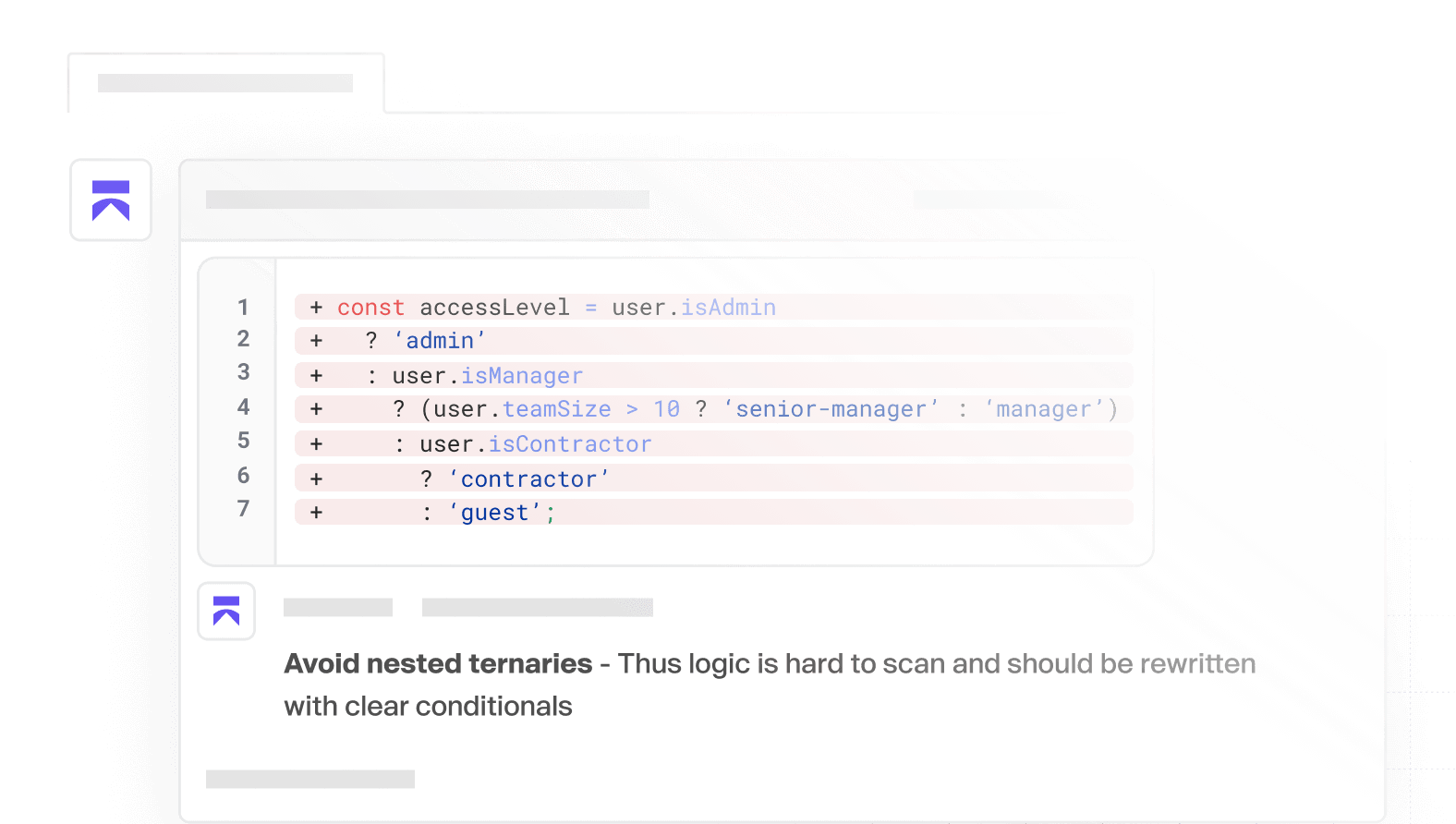
AI Code Quality
Ship quality code, faster. Instant feedback, smart detection, and clear PR comments, so you can focus on building.
Compliance
Get Your Compliance In Check
Aikido performs checks and generates evidence for technical controls for ISO 27001:2022, SOC 2 Type 2, PCI Security standard, and for DORA. Automating technical controls is a big step-up towards achieving compliance.
ISO 27001:2022
ISO 27001 is particularly relevant for FinTech companies. This globally recognized standard ensures that you have a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. Aikido automates a variety of ISO 27001:2022 technical controls.

SOC 2 Type 2
SOC 2 is a procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. Show your commitment to safeguarding data by complying with SOC2. Aikido automates all technical controls, making the compliance process much easier.

DORA
The Digital Operational Resilience Act (DORA) is an EU regulation that requires financial institutions to strengthen their defenses against IT-related risks. Aikido helps with DORA compliance by automating the detection, and remediation of security vulnerabilities, enabling continuous monitoring, incident reporting, and management of 3d-party risks as required by the DORA regulation.

Payment Card Industry Data Security
The Payment Card Industry Data Security Standard (PCI DSS) require a set of security standards designed to protect cardholder data during and after financial transactions. Any organization that handles credit card information must comply with these standards to ensure the secure processing, storage, and transmission of cardholder data. Aikido automates many technical controls.


.png)



"We tried Checkmarx and Snyk, but Aikido was faster, more actionable, and easier to work with."
"Aikido has had a tremendous impact on how we approach vulnerability management and remediation."
Integrations
Integrate with your compliance suite
Are you using a compliance suite? Aikido integrates with the suite of your choice.
See our integrations


Vanta
The fastest path to compliance. It collects 90% of the evidence needed for your certification.

Drata
Automates your compliance journey from start to audit-ready and beyond.

Sprinto
Sprinto is a one-stop platform for all security compliances and certification audits.
Thoropass
Thoropass is an end-to-end compliance solution offering a seamless security audit experience.
Secureframe
Leading security compliance automation platform that makes getting any compliance fast & easy.
Minimizing false positives, while keeping GitHub as the single source of truth.
"Aikido has had a tremendous impact on how we approach vulnerability management and remediation."

Get secure now
Secure your code, cloud, and runtime in one central system.
Find and fix vulnerabilities fast automatically.


FAQ
Has Aikido itself been security tested?
Yes — we run yearly third-party pentests and maintain a continuous bug bounty program to catch issues early.
Does Aikido require agents?
No! Unlike others, we're fully API based, no agents are needed to deploy Aikido! This way you're up & running in mere minutes & we're way less intrusive!
I don’t want to connect my repository. Can I try it with a test account?
Of course! When you sign up with your git, don’t give access to any repo & select the demo repo instead!
What happens to my data?
We clone the repositories inside of temporary environments (such as docker containers unique to you). Those containers are disposed of, after analysis. The duration of the test and scans themselves take about 1-5 mins. All the clones and containers are then auto-removed after that, always, every time, for every customer.

.svg)


