Why do Security Tech companies use Aikido?
As a security technology company, it is essential to lead by example and maintain the highest standards of security for your application. After all, how can your customers trust you if you don’t implement the strictest security practices?
A data breach could severely compromise your company’s reputation and credibility. With Aikido’s application security solution, you get all-round protection and real-time vulnerability detection, so you have peace of mind for you and your clients.
Compliance
Prepare for ISO & SOC2 compliance
Aikido performs checks and generates evidence for technical controls for ISO 27001:2022 & SOC 2 Type 2. Automating technical controls is a big step-up towards achieving ISO & SOC 2 compliance.
ISO 27001:2022
ISO 27001 is particularly relevant for Security Tech companies. This globally recognized standard ensures that you have a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. Aikido automates a variety of ISO 27001 technical controls.

SOC 2 Type 2
SOC 2 is a procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. Show your commitment to safeguarding data by complying with SOC2. Aikido automates all technical controls, making the compliance process much easier.

Aikido covers all technical code and cloud security requirements for SOC2 Type 2, ISO 27001:2022, and more
SOC 2 Controls
CC3.3: Consider the potential for fraud
CC3.2: Estimate Significance of Risks Identified
CC5.2: The entity selects and develops general control activities over technology to support the achievement of objectives
CC6.1 • CC6.6 • CC6.7 • CC6.8
CC7.1: Monitor infrastructure and software
CC7.1: Implement change detection mechanism
CC7.1: Detect unknown or unauthorized components
CC7.1: Conduct vulnerability scans
CC7.1: Implement filters to analyze anomalies
CC7.1: Restores the affected environments
CC10.3: Tests integrity and completeness of backup data
CC8.1: Protect confidential information
CC8.1: Track system changes
ISO 27001 Controls
A.8.2 Privileged access rights • A.8.3 Information access restriction • A.8.5 Secure authentication • A.8.6 Capacity management • A.8.7 Protection against malware • A.8.8 Management of technical vulnerabilities • A.8.9 Configuration management • A.8.12 Data leakage prevention • A.8.13 Backups • A.8.15 Logging • A.8.16 Monitoring activities • A.8.18 Use of privileged utility programs • A.8.20 Network security • A.8.24 Use of cryptography • A.8.25 Secure development lifecycle • A.8.28 Secure coding • A.8.31 Separation of development, test and production environments • A.8.32 Change management
A.5.15: Access control
A.5.16: Identity management
A.5.28: Collection of evidence
A.5.33: Protection of records
Integrations
Integrate with your compliance suite
Are you using a compliance suite? Aikido integrates with the suite of your choice.
See our integrations


Vanta
The fastest path to compliance. It collects 90% of the evidence needed for your certification.

Drata
Automates your compliance journey from start to audit-ready and beyond.

Sprinto
Sprinto is a one-stop platform for all security compliances and certification audits.
Thoropass
Thoropass is an end-to-end compliance solution offering a seamless security audit experience.
Secureframe
Leading security compliance automation platform that makes getting any compliance fast & easy.
Everything You Wish Security Tools Actually Did
Static Application Security Testing (SAST)
Scans your source code for security vulnerabilities such as SQL injection, XSS, buffer overflows and other security risks. Checks against popular CVE databases. It works out-of-the-box and supports all major languages.

Software Composition Analysis
Analyse third-party components such as libraries, frameworks, and dependencies for vulnerabilities. Aikido does reachability analysis, triages to filter out false positives, and provides clear remediation advice. Auto-fix vulnerabilities with one click.

Infrastructure as code (IaC)
Scans Terraform, CloudFormation & Kubernetes Helm charts for misconfigurations.
- Catch misconfigurations that expose your infrastructure to risk
- Identify vulnerabilities before they reach your main branch
- Integrates in your CI/CD Pipeline

Container Security
Scan your container operating system for packages with security issues.
- Checks if your containers have any vulnerabilities (Like CVEs)
- Highlights vulnerabilities based on container data sensitivity
- Auto-fix your container images with AI

DAST & API Security
Monitor your app and APIs to find vulnerabilities like SQL injection, XSS, and CSRF, both on the surface and with authenticated DAST.
Simulate real-world attacks and scan every API endpoint for common security threats.
.avif)
Cloud & K8s Security Posture Management (CSPM)
Detect cloud infrastructure risks across major cloud providers.
- Scans Virtual Machines (AWS EC2 instances) for vulnerabilities.
- Scan your cloud for misconfigurations and overly permissive user roles/access
- Automate security policies & compliance checks for SOC2, ISO27001, CIS & NIS2

Secrets detection
Check your code for leaked and exposed API keys, passwords, certificates, encryption keys, etc…

Malware detection
The npm ecosystem is susceptible to malicious packages being published because of its open nature. Aikido identifies malicious code that may be embedded within JavaScript files or npm packages. (Scans for backdoors, trojans, keyloggers, XSS, cryptojacking scripts and more.)

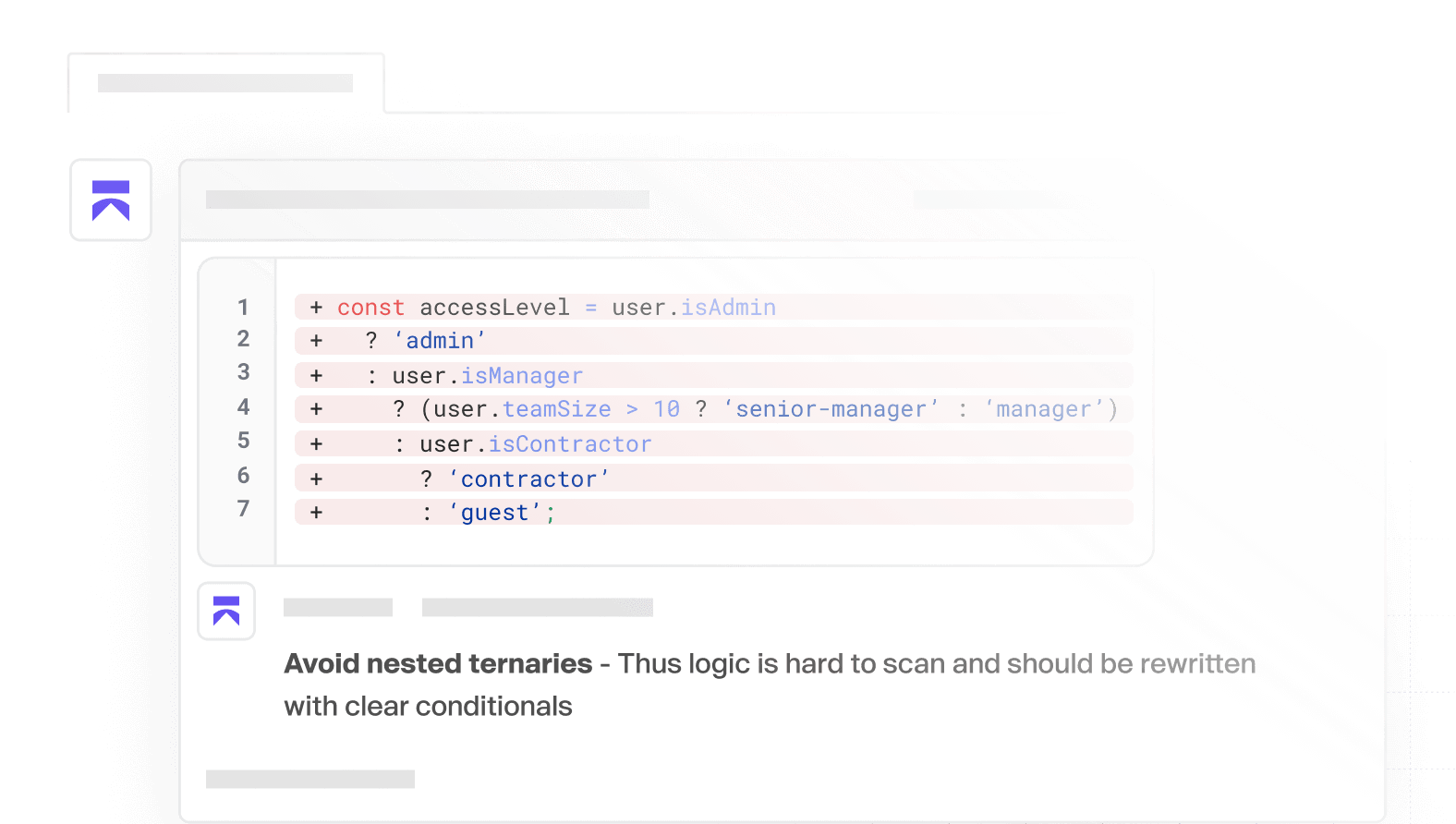
AI Code Quality
Ship quality code, faster. Instant feedback, smart detection, and clear PR comments, so you can focus on building.
FAQ
Has Aikido itself been security tested?
Yes — we run yearly third-party pentests and maintain a continuous bug bounty program to catch issues early.
Does Aikido require agents?
No! Unlike others, we're fully API based, no agents are needed to deploy Aikido! This way you're up & running in mere minutes & we're way less intrusive!
I don’t want to connect my repository. Can I try it with a test account?
Of course! When you sign up with your git, don’t give access to any repo & select the demo repo instead!
What happens to my data?
We clone the repositories inside of temporary environments (such as docker containers unique to you). Those containers are disposed of, after analysis. The duration of the test and scans themselves take about 1-5 mins. All the clones and containers are then auto-removed after that, always, every time, for every customer.
Get secure now
Secure your code, cloud, and runtime in one central system.
Find and fix vulnerabilities fast automatically.



.avif)



.svg)




.svg)


