The all-in-one Veracode alternative
Secure your code, cloud, and runtime in one central system. Find and fix vulnerabilities automatically.
.avif)


.png)






















How Aikido compares to Veracode
Aikido offers flat, transparent fees with no hidden charges. Veracode is modular and can get expensive if you require multiple scanning features.
Modular pricing





- Reachability Analysis
- Malware Detection in Dependencies
- AutoFix for SCA
- License Compliance
- SBOM Support
- License PR Release Gating
- Noise Reduction (False Positive Filtering)
- More Noisy



- SAST AI Autofix
- Multi-file Analysis
- Taint Analysis
- Custom SAST Rules
- SAST Directly In IDE



- API Discovery/API Fuzz Testing
- Authenticated DAST
- Automated Swagger Creation
- Attack Surface Monitoring
- Only API Scanning


- Whitebox, Greybox, Blackbox Pentests
- IDOR Detection
- Compliance PDF Reports (ISO27001, SOC2)


- Infrastructure as Code Scanning
- Cloud and K8s Posture management
- Virtual Machine Scanning
- Attack Path Analysis
- Cloud Search



- Extended Lifetime Support
- AI AutoFix For Container Images
- Malware Detection in Containers








How users rate us
Based on G2 user reviews.


Everything You Wish Security Tools Actually Did
Static Application Security Testing (SAST)
Scans your source code for security vulnerabilities such as SQL injection, XSS, buffer overflows and other security risks. Checks against popular CVE databases. It works out-of-the-box and supports all major languages.

Software Composition Analysis
Analyse third-party components such as libraries, frameworks, and dependencies for vulnerabilities. Aikido does reachability analysis, triages to filter out false positives, and provides clear remediation advice. Auto-fix vulnerabilities with one click.

Infrastructure as code (IaC)
Scans Terraform, CloudFormation & Kubernetes Helm charts for misconfigurations.
- Catch misconfigurations that expose your infrastructure to risk
- Identify vulnerabilities before they reach your main branch
- Integrates in your CI/CD Pipeline

Container Security
Scan your container operating system for packages with security issues.
- Checks if your containers have any vulnerabilities (Like CVEs)
- Highlights vulnerabilities based on container data sensitivity
- Auto-fix your container images with AI

DAST & API Security
Monitor your app and APIs to find vulnerabilities like SQL injection, XSS, and CSRF, both on the surface and with authenticated DAST.
Simulate real-world attacks and scan every API endpoint for common security threats.
.avif)
Cloud & K8s Security Posture Management (CSPM)
Detect cloud infrastructure risks across major cloud providers.
- Scans Virtual Machines (AWS EC2 instances) for vulnerabilities.
- Scan your cloud for misconfigurations and overly permissive user roles/access
- Automate security policies & compliance checks for SOC2, ISO27001, CIS & NIS2

Secrets detection
Check your code for leaked and exposed API keys, passwords, certificates, encryption keys, etc…

Malware detection
The npm ecosystem is susceptible to malicious packages being published because of its open nature. Aikido identifies malicious code that may be embedded within JavaScript files or npm packages. (Scans for backdoors, trojans, keyloggers, XSS, cryptojacking scripts and more.)

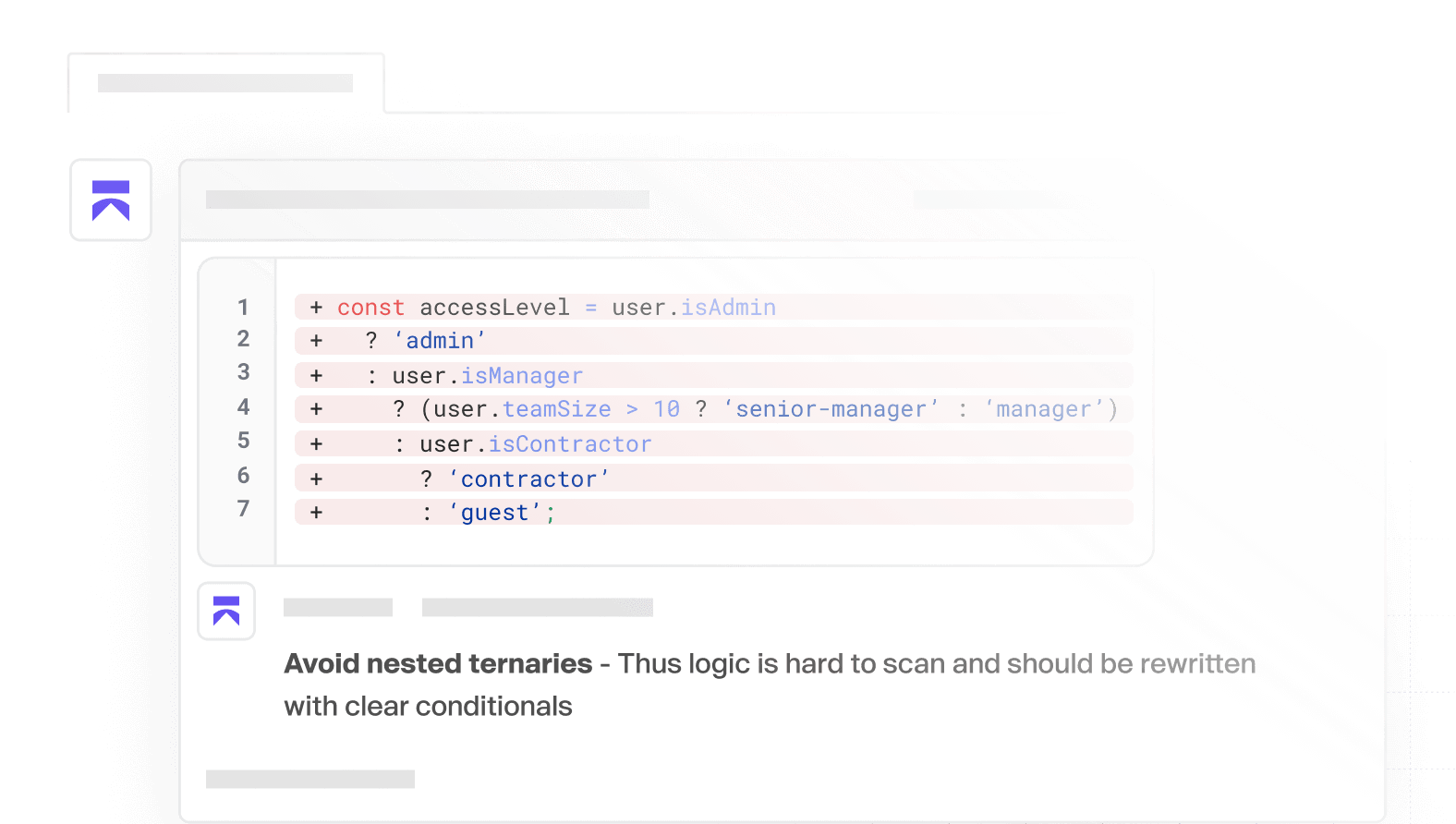
AI Code Quality
Ship quality code, faster. Instant feedback, smart detection, and clear PR comments, so you can focus on building.
Get secure now
Secure your code, cloud, and runtime in one central system.
Find and fix vulnerabilities fast automatically.




