As artificial intelligence becomes central to how software is written, deployed, and operated, AI security tools are no longer a nice-to-have; they’re essential.
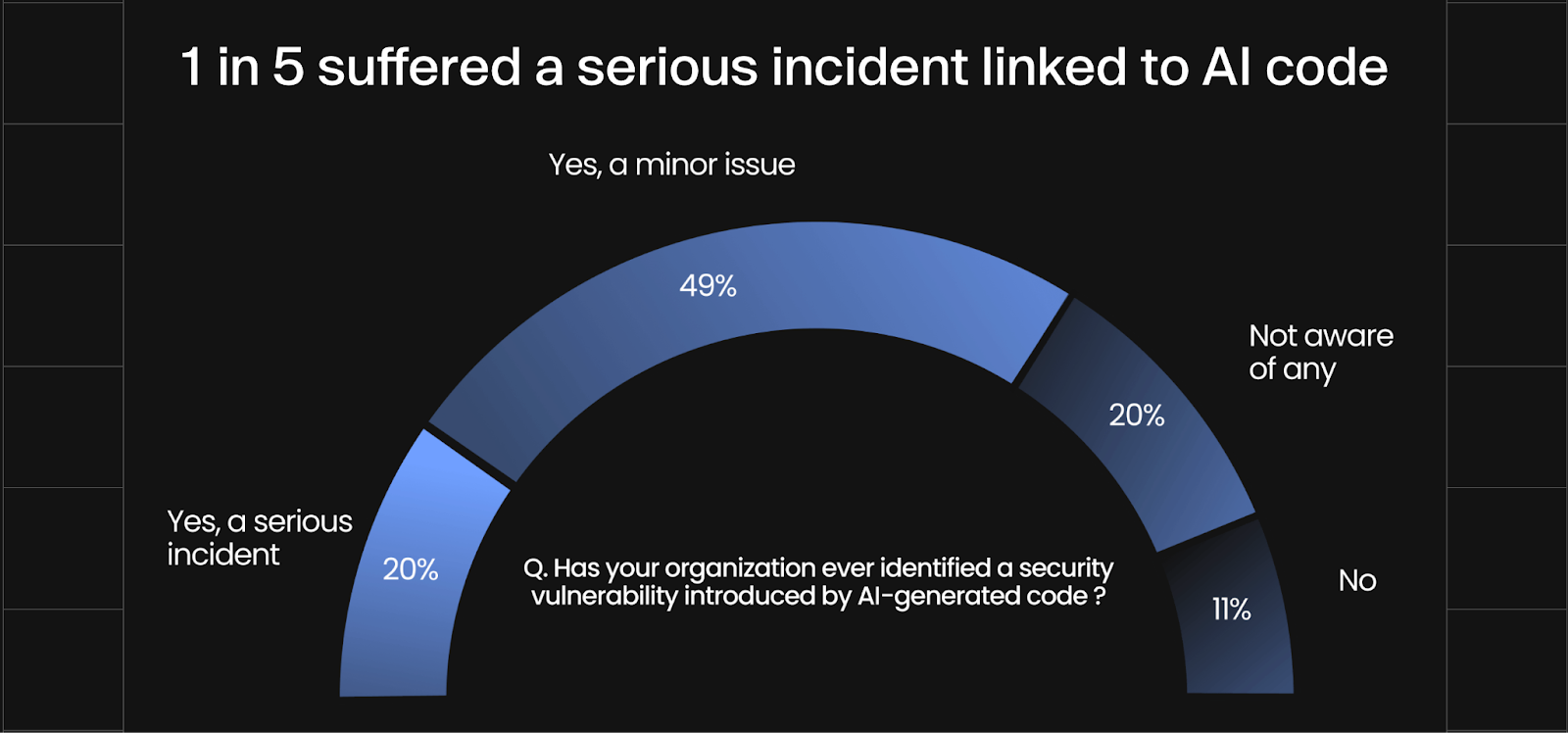
The Aikido 2026 State of AI in Security & Development report revealed that one in five organizations have already experienced a serious security incident linked to AI-generated code. This highlights a growing challenge: as development speeds up with AI assistance, traditional security tooling often struggles to keep up.
This shift is pushing teams to rethink how they secure applications, data, and cloud environments. Regardless of if you’re a developer adopting AI-assisted coding or a security leader evaluating modern tooling, a basic understanding of how AI can be used to improve your security outcomes can go a long way.
In this guide, we’ll look at a range of AI security tools, covering platforms that use AI for vulnerability detection, intelligent triage, automated remediation, AIcontinuous pentesting, and enterprise-grade risk management.
Here’s a quick glance of all the tools we’ll cover:
- Aikido Security
- Arctic Wolf
- Cato Networks
- Cisco AI Defense
- CodeRabbit
- CrowdStrike
- Invicti
- Protect AI (Palo Alto Networks)
- SentinelOne
- XBOW
What are AI Security Tools?
AI security tools platforms that use artificial intelligence to detect, prioritize, and remediate security risks across applications, cloud infrastructure, and development workflows.
By applying techniques like large language models, contextual analysis, and automated reasoning to tasks such as code scanning, vulnerability triage, pentesting, and incident response, these tools reduce false positives and focus teams on real, exploitable issues.
The result is faster, smarter security that scales with modern cloud-native development, offering end-to-end visibility across code, dependencies, APIs, and runtime environments while helping teams fix issues quickly without slowing down delivery.
What to Look For in an AI Security Tool
Choosing an AI security tool is not about who uses the most AI buzzwords. The right tool should reduce real risk, save developer time, and fit naturally into existing workflows. When evaluating options, focus on these core qualities rather than long feature lists.
- Clear security value, not AI for its own sake: Strong AI security tools apply AI where it genuinely improves outcomes, such as reducing false positives, adding context to findings, or helping teams understand what matters first. The goal is clarity and signal, not more alerts.
- Coverage that matches your environment: No single tool covers everything, but it should align with how your applications are built and deployed. Whether that is source code, dependencies, APIs, cloud infrastructure, or runtime environments, the tool should secure the parts of the stack that matter most to your team.
- Actionable findings and remediation support: Detection alone is not enough. Look for tools that help teams move from finding issues to fixing them, through clear guidance, prioritization, or automation that shortens remediation time and reduces back-and-forth between security and engineering.
- Workflow fit and ease of adoption: The best tools integrate smoothly into source control, CI/CD pipelines, or cloud environments without slowing development. Easy setup, intuitive interfaces, and developer-friendly outputs increase adoption and make security a natural part of the workflow rather than a blocker.
Top 10 AI Security Tools
1. Aikido Security
Aikido Security is an AI-powered security platform that is designed to reduce the friction between finding vulnerabilities and fixing them. It applies AI across the security lifecycle, helping teams review code, triage findings, remediate issues, and validate real-world exploitability without relying on fragmented tools or manual analysis.
At the code level, Aikido uses AI code review to analyze pull requests and source code for logic errors, insecure patterns, and edge cases that traditional scanners often miss. Instead of producing generic warnings, it evaluates code in context and provides actionable feedback that fits naturally into developer workflows.
A core part of the platform is AutoTriage, which addresses one of the biggest problems in application security: false positives. AutoTriage uses AI reasoning, reachability analysis, and environment context to assess whether a vulnerability is actually exploitable and how urgently it should be addressed. This allows teams to focus on high-impact issues while automatically dismissing findings that do not pose real risk.
To complete the workflow, Aikido pairs detection with AI AutoFix and AI Pentesting. AutoFix generates targeted fixes for confirmed vulnerabilities and opens pull requests automatically, while AI-powered pentesting simulates real attack paths across code, cloud, and runtime environments. Together, these capabilities help teams validate their defenses and close security gaps earlier in the development process.
Features
- AI-Code Review: Reviews pull requests and code for logic bugs, risky patterns, and unsafe constructs with context-aware analysis.
- AutoTriage: Uses AI and reachability analysis to filter false positives, confirm true positives, and prioritize vulnerabilities based on exploitability and impact across languages and environments.
- AI AutoFix: Generates safe, minimal fixes for SAST, IaC, container, and dependency issues and creates pull requests automatically.
- AI Pentesting: Autonomous AI-powered penetration testing that maps real attack paths and validates vulnerabilities across code, cloud, and runtime environments.
- Developer Workflows: Integrates into IDEs, CI/CD pipelines, and developer tools for early detection and in-context remediation.
Pros
- Uses AI to reduce noise and improve accuracy, not just generate more alerts.
- Covers the full application security lifecycle without requiring multiple disconnected tools.
- Strong focus on remediation speed, not just detection.
- Designed for developers, not just security teams, which improves adoption.
- Consistently strong user feedback around usability and onboarding.
Gartner Rating: 4.8/5.0
2. Arctic Wolf

Arctic Wolf is an AI-powered Managed Detection and Response (MDR) platform designed to help organizations detect, prioritize, and respond to security threats without building or staffing a full in-house SOC. Rather than replacing existing security tools, Arctic Wolf sits on top of them, using AI-driven analytics and human security operations to correlate signals across endpoints, networks, cloud environments, and identity systems. Its core value lies in turning noisy security data into prioritized, actionable incidents that security teams can actually respond to.
Features
- AI-Driven Threat Detection: Uses machine learning and behavioral analytics to detect suspicious activity across endpoints, networks, cloud workloads, and identities.
- Security Operations Platform (Aurora): Centralized platform that ingests telemetry from existing security tools and applies AI-based correlation and risk scoring.
- Managed Detection & Response (MDR): 24/7 monitoring and incident response delivered by Arctic Wolf’s security operations team.
- Risk Prioritization & Alert Reduction: AI filters low-signal alerts and escalates verified, high-impact incidents to reduce alert fatigue.
Pros
- Strong AI-assisted detection combined with human-led response reduces operational burden on internal teams.
- Effective at reducing alert noise by correlating signals across multiple security tools.
- Well-suited for organizations without a mature SOC or 24/7 security coverage.
- Broad integration support across endpoint, cloud, network, and identity tools.
Cons
- Not a developer-focused tool; offers no code scanning, SAST, SCA, or CI/CD integrations.
- Remediation is advisory rather than automated, requiring internal teams to execute fixes.
- Heavily reliant on existing security tooling, so value depends on current stack maturity.
- Less visibility into application-layer or code-level vulnerabilities.
- Pricing is service-based and can be expensive for smaller teams or startups.
- Limited control over detection logic compared to fully self-managed platforms.
Gartner Rating: 4.9/5.0
3. Cato Networks (with AI Security from Aim)

Cato Networks is a Secure Access Service Edge (SASE) platform that combines networking and security capabilities into a cloud-native service designed to protect users, devices, applications, and data wherever they are. In 2025, Cato expanded its platform’s AI security capabilities by acquiring Aim Security, bringing advanced AI-centric protections into its SASE Cloud Platform.
This acquisition enables Cato to secure not just network traffic and application access, but also AI-related interactions and workflows, such as employee use of public AI apps, internal AI agents, and the broader AI development lifecycle, all under unified policies and visibility.
Features
- Unified SASE Platform: Secure networking, secure access, and AI-aware protection delivered from a single cloud service.
- AI Interaction Security: Aim’s technology secures employee use of public AI tools, internal AI applications, and runtime AI agents, and enforces governance policies across AI interactions.
- AI Firewall & Policy Enforcement: Controls AI traffic and enforces corporate security rules for AI workloads and communications.
- AI Security Posture Management: Continuously discovers, detects, and remediates AI-specific risks across development, training, and runtime environments.
- Global SASE Capabilities: Secure SD-WAN, Zero Trust Network Access (ZTNA), firewall, threat prevention, and data protection all in one platform.
Pros
- Comprehensive, converged platform: Networking, security, and AI security under one cloud-native umbrella.
- Strong Gartner positioning: Named a Leader in the 2025 Gartner Magic Quadrant for SASE Platforms, reflecting broad enterprise recognition.
- Centralized AI policy control: Protects AI interactions consistently across user, cloud, and application surfaces.
- Broad visibility and threat enforcement: Leverages a global cloud fabric to inspect and protect traffic in real time.
Cons
- Complexity for small teams: As a full enterprise SASE platform, it may be overkill for small companies that don’t yet need full SASE + AI security convergence.
- Integration & migration: Full Aim-powered AI security features will fully converge into the platform by early 2026, which can create transitional complexity for current customers.
- Pricing model: SASE solutions with AI extensions can have complex licensing and cost structures that require careful budgeting.
- Less focused on pure app security: While strong at network and policy-based protections, it doesn’t replace specialized code-level tools like SAST/SCA for developer teams.
- AI security still evolving: The integration and maturity of advanced AI risks (e.g., prompt injection detection) are comparatively new and may lack depth found in dedicated AI security startups.
- Operational learning curve: Admins may need additional training to configure AI policy enforcement and AI risk workflows effectively.
- Peer reviews vary: While strong as a SASE platform, specific AI security experience feedback from users is still emerging.
Gartner Rating: 4.6/5.0
4. Cisco AI Defense
Cisco AI Defense is an enterprise-grade AI security solution designed to protect organizations’ AI initiatives across development, deployment, and runtime. Built on Cisco’s long-standing cybersecurity and networking expertise, AI Defense fills critical gaps left by traditional security tools by offering comprehensive visibility into AI assets, proactive vulnerability detection, and real-time protection against adversarial threats like prompt injections, data leakage, and denial-of-service attacks.
Features
- AI Asset Discovery & Visibility: Automatically identifies AI models, applications, and agents across multi-cloud environments to map the full AI attack surface.
- AI Model & Application Validation: Uses algorithmic red teaming and automated testing to detect vulnerabilities and safety issues in models and custom AI applications.
- AI Runtime Protection: Provides guardrails and defenses at runtime to block adversarial inputs and harmful outputs in real time.
- AI Access Control: Monitors and manages employee access to sanctioned and unsanctioned third-party AI tools to prevent sensitive data exposure.
- AI Supply Chain Risk Management: Detects risks from external or third-party models and ensures governance across the AI supply chain.
- Network-Level Enforcement: Leverages Cisco Security Cloud and Talos threat intelligence for high-accuracy threat detection and continuous protection.
Pros
- Offers end-to-end coverage across discovery, detection, and protection for enterprise AI environments.
- Integrates with Cisco’s broader security portfolio for unified visibility and policy management.
- Provides proactive testing and runtime guardrails tailored to emerging AI threats.
- Strong access control and shadow AI monitoring help mitigate risky employee use of external AI tools.
Cons
- Designed primarily for large enterprises, which can make deployment and configuration complex for smaller teams.
- May not replace specialized AppSec tools (e.g., SAST/SCA) for deep code-level vulnerabilities.
- Pricing and licensing can be complicated due to its extensive enterprise features.
- Advanced AI security policies may require experienced security teams to tune effectively.
- Peer review and independent ratings specifically for AI Defense are still emerging given its recent launch.
- Integration with existing cloud and DevSecOps tooling may need customization.
- Runtime protections can generate nuanced alerts that require expert interpretation.
Gartner Rating: 4.6/5.0
5. CodeRabbit
CodeRabbit is an AI-powered code review assistant designed to help engineering teams automate and scale the code review process. It integrates with version control systems, IDEs, and CI workflows to analyze pull requests and commits, providing contextual feedback on bugs, logic issues, style inconsistencies, and potential security concerns.
Features
- AI Code Reviews: Automated, context-aware analysis of pull requests with inline suggestions and summaries.
- IDE & CLI Integration: Review code directly in editors like VS Code or via command-line tools.
- Custom Rules & Learnings: Teams can tailor review behavior with custom guidelines and feedback loops.
- Security & Privacy Controls: SOC 2 Type II certification, ephemeral processing with no persistent code storage, and encrypted reviews.
Pros
- Speeds up code reviews and identifies issues developers might miss.
- Integrates smoothly with GitHub, GitLab, and IDE environments.
- Learns from team feedback to refine suggestions over time.
- Provides helpful summaries and walkthroughs for large pull requests.
Cons
- Generates a high volume of suggestions, sometimes including low-value or incorrect feedback that creates review noise.
- Some users report inconsistent accuracy, particularly with more complex logic or nuanced contexts, requiring careful human oversight.
- Customer support experiences have been mixed, with slow or unhelpful responses in some cases.
- Customization for advanced workflows can have a learning curve or require manual configuration.
- Free tier and rate limits may restrict full use for high-volume teams.
Gartner Rating: 4.3/5.0
6. CrowdStrike
CrowdStrike is a leading cybersecurity platform that uses AI and machine learning to power threat detection, prevention, and response across endpoints, identities, cloud workloads, and more.
Its core product, the Falcon platform, combines real-time telemetry with AI-driven analytics to help teams detect sophisticated threats quickly, prioritize what matters most, and automate response actions where possible.
Features
- AI-Powered Detection & Response: The Falcon platform uses machine learning trained on trillions of security events to identify and respond to threats in real time across endpoints, identities, and cloud environments.
- Generative AI Analyst (Charlotte AI): Allows users to interact with security data using natural language, accelerating threat hunting and investigation.
- Threat Hunting & Intelligence: AI augments proactive threat discovery and contextualized threat intelligence to help uncover advanced adversary behaviors.
- Automated Triage & Remediation: AI prioritizes critical alerts and can automate response actions (e.g., containment or isolation) to reduce analyst workload.
Pros
- Strong AI-driven detection and prioritization help reduce noise and focus teams on real risk.
- Uses world-scale telemetry and threat intelligence to continuously improve accuracy and threat context.
- Generative AI tools like Charlotte AI help analysts of all experience levels work faster and make better decisions.
- Falcon’s lightweight agent architecture simplifies deployment and scaling across large environments.
Cons
- Not focused on traditional application security (e.g., code scanning, SAST, API security). It’s primarily about detection and response.
- Advanced features and full AI-driven automation may require skilled security teams to configure and operate effectively.
- Pricing and licensing can be complex for smaller organizations due to the breadth of modules.
- Endpoint and identity telemetry volumes can be large, requiring careful management to avoid alert overload.
- Some teams report a learning curve with the Falcon interface and configuration complexity.
- Deep integrations for cloud-native workloads may necessitate additional planning and resources.
Gartner Rating: 4.7/5.0
7. Invicti
Invicti is an AI-powered application security platform that strengthens traditional vulnerability scanning with machine learning and automation. At its core is a dynamic application security testing (DAST) engine that not only discovers real vulnerabilities in web apps and APIs but also uses AI-driven techniques to enhance discovery, crawl coverage, and risk prioritization. Invicti integrates static and dynamic analysis with predictive risk scoring and remediation guidance to help teams surface real, exploitable issues and reduce noise in security workflows.
Features
- AI-Enhanced DAST: Uses machine learning to improve scan accuracy, extend crawl coverage, handle complex application behaviors, and detect deep vulnerabilities.
- Predictive Risk Scoring: Assigns risk levels to applications or endpoints before scanning, helping teams prioritize which assets to test first.
- AI-Assisted Auto-Login & Crawling: Automatically identifies and interacts with login forms and complex app workflows for fuller scan coverage.
- Integrated AppSec Platform: Combines DAST with SAST, SCA, API scanning, and application security posture management (ASPM) for consolidated vulnerability views.
- AI-Driven Remediation Guidance: Provides context-aware fix suggestions and correlates results across tools to reduce false positives and streamline developer action.
Pros
- AI capabilities enhance traditional scanning, improving coverage and accuracy compared to legacy tools.
- Predictive risk scoring helps teams focus on the most critical assets first.
- Integration across SAST, DAST, and SCA provides a unified view of application risk.
- AI-assisted crawling and auto-login reduce the manual setup required for comprehensive scans.
Cons
- Scans can be slower and consume significant resources on very large applications.
- Some users find the interface cluttered and reporting less intuitive than competitors.
- Pricing and licensing can be high for smaller teams or midsize organizations.
- Advanced API testing may require careful configuration and up-front work to maximize effectiveness.
- Not focused on real-time runtime security; it primarily enhances traditional scanning.
- Depth of AI assistance can vary based on application complexity and configuration.
Gartner Rating: 4.4/5/0.
8. Protect AI
Protect AI by Palo Alto Networks is an AI security and compliance platform built specifically to protect machine learning and AI systems throughout development, deployment, and runtime.
Unlike traditional cybersecurity tools that focus on networks or endpoints, Protect AI is centered on securing AI models, their supply chain, and operational behavior. It scans models for malicious or unsafe code, enforces security policies before models are used, monitors model behavior for adversarial attacks, and provides governance features that help teams maintain trust and compliance as they scale AI adoption.
Features
- ModelScan & Guardian: Scans open-source and proprietary ML models for unsafe code, malware, and serialization attacks before models enter production.
- AI Threat Detection: Continuously monitors AI and ML workflows for adversarial inputs, data poisoning, and unexpected behaviors.
- AI Asset Visibility: Centralized dashboards give insight into model inventories, dependencies, lineage, and compliance status.
- Governance & Compliance: Tracks and reports on AI system behaviors to help meet regulatory standards like SOC 2, ISO 27001, and data protection frameworks.
- Seamless Integration: Works with major ML frameworks such as TensorFlow, PyTorch, and Hugging Face ecosystems, enabling rapid setup with existing workflows.
Pros
- Tailored to the unique risks of AI and ML systems, which traditional security tools often miss.
- Provides model-level scanning and continuous monitoring that extends beyond simple vulnerability detection.
- Helps teams enforce policies and maintain compliance in regulated environments.
- Supports both cloud and on-premises workflows for flexible deployment.
Cons
- Not yet widely rated on major analyst platforms with extensive peer reviews, so comparative visibility is limited.
- Focused primarily on AI/ML system security; it’s not a full application security suite.
- Advanced governance and compliance features may require dedicated expertise to configure correctly.
- Model scanning and runtime detection can generate contextual alerts that still require human analysis.
- Some organizations may need to combine this with other tools for complete DevSecOps coverage.
- Enterprise pricing and license structure are typically custom, making budgeting unclear for smaller teams.
- Teams without mature MLSecOps practices may need time to fully integrate and operationalize the platform.
Gartner Rating: 4.7/5.0
9. SentinelOne

SentinelOne is an AI-powered endpoint and extended detection and response (XDR) platform that uses advanced machine learning and autonomous reasoning to detect, prevent, and respond to threats across endpoints, cloud workloads, identities, and more.
Built around its Singularity platform, SentinelOne applies AI at every stage of the security lifecycle helping security teams reduce manual work and prioritize real risk faster. Its AI-centric architecture means it was designed from the ground up to leverage machine intelligence as a core part of its defenses, not just bolt it on.
Features
- AI-Powered Detection & Response: Uses machine learning and behavioral models to detect threats like ransomware, zero-day attacks, and anomalous behavior without relying solely on signatures.
- Singularity Platform: Unified architecture for endpoint, cloud, identity, and workload security with one lightweight agent for broad protection.
- Automated Remediation & Rollback: Offers automated or one-click remediation and rollback capabilities to quickly contain and resolve incidents.
- Threat Hunting & Intelligence: AI helps proactively uncover sophisticated threats and correlate signals across environments to guide responses.
Pros
- Uses AI extensively for real-time detection, prioritization, and automated response, reducing manual analyst burden.
- Unified platform covers endpoint, cloud workloads, identity, and XDR with a single agent, simplifying deployment.
- Automated rollback and remediation help teams fix issues quickly with minimal human effort.
Cons
- Primarily focused on endpoint and XDR; less coverage of application security scanning like SAST/DAST.
- Advanced features and AI tuning may require experienced security teams to configure effectively.
- Pricing and licensing can be higher and complex for smaller organizations due to broad platform breadth.
- Some integrations (e.g., deeper CI/CD or developer-centric workflows) are limited compared with specialized DevSecOps tools.
- Endpoint telemetry volume can generate noise unless tuned carefully, AI helps, but management still matters.
Gartner Rating: 4.8/5.0
10. XBOW
XBOW is an AI-powered autonomous penetration testing platform that simulates real-world attacks without scheduled human pentesters. It uses hundreds of coordinated AI agents to discover, validate, and exploit vulnerabilities across web applications and cloud systems at machine speed. This approach enables security teams to run continuous security assessments and penetration tests that keep pace with fast development cycles, helping identify hidden flaws before attackers do.
Features
- Autonomous Penetration Testing: Fully automated offensive security workflows that discover and exploit vulnerabilities without manual scheduling.
- AI Agent Collaboration: Hundreds of specialized AI agents work in parallel to analyze attack surfaces and validate findings.
- On-Demand Pentesting: Test applications quickly without waiting for human pentesters or lengthy engagements.
- Continuous Security Assessment: Continuous scanning across multiple targets to detect vulnerabilities at development speed.
- Benchmark-Backed Effectiveness: Demonstrated success solving common web security challenges in industry benchmarks.
Pros
- High Speed & Scale: Significantly faster than traditional manual pentesting, enabling frequent and broad vulnerability assessments.
- Real Proof-of-Concept Validation: Attempts to exploit vulnerabilities to confirm impact rather than just flag potential issues.
- Automated Continuous Coverage: Works continuously and autonomously, making security testing a regular part of development.
Cons
- False Positives & Noise: While the platform verifies reports, some automated findings still require manual review to ensure relevance and reduce noise.
- Limited Business Logic Understanding: Struggles with complex logic and contextual issues that rely on deep application understanding.
- Human Oversight Still Needed: Reports often need human verification, so it does not fully replace expert pentesters.
- Opaque Results & Black-Box Outputs: Some users find the output difficult to interpret without detailed expertise, which can slow remediation.
- Compliance and Workflow Integration Gaps: Integrations with developer workflows (e.g., IDEs or CI/CD) are limited compared to dedicated AppSec tools.
- Enterprise Hosting & Compliance Concerns: Hosting and data residency may be constrained by its geographic footprint, which could matter for regulated industries.
Comparing the Top AI Security Tools
Choosing the Right AI Security Tool for Your Organization
Choosing the right AI security tool goes beyond feature checklists. It comes down to how well the platform fits your development workflow, how clearly it surfaces real risks, and how quickly your team can act on them. Many tools focus on isolated parts of the security stack, which often leads to blind spots, alert fatigue, and fragmented security processes.
Aikido Security stands out by applying AI across the entire security lifecycle, from AI-powered code reviews and AutoTriage to one-click AutoFix and autonomous AI pentesting. Instead of overwhelming teams with noise, it focuses on what is truly exploitable and helps developers fix issues where they already work. This makes it a strong choice for startups and enterprises alike, especially teams securing both AI and non-AI workloads without added complexity.
No more stitching together multiple tools, second-guessing alerts, or slowing down delivery just to stay secure. With Aikido, security becomes a natural part of development.
Looking for an AI security platform that helps your team move faster while staying secure? Start a free trial or book a demo with Aikido Security today!

Secure your software now






