The more code you write, the less secure your application becomes.
Why? In one word, complexity.
Modern applications aren’t written from scratch. They are assembled. Developers write custom logic on top of open-source frameworks, libraries, container images, and cloud services. That means security vulnerabilities can be introduced in two very different ways:
- Through the code you write, and
- Through the code you depend on.
According to the OWASP Top 10, the most common categories of vulnerabilities (SQL Injection, Cross-Site Scripting, Broken Access Control, and Insecure Design) are rooted in coding and logic flaws.
This is why SAST (Static Application Security Testing) and SCA (Software Composition Analysis) are important, and where the confusion starts. SAST and SCA are both techniques for reducing risk in the proprietary code we write, but they solve different problems with different approaches.
In this article, we’ll unpack SAST and SCA, when each security testing tool matters most, and how modern AppSec teams can combine both without slowing development to a crawl.
TL;DR
In summary:
- SAST finds security issues in the code you write (logic flaws, injections, buffer overflows).
- SCA finds security issues in the code you depend on (open-source vulnerabilities, licenses, supply-chain risk).
- They are both critical to a secure Software Development Lifecycle (SDLC). They just solve different problems created by different sources of risk.
- Using only one creates blind spots in your applications. Security-conscious teams use both to move fast and reduce the cost of fixing issues in production.
SAST vs. SCA: Main Differences
What is Static Application Security Testing (SAST)?
SAST is the first line of defense against insecure code. It is a methodology for analyzing an application's source code, bytecode, or binary code to identify vulnerabilities and security flaws early in the software development lifecycle (SDLC).
There are many types of vulnerabilities SAST can find, and it depends on the coding practices, technology stack, and frameworks you use.
Below are three examples of vulnerabilities SAST finds in code.
Insecure Cryptographic Practices: The following is a vulnerable Python cryptography code using the obsolete MD5 hash function:
import hashlib
def store_password(password):
# Weak hashing algorithm (MD5 is broken and unsuitable for passwords)
hashed_password = hashlib.md5(password.encode()).hexdigest()
print(f"Storing hashed password: {hashed_password}")
return hashed_password
Hard-coded secrets in source code: The following is a vulnerable JavaScript code with a hard-coded secret:
import { Client } from "pg";
const client = new Client({
host: "db.internal",
user: "admin",
password: "secret",
database: "app",
});
await client.connect();
Remote Code Execution (RCE) vulnerabilities: Giving an attacker the ability to run arbitrary code with the JavaScript eval() function.
eval(userInput);
One line. One vulnerability. One red flag!
There are so many other examples we could show you. Using SAST tools provides valuable insights, enabling you to fix these issues before they become critical.
SAST main features
There are fundamental features and capabilities a SAST tool must have. If a tool can’t deliver on them, it’s likely to become shelfware or slow down your team instead of helping them.
- Broad language and framework support: A SAST tool should work across your entire codebase. Not just one set of frameworks. Modern engineering teams often work in polyglot environments or rely on monorepos. If the SAST scanner doesn’t support various languages or frameworks, you’ll end up with gaps that undermine your entire application security program. For reference, see OWASP’s Application Security Verification Standard (ASVS) for baseline expectations of any SAST tool.
- Source-level (or bytecode-level) analysis without execution: Your SAST should analyze proprietary code without having to run it. That’s what the “Static” stands for. It should also provide real-time insights as you write code. For more on how SAST works, read this ultimate SAST guide.
- Data-flow, control-flow, and taint analysis: First, the SAST understands how data moves through your application, then uses predefined rules on known issues from insecure patterns to taint propagation to flag potential vulnerabilities across code.
- Integration with developer workflows (IDE, CI/CD, version control): Some teams love Travis CI, others swear by Jenkins. Just like broad language and framework support, supporting varied development workflows is critical. A SAST tool like Aikido Security’s solution gives you 100+ integrations with development tools alongside inline feedback in IDEs and PR comments, and gating in CI/CD pipelines.
- Low false-positive rate and meaningful prioritization: You’ve probably heard this before: “We tried SAST, but the noise was too high. We spent time chasing non-issues.”
False positives kill adoption.
SAST should come with accurate and context-aware reachability analysis and be designed to surface real vulnerabilities, not stylistic opinions.
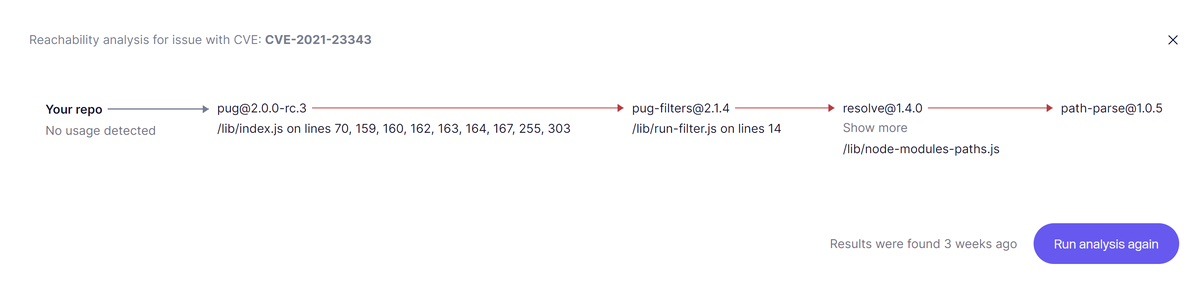
- Clear and actionable remediation guidance: Finding vulnerabilities is only half the job of a SAST tool. Developers need to understand what went wrong and how to fix it. Beyond good remediation guidance – which should be easy to follow and grounded in real-world best practices – AI-Generated fixes are a game changer for SAST today. Your SAST tool of choice should give you instant code-fix suggestions (with confidence levels).
- Enhances compliance and secure-coding enforcement: Code non-compliance can make or break your product. A SAST should flag violations of standards such as OWASP Top-10, CWE/CERT policies, and help you meet regulatory requirements. Even better, choose a tool that can integrate directly with your compliance suite.
- Fast performance and scalability: Avoid any SAST tooling that becomes a bottleneck as you scale. As your codebase grows, your scanner should scale with it, not frustrate engineers.
Advantages of SAST
- Finds vulnerabilities early in the SDLC (Shift-Left): SAST enables organizations to “shift-left” security by catching vulnerabilities early at lower cost.
- Improves secure coding practices over time: By continuously flagging insecure patterns and recommending safer alternatives, SAST raises the security baseline across teams and helps developers learn secure-by-default habits.
- Supports automation and AI-assisted remediation: Today’s SAST tools can suggest fixes automatically which reduces manual effort and accelerates remediation.
- Compliance: As mentioned earlier, compliance is one of the main features of SAST, and this is a huge advantage for organizations in highly regulated industries like financial services and healthcare. With SAST they can meet these requirements at source-code level.
Limitations of SAST
- Coverage gaps: SAST does not cover third-party or open-source risk and it also cannot detect runtime or configuration issues. SAST alone cannot provide holi
- False positives: One major limitation of SAST solutions is that they are prone to false alarms. And with the complexity of infrastructure today, there are mostly a high number of false positives.
- Different SAST tools for every language or framework: Organizations that use more than one programming language struggle to find a SAST that offers support for many languages. If they use more than one, each SAST instance requires different maintenance and configuration processes, operating costs may stack up.\
What is Software composition analysis (SCA)?
SCA is also known as open-source dependency scanning. The SCA testing process involves identifying and managing risks within the open-source components that power your applications.
Most times when we use dependencies, we think it's all rosy. But in reality, the chaos at scale cannot be managed without urgency.
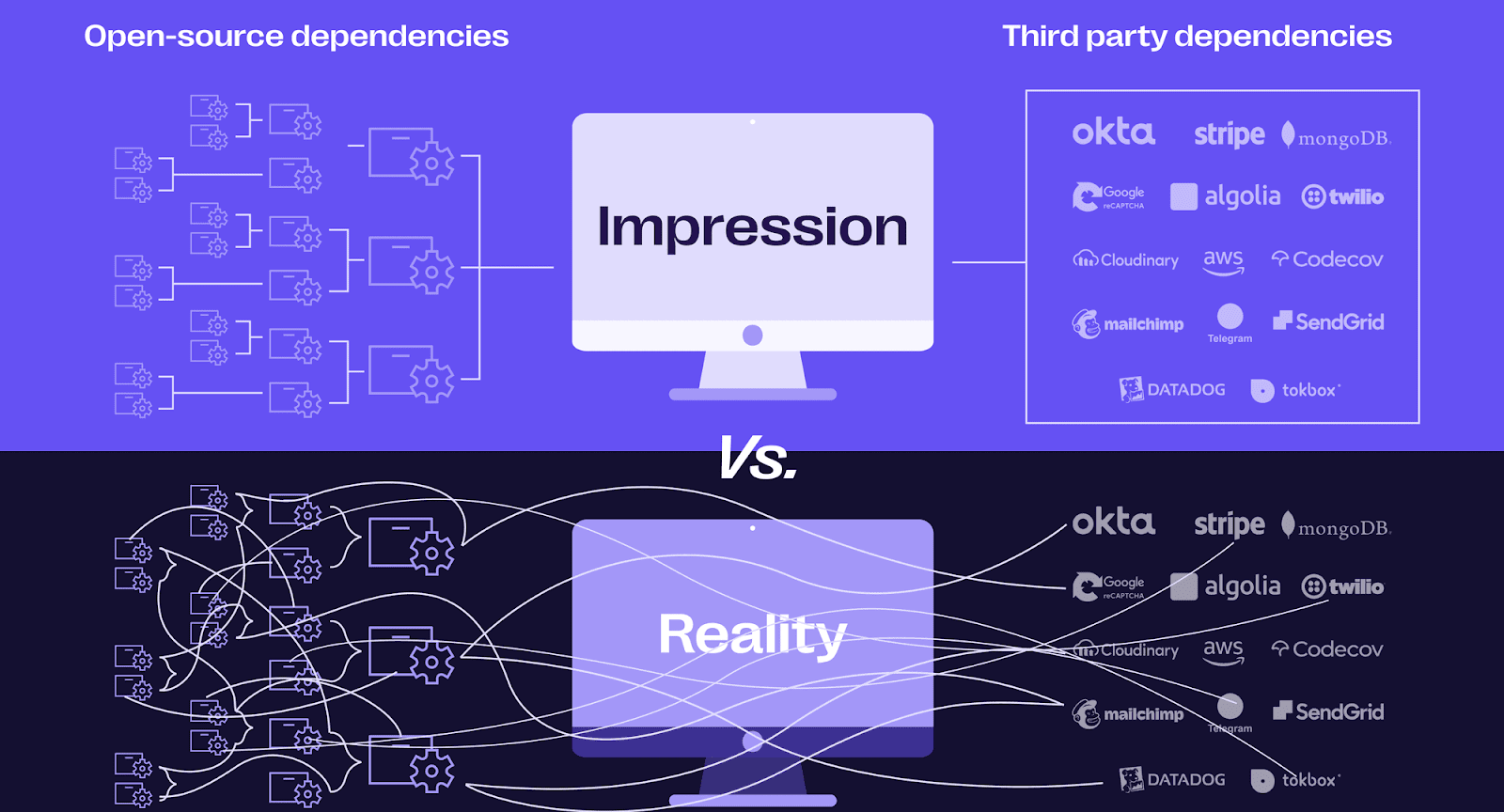
With this reality, understanding the composition of your open-source supply chain is very difficult. This is why SCA tools have become an integral part of security programs across most organizations.
So what kind of vulnerabilities can SCA testing find?
Below are three examples of vulnerabilities SCA testing finds code.
Vulnerable open-source dependency (known CVE): The following example is a vulnerability because lodash < 4.17.21 is affected by multiple prototype pollution vulnerabilities.
{
"dependencies": {
"lodash": "4.17.15"
}
}
It can lead to denial of service or arbitrary code execution depending on usage.
Insecure container base image: SCA testing can identify insecure base images by matching installed packages against known CVE databases and flagging inherited security flaws. For example, a scan of an unpatched Ubuntu 24.04 base image might detect critical vulnerabilities like CVE-2025-9900 in system libraries, which can be inherited by every container built upon it.
License compliance violation: When a dependency uses a restrictive license (e.g. GPL) that may conflict with commercial distribution. SCA detects the:
- License type
- Policy violations
- Risk level for redistribution
SCA main features
There are fundamental features and capabilities a SCA testing tool must have. The following are five of them:
- Identifies both direct and transitive open-source components: SCA tools scans entire code repositories including source code, package managers, binaries, CI/CD pipelines and containers, to detect not only explicitly declared dependencies but also those included transitively (inherited). This visibility is critical because 95% of open source components vulnerabilities stem from transitive or indirect dependencies.
- Generating a Software Bill of Materials (SBOM): You can use a SCA to create an inventory of all open source components with:
- Component names, versions, locations, suppliers/maintainers
- Associated open-source licenses.
And can go a step further to visualize dependency relationships for better analysis and identifying potential vulnerabilities/conflicts.
- Vulnerability Assessment: A SCA can compare the SBOM against known vulnerability databases such as NVD (National Vulnerability Database), CVE, GitHub Advisory, and Aikido Intel. Regularly updated databases like Aikido Intel ensure new vulnerabilities are flagged in real time to reduce your attack surface.
- OSS License Compliance: A SCA can identify licensing terms for each dependency. For example:
- GPL license: Restrictive, requires sharing modifications
- MIT license: Highly permissive open-source software license allowing nearly total freedom.
- BSL license: Published code but limits use.
A SCA like Aikido, flags license conflicts, restrictions, or violations of internal organizational policies.
- Vulnerability Remediation and Auto-Triaging: A modern SCA finds not only risks but provides remediations and auto-fixes powered by AI. For example, you can use Aikido AutoFix to fix vulnerabilities in 3rd party dependencies in your projects.
Aikido AutoFix will do this by creating pull requests that remove the vulnerability via package updates or by other means. In some cases an Aikido AutoFix can remove a whole class of vulnerabilities instead of just 1 issue.
Continuous Monitoring and Reporting: A SCA periodically rescans the codebase for emerging vulnerabilities and updates SBOMs. Doing this maintains real-time visibility into OS components, their versions, and associated risks.
Advantages of SCA
- Automation: Manually identifying open source code vulnerabilities is impossible. SCA tracks and identifies known security vulnerabilities in open source components at the same time that development teams write code that introduces them. Once integrated, SCA runs continuously with minimal developer effort.
- Reduces supply-chain attack exposure: Many high-profile security breaches originate from dependencies. SCA helps catch vulnerable or compromised components before release.
- License compliance and governance: Prevents accidental use of licenses that conflict with commercial or regulatory requirements.
Limitations of SCA
- Noise without reachability context: Same as SAST, false positives riddles SCA. Vulnerable dependencies may not actually be used or don’t have any impact. You can’t review SCA results manually, and if you choose to, you might waste extensive resources that could have been spent assessing real risks. Without reachability analysis, results can overwhelm teams.
- Coverage gaps (No zero-day): SCA relies on public databases. It cannot detect zero-day vulnerabilities or unknown flaws. For a zero-day, you need a runtime application self-protection tool like Aikido Zen. Zen can prevent OWASP Top 10 and zero day threats on autopilot. Also, block traffic at a granular level to prevent exposure.
- Fixes often depend on third parties: Remediation of open source components vulnerabilities may require waiting for upstream maintainers to release patches.
Use cases for SAST and SCA
When SAST is the right tool
Use SAST when you want to:
- Catch insecure coding patterns early
- Prevent logic flaws and SQL injections
- Enforce secure coding standards
- Shift security left into development
- Reduce costly production fixes
When SCA is the right tool
Use SCA when you need to:
- Manage open-source and dependency risk.
- Detect vulnerable packages and libraries.
- Enforce license policies.
- Reduce supply-chain security exposure.
- To create a software bill of materials (SBOM).
- Gain visibility into what you ship.
When you need both
You need both SAST and SCA when:
- You ship modern applications (which is almost always).
- You want full coverage across custom code and dependencies.
- You care about reducing real-world risk, not just checking boxes.
Combining SAST and SCA For Effective Application Security
SAST and SCA solve different problems but are both essential to a strong application security posture. And that’s exactly why they’re most effective when used together.
A layered approach combining SAST and SCA security testing tools allows teams to:
- Catch vulnerabilities earlier
- Reduce noise through better context and prioritization
- Maintain developer velocity
- Minimize production risk without slowing releases
An advanced AppSec suite like Aikido security helps you bring this unification to life. From vulnerability management to continuous compliance visibility, Aikido enables you to secure your code from the first commit to production.
Want to see Aikido in action? Sign up to scan your repos and get your first SCA and SAST results in less than 2 minutes.
FAQs
Can SAST and SCA be used together?
Yes. And they should be.
SAST and SCA solve different problems:
- SAST finds vulnerabilities in the code you write
- SCA finds vulnerabilities in the code you depend on
Using only one creates blind spots. Modern AppSec teams run both continuously to cover the full application stack without slowing development.
What types of vulnerabilities does SAST detect?
SAST detects vulnerabilities introduced during coding and logic design, including:
- Injection flaws (SQL injection, command, code injection)
- Broken authentication and access control
- Insecure cryptographic usage
- Hard-coded secrets
- Unsafe data flows
- Business logic errors
These map closely to the most common OWASP Top 10 categories.
The best SAST tools also offer AI-Powered triaging to prioritize real risks, dismiss false positives, and implement remediation
How do SAST tools analyze source code?
SAST tools analyze code without running it.
They use techniques such as:
- Pattern and rule-based analysis.
- Data-flow graphs and control-flow analysis.
- Taint tracking from inputs to dangerous sinks.
- Semantic understanding of frameworks and APIs.
This allows SAST to catch issues early while code is still being written in real time.
What are the differences between SAST, DAST, SCA, & IAST?
- SAST (Static Application Security Testing): Analyzes source code to find vulnerabilities before runtime.
- DAST (Dynamic Application Security Testing): Tests running applications from the outside to find runtime issues.
- SCA (Software Composition Analysis): Scans third-party dependencies for known vulnerabilities and license risk.
- IAST (Interactive Application Security Testing): Observes application behavior during runtime with instrumentation.
Each technique covers different risk areas. No single one is sufficient alone.


