.png)

Full Visibility & Security for Your Entire Cloud Environment
A single view of your cloud risks: misconfigs, exposures, overly permissive IAM, compliance gaps, and more - across AWS, Azure, and GCP.
- Scan container images for CVEs
- Detect misconfigs and over-permissioned roles
- Automate compliance checks
























Agentless Setup in Minutes
Secure Everything: Code → Cloud → Runtime
API-based setup. No agents. No data access. Zero slowdown.

Set Up in Minutes
Aikido requires the minimum read-only rights necessary to do it’s misconfiguration checks.

Replaces Multiple Tools
Ditch point solutions. Aikido covers code, cloud, and runtime in one tool – no juggling, no extra cost.

Automates Compliance Reporting
Each check maps to SOC 2 / ISO 27001. Auto-syncs to Vanta, Drata, and more.
CSPM Features
Context-Aware Risk Scoring
Aikido automatically adjusts vulnerability severity based on context. For example, an issue in a production environment is prioritized higher than the same issue in staging. If you link containers to their cloud environments, those container CVEs get re-scored too – so you always know which vulns truly pose a risk.

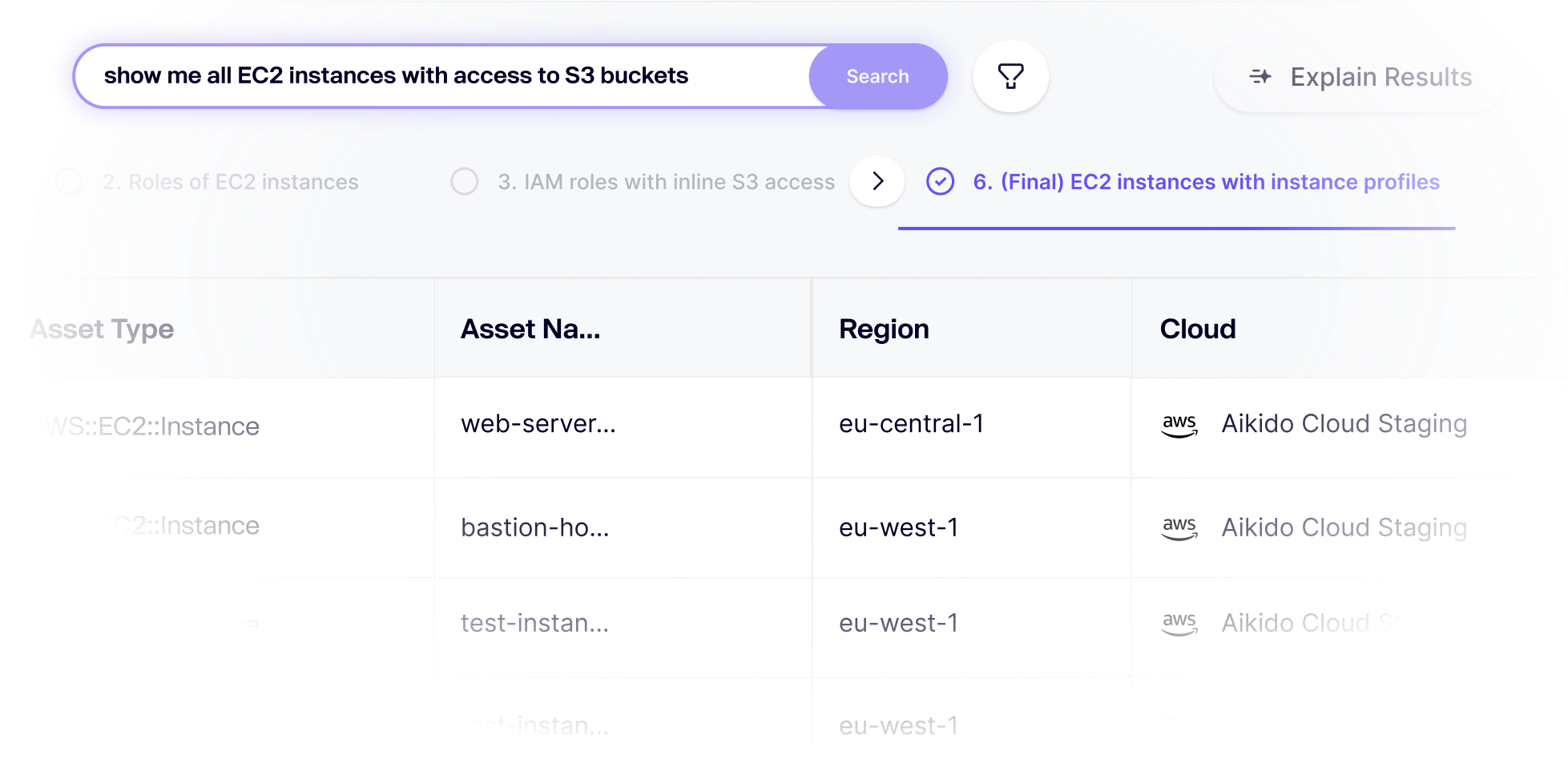
Get Instant Visibility Into Your Cloud Security
No more clicking through AWS consoles – ask questions about your cloud in plain language and get answers in seconds. Aikido’s Cloud Search lets you search your entire cloud like a database, so you can instantly find resources, misconfigs, relationships, you name it.
Alerts for Your Cloud Assets
Get notified when something important changes.
Turn any Cloud Asset Search into a real-time alert. Whether it’s a new public S3 bucket, a VM with port 22 open, or an admin role added—Aikido watches for it. The moment an asset matches your query, you’ll get a notification. No more surprises. No need to re-run checks.

Virtual Machine Scanning
Aikido scans your AWS EC2 instances for vulnerabilities. 100% coverage, from code to cloud, with or without agents.

Container Image Scanning
Aikido scans your container images for vulnerabilities and deduplicates cloud-provider findings. You get one clean report without redundant noise.

Infrastructure as Code Scanning

Outdated Runtime Detection

Cut Remediation Time with AI AutoFix
Aikido goes beyond detection—it autofixes security issues in your cloud setup. Get auto-generated PRs for:
- Vulnerabilities in container base images
- CVEs in virtual machines
- Misconfigs in Terraform, Kubernetes, and other IaC files
AI handles the complex fixes, scripts cover the rest. Just review, merge, and move on. No docs, no guesswork, no wasted time.

Full Coverage in One Platform
Replace your scattered toolstack with one platform that does it all - and shows you what matters.


FAQ
What is Cloud Security Posture Management (CSPM), and why do I need it to secure my cloud environment?
CSPM continuously audits your cloud configurations to identify misconfigurations or risky settings in AWS, Azure, GCP, and other cloud platforms. Even small errors - like a public S3 bucket - can expose sensitive data. Aikido automates this process, flagging dangerous settings before attackers exploit them. It helps you stay secure without manually reviewing hundreds of cloud settings.
How does Aikido's CSPM identify misconfigurations or security risks in my cloud setup?
Aikido connects via read-only API to your cloud accounts and scans for risky configurations. It checks things like storage access, IAM roles, and firewall rules against best practices. Misconfigured or overly permissive settings are flagged for review. No agents are required - it works entirely from metadata and config analysis.
What are some examples of cloud misconfigurations that Aikido's CSPM would catch (like an open S3 bucket)?
Examples include public S3 buckets, unencrypted databases, open SSH ports, or IAM policies granting admin to everyone. It also flags resources deployed outside allowed regions or with missing tags. Anything that could expose services or data is surfaced for review.
Does Aikido's CSPM require installing agents on my cloud resources, or is it an agentless solution?
Aikido is fully agentless. It uses your cloud provider's APIs to read configuration data - no installs, no performance impact. You simply grant it read-only access, and it continuously monitors your setup from the outside.
How do I connect Aikido to my AWS/Azure/GCP accounts, and is it safe to grant access?
You connect by creating read-only roles or credentials in AWS, Azure, or GCP. Aikido only requests minimal permissions to read configurations - it cannot change settings or access data. It's like giving a security auditor read-only access. You can revoke access anytime.
Will Aikido's CSPM flood me with alerts, or does it prioritize and filter the findings for relevance?
Aikido prioritizes issues based on risk and context. High-impact misconfigs in production rank higher than minor ones in dev. You won't get overwhelmed with noise - just a focused list of meaningful risks that need attention.
Can Aikido's CSPM auto-remediate issues (for example, close a public S3 bucket), or does it just report them?
Aikido offers guided remediations, auto-generated fixes (e.g. Terraform), and one-click PRs for many issues. It won't change infrastructure automatically, but it helps you resolve problems quickly - with safe, developer-friendly fixes.
How does Aikido's CSPM compare to cloud security platforms like Wiz or Orca Security?
Unlike Wiz or Orca, Aikido offers full-stack security - from code to cloud - in one platform. You get fewer duplicate alerts, better context linking (like vulnerabilities tied to exposed resources), and developer-first features like auto-fixes. It's lighter, faster, and built to support DevSecOps teams.
Which cloud providers and services does Aikidos CSPM support (AWS, Azure, GCP, etc.)?
Aikido supports AWS, Azure, GCP, and select others like DigitalOcean. It covers services such as EC2, S3, RDS, IAM, Kubernetes (EKS, AKS, GKE), and more. If it's a widely used cloud resource, Aikido likely scans it.
Is Aikido's CSPM part of a broader CNAPP solution that covers end-to-end code-to-cloud security?
Yes. Aikido's CSPM is part of a CNAPP that includes code scanning (SAST, SCA), IaC scanning, container security, secrets detection, and more. All tools work together to give you full visibility from development to production, with unified reporting and alerts.
Can I define custom rules for my cloud environments?
Yes. You can read more about custom CSPM rules here.
Get secure now
Secure your code, cloud, and runtime in one central system.
Find and fix vulnerabilities fast automatically.







