Traditional pentesting is like searching for a needle in a haystack with a magnifying glass. You'll find it eventually, but it takes forever and you might miss other needles nearby. AI pentesting tools automate and scale that search.
AI pentesting tools can analyze patterns, predict attack vectors, and even simulate complex attack chains that would take human testers days to explore. AI pentesting is also far more sophisticated than what has been known as automated pentesting, which only provides surface-level insights.
According to IBM’s Cost of a Data Breach Report, organizations leveraging AI and automation in security reduced average breach costs and incident response times significantly. Meanwhile, Aikido's 2026 State of AI in Security & Development report shows that 97% of organizations are considering adopting AI in penetration testing, and 9 out of 10 believe AI would eventually take over the penetration testing field.
In this guide, we break down the top AI pentesting tools being used by engineering teams today. We’ll explore the leading tools in the space, then walk through best practices for integrating them into your workflows.
TL;DR
Among all the AI pentesting tools reviewed, Aikido Security stands out as the most complete solution. Its combination of multi-region hosting (EU & US) for data sovereignty, trusted customer base of over 50,000 organizations, plug-and-play setup, and affordable pricing, make it ideal for both startups and enterprises.
Aikido Security’s Attack module uses agentic AI to simulate real attacker workflows across application code, APIs, cloud infrastructure, containers, and runtime, without demanding full source-code access. This allows teams to save the time and cost of using human pentesters.
Aikido Security Attack is available in three fixed tiers: Feature, Discovery, and Exhaustive, with the Exhaustive Scan providing the most thorough coverage.

How Aikido Security Compares to Top AI Pentesting Tools
What are AI Pentesting Tools?
AI pentesting tools use artificial intelligence to automate the key parts of penetration tests; reconnaissance, vulnerability discovery, exploit simulation, and risk prioritization, reducing pentests from days to hours.
Unlike traditional once-off audits, AI pentesting tools can run on-demand or continuously. They can automatically map out your attack surface (domains, IPs, cloud assets, APIs), then launch a barrage of safe attacks: SQL injection attempts, weak password exploits, privilege escalation in networks, you name it.
The goal: Identify holes before real attackers do – and do it faster, more frequently, and at scale.
But not every AI pentesting tool works the same way. They can be grouped into two models:
- Out-of-the-loop: Pentesting tools in this category are fully autonomous. They offer everything a human pentester can but in a more efficient and effective way.
- Human-in-the-loop: Also known as co-pilots, tools in this category automate repetitive pentesting tasks and only escalate validated issues to pentesters.
What to Look for in AI Pentesting Tools
Selecting the right AI pentesting tool isn't just about features, it's about finding the solution that fits your team's workflow and security needs. Here are a few criteria you should consider when choosing one:
- Data Residency Options: Can you choose the region your tool is hosted? Look for tools that offer multi-region hosting.
- End-to-End Coverage: Does it perform end-to-end attack path analysis, or does its test stop at the codebase level?
- Deployment: How long does it take to deploy? Do you need specialists to configure it?
- Compliance Support: Does it map tests to compliance standards like the OWASP TOP 10?
- Risk Prioritization: Can it apply context when analyzing risks? How frequent are its false positives? Platforms like Aikido Security filter out over 85% of false positives.
- Product Maturity: How many organizations use the tool? What do they have to say about it?
- Integration: Does it fit into your current workflow? For example, CI/CD pipeline security is crucial for rapid deployments.
- Pricing: Can you predict how much it will cost you in the next 1 year?
- User Experience: Is it intuitive for both devs and security professionals? Look for tools that are built with a dev-first mindset.
Top 6 AI Pentesting Tools
1. Aikido Security
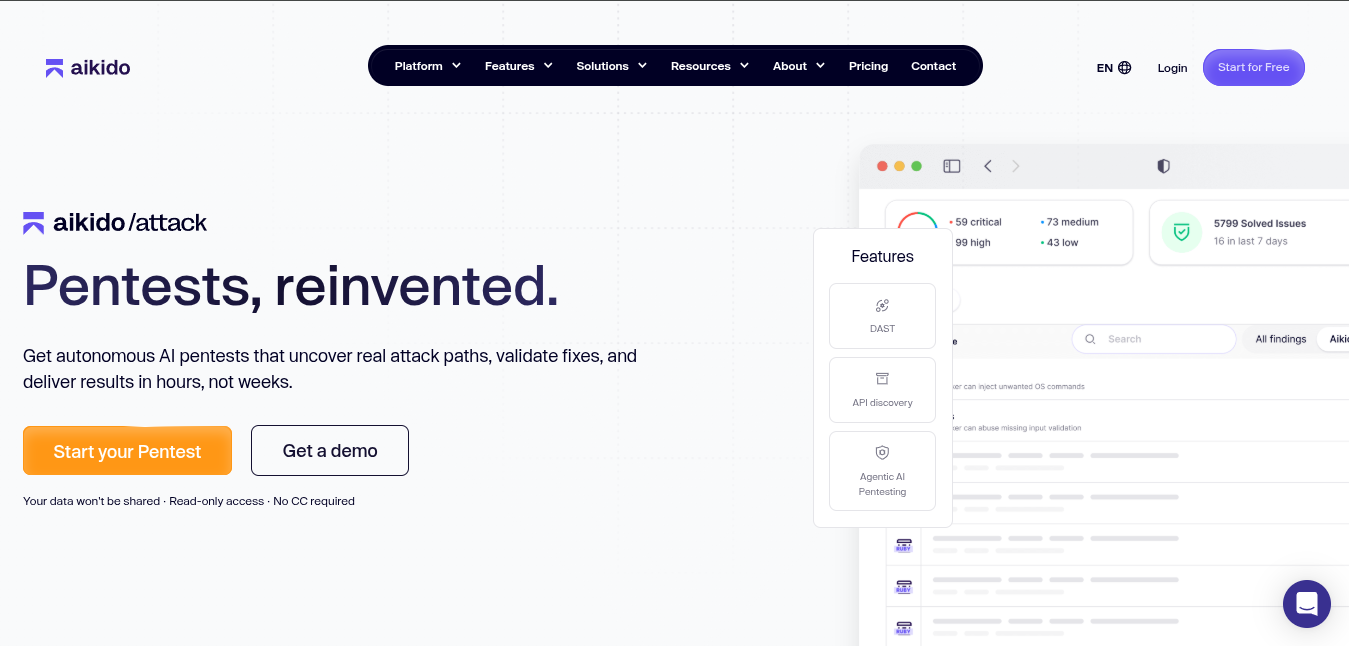
Aikido Security is an AI pentesting tool that stands out with clear differentiation from the other AI penetration testing tools in this list. Coming out on top in comparisons with manual pentesters, automated pentest solutions and other AI pentesting alternatives, Aikido’s breadth of offensive testing uses agentic AI and reactive exploitation simulations that go beyond traditional passive analysis.
Aikido Security’s Attack module runs attacker-style simulations across code, containers and cloud, so you not only discover exploitable vulnerabilities but also see how they can be chained into real attack paths rather than remaining isolated findings.
By simulating attackers techniques, Aikido Security shows you which vulnerabilities can truly be exploited. No noise, no endless lists - just the exploitable routes that matter most.
Now with all these findings what next?
Aikido Security gives developers everything they need to fix issues quickly:
- Clear explanations,
- Suggested fixes in their IDE or PRs, and
- AI-powered Autofix.
It also turns every simulation into audit-ready reports that map directly to standards like SOC2 and ISO27001, and you can then use a trusted advisor and partner to Aikido to rubber stamp the certification at a much lower cost. With all of this, you can start and finish full blown human-level penetration tests in hours, not weeks.
Human-level pentesting means the full replacement of humans.
Key Features:
- Product maturity: Aikido Security has established itself as a mainstay in the cybersecurity market, with 50,000+ customers already across their well-established base of code, cloud and runtime security.
- End-to-end attack path analysis: Aikido Security simulates attacker tactics to validate exploitability, prioritize real attack paths, and produce reproducible exploit proofs.
- Noise reduction: Aikido auto-triages results to cut out the noise. If an issue isn’t exploitable or reachable, it’s silenced automatically. You get real signals, not just alerts.
- Seamless integration: Integrates deeply with GitHub, GitLab, Bitbucket and much more.
- Developer-friendly UX: Clear, actionable dashboards your team will actually use. It can be fully deployed in under an hour.
- Supports OWASP Top 10: Aikido Security maps to OWASP Top 10 and compliance standards so security teams can trust what’s covered.
- Fast Deployment: Aikido Security scanning and Zen firewall can be deployed in less than an hour.
- Custom Region Hosting: Aikido Security is hosted in your region of choice (EU or US). This is one of many reasons European companies opt for Aikido as their cybersecurity partner.
Pros:
- Developer-focused approach with numerous IDE integrations and mitigation guidance.
- Customizable security policies and flexible rule tuning for any kind of needs.
- Centralized reporting and compliance templates (PCI, SOC2, ISO 27001).
- Mobile and binary scanning support (APK/IPA, hybrid apps).
- Predictable pricing
Pentesting Model:
Fully autonomous
Hosting/ Data Residency:
Aikido Security supports hosting in the US and EU
Testing Approach:
Using specialized AI agents, Aikido Security goes beyond periodic manual pentests by combining asset discovery, static and dependency analysis, reachability analysis, and exploit simulations to map end-to-end attack paths and surface real vulnerabilities.
Pricing:
Plans start from $100 for a feature scan, $500 for a release scan, and more for a regular scan.
Gartner Rating: 4.9/5.0
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra and SourceForge.
Why It Excels:
Aikido Security's Attack module doesn't just find vulnerabilities, it understands context. The platform analyzes your entire security posture, identifying which vulnerabilities pose actual risks to your specific environment. This contextual intelligence eliminates the false positive nightmare that plagues other tools.
The platform's strength lies in its holistic approach. Instead of juggling multiple point solutions, teams get comprehensive coverage through a single interface. The AI learns from your codebase patterns, improving accuracy over time while maintaining consistently low false positive rates.
Get an AI pentest done today, or schedule a scoping call here.
2. RunSybil
RunSybil uses an autonomous orchestrator AI agent named “Sybil” to control specialized AI agents, each tailored to a particular pentest phase. Its aim is to mimic hacker intuition and perform reconnaissance, exploit simulation, and vulnerability chaining. It executes all these phases without any human intervention.
Key Features:
- Orchestration Agent: Uses an orchestrator AI agent to manage multiple specialized AI agents in parallel.
- Report Generation: Report agents generate detailed findings on exploits and reproducibility in real-time.
- Continuous Coverage: Performs continuous automated pentests.
- Attack Replay: Enables team replay identified attack paths.
- CI/CD Integration: Supports common CI/CD platforms.
Pros:
- Simulates red-team behaviour
- Continuous automated testing
- Users can replay attack paths
Cons:
- False positives
- Low product maturity (still in early-access)
- May miss deep business-logic
- No human-verification to spot hallucinations
- Users have raised concerns on where scan data is stored/processed
Pentesting Model:
Out-of-the-loop
Hosting/ Data Residency:
Not publicly available
Testing Approach:
RunSybil’s testing approach involves coordinating fully autonomous AI-agents to map apps, probe inputs, and attempt chained exploits
Pricing:
Custom pricing
Gartner Rating:
N/A (early-access)
RunSybil Reviews:
No independent user generated review.
3. Cobalt.io
Cobalt is a pentesting-as-a-service (PTaaS) platform that connects companies seeking pentesters, on-demand access to its community of security experts "Cobalt Core." Automated tools are used to map a customer's attack surface, and then a specialized pentesting team is assigned to them.
Key Features:
- Real-time Collaboration: Provides real-time communication between internal teams and pentesters.
- Pentesting-as-a-service(PTaaS): Connects companies to experienced pentesters.
- Compliance Support: Provides support for compliance frameworks.
Pros:
- Access to experienced pentesters
- Data residency options
- Real-time communication
Cons:
- Pricing can become expensive
- Workflow friction may exist when onboarding pentesters
- Customers must define clear objectives
- Pentest quality varies based on the pentesters
- Not ideal for long-term, continuous pentests
Pentesting Model:
Human-in-the-loop
Hosting/ Data Residency:
Cobalt supports hosting in the US and EU
Testing Approach:
Cobalt’s testing approach uses a "human-led, AI-powered" approach to run its Pentest-as-a-Service (PTaaS) model that pairs vetted human pentesters with companies.
Pricing:
Custom Pricing
Gartner Rating: 4.5/5.0
Cobalt Reviews:


4. XBOW
XBOW is a fully autonomous pentesting platform. It uses multiple AI agents to discover, validate and exploit web-application vulnerabilities, with no human intervention.
Key Features:
- AI agents: Orchestrates multiple AI agents to exploit web application vulnerabilities.
- Compliance integrations: One-click pen test purchase and review inside Vanta’s UI.
- PoC Validation: Automatically validates vulnerabilities by running PoC exploits.
Pros:
- Automated PoC validation
- Autonomous discovery
- Compliance integration
Cons:
- Its “per repo” scaling is expensive
- Hallucination risk
- Hosted only in the US (unlike Aikido Security which supports hosting in the EU and US)
- Limited support beyond web applications (mobile, cloud)
- High initial setup cost
- Primarily enterprise focused
- May struggle with uncommon/complex applications and environments
Pentesting Category:
Out-of-the-loop
Hosting/ Data Residency:
XBOW supports hosting only in the US
Testing Approach:
XBOW’s testing approach uses an autonomous, multi-agent based AI approach to discover, exploit and validate vulnerabilities
Pricing:
Custom Pricing
Gartner Rating:
No Gartner review.
XBOW Reviews:

5. Astra Security

Astra Security is a Pentest-as-a-Service (PTaaS) platform that uses a hybrid approach of cloud-based vulnerability assessments and manual penetration testing to identify flaws in web applications, cloud environments, and networks.
Key Features:
- Web Application Firewall (WAF): Actively filters incoming traffic in real-time for malicious attacks and requests.
- Blacklist Monitoring: Monitors search engine blacklists and informs users if their website has been flagged.
Pros:
- Remediation guidance
- Compliance support
- Comprehensive WAF
Cons:
- lack of real-time visibility into the status of ongoing audits
- Enterprise focused
- Steep learning curve
- Frequent false positives in initial scans
- Steep pricing
- Certain functions need customer support help
- Communication delay outside India's time-zone
Pricing:
- Pentest: $5,999/year (for 1 target)
- Pentest plus: $9,999/year (for 2 targets)
- Enterprise: Custom pricing
Pentesting Category:
Human-in-the-loop
Hosting/ Data Residency:
Astra Security supports hosting in the US and EU
Testing Approach:
Astra Security uses a hybrid testing approach that combines its automated vulnerability scanner with manual expert penetration testing for continuous discovery, reporting, and remediation.
Gartner Rating: 4.5/5.0
Astra Security Reviews:


6. Terra Security

Terra Security is an Agentic-AI PTaaS platform. It combines autonomous AI agents with expert pentesters to continuously perform web-app penetration testing.
Key Features:
- Business-context Aware Attacks: Prioritizes risks by business context.
- AI Orchestration: Orchestrates multiple agents to map and exploit web application vulnerabilities.
- Human Validation: Provides security experts to verify findings from automated AI scanners.
Pros:
- Context-Aware Testing
- Continuous Coverage
Cons:
- Limited scope beyond web applications
- Enterprise focused
- Automated scanners may struggle with deep business-logic
- Steep pricing
Pentesting Category:
Human-in-the-loop
Hosting/ Data Residency:
Terra Security supports hosting in the US and Israel
Testing Approach:
Terra Security’s testing approach involves using autonomous agentic AI’s with human-in-the-loop validation to run continuous, context-aware web-application penetration testing.
Pricing:
Custom pricing
Gartner Rating:
No Gartner review.
Terra Security Reviews:
No independent user generated review.
Comparing the Best 6 AI Pentesting Tools
To help you compare the capabilities of the tools above, the table below summarizes each tool's strengths and limitations along with their ideal use case.
Best Practices When Integrating AI Pentesting Tools
Start with Risk Assessment
Before implementing any AI pentesting tool, understand your current security posture and primary risk areas. This context helps you configure your tools to focus on what matters most to your organization.
Integrate Gradually
Don't replace your entire security testing workflow overnight. Start with one area,perhaps dependency scanning or static analysis and expand coverage as your team becomes comfortable with the AI-powered approach.
Monitor and Tune
AI tools improve with feedback and configuration. Regularly review findings, mark false positives, and adjust sensitivity settings to optimize the signal-to-noise ratio for your specific environment.
Combine Human Expertise with AI Insights
The most effective security testing combines AI efficiency with human judgment. Use AI to identify and prioritize potential issues, then apply human expertise to validate findings and determine remediation priorities.
Conclusion
As more organizations adopt AI-driven pentesting, the need for flexible tools that deliver compliance, speed, and real-world attack simulation is more important now than ever. Aikido Security leads this shift by combining autonomous pentesting, compliant hosting, and a frictionless developer experience, allowing teams to focus on what truly matters.
Aikido Security offers the best-in-class AI pentests for start-ups and enterprises. It comes out on top in technical comparisons and POC head-to-heads with pricing that stays predictable and continuous without forced credit bundles.
Want less noise and more real protection? Start your free trial or book a demo with Aikido Security today.
FAQ
How do AI pentesting tools identify security vulnerabilities?
AI pentesting tools work by simulating hacker-like behavior using machine learning and automation. They scan code, infrastructure and live environments to detect misconfigurations, insecure APIs, exposed secrets and exploitable flaws. Some tools operate fully autonomously like Aikido Security.
Which AI pentesting tools are the most effective for automated penetration testing?
The best tools are those that combine continuous automated scanning with validated exploit testing and clear remediation guidance. Platforms like RunSybil, Cobalt, and Aikido Security stand out by providing exploit simulation, actionable reporting, and developer-focused workflows. Aikido Security in particular goes beyond simple vulnerability detection by correlating findings from code to cloud and using AI-driven attack paths to show how real-world exploits could unfold.
What types of security threats can AI pentesting tools detect?
AI pentesting tools can detect a wide range of threats, including SQL injection, XSS, authentication bypasses, insecure APIs, misconfigured cloud resources and much more. Advanced platforms like Aikido Security can also chain smaller vulnerabilities to reveal full attack paths and exploit business logic flaws that static scanners alone can't identify.
What are the privacy and ethical considerations when using AI for pentesting?
Using AI for pentesting requires strong ethical guidelines and respect for user privacy. AI tools must only be used on assets where you have explicit permission, and sensitive data should not be stored or shared unnecessarily. Vendors like Aikido Security ensure that findings, proof-of-concepts and logs remain encrypted and only accessible to authorized teams. They are also compliant with standards such as GDPR and ISO 27001 to reduce legal and ethical risks.
What are the common challenges faced when using AI in penetration testing?
AI-driven pentesting isn’t without limitations. Automated tools sometimes miss complex business logic vulnerabilities or produce false positives if not properly trained on real-world environments. They may also struggle in highly regulated industries with strict access controls. This is why Aikido Security adopts a autonomous approach reduce noise and handle repetitive exploitation task.
You Might Also Like:




