Over a hundred zero-day vulnerabilities, no public announcements, no researchers taking credit; just technical proofs, exploit chains and stack traces showing they were real. This was what happened to Microsoft Access and 365 in January 2025.
For years, pentesting was a once-a-year event. You’d hire a firm, wait weeks for results, then scramble to fix findings that attackers have already exploited.
That doesn’t work anymore.
Modern teams ship code daily, and attackers move even faster. That’s why a new generation of pentesting tools has emerged that use AI to go beyond what manual pentesting and automated pentesting can offer.
AI pentesting or agentic AI penetration testing uses AI agents to interpret the current context with previous pentest attempts and then adjust its next actions just like a human pentester would.
The agents continually scan for known vulnerabilities, misconfigurations, and common weaknesses. Think of it as having a tireless security guard that checks your code, websites, APIs, and infrastructure 24/7.
In fact, 97% of the CISOs, AppSec engineers and developers surveyed in Aikido's 2026 State of AI in Security & Development report said that they would consider AI penetration testing and 9 in 10 said they believed AI would eventually take over the penetration testing field.
This is partly because AI pentesting platforms can cut testing costs by more than 50% compared to traditional automated pentesting or consulting. Instead of paying a firm $10k+ for a one-time test, you could be running year-round context aware checks for a fraction of the price.
With AI penetration testing on your mind, choosing the right penetration testing tool becomes easier. The most effective solutions continously cut through the noise, offering real, actionable results, helping you keep pace with your security and compliance requirements, such as; SOC 2 (Type I and II), NIST 800-53, OWASP Top 10 and ISO 27001.
TL;DR
Aikido Security’s Attack earns the #1 spot for modern teams thanks to its comprehensive AI-powered pentesting, multi-region hosting (EU and US) for data sovereignty, plug-and-play experience, and predictable pricing.
Aikido's AI penetration testing solution has already fared better in side-by-side comparisons with human pentesters. It finds vulnerabilities more efficiently and can detect issues that may evade manual methods.
Backed by a mature technology ecosystem and industry-wide recognition, Aikido Security Attack solves the hard trade-offs other tools force on teams such as; mandatory full-repo access, lack of regional compliance options, and unpredictable pricing, delivering a solution that scales from startups to enterprises.
Its agentic AI performs human-level exploitation workflows across application code, cloud, containers, and runtime environments, all without requiring source-code-level repository access. This saves teams significantly in resources compared to using manual pentest or automated pentest methods.

What are Pentesting Tools?
Pentesting tools are solutions used to identify, test, and remediate vulnerabilities and weaknesses in an organization's security controls. They automate certain tasks, improve testing efficiency, and uncover issues that are difficult to discover with manual analysis techniques alone.
Up until now there have only been two types of pentesting tools: the ones that assist human only testing, where pentesters manually use them to attempt to hack your systems, and automated pentesting. Automated pentesting can be useful, but ultimately is not a pentest.
AI pentesting or agentic AI penetration testing tools is a real alternative to manual penetration tests as it can interpret the current context with previous attempts and then adjust its next actions just like a human pentester would.
Instead of a once-off audit, AI pentesting tools can run on-demand or continuously to scan for vulnerabilities, simulate exploits and assess security posture. They can automatically map out your attack surface (domains, IPs, cloud assets, etc.), then launch a barrage of safe attacks: SQL injection attempts, weak password exploits, privilege escalation in networks, you name it.
The goal is to identify holes before real attackers do – and do it faster and more frequently than a human-only approach.
What to Look for in Modern Pentesting Tools
The days of clunky, standalone security scanners are over. With the adoption of CI/CD pipelines and cloud-native architecture, pentesting tools must be capable of integrating with complex development workflows; from the way they scan for vulnerabilities to how fast they find them.. It's not just about finding vulnerabilities, it’s about resolving them automatically.
Here are the key criteria you should consider when evaluating modern pentesting tools:
- Product maturity: How many organizations use the tool? What do they have to say about it?
- Integration: Does it fit into your current DevOps workflow? For example, CI/CD pipeline security is crucial for rapid deployments.
- AI Penetration Testing: Does it use AI to perform continuous, context aware pentests that are more efficient andgo deeper than humans?
- Signal-to-Noise Ratio: Can it filter out false positives? Alert fatigue threatens both productivity and security. Platforms like Aikido Security filter out over 90% of false positives.
- Comprehensive Coverage: Does its coverage stop at the code level or, includes dependencies, deployment pipelines and cloud infrastructure?.
- Usability: Is it intuitive for both devs and security professionals? Pentesting is delicate; you don’t need an overly complex setup to add to it.
- Pricing: Can you predict how much it will cost you in the next 1 year? Or its all vibes.
Top 10 Pentesting Tools for Modern Teams
1. Aikido Security
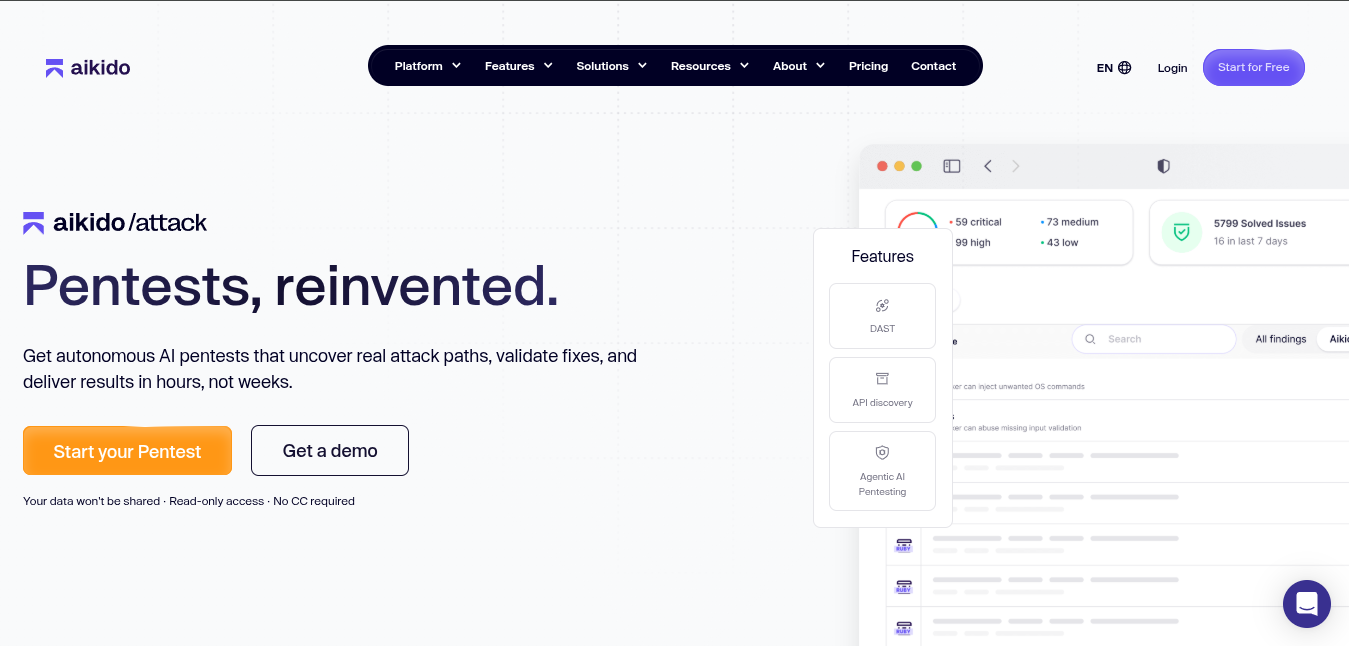
Aikido Security’s Attack is an AI pentesting tool that stands out from the other penetration testing tools in this list. It runs attacker-style simulations across code, containers and cloud, so you not only discover exploitable vulnerabilities but also see how they can be chained into real attack paths rather than remaining isolated findings.
By simulating attackers techniques, Aikido Security shows you which vulnerabilities can truly be exploited.
Defenders see the same picture of how attacks unfold. Red-team style simulations test resilience, while blue teams get the evidence and visibility to respond with confidence.
Aikido already performs better than manual pentests in side-by-side comparisons.
Aikido Security provides:
- On-demand testing
- AI-powered whitebox, graybox and blackbox pentests
- False-positive and hallucination prevention
- A full, audit-grade (SOC2, ISO27001, etc) dossier equivalent to amanual pentest, with evidence, repro steps, and remediation guidance for certification.
Aikido Security Attack is available in three fixed plans: Feature, Discovery, and Exhaustive, with the Exhaustive Scan providing the most thorough coverage.
Try Aikido's pentest today.
Key Features:
- Better than manual pentests: Aikido simulates attacker tactics to validate exploitability, prioritize real attack paths, and produce reproducible exploit proofs,. in a cheaper, more effective way than manual pentests.
- Broad coverage: From cloud configuration scanning to advanced secrets detection.
- Noise reduction: Aikido auto-triages results to cut out the noise. If an issue isn’t exploitable or reachable, it’s silenced automatically. You get real signals, not just alerts.
- Developer-friendly UI: Clear, actionable dashboards your team will actually use.
- Supports OWASP Top 10: Aikido Security maps to OWASP Top10 and compliance standards so security teams can trust what’s covered.
- Fast Deployment: Aikido Security scanning and Zen firewall can be deployed in less than an hour.
- Custom Region Hosting: Aikido Security is hosted in your region of choice (EU or US). This is one of many reasons European companies opt for Aikido as their cybersecurity partner.
- Comprehensive compliance mapping: Supports major frameworks like SOC 2, ISO 27001, PCI DSS,GDPR, and much more.
- Product maturity: Aikido Security has established itself as a mainstay in the cybersecurity market, with 50,000+ customers already across their well-established base of code, cloud and runtime security.
Pros:
- Agentic Pentesting (Human-Level Pentesting, Automated by AI) that delivers results in hours.
- Developer-focused approach with numerous IDE integrations and mitigation guidance.
- Customizable security policies and flexible rule tuning for any kind of needs.
- Centralized reporting and compliance templates (PCI, SOC2, ISO 27001).
- Mobile and binary scanning support (APK/IPA, hybrid apps).
- Predictable pricing
AI-Powered Pentesting:
Yes, Aikido Security performs AI-powered autonomous pentesting.
Testing Approach:
Using specialized AI agents, Aikido Security goes beyond periodic manual pentests, so you don't require humans.
Pricing:
Prices begin at $100 for a feature scan, $500 for a release scan and $6,000 for a regular scan.
Gartner Rating: 4.9/5.0
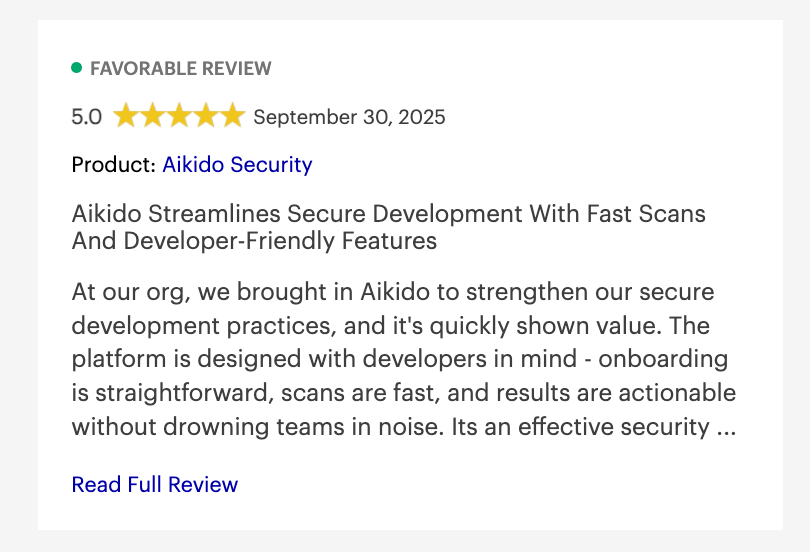
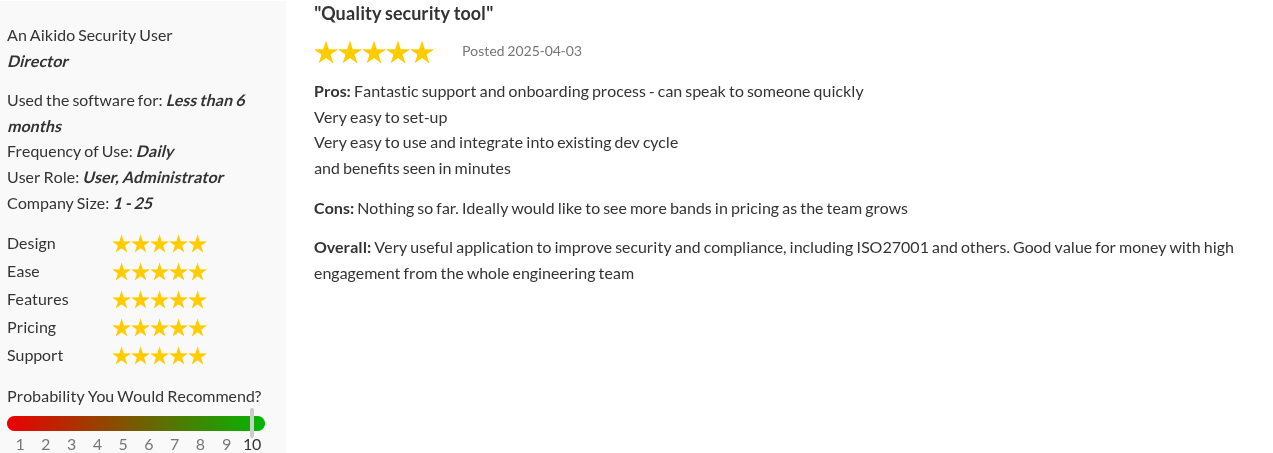
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra and SourceForge.
Exploring code quality tools as well? Check out our guide on The Best Code Quality Tools for 2026 .
2. Burp Suite

Burp Suite is a toolkit for web application penetration testing. It acts as a proxy, by letting testers inspect, modify, and replay web requests, to discover critical flaws like SQL injection and XSS.
Key Features:
- Interception Proxy: Allows testers capture and modify HTTP(s) requests.
- Supports customized brute-force and fuzzing attacks.
- OAST Support: Detects out-of-band issues (SSRF, blind XXE/SQLi) via callback tracking.
- Modular: Highly extensible through plugins.
Pros:
- Granular manual control
- Large community support
- Deep web-application focus
Cons:
- No reachability analysis
- Steep learning curve
- High false positives
- Primarily manual
- Performs periodic (point-in-time) scans
- Users have reported CI/CD pipelines slowing down during scans
AI-Powered:
Yes with Burp AI, but it still relies heavily on human operators
Testing Approach:
Burp Suite’s testing approach is manual and researcher-guided. Using a hybrid testing approach it combines automated tools with hands-on manual testing.
Pricing:
- Burp Suite Community Edition: Free
- Burp Suite Professional: $475 per user/year
- Burp Suite Enterprise Edition: Custom pricing
Gartner Rating: 4.7/5.0
Burp Suite Reviews:
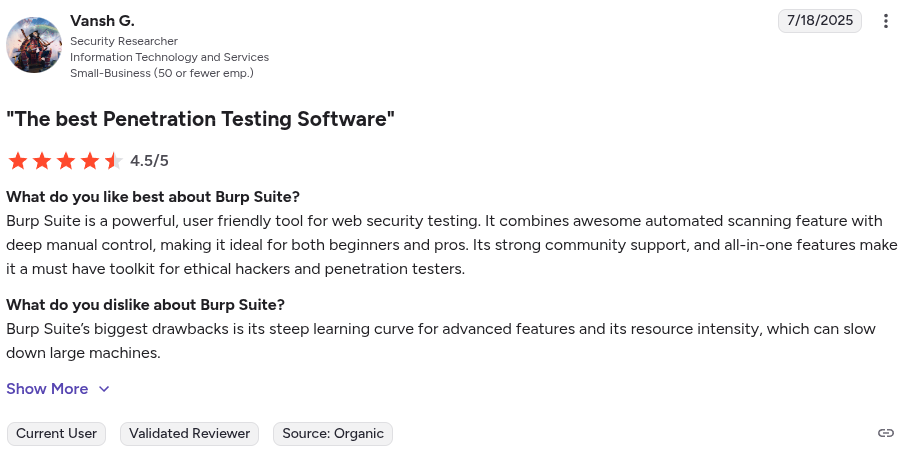

3. Metasploit Framework

Metasploit Framework is an open-source pentesting tool, widely used for exploitation, vulnerability validation, and post-exploitation.It’s known primarily for its comprehensive database of exploits..
Key Features:
- Scripting support: Uses the “msfconsole” CLI and Ruby for advanced automation.
- Database integration: Tracks hosts, services, sessions, and captured data.
- Custom modules: Supports custom modules and community contributions.
- Cross-platform support: Windows, Linux, macOS and network devices.
Pros:
- Open-source
- Great community support
- Large exploit library
Cons:
- Only detects and exploits vulnerabilities already in its database
- Steep learning curve for beginners
- May require disabling antivirus, as payloads are often flagged as malicious
- Lacks a native Graphical User Interface (GUI)
- Module quality varies and may require manual tweaking
AI-Powered:
No, Metasploit Framework does not natively integrate AI
Testing Approach:
The Metasploit Framework's testing approach is exploit-driven and operator-guided. By providing modules for the phases of a penetration test, Metasploit enables security professionals to validate, reproduce, and extend known exploit paths.
Pricing:
Free (Open-source)
Gartner Rating: 4.3/5.0
Metasploit Framework Reviews:

4. Nmap
Nmap is an open-source tool used for network security assessment and investigation.Pentesters use it to determine which services are running and where.
Key Features:
- Network reconnaissance: Discovers live hosts and running services on a network.
- Port scanning: Identifies open, closed, and filtered ports.
- Platform support: Cross-platform (Windows, Linux, macOS, and BSD).
Pros:
- Fast host and port discovery for quick network insights
- Free and open-source
- Supports custom automation through NSE scripting
- Performs basic OS detection to understand target systems
Cons:
- Primarily Discovery-focused, rather than a vulnerability scanner
- Only reports what’s running, not whether services are exploitable
- Can be noisy and trigger IDS/IPS alerts during aggressive scans
- Firewall/IDS can produce false negatives by blocking probes
- Clunky user interface
- Some advanced scans require root/administrator privileges
AI-Powered:
No, Nmap does not have any AI integration
Testing Approach:
Nmap's testing approach is reconnaissance-focused. It uses crafted packets to systematically map and gather information about a target network and its hosts.
Pricing:
Free (Open-source)
Capterra Rating: 4.8/5.0
Nmap Reviews:

Users also shared:
“Nmap has a steep learning curve and can be a bit challenging for newcomers, especially if you're not already familiar with networking concepts.” – Nmap user
5. OWASP ZAP

OWASP ZAP is a free, open-source solution for finding web application vulnerabilities.It is maintained by its open-source community .
Key Features:
- Passive and Active Scanning: ZAP’s active scanner actively attempts attacks on target web apps to find vulnerabilities, whereas the passive scanner observes traffic for issues.
- API Testing: It is capable of scanning API endpoints.
- Extensible via add-ons: You can expand ZAP’s capabilities through add-ons.
- Intercepting Proxy: Allows testers capture and modify HTTP(s) requests in real-time.
Pros:
- Passively scans web requests
- Open-source
- Large community support.
- Beginner Friendly
Cons:
- False positives
- Steep learning curve
- Scans can be resource-intensive
- Requires additional configurations for javascript-heavy web applications
- Performance may degrade during deep crawls
AI-Powered:
No, Owasp zap does not natively integrate AI.
Testing Approach:
OWASP ZAP’s testing approach uses an intercepting proxy model, combining automated, dynamic, and manual methods to find vulnerabilities in web applications.
Pricing:
Free (Open-source)
OWASP ZAP Reviews:

6. XBOW
XBOW is a fully autonomous, AI-powered pentesting platform that discovers, validates and exploits web-application vulnerabilities.
Key Features:
- CI/CD Integration: Supports common CI/CD pipelines.
- Autonomous AI agents: Runs AI agents to exploit vulnerabilities.
- PoC Validation: Automatically validates vulnerabilities by running PoC exploits.
Pros:
- Automated PoC validation
- Autonomous discovery
- CI/CD integration
- Fast scans
Cons:
- Hosted only in the US (unlike Aikido Security Attack which is in the US and EU)
- Primarily enterprise focused
- False positives / hallucination risk
- Highly dependent on training data
- May struggle with uncommon/complex applications and environments
- Can end up being very expensive in comparison to alternatives
AI-Powered:
Yes, XBOW natively integrates AI
Testing Approach:
XBOW’s testing approach uses an autonomous, multi-agent based AI approach to discover, exploit and validate vulnerabilities
Pricing:
Custom Pricing
XBOW Reviews:

7. Cobalt.io
Cobalt is a pentesting-as-a-service (PTaaS) platform that connects companies with its network of penetration testers.
Key Features:
- Pentesting-as-a-service(PTaaS): Provides a unified platform for companies to access pentesters.
- Compliance Support: Provides support for compliance frameworks.
- Real-time Collaboration: Provides real-time communication between internal teams and pentesters.
Pros:
- Vetted pentesters
- Data can be hosted in the EU and US
- Real-time communication
Cons:
- Pricing can become expensive
- Pentester experience vary
- Not ideal for long-term, continuous pentests
- Learning curve
- Clients must define detailed rules-of-engagement
AI-Powered:
Yes, but relies heavily on human pentesters
Testing Approach:
Cobalt’s testing approach uses a "human-led, AI-powered" approach to run its Pentest-as-a-Service (PTaaS) model that pairs vetted human pentesters with companies.
Pricing:
Custom Pricing
Gartner Rating: 4.5/5.0
Cobalt Reviews:


8. RunSybil
RunSybil is an AI-driven penetration-testing platform that “mimics hacker intuition” by running coordinated agentic probes to discover and chain vulnerabilities.
Key Features:
- Attack Replay: Provides features for replaying identified attack paths.
- CI/CD Integration: Supports common CI/CD tools.
- Agent Orchestration : Uses an orchestrator AI agent to manage multiple probes
Pros:
- Continuous testing
- Simulates red-team behaviour
- Users can replay attack paths
Cons:
- False positives
- Low product maturity (still in early-access)
- May miss deep business-logic
AI-Powered:
Yes, RunSybil natively integrates AI.
Testing Approach:
RunSybil’s testing approach involves coordinating fully autonomous AI-agents to map apps, probe inputs, and attempt chained exploits
Pricing:
Custom pricing
Gartner Rating: N/A (early-access)
9. Terra Security

Terra Security is an Agentic-AI PTaaS platform that uses AI agents with human-in-the-loop oversight to deliver continuous web-app penetration testing.
Key Features:
- Agentic AI orchestration: Uses dozens of agents to probe, map and exploit web application vulnerabilities.
- Human-in-the-loop validation: Provides human experts to verify findings.
- Business-context mapping: Prioritizes risks by business context.
Pros:
- Supports major cloud providers
- Context-Aware Testing
- Continuous Coverage
Cons:
- Primarily enterprise focused
- May miss very deep business-logic
- Pricing can become expensive
- Security professionals may be hesitant with its “Black box” AI methods
AI-Powered:
Yes, Terras Security natively integrates AI
Testing Approach:
Terra Security’s testing approach involves using autonomous agentic AI’s with human-in-the-loop validation to run continuous, context-aware web-application penetration testing.
Pricing:
Custom pricing
10. Astra Security

Astra Security is a cloud-based vulnerability assessment and penetration testing (VAPT) platform to identify vulnerabilities in web applications, cloud and networks.
Key Features:
- Web Application Firewall (WAF): Actively filters incoming traffic in real-time for malicious attacks and requests.
- Compliance Monitoring: Monitors and maintains compliance with regulatory bodies.
- Blacklist Monitoring: Monitors search engine blacklists and informs users if their website has been flagged.
Pros:
- Continuous coverage
- Remediation guidance
- Compliance support
- Comprehensive WAF
Cons:
- Primarily focused on web applications
- Steep pricing
- Limited Customization
- May add latency to website load times
- Learning curve
Pricing:
- Pentest: $5,999/year (for 1 target)
- Pentest plus: $9,999/year (for 2 targets)
- Enterprise: Custom pricing
AI-Powered:
Yes, Astra Security supports AI
Testing Approach:
Astra Security uses a hybrid testing approach that combines its automated vulnerability scanner with manual expert penetration testing for continuous discovery, reporting, and remediation.
Gartner Rating: 4.5/5.0
Astra Security Reviews:


Searching for more open-source options? Check out our article on The Top 13 Code Vulnerability Scanners in 2026.
Comparing Best 10 Pentesting Tools
To help you compare the capabilities of the tools above, the table below summarizes each tool's strengths and limitations along with their ideal use case.
Curious on how to integrate autonomous AI-driven pentesting into your CI/CD pipelines? Check out our articles on Continuous Pentesting in CI/CD and the Top 12 Dynamic Application Security Testing (DAST) Tools in 2026.
Choosing the Right Pentesting Tool for Your Team
Aikido Security is the leading choice for teams seeking comprehensive, low-noise penetration testing that integrates seamlessly with modern development workflows.
Its AI-powered pentesting feature goes beyond traditional tools by acting as an additional pentesting specialist that never sleeps, misses vulnerabilities, and allows your team to stay focused on what truly matters, tackling complex problems.
Want less noise and more real protection? Start your free trial or book a demo with Aikido Security today.
FAQ
Does Aikido run autonomous penetration tests end-to-end?
Yes, Aikido Security runs continuous, AI-driven autonomous pentests to discover assets, test attack surfaces, and simulate exploits across code, infrastructure, APIs and runtime with no human intervention.
How does Aikido validate that a finding is truly exploitable (produce PoCs)?
Aikido Security performs exploit simulations and dynamic checks to validate reachability and exploitability. Afterwards, it generates reproducible evidence and PoC artifacts to prove an issue is exploitable.
What types of coverage does Aikido provide?
Aikido Security covers everything from code-to-cloud; SAST, SCA (dependencies), IaC scanning, DAST/API scanning, cloud posture management, and runtime protections, and uses autonomous pentests to link findings into attack paths.
You can benefit from one suite with everything covered or you can get each best-in-class product (SAST, SCA, DAST) and expand and integrate as you wish
You Might Also Like:



