Modern application environments are complex and constantly changing. As organizations adopt microservice architectures, APIs, and multi-cloud infrastructures, maintaining consistent visibility into security risks has become difficult.
According to the IBM 2025 Cost of a Breach Report, cross-environment breaches took an average of 276 days to detect and contain, significantly longer than breaches to isolated private cloud, public cloud, or on-premises environments.
Application Security Posture Management (ASPM) tools address this challenge by unifying your AppSec ecosystem, allowing teams to continuously monitor, identify and fix vulnerabilities throughout the application lifecycle. These tools provide the visibility and control needed to protect your applications.In this guide we’ll explore the top ASPM tools teams are using today, along with side-by-side comparisons to help you determine which ASPM tools fits your team’s workflow,
TL;DR
Aikido Security stands out as the #1 ASPM solution, thanks to its developer-first design and end-to-end Application Security Posture Management platform. It gives security teams and developers a single pane of glass, from code vulnerabilities to cloud misconfigurations, with AI-driven analytics and correlation to cut through noise and surface real exploitable vulnerabilities
Aikido Security’s ASPM integrates SAST, SCA, IaC, secrets scanning, and more into a single workflow, ensuring critical issues are fixed directly within the development workflow. No more context switching.
For both start-ups and enterprises, compared with other ASPM solutions, Aikido Security comes out top in technical comparisons and POC head-to-heads.
What is Application Security Posture Management (ASPM)?
Application Security Posture Management (ASPM) involves managing application security risks. ASPM tools collect, analyze, and prioritize security issues throughout the software development lifecycle, offering a complete view of your application security landscape.
ASPM tools utilize advanced technologies like AI and machine learning to prioritize vulnerabilities by severity. Consolidating data from various security testing tools and integrating with development workflows. Helping teams identify and resolve vulnerabilities faster and more efficiently.
Why You Need an ASPM Tool
Application Security Posture Management (ASPM) tools play a crucial role in maintaining a strong security posture across the software development lifecycle. Some of its key benefits include:
- Centralized Visibility: Provides a unified view of security risks, simplifying the tracking and management of vulnerabilities.
- Contextual Prioritization: Helps teams focus on critical risks by considering business impact, likelihood of exploitation, and asset value.
- Seamless Integration: Works with existing development tools and workflows, allowing developers to address security issues without unnecessary context-switching.
- Continuous Monitoring: Offers real-time monitoring and alerts to maintain security posture throughout the application lifecycle.
- Aggregated Findings: Collect vulnerability data from multiple Application Security Testing (AST) tools, such as SAST, DAST, SCA, and IaC scanners.
- Enforce Security Policies and Compliance: Teams can define and enforce compliance security policies such as GDPR, HIPAA, SOC 2 and much more.
What to Look for in ASPM Tools
Here are the key criteria you should consider when evaluating ASPM tools:
- Risk-Based Prioritization: Does it use AI to prioritize vulnerabilities based on exploitability? Can it correlate risks across multiple scanners?
- Developer-Friendly UI: Is the UI intuitive for developers, not just security teams? Does it provide clear remediation guidance directly within developer workflows
- Inventory Monitoring: Does it automatically detect applications, APIs, and cloud assets across environments? Can it map the relationship between assets?
- Pricing: Can you predict how much it will cost you in the next 1 year? Or is it all vibes?
- Vendor Support: How responsive is the vendor’s customer support? Are there detailed documentation, community forums, or dedicated success teams available?
- Cross-Team Collaboration: Does it support role-based access control and shared dashboards? Can DevSecOps teams collaborate on findings directly from integrated tools like GitHub, GitLab, Jira and Slack?
Top 12 ASPM Tools
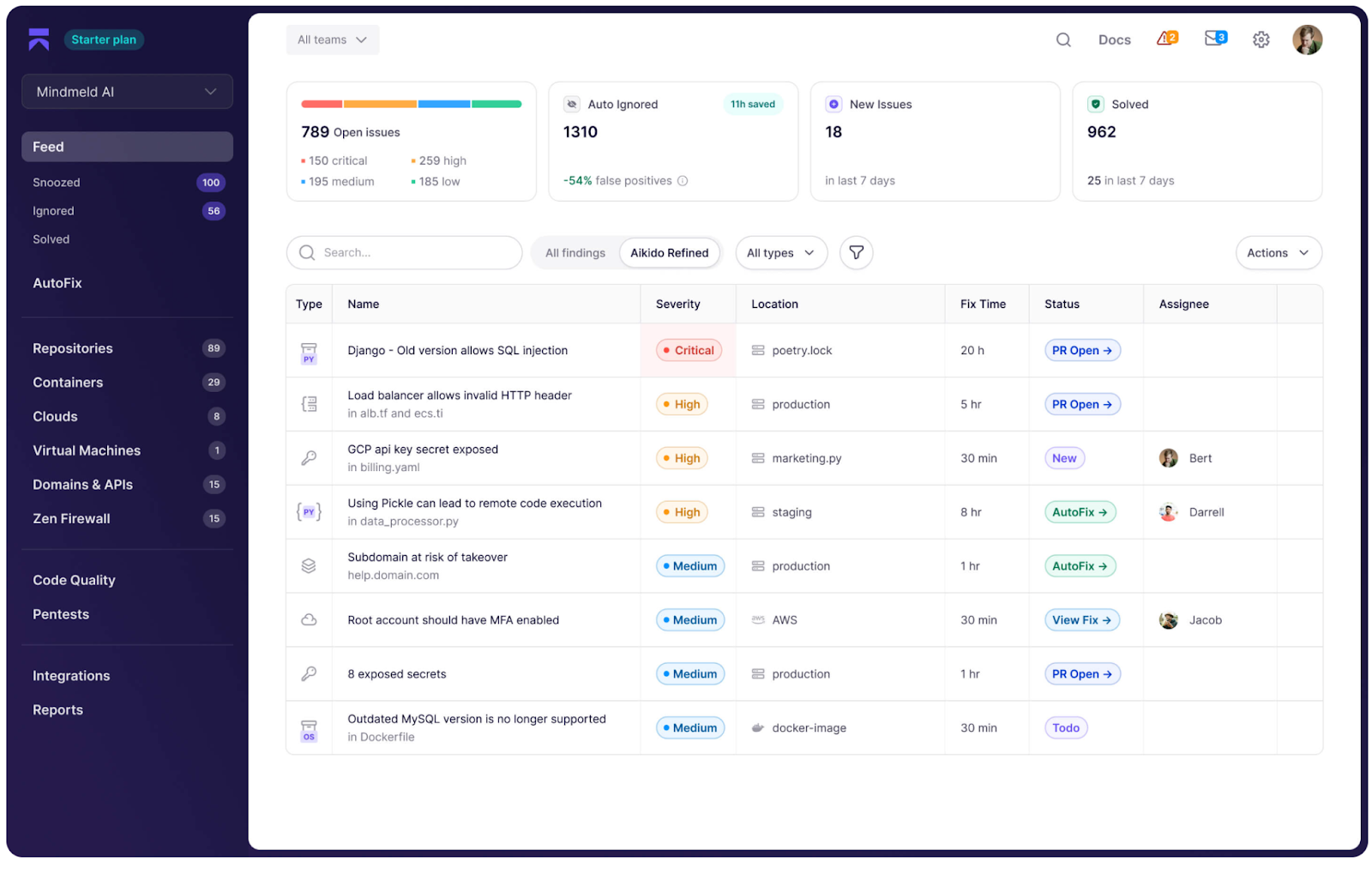
1. Aikido Security
Aikido Security is a developer-first, AI-driven Application Security Posture Management (ASPM) platform that focuses heavily on securing the entire Software Development Lifecycle (SDLC), from code to cloud. It uses AI-powered risk analytics, to automatically correlate issues across SAST, DAST, SCA, IaC, secrets scanners and CSPM .
Instead of drowning you in alerts, Aikido Security cuts through the noise by using graph-based intelligence to highlight the actual, exploitable attack paths across your entire environment, code, containers, and cloud.
Now with your entire development process covered, what’s next?
Aikido Security gives developers everything they need to fix issues quickly:
- Clear, context-based explanations of each vulnerability
- Fix suggestions right in their development workflow (IDE, PRs) and
- One-click AI-remediation.
Every scan is automatically into actionable, audit-ready compliance evidence mapped to leading frameworks such as SOC 2 and ISO 27001. You can then use a trusted advisor and partner to Aikido to rubber stamp the certification at a much lower cost.
With Aikido Security, development and security teams move from detection to resolution in minutes, securing applications with less noise, friction, and stronger confidence in their security posture.
Key Features:
- AI-driven Prioritization: Aikido Security cuts out noise by auto-triaging results. If an issue isn’t exploitable or reachable, it’s automatically silenced.
- Cross-Scanner Correlation: Integrates with the best-in-class scanners; SAST, SCA, secrets, IaC, containers, and much more, and correlates the data in a unified dashboard.
- Seamless integration: Provides seamless integration with GitHub, GitLab, Bitbucket and much more.
- Security and compliance mapping: Supports major security and compliance frameworks like GDPR, SOC 2, ISO 27001, PCI DSS, and much more.
- Developer-first Workflow: Provides instant AI powered feedback in PRs and IDEs, IDE plugins for real-time feedback, AI-powered autofix and actionable remediation workflows.
- Continuous Compliance Monitoring: Automates SOC 2, GDPR, HIPAA, and other compliance frameworks with up-to-date, exportable compliance reports. Ideal for highly regulated industries where audit readiness is essential.
- Automatic Asset Discovery: Automatically discovers and inventories all cloud services, domains, API endpoints and code repositories.
- Dynamic Asset Graph: It builds a real-time graph of your assets and their relationships.
- Code-to-cloud Coverage: Aikido Security links code, cloud, and runtime into one seamless workflow. You can start with a single module and expand (code scanning, container scanning, Iac scanning, API security, and runtime protection).
Pros:
- Best-in-class scanners
- Developer-first UI
- Predictable pricing
- Strong compliance features
- Strong vendor support
- Centralized reporting and compliance templates
- Broad language support
- Context-aware remediation guidance and risk scoring
- Advanced filtering reduces false positives, making alerts actionable.
Ideal Use Case:
- Startups looking for an easy-to-use, developer-first ASPM tool with AI-driven risk correlation, automated remediation, and intelligent noise reduction.
- Enterprises in highly regulated industries that require strong governance, detailed compliance reporting, and secure SDLC management.
Pricing:
All paid plans starting from $300/month for 10 users
- Developer (Free Forever): Free for up to 2 users. Supports 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Supports 10 repos, 25 container images, 5 domains and 3 cloud accounts.
- Pro: Supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Supports 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Custom offerings are also available for startups (30% discount) and enterprises.
Gartner Rating: 4.9/5.0
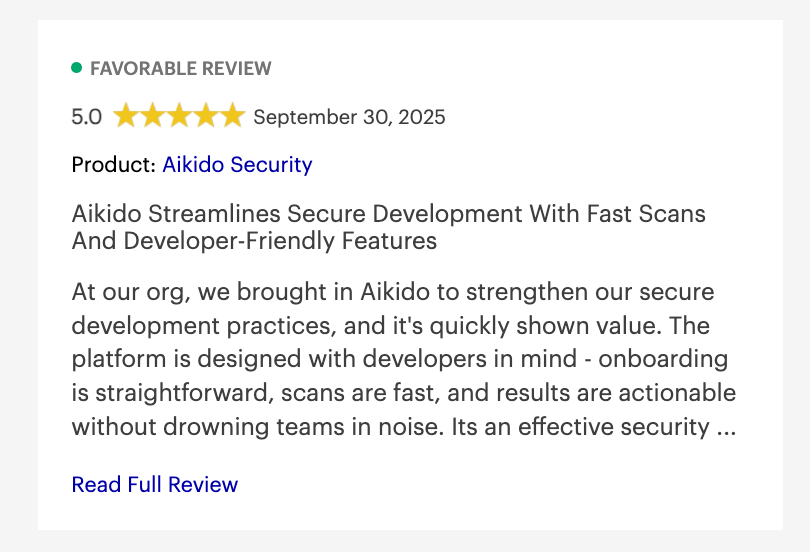
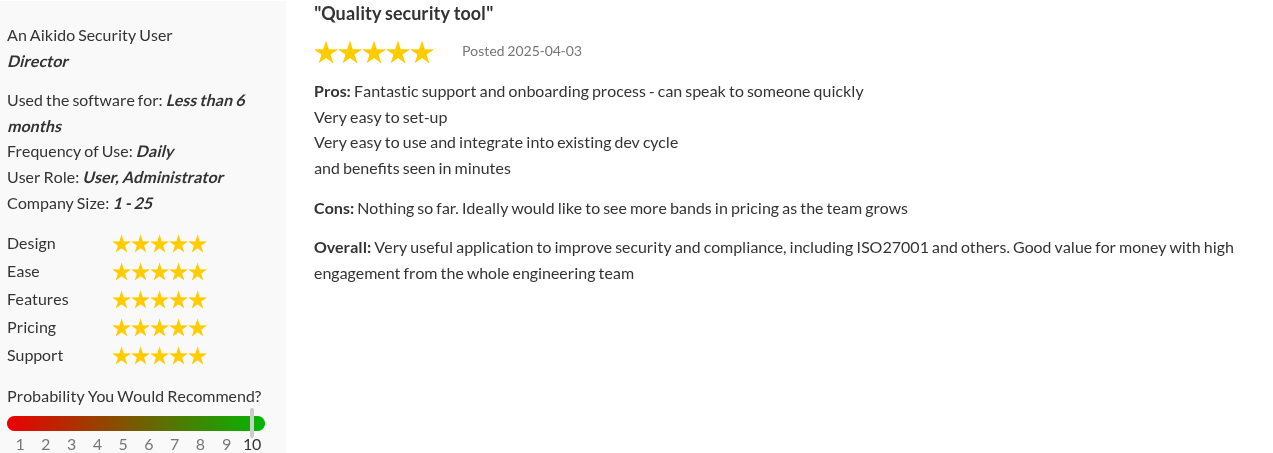
Aikido Security Reviews:
2. Xygeni
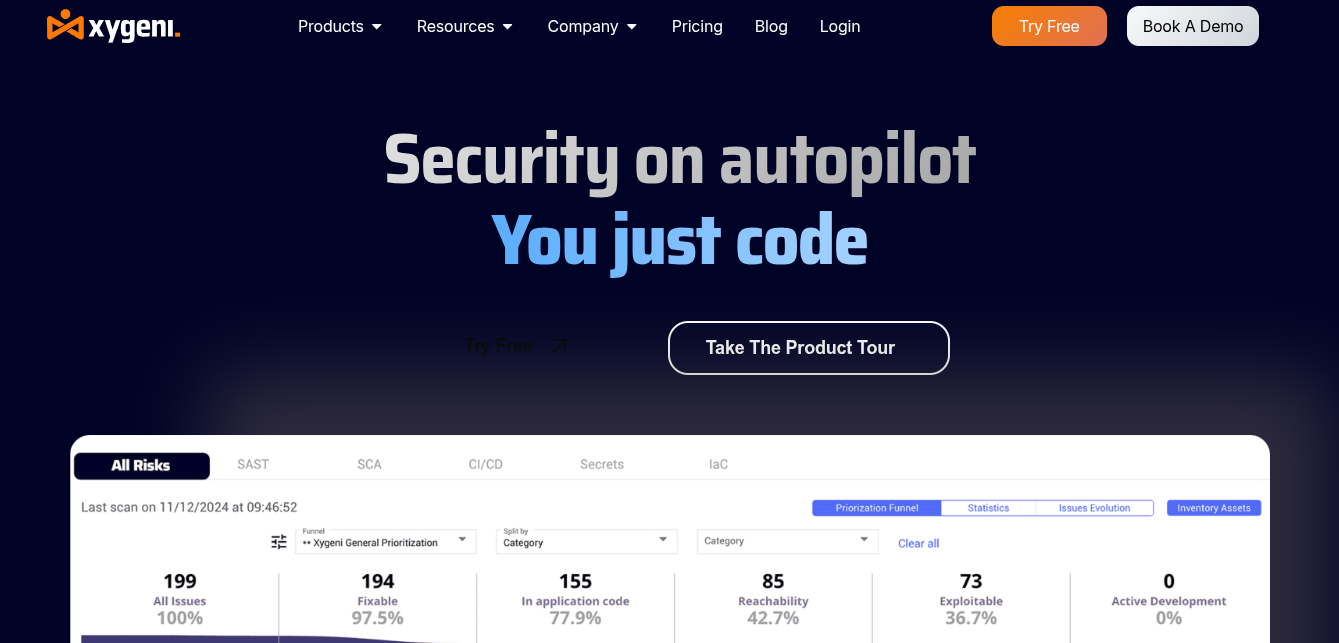
Xygeni offers detailed insights into security postures across development stages, identifying both common vulnerabilities and subtle issues like data leaks. It extends protection to open-source components and container environments for a comprehensive approach.
Key Features:
- Compliance and audit features: Includes audit trail of security events, and supports policy enforcement.
- Malicious Code Detection: Automatically detect malicious code in open-source components and application code in real-time.
- Risk‑based prioritization: Uses contexts such as exploitability, and production proximity to rank vulnerabilities
Pros:
- Malware detection
- Context-aware prioritization
- Dependency graphs
Cons:
- Steep learning curve
- It can become expensive when scaling
- It can be complex to configure
- Users have reported high alert volume
- Users have reported historical or invalid leaks being flagged as active
Ideal Use Case:
Ideal for security teams that need contextual insights and linking of application risks to business impact.
Pricing:
- Standard: $399 per month
- Premium: $715 per month
- Enterprise: Custom pricing
Gartner Rating:
No Gartner review.
Xygeni Reviews:
No independent user generated review.
3. ArmorCode
ArmorCode consolidates data and uses intelligent algorithms to prioritize risks, ensuring immediate attention to critical vulnerabilities.
Key Features:
- Compliance and Reporting: Provides real-time dashboards and reporting features to track security KPIs, and compliance.
- Data Correlation: Aggregates findings from sources into a single platform.
- Supply Chain Security: Includes CI/CD posture management, and SBOM monitoring
Pros:
- Workflow automation
- Remediation guidance
Cons:
- Enterprise focused
- Primarily an aggregation and orchestration layer
- Teams need to source for compatible third-party scanners.
- Initial configuration can be complex
- Clunky User Interface (UI)
Ideal Use Case:
Enterprises managing complex hybrid environments that require centralized orchestration to consolidate fragmented security tools.
Pricing:
Custom pricing
Gartner Rating: 4.7/5.0
ArmorCode Reviews:
4. Legit Security
Legit Security strengthens pipeline security by identifying vulnerabilities in the development infrastructure. It offers a detailed overview of the environment, protecting against data breaches and internal threats.
Key Features:
- Policy Enforcement: Allows teams create and enforce custom policies as code , "Legit Query".
- Contextual Risk Scoring: Ranks risks based on context, such as business impact and environment.
Pros:
- Strong governance and compliance features
- End-to-end visibility
- AI-driven remediation
Cons:
- Primarily enterprise focused
- Requires existing scanners
- Steep learning curve
- Initial configuration can be complex
- Less developer-centric when compared to tools like Aikido Security
Ideal Use Case:
Large, complex organizations that need a unified and automated approach to managing their security posture.
Pricing:
Custom Pricing
Gartner Rating: 4.8/5.0
5. Apiiro
Apiiro is an Application Security Posture Management (ASPM) platform that provides end-to-end visibility, prioritization, and automated remediation. It uses its proprietary "Risk Graph" to connect security findings with business context and runtime exposure.
Key Features:
- Risk Graph: Constructs an application/supply-chain graph to show the relationship between vulnerabilities and the associated code and cloud assets.
- Code-to-Runtime Visibility: Links vulnerabilities in code to their actual exposure in the runtime environment.
- Design-first posture: Detects design-level risks to prevent issues earlier in the SDLC.
Pros:
- AI-driven remediation
- Context-aware prioritization
Cons:
- Enterprise focused
- Steep learning curve
- False positives
- Primarily enterprise focused
- Requires third-party scanners
Ideal Use Case:
Large enterprises with complex, interconnected application and cloud environments that require contextual risk analysis and powerful remediation playbooks.
Pricing:
Custom pricing
Gartner Rating: 4.7/5.0
Apiiro Reviews:
No independent user generated review.
6. Phoenix Security
Phoenix Security is an AI-powered Application Security Posture Management (ASPM) platform. It uses its real-time threat intelligence engine and reachability analysis to filter out noise and focus on exploitable risks. .
Key Features:
- Reachability Analysis: Determines whether a vulnerability is actually exploitable by checking if the vulnerable code is actively being used.
- Ownership and Attribution: Automatically attributes vulnerabilities to the correct code owners and teams.
- Risk Quantification: Helps quantify cybersecurity risk in monetary terms using methodologies like FAIR,
Pros:
- Comprehensive Visibility
- Offers governance features
Cons:
- Primarily enterprise focused
- Requires third-party scanners
- Initial configuration is complex
Ideal Use Case:
Enterprises with mature security teams that need a customizable risk-based vulnerability management (RBVM) platform to consolidate vulnerability data across large, complex environments
Pricing:
- Phoenix Free: Free
- Phoenix Professional: £1,495 per month (~ $1,963 per month)
- Phoenix Enterprise: Custom pricing
Gartner Rating: 4.4/5.0
Phoenix Security Reviews:
7. OX Security
OX Security is an Application Security Posture Management (ASPM) platform that provides contextual prioritization and automated remediation. It is primarily known for its "Code Projection” approach and an AI-backed data fabric for mapping risks.
Key Features:
- AI Data Lake: Uses its AI data fabric (“AI Data Lake”) to align security signals.
- Integrations: Integrates with common DevOps tools and platforms.
Pros:
- Code-to-cloud coverage
- Strong vendor support
Cons:
- Steep learning curve
- Primarily enterprise focused
- Users have reported a lack of proper documentation for some of its features
- Users report limited customization for reports
- Lacks advanced Role-Based Access Control (RBAC) features
Ideal Use Case:
Enterprises with large DevSecOps ecosystems requiring supply chain transparency and continuous security posture monitoring.
Pricing:
Custom pricing
Gartner Rating: 4.7/5.0
OX Security Reviews:
8. Veracode
Veracode is an Application Security Posture Management (ASPM) tool designed to help enterprises identify, manage, and remediate application-layer risks at scale.
Key Features:
- Binary Analysis: Scans compiled applications binaries for vulnerabilities
- Enterprise Compliance: Provides reporting and governance features to support audit and compliance workflows.
Pros:
- Strong Compliance Focus
- Context-based insights
Cons:
- Primarily enterprise focused
- Poor Developer Experience
- High False Positives
- Steep Learning Curve
- Users have reported limitations when integrating with certain scanners
- Does not support on-premise applications
Ideal Use Case:
Large companies with a mix of in-house developed code and third-party commercial software where scanning compiled code is essential.
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
Veracode Reviews:

9. Invicti
Invicti is an application security platform best known for "proof-based scanning" philosophy. It focuses on providing accurate, verified vulnerability data to eliminate false positives and streamline remediation efforts.
Key Features:
- Automated Asset Discovery: It continuously searches web applications, APIs, and cloud assets across environments.
- Risk Prioritization: Aggregated data across tools and uses its “proof-based” scanning engine to determine exploitable vulnerabilities.
Pros:
- Asset discovery
- Supports common CI/CD platforms
- AI-guided remediation
Cons:
- Heavily enterprised focused
- Steep learning curve
- Users have reported additional configuration for complex applications
- It needs to be whitelisted to prevent being blocked by WAFs and IPS/IDS
- It is DAST-centric, and requires third part scanners for full coverage
Ideal Use Case:
Teams prioritising thorough DAST scans to find vulnerabilities in complex Single Page Applications (SPAs) and dynamic JavaScript applications.
Pricing:
Custom pricing
Gartner Rating: 4.5/5.0
Invicti Reviews:

10. Wiz

Wiz is a cloud-native security platform with an integrated Application Security Posture Management (ASPM) platform. It creates a "Security Graph" connecting application-layer risks in code to their potential impact on the runtime and cloud infrastructure.
Key Features:
- Automated Remediation: Generates actionable remediation guidance and one-click pull requests in CI/CD platforms.
- Compliance Support: Assesses compliance posture against its built-in compliance frameworks
Pros:
- Security graph
- Attack path analysis
- Cloud discovery and inventory
Cons:
- Primarily cloud-focused
- Only suitable for enterprises
- Pricing can become expensive when scaling
- May require complementary tools for full AppSec coverage
- It’s not as developer-centric as platforms like Aikido Security
Ideal Use Case:
Companies operating exclusively in public cloud (AWS, Azure, GCP) that need instant, agentless visibility across all environments
Pricing:
Custom pricing
Gartner Rating: 4.7/5.0
Wiz Reviews:
“We use Wiz. There's a lot of features in there and I'm overall pretty impressed with it, but it's mostly the security team using it and me keeping an eye on things…” – Platform engineer on Reddit
“While Wiz excels in many areas, its pricing can be on the higher side for smaller teams or organizations, and the vast amount of data and alerts can sometimes feel overwhelming without proper tuning.” – G2 reviewer (Head of Engineering)
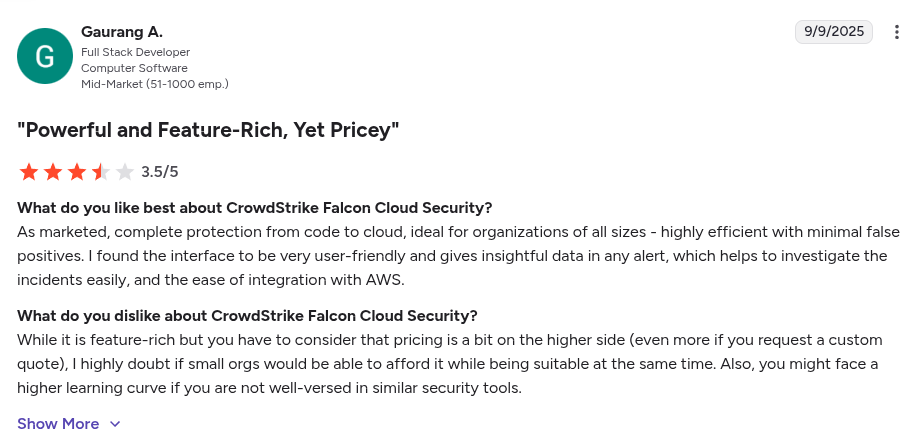
11. Crowdstrike Falcon Cloud Security

CrowdStrike offers an integrated Application Security Posture Management (ASPM) solution as part of its Falcon Cloud Security platform. It operates by delivering deep, agentless visibility into applications, APIs, and microservices running across multi-cloud environments.
Key Features:
- Integration with CrowdStrike Falcon platform: Integrates seamlessly with CrowdStrike ecosystem.
- Real-time threat detection with AI: Uses AI and behavioral analytics to detect threats.
- Agentless Application Mapping: Provides a real-time map of all applications, microservices, APIs, and dependencies running in the cloud.
Pros:
- Strong threat intelligence
- Code-Level Insight
Cons:
- Primarily enterprise focused
- Learning Curve
- False positives
- Users have reported issues integrating with custom third part tools
Ideal Use Case:
Organizations that already use CrowdStrike for EDR/XDR and want to consolidate security tools into a unified platform
Pricing:
Custom pricing
Gartner Rating: 4.8/5.0
Crowdstrike Falcon Cloud Security Reviews:

12. AccuKnox

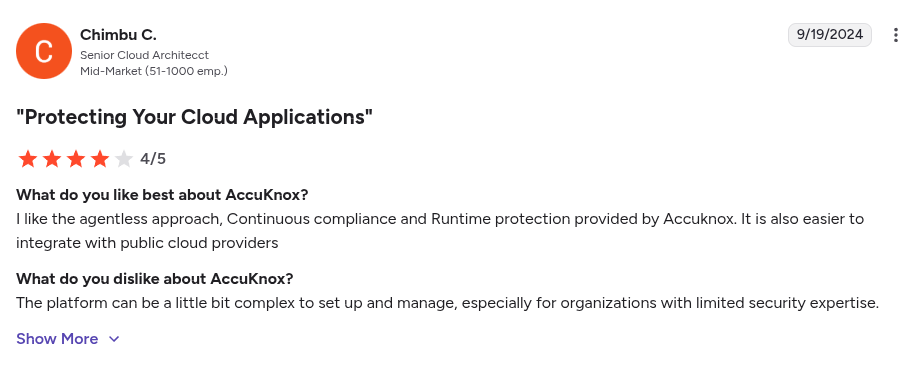
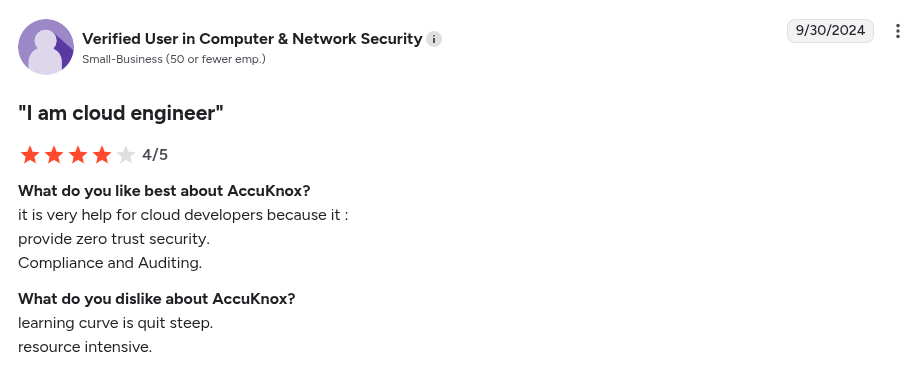
AccuKnox’s ASPM solution combines security testing tools and runtime insights to provide a unified, contextual view of application risks from code to cloud. It is primarily focused on runtime enforcement via eBPF.
Key Features:
- Code-to-Runtime Correlation: Analyzes findings from build phases with runtime behavior to provide actionable insights and help trace vulnerabilities back to the source code.
- Flexible Deployment Options: Supports SaaS, on-premises, and air-gapped deployments.
- AI-Powered Risk Prioritization: It uses AI to correlate vulnerabilities, exploitability data, and business impact.
Pros:
- Compliance Support
- Flexible deployment
- Open-source foundation
Cons:
- Enterprise focused
- Initial configuration can be complex
- Steep learning curve
- Users have reported slow responses from customer support
Ideal Use Case:
Security teams that prefer solutions built on transparent, open-source foundations (CNCF projects).
Pricing:
Custom pricing
Gartner Rating: 4.5/5.0
AccuKnox Reviews:
Comparing The Top 12 ASPM Tools
To help you compare the capabilities of the tools above, the table below compares each tool's features along with their ideal use case.
Choosing the Right ASPM Tool for Your Workflow
Developing applications in today’s environment can be challenging, but securing them doesn’t have to be. The right tools give teams end-to-end visibility, actionable insights, and seamless integration with existing workflows.
Aikido Security delivers all this for both startups and enterprises. Its AI-driven, developer-first ASPM platform provides a centralized view of application security, correlating risks across code and cloud environments while reducing alert fatigue from SAST, SCA, IaC, and secrets scanners.
Want full visibility across your applications? Start your free trial or book a demo with Aikido Security today.
FAQ
How do ASPM tools integrate with existing DevSecOps workflows?
ASPM tools integrate by connecting with source control systems, CI/CD pipelines, issue tracking, and collaboration platforms. This allows security findings from SAST, DAST, SCA, and IaC scans to flow directly into developers’ workflows, minimizing context switching. For example, Aikido Security provides in-PR feedback, IDE plugins, and native integrations with GitHub, GitLab, Jira, and Slack, making security part of the natural DevOps flow.
What is the difference between DAST and ASPM?
DAST (Dynamic Application Security Testing) analyzes running applications to find security vulnerabilities, focusing mainly on runtime behavior. ASPM, on the other hand, offers a broader view, aggregating results from multiple scanners (SAST, DAST, SCA, IaC), prioritizing risks, and continuously monitoring application posture across the software lifecycle. Tools like Aikido Security unify these approaches, correlating findings from DAST and other sources into actionable, developer-friendly remediation workflows.
Why is using ASPM tools important for enterprise security?
ASPM tools help enterprises maintain consistent visibility into vulnerabilities, prioritize risks based on business impact, and enforce compliance policies across large applications. By unifying the AppSec ecosystem, organizations can reduce alert fatigue and improve remediation efficiency. Aikido Security, for example, uses AI-driven risk prioritization and automated remediation to strengthen security posture while enhancing developer productivity.
How do you benchmark and POC ASPM solutions?
Benchmarking ASPM solutions involves evaluating integration ease, coverage of scanners and cloud assets, AI-driven prioritization, developer experience, and compliance capabilities. A proof of concept (POC) usually tests real pipelines, sample applications, and remediation workflows to validate effectiveness. Solutions like Aikido Security provide fast onboarding for POCs, in-PR guidance, and actionable feedback, making it easier to assess both security impact and developer usability.
You might also like:

Secure your software now



.jpg)


