In 2025, 99% of all cloud breaches were traced back to cloud misconfigurations. From managing multi-cloud sprawl and rapid DevOps deployments to keeping up with shifting compliance standards and verifying AI-generated configurations, modern teams are fighting an uphill battle.
Cloud Security Posture Management (CSPM) tools are no longer a “nice-to-have”, they’re a must-have for any organization seeking complete visibility and protection across their cloud environments. CSPM tools have evolved to include advanced automation, AI-driven remediation, and continuous compliance monitoring to keep up with today’s complex, fast-moving threat landscape.
In this guide, we’ll explore the top CSPM tools to help you secure your cloud infrastructure across AWS, Azure, GCP, and beyond. We’ll start with a comprehensive list of the most trusted CSPM platforms, then break down which tools are best for specific use cases, whether you’re a developer, startup, or large enterprise managing multi-cloud deployments.You can jump to specific use cases below:
- Best 4 CSPM Tools for Developers
- Best 5 CSPM Tools for Enterprise
- Best 4 CSPM Tools for Startups
- Best 5 CSPM Tools for Multi-Cloud Environments
- Best 5 CSPM Tools for Cloud Protection
- Best 5 CSPM Tools for AWS
- Best 5 CSPM Tools for Azure
TL;DR
Among all the CSPM tools reviewed, Aikido cloud emerges as the most complete posture management platform. Built for dev-first cloud security its features include both agent-based and agentless virtual machine scanning, cloud and kubernetes posture management, cloud misconfiguration checks and much more.
In addition, it incorporates additional modules for code, containers and API security. Organizations can decide to start with the CSPM module , and expand as they go on (to include SAST, DAST, etc), integrate it with other existing products, or select Aikido as a single suite that covers all aspects of code, cloud and runtime security.

What is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) refers to a class of security tools that continuously monitor and evaluate your cloud infrastructure for misconfigurations, compliance violations, and security risks. These tools automatically scan across your cloud environments, comparing configurations against industry best practices and frameworks such as CIS Benchmarks, SOC 2, and ISO 27001.
Rather than relying on manual reviews or occasional audits, CSPM tools operate continuously,giving security and DevOps teams real-time visibility and alerts to potential exposures. Many modern CSPMs also include automation for fixing issues, whether through AI-generated remediations or direct integrations with developer pipelines.
Why You Need a CSPM Tool
Deploying cloud infrastructure has never been easier, you spin up a terminal, deploy a VM, and you're done. However, this also means that a lot of default configurations, ports, and settings get deployed along with it. CSPM tools spot these giving you complete visibility into what’s deployed and how secure it is. Here’s a few thing CSPM tools ensure:
- Prevent Misconfigurations: Detect insecure configurations (like open S3 buckets, overly permissive IAM roles, or unencrypted storage) before they become breach vectors.
- Ensure Compliance: Automate alignment with regulatory frameworks like SOC 2, PCI-DSS, NIST, and CIS Benchmarks. Generate audit-ready reports on demand.
- Improve Visibility: Provides a centralized view of cloud assets and misconfigs across providers.
- Automated Remediation: Save engineering time by auto-fixing IaC or runtime issues, or pushing alerts to tools like Jira or Slack.
- Scale Securely: As your infrastructure scales, CSPMs ensure your security controls keep up.
Curious about real-world CSPM incidents? Check out the 2025 Verizon DBIR report as well as the Cloud Security Alliance.
What to Look for When Choosing a CSPM Tool
Picking the right CSPM tool depends on your stack, team structure, and regulatory needs. Here are few key things to look out for:
- Cloud Coverage: Does it support the cloud provider you use;AWS, Azure, GCP, Digital Ocean, Civo and beyond?
- CI/CD & IaC Integration: Can it scan infrastructure-as-code and integrate into your CI/CD pipeline?
- Compliance Support: Are common standards preconfigured (SOC 2, ISO, HIPAA), and can you build your own policies?
- Alert Quality: Does it provide actionable, low-noise alerts?Ideally with context-aware prioritization.
- Scalability & Pricing: Does it fit your team's scaling needs (multi-cloud setups, on-premise (private cloud) etc.)? And is its pricing sustainable when scaling.
Top 16 Cloud Security Posture Management (CSPM) Tools
1. Aikido Security
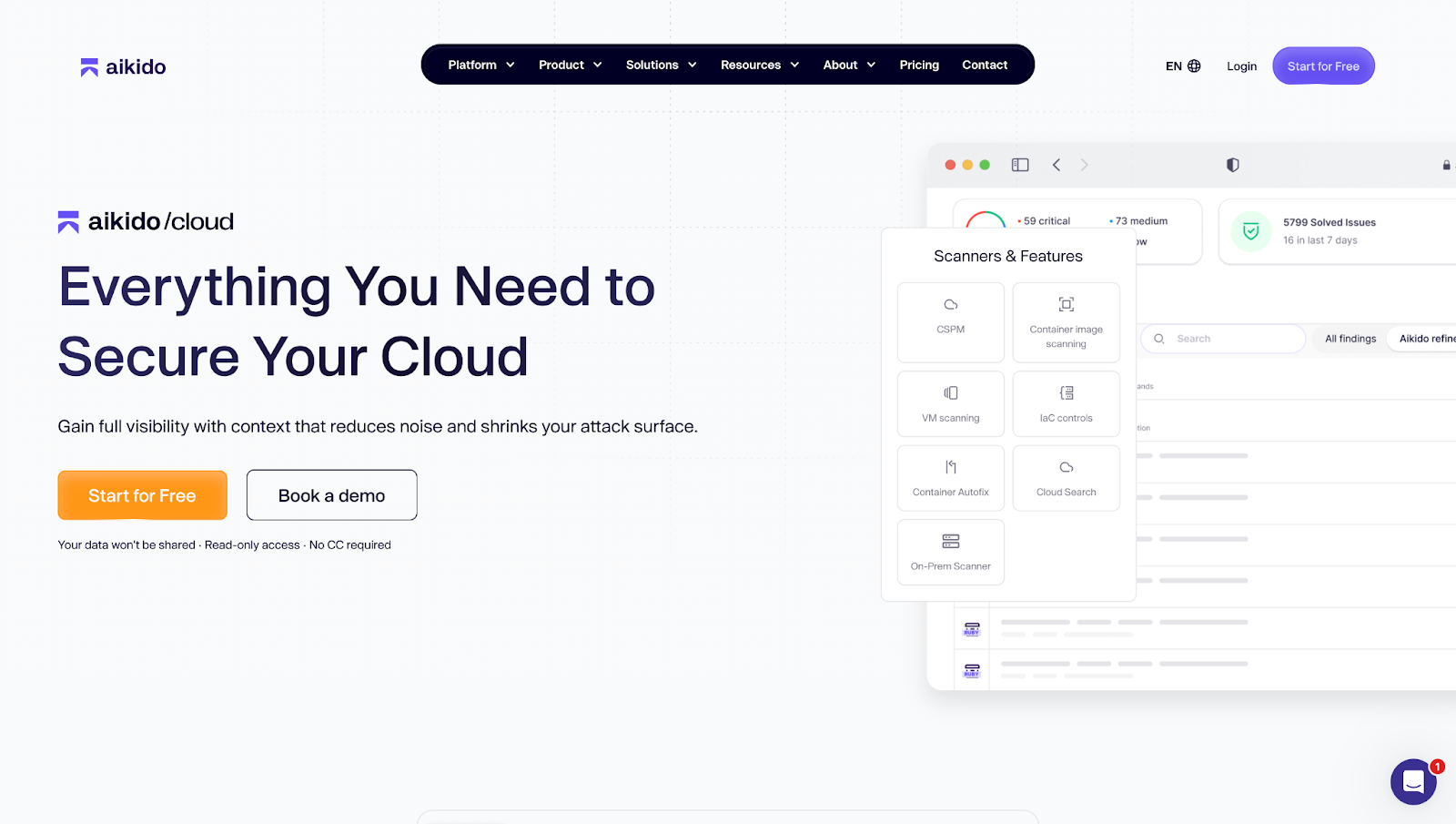
Aikido Security is the ultimate CSPM platform that covers everything in the cloud and even runtime security. It’s designed for teams that want real protection without the noise. Compared to alternatives, it provides a better developer experience, has superior alert suppression, and can prioritize issues more seamlessly.
In addition, even though other vendors tout code to cloud security, only Aikido covers elements like fully-native SAST, open-source scanning (SCA) and code quality. This means Aikido gives teams a single pane of glass for monitoring their security posture without the usual friction, while giving engineering and security leaders peace of mind.
Aikido Cloud offers the best-in-class scanners to augment its CSPM tool, container scanning, IaC scanning, virtual machine Scanning, on-prem scanner, cloud search and more. Each module can be selected as a standalone solution that can compete with alternatives, or can be integrated to create a complete code to cloud to runtime security platform.
Key Features:
- Agentless/API-Based Setup: Connects to your cloud accounts using read-only APIs–no installation agents required.
- Cloud Asset Search: You can query your cloud environments with natural language or structured queries to find resources, relationships, misconfigurations, etc.
- Developer-Centric Workflow: Instant feedback in PRs and IDEs, plus AI-powered autofix and actionable remediation workflows.
- Context-Aware Risk Scoring: Uses reachability analysis and curated rules to surface what matters. Cutting the false positives by up to 90%.
- Built for Devs: Integrates deeply with GitHub, GitLab, Bitbucket, Jira, Slack, and much more. You can run scans locally, in pull requests, or as part of your release process.
- Connected “code-to-cloud” coverage: Aikido links code, cloud, and runtime in one seamless workflow. You can start with the CSPM module and expand (code scanning, container/IaC scanning, API security, and runtime protection)
- Comprehensive compliance mapping: Supports major frameworks like SOC 2, ISO 27001, PCI DSS, GDPR, and much more.
Pros:
- Supports multi-cloud monitoring (AWS, Azure, GCP)
- Reduced security risk since permissions are read-only.
- Scales automatically as new resources are added
- No installation agents required
- Centralized reporting and compliance
- IaC scanning and Kubernetes security
- Provides context-aware remediation guidance and risk scoring
Best For:
Any organization looking for an intuitive platform to monitor and secure everything from code-to-cloud.
Pricing:
All paid plans starting from $300/month for 10 users
- Developer (Free Forever): Free for up to 2 users. Supports 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Supports 10 repos, 25 container images, 5 domains and 3 cloud accounts.
- Pro: Supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Supports 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Custom offerings are also available for startups (30% discount) and enterprises
Gartner Rating: 4.9/5.0
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra and SourceForge.
2. Aqua Security

Aqua Security combines CSPM with runtime protection across containers, serverless, and cloud VMs. It is backed by open-source tools like Trivy and CloudSploit. .
Key Features:
- Multi-cloud support: Supports workloads across AWS, Azure and Google Cloud.
- Integration: Integrates with common CI/CD pipelines
- Compliance mapping: Aligns scan results with compliance frameworks
Pros:
- Supports a broad range of cloud providers
- CI/CD integration
- Runtime protection
- Established enterprise ecosystem
Cons:
- Primarily enterprise focused
- Setup can be complex compared to agentless tools like Aikido Cloud
- Some features require separate modules and licenses
- Steep learning curve
- Remediation workflows often require manual fixes
Best For:
Teams running cloud-native apps and Kubernetes in production.
Pricing:
Custom Pricing
Gartner Rating: 4.0/5.0
Aqua Security Reviews:


3. BMC Helix Cloud Security
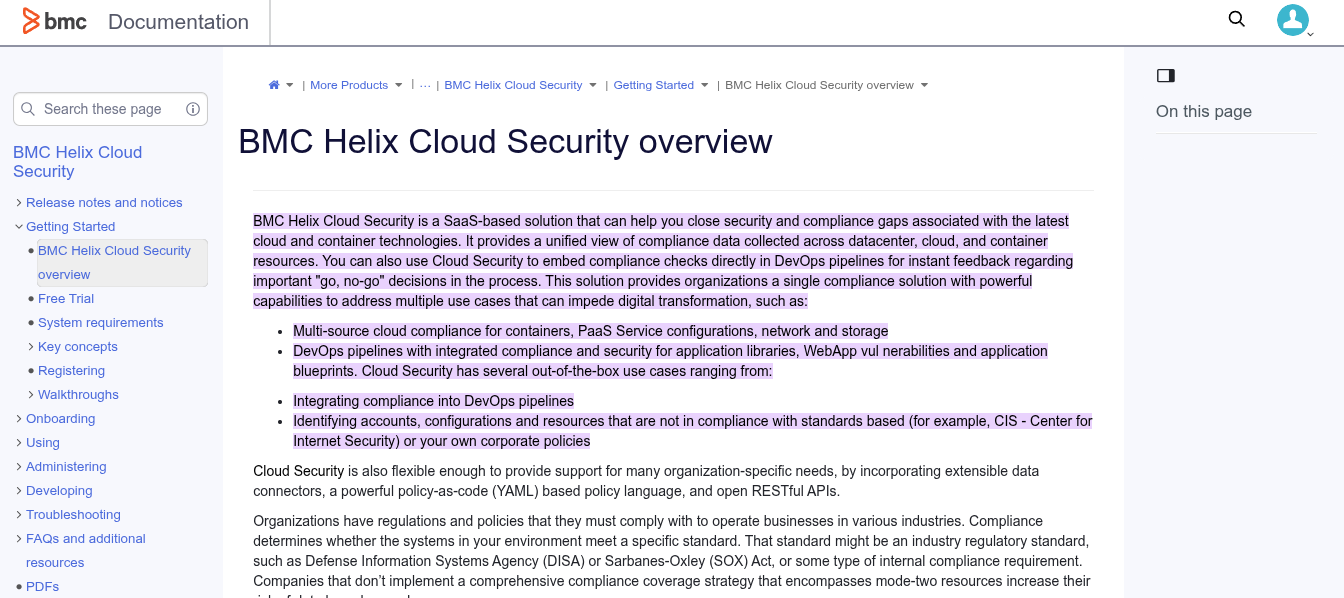
Now part of the BMC Helix suite, BMC Helix Cloud Security automates cloud compliance and security via policy-driven governance across AWS, Azure, and GCP.
Key Features:
- Prebuilt policies: Comes with out-of-the box policies mapped to compliance frameworks.
- Tight integration with BMC ITSM: Connects directly with BMC’s IT Service Management suite.
- Unified multicloud security reporting: Provides a single dashboard for compliance posture and security findings.
Pros:
- Integrates into BMC ecosystem
- Strong compliance focus
- Policy-driven governance
Cons:
- Primarily enterprise focused
- Steep learning curve
- Heavy reliance on BMC stack
- Minimal CI/CD integration
- Onboarding can be complex due to reliance on BMC ecosystem
Best For:
Enterprises already using the BMC ecosystem
Pricing:
Custom Pricing
G2 Rating: 4.5/5.0
BMC Helix Cloud Security Reviews:
“Very minimal effort to onboard – provides a full posture view across clouds.” — IT Ops Manager on G2
4. Check Point CloudGuard

CloudGuard is Check Point’s CNAPP offering with CSPM built-in. It pairs configuration scanning with threat detection using its ThreatCloud intelligence engine.
Key Features:
- Out-of-the-box Compliance Policies: Provides 50+ predefined compliance policies
- Automated remediation: Used pre-packaged scripts called CloudBots to automatically identify and fix issues.
- Multi-cloud Support: Integrates with the three major cloud providers–AWS, Google Cloud, Azure.
Pros:
- Comprehensive compliance coverage
- Strong automated remediation
- Supports custom policies
- Advanced threat detection
Cons:
- Pricing can become steep when scaling
- Often requires specialist to setup
- Clunky User Interface
Best For:
Enterprises using Check Point firewall/endpoint tools seeking unified cloud and network security.
Pricing:
- Pay-As-You-Go (PAYG)
- Bring Your Own License (BYOL)
- Enterprise Agreements
Gartner Rating: 4.6/5.0
Check Point CloudGuard Reviews:


5. CloudCheckr

CloudCheckr blends cost optimization and CSPM in one platform. It’s primarily used by MSPs and enterprise SecOps teams to enhance cloud governance.
Key Features:
- Best practice checks: Utilized hundreds of checks to identify issues
- Compliance scorecards: Assesses your environment against major compliance frameworks.
- Custom policy engine: Teams can define and enforce custom policies on their cloud environments.
- Cost management insights: Provides insights on your cloud infrastructure cost.
Pros:
- Combines cost optimization and CSPM
- Good cloud cost analytics
- Granular cost and compliance reporting
Cons:
- Users have reported delays in consumption data updates and receiving alerts.
- Setting up the platform can be complex, especially in large-scale cloud environments.
- Users report experiencing latency when exporting reports.
Best For:
MSPs and teams balancing security with cloud spend optimization.
Pricing:
Custom pricing
Gartner Rating: 3.8/5.0
CloudCheckr Reviews:
“Security and cost visibility in one tool – huge time saver.” — SecOps Lead on G2
6. CloudSploit
Originally a standalone open-source project, CloudSploit, now maintained by Aqua Security, offers agentless scanning of cloud environments for misconfigurations.
Key features:
- Open-source and community-driven: It is constantly updated and improved by its community of security professionals.
- Extensible via plugins: New Security checks can be added as plugins.
- Flexible outputs:Cloudspoilt is capable of outputting results in multiple formats(JSON, CSV,Junit XML).
Pros:
- Open-source
- CI/CD integration
Cons:
- Issue remediation is largely manual
- No risk based prioritization
- No issue correlation
- Lacks historical data
Best For:
DevOps teams seeking a simple, scriptable scanner to validate cloud posture.
Pricing:
Free (open-source)
Gartner Rating: Unavailable after being acquired by Aqua Security
CloudSploit Reviews:
“Lightweight, fast, and surprisingly deep for a free tool.” — DevOps Engineer on Reddit
7. CrowdStrike Falcon Cloud Security
Falcon Cloud Security blends CSPM with runtime threat detection powered by CrowdStrike’s EDR and XDR.
Key Features:
- Real-time threat detection with AI: Uses AI and behavioral analytics to detect threats.
- Identity risk analysis (CIEM): Analyzes identities, roles, and permissions to identify exploitation paths.
- Integration with CrowdStrike Falcon platform: Integrates seamlessly with CrowdStrike ecosystem.
Pros:
- Comprehensive security suite
- Threat intelligence
- Supports cloud-native architectures
Cons:
- False positives
- Steep learning curve
- Limited on-premise options
- Complex to configure
- Users report support delays
Best For:
Security teams looking to combine misconfig detection with breach prevention.
Pricing:
Custom pricing
Gartner Rating: 4.8/5.0
CrowdStrike Falcon Cloud Security Review:
“Finally, a CSPM with real detection capabilities, not just another checklist.” — Security Analyst on X
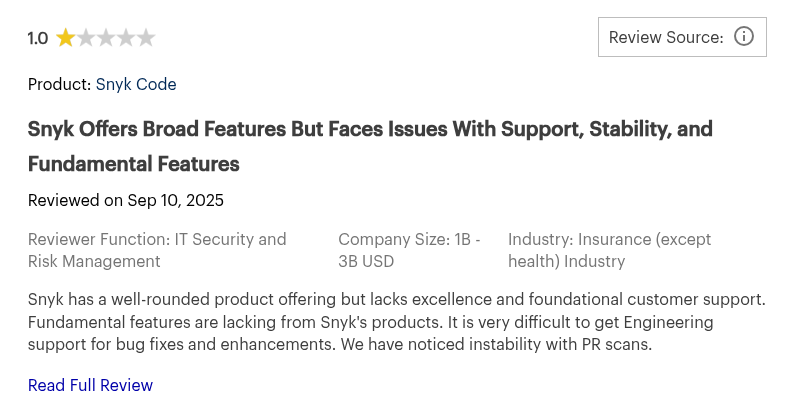
8. Snyk Cloud (Formerly Fugue)
Snyk Cloud focuses on policy-as-code and drift detection. It integrates IaC scanning with CSPM for a complete DevSecOps flow.
Key features:
- Policy-as-code enforcement: Compliance requirements are written as code.
- CI/CD integration: Integrates with some CI/CD tools
Pros:
- Fast scans
- Open-source security
- Remediation guidance
Cons:
- Pricing is expensive
- False positives
- Poor customer support
- It does not support IAST for runtime security (Aikido Cloud does)
Best for:
Organizations seeking policy-as-code workflows.
Pricing:
Included in Snyk Cloud plans
Gartner Rating: 4.4/5.0
Snyk Cloud Reviews:
9. JupiterOne
JupiterOne offers its CSPM via a graph-based asset management approach. It builds a knowledge graph of all cloud assets and relationships to identify risks.
Key Features:
- Graph-based query engine (J1QL): Provides graph-style database for querying and analyzing relationships between cloud assets.
- Asset discovery: Automatically discovers and inventories assets from cloud environments.
- Built-in compliance packs: Offers ready-to-use compliance templates.
Pros:
- Free community tier available
- Flexible querying
- Asset relationship graph
Cons:
- Steep learning curve
- Enterprise focused
- Can feel overwhelming for small teams
- Connectors may miss data and require manual reconsciliation
- Pricing can become complex when scaling
Query performance can slow down on large graphs
Best For:
Security teams who want relationship-aware asset graphs and flexible querying across sprawling environments.
Pricing:
Custom pricing
Gartner Rating: 4.8/5.0
Jupiter One Reviews:
“JupiterOne made asset visibility click for our team. J1QL is powerful.” — SecOps Lead on G2
10. Lacework
Lacework by Fortinet is a CNAPP platform offering CSPM alongside anomaly detection and workload protection. Its Polygraph Data Platform maps behaviors across your cloud to surface threats and misconfigurations.
Key Features:
- ML-powered anomaly detection:Learns the normal behavior of users, applications, and network, and provides a visual mapping of their connection.
- Agentless workload protection: Uses both API-based (agentless) and agent-based data collection methods to access cloud environments.
- Compliance assessments and automated reports: Users can generate automated compliance reports on demand or at set intervals.
Pros:
- Runtime and behavior anomaly detection
- Reduced alert fatigue
- Seamless integration with Fortinet ecosystem
Cons:
- Complex to setup
- Steep learning curve
- Potential vendor lock-in
- Users have reported a slowdown in feature developments
Best For:
Teams that want a CSPM combined with threat detection and minimal alert fatigue, and have existing fortinet integrations.
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
Lacework Reviews:

11. Microsoft Defender for Cloud
Microsoft Defender for Cloud is Azure’s built-in CSPM, extended with integrations for AWS and GCP. It gives you posture management, compliance checks, and threat detection in one pane.
Key features:
- Cloud Posture Security Score: Highlights the highest-impact issues/vulnerabilities that will effectively reduce the organization's risk profile.
- Multi-Cloud Misconfiguration Detection: It flags misconfigurations that do not align with industry best practices.
- Integration with Microsoft Defender XDR and Sentinel SIEM: It shares threat intelligence and alerts with Microsoft Defender XDR and Microsoft Sentinel.
Pros:
- Mult-cloud support
- Comprehensive cloud workload protection (CWP)
- Native support for Microsoft ecosystem
Cons:
- It can be complex to setup
- Pricing can become expensive when scaling
- Although multi-cloud, it is primarily focused on Microsoft Azure
- Steep learning curve
- Users have reported delayed detection
Best For:
Azure-first organizations looking for seamless, native posture management and threat protection.
Pricing:
- Foundational CSPM: Free
- Defender CSPM: $5.11 per month/billable resource
Gartner Rating: 4.2/5.0
Microsoft Defender for Cloud Reviews:
12. Prisma Cloud (Palo Alto Networks)
Prisma Cloud is a comprehensive CNAPP that includes a robust CSPM, IaC scanning, and workload security. It covers the entire lifecycle from code to cloud.
Key features:
- Real-time cloud posture monitoring: Continuously monitors cloud environments and provides historical data in configuration changes.
- Attack path visualization: Provides graph to visualize attack paths.
- Broad compliance and policy packs: Includes over 100 built in security policies.
Pros:
- Strong compliance features
- AI-powered risk prioritization
- Multi-cloud support
Cons:
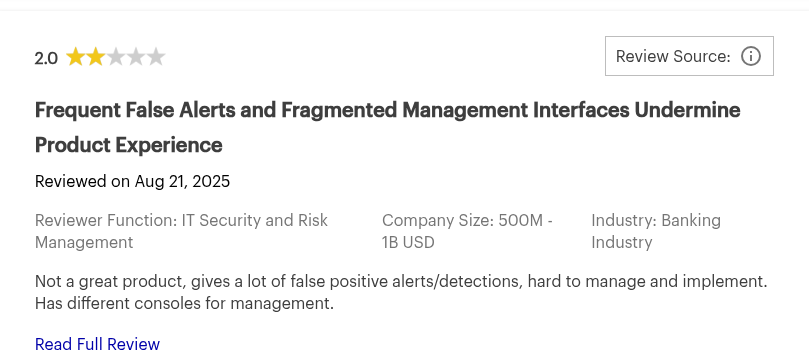
- Steep pricing
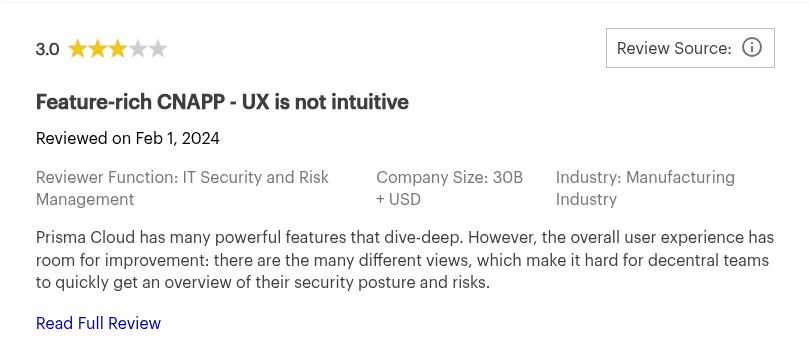
- Outdated user interface and console
- Deployment processes in large environments can become complex and length
Steep learning curve
Best For:
Enterprises running complex multi-cloud environments and requiring deep visibility and coverage.
Pricing:
Custom pricing
Gartner Rating: 4.2/5.0
Prisma Cloud Reviews:
13. Prowler
Prowler is an open-source security auditing tool focused primarily on AWS. It checks your infrastructure against best practices and regulatory frameworks.
Key Features:
- Automated Compliance: Prowler includes dozens of pre-built controls that map directly to industry-standard frameworks.
- Basic Multi-cloud Support : The multi-cloud features are actively being developed by the open-source community.
- CI/CD Pipeline Integration: Supports common CI/CD pipelines.
Pros:
- Open-source
- Community-driven
- Remediation support
Cons:
- Remediation is primarily manual
- Lack of vendor support
- No historical data and trend analysis
- Adds operational overhead when self-hosting
Best For:
AWS-heavy organizations seeking customizable, open-source scanning.
Pricing:
Free (open-source)
Prowler Reviews:

14. Sonrai Security
Sonrai Security combines CSPM with CIEM and data security, emphasizing cloud identity governance and sensitive data exposure prevention.
Key Features:
- Identity relationship and privilege risk analysis: It identifies risky privilege escalation paths and "toxic combinations" of permissions.
- CSPM and compliance auditing: Continuously monitors cloud environments for misconfigurations and posture drift.
- Automation for least-privilege enforcement: Its Cloud Permissions Firewall can automatically disable unused services, identities, and remove unused sensitive permissions.
Pros:
- Just-in-Time (JIT) access:
- Intelligent risk prioritization
Cons:
- Primarily enterprise focused
- Limited customization options
- Reports of performance issues with advanced queries
- Integration can be complex
- License can be difficult to predict
Best For:
Enterprises focused on identity governance, compliance, and protecting cloud-resident sensitive data.
Pricing:
- Partial Cloud Coverage: $200 per account/month
- Full Cloud Coverage: $150 per account/month
Gartner Rating: 4.0/5.0
Sonrai Security Reviews:
15. Tenable Cloud Security ( Formerly Accurics)
Tenable Cloud Security (formerly Accurics) focuses on IaC scanning, drift detection, and posture management. It fits well into GitOps and DevSecOps pipelines.
Key Features:
- Policy enforcement: Policies can be custom or based on industry benchmarks.
- Misconfiguration detection : Continuously scans your cloud resources against industry standards and regulations.
- Integration with Tenable.io: Combines insights from your cloud environments with Tenable's broader vulnerability intelligence.
Pros:
- Comprehensive security controls
- Automated compliance management
- Risk-based prioritization
Cons:
- Pricing is expensive
- Complex setup
- Users have reported slow performance and inefficiency when dealing with large, complex cloud environments
- False Positives
- Limited feature depth
Best For:
DevOps teams needing pre-deployment and runtime posture checks tied to IaC.
Pricing:
Part of Tenable platform; usage-based pricing.
Gartner Rating: 4.7/5.0
Tenable Cloud Security Reviews:
16. Zscaler Posture Control
Zscaler Posture Control brings CSPM to Zscaler’s Zero Trust Exchange. It blends posture, identity, and vulnerability context to highlight real risks.
Key Features:
- Unified CSPM and CIEM: Provides a single platform to manage both CSPM and CIEM.
- Threat Correlation: It correlates findings from multiple security engines to identify the most critical and exploitable attack paths.
- Multi-cloud coverage: Supports all major cloud providers.
- Integrated with Zscaler’s broader Zero Trust ecosystem: Native part of the Zscaler Zero Trust Exchange platform
Pros:
- Part of a Zero Trust ecosystem
- Agentless deployment
- Policy enforcement
Cons:
- Steep learning curve
- Pricing can be expensive
May require external professionals when deploying due to complexity
Best For:
Zscaler customers seeking native posture insights aligned to Zero Trust strategies.
Pricing:
Add-on to Zscaler platform; enterprise-focused.
Gartner Rating: 4.0/5.0
Zscaler Posture Control Reviews:
Best 4 CSPM Tools for Developers
Key Criteria When Choosing CSPM Tools For Developers:
- Infrastructure as Code (IaC) scanning
- Developer-friendly UI and APIs
- GitOps and CI/CD compatibility
- Autofix or actionable remediation guidance
- Clear ownership and minimal false positives
Here are the top 4 CSPM tools tailored for developers:
- Aikido Cloud: Easy setup, AI-based autofix, and built for developers. Integrates directly with CI and GitHub.
- Snyk Cloud (Formerly Fugue): Policy-as-code with Regula; ideal for teams using Terraform and GitOps.
- Prisma Cloud: Full code-to-cloud scanning and IDE integration.
- Prowler: Simple CLI tool that devs can run locally or in pipelines.
Best 5 CSPM Tools for Enterprise
Key Criteria For Choosing a CSPM Tool For Your Enterprise:
- Multi-account, multi-cloud support
- Built-in compliance frameworks
- Role-based access control (RBAC)
- SIEM/ITSM integrations
- Scalable pricing and vendor support
Here are the top 5 CSPM tools tailored for enterprises:
- Aikido Cloud: Comprehensive CSP coverage, compliance reporting, affordable enterprise pricing
- Prisma Cloud: Covers posture, runtime, and compliance at scale.
- Check Point CloudGuard: Multi-cloud governance and deep policy enforcement.
- Microsoft Defender for Cloud: Native Azure coverage plus AWS/GCP.
- Ermetic: Advanced CIEM and governance for complex environments.
Best 4 CSPM Tools for Startups
Key Criteria For Choosing a CSPM Tool for Your Startup:
- Free tier or affordable plans
- Easy onboarding and UX
- SOC 2/ISO readiness out of the box
- Developer-first focus
- Unified platform features
Here are the top 4 CSPM tools tailored for startups:
- Aikido Cloud: Free tier, AI autofix, and dev-centric.
- CloudSploit: Free, open-source, and easy to integrate.
- JupiterOne: Free community tier and simple asset-based risk queries.
- Prowler: CLI-driven, cost-free AWS scanner with compliance support.
Best 5 CSPM Tools for Multi-Cloud Environments
Key Criteria When Choosing a CSPM Tool For Multi-Cloud Environments:
- Full support for AWS, Azure, GCP (and more)
- Unified dashboards
- Normalized compliance reporting
- Multi-account and multi-region visibility
- Consistent alerting across clouds
Here are the top 5 CSPM tools tailored for multi-cloud environments:
- Aikido Cloud: Cloud-agnostic with support for all three major cloud providers and more.
- Prisma Cloud: Truly cloud-agnostic with deep features.
- JupiterOne: Graph-based visibility across clouds and services.
- Check Point CloudGuard: One policy engine for all clouds.
- CloudCheckr: Governance and cost optimization across clouds.
Best 5 CSPM Tools for Cloud Protection
Key Criteria When Choosing a CSPM Tool For Cloud Protection:
- Threat detection (beyond config scanning)
- Runtime workload visibility
- Cloud network traffic insights
- Alert correlation and prioritization
- Automated remediation or blocking
Here are the top 5 CSPM tools tailored for cloud protection:
- Aikido Cloud: Provides coverage from code-to-cloud and everything in between, as well as kubernetes. environments.
- CrowdStrike Falcon Cloud Security: CNAPP with best-in-class threat intel.
- Lacework: Polygraph engine detects misconfigs and anomalies together.
- Microsoft Defender for Cloud: Runtime + config threat visibility in Azure.
- Check Point CloudGuard: Combines posture with active threat prevention.
Best 5 CSPM Tools for AWS
Key Criteria When Choosing a CSPM Tool for AWS:
- Deep AWS API integration
- Support for AWS CIS/NIST frameworks
- Multi-account support
- Compatibility with native services (e.g., GuardDuty, Config)
- Low-latency misconfig detection
Here are the top 5 CSPM tools tailored for AWS:
- Aikido Cloud: Comprehensive AWS support, broad compliance coverage, and dev-centric.
- Prowler: Lightweight, CLI-first, and AWS-native.
- CloudSploit: Easy to deploy and open-source.
- Aqua Security: Extended AWS support + containers.
- CloudCheckr: Broad AWS compliance and cost insights.
Best 5 CSPM Tools for Azure
Key Criteria When Choosing a CSPM Tool for Azure:
- Native integration with Azure ecosystem
- Secure Score and Azure Security Benchmark support
- Coverage of Azure RBAC and Identity
- Automated remediation and alerts
- Compatibility with Sentinel and Defender XDR
Here are the top 5 CSPM tools tailored for Azure:
- Microsoft Defender for Cloud: First-party coverage with free tier.
- Aikido Cloud: Azure-ready CSPM platform with agentless scanning, real-time misconfiguration alerts, and AI-based remediation.
- Ermetic: Advanced identity posture management for Azure.
- Check Point CloudGuard: Multi-cloud visibility including Azure.
- Tenable Cloud Security: IaC and runtime scanning for Azure with drift detection.
Conclusion
Cloud Security Posture Management isn’t just a checkbox for audits, it’s the difference between a secure, scalable cloud and one that leaks sensitive data.
Whether you’re a startup founder looking for a free tool to harden your AWS account or a security lead at an enterprise managing multi-cloud environments, the right CSPM tool can make your job a whole lot easier.
Aikido Cloud caters to both startups and enterprises with a dev-first CSPM solution that delivers complete code-to-cloud coverage at an affordable price. No more context switching between tools, hours of manual configuration, or inflated budgets — just posture management done right.
Want less noise and more real protection? Start your free trial or book a demo with Aikido Cloud today.
FAQ
Does Aikido Cloud require agents or runtime sensors?
No. Aikido Cloud is completely agentless, it connects to your cloud environments using read-only APIs, so there’s nothing to install, no resource overhead, and no impact on workloads.
What compliance standards does it support out-of-the-box?
Aikido Cloud maps findings to SOC 2, ISO 27001, CIS Benchmarks, GDPR, NIST 800-53, and other frameworks. Reports can be exported for audits or integrated into compliance workflows.
Can Aikido Cloud detect IAM privilege escalation risks?
Yes. It can identify over-permissive IAM roles, unused privileges, and “toxic combinations” that could allow privilege escalation or lateral movement.
How does Aikido Cloud handle multi-cloud and multi-account environments?
You can connect multiple AWS, Azure, and GCP accounts under a single workspace. Aikido automatically normalizes data and provides unified visibility, posture scoring, and compliance tracking across all of them
How does Aikido Cloud handle sensitive data?
Aikido Cloud uses read-only access, does not modify configurations, and complies with strict data-handling and encryption policies, ensuring no customer data or secrets are stored or exposed.
You might also like:
{
"@context": "https://schema.org",
"@graph": [
{
"@type": "FAQPage",
"mainEntity": [
{
"@type": "Question",
"name": "What is Cloud Security Posture Management (CSPM)?",
"acceptedAnswer": {
"@type": "Answer",
"text": "Cloud Security Posture Management (CSPM) refers to tools that continuously monitor cloud infrastructure (AWS, Azure, GCP, etc.) for misconfigurations, compliance violations, and security risks:contentReference[oaicite:9]{index=9}. CSPM solutions compare your cloud settings against best practices and standards (like CIS Benchmarks, SOC 2, ISO 27001) and alert you to any issues:contentReference[oaicite:10]{index=10}. Instead of occasional cloud audits, CSPM tools provide ongoing, automated checks to ensure your cloud environment remains secure and compliant."
}
},
{
"@type": "Question",
"name": "Why are CSPM tools important?",
"acceptedAnswer": {
"@type": "Answer",
"text": "With modern organizations using multi-cloud and fast-paced DevOps, misconfigurations can easily slip through and expose critical assets:contentReference[oaicite:11]{index=11}. In 2025, cloud breaches are often due to preventable config mistakes. CSPM tools are essential because they catch issues like open storage buckets or overly permissive roles before attackers do:contentReference[oaicite:12]{index=12}:contentReference[oaicite:13]{index=13}. They also help enforce best practices and compliance in dynamic cloud environments where manual checks can’t keep up."
}
},
{
"@type": "Question",
"name": "What should I consider when choosing a CSPM tool?",
"acceptedAnswer": {
"@type": "Answer",
"text": "Key considerations include multi-cloud support (does it cover AWS, Azure, GCP, etc. in one tool?), the breadth of policies and benchmarks it checks, ease of deployment (SaaS vs. self-hosted), and integration with your workflows:contentReference[oaicite:14]{index=14}. Scalability and automatic asset discovery are important for enterprises – good CSPM tools will find new cloud resources on their own:contentReference[oaicite:15]{index=15}:contentReference[oaicite:16]{index=16}. Also consider if the tool provides remediation help or automated fixes for findings. In short, pick a CSPM that fits your cloud stack and security requirements, and that can grow with your environment."
}
},
{
"@type": "Question",
"name": "Are there free or open-source CSPM tools?",
"acceptedAnswer": {
"@type": "Answer",
"text": "Yes. For example, **CloudSploit** started as a standalone open-source project and provides agentless scanning of cloud environments for misconfigurations:contentReference[oaicite:17]{index=17}. Another is **Prowler**, an open-source tool focused on AWS security best practices and compliance checks:contentReference[oaicite:18]{index=18}. These free tools can be used for basic cloud posture auditing. Vendors like Aqua Security have also open-sourced components (CloudSploit, for instance) that you can use at no cost, though enterprise versions with more features are available."
}
}
]
},
{
"@type": "ItemList",
"itemListElement": [
{
"@type": "ListItem",
"position": 1,
"name": "Aikido Security",
"url": "https://www.aikido.dev/blog/top-cloud-security-posture-management-cspm-tools#1-aikido-security"
},
{
"@type": "ListItem",
"position": 2,
"name": "Aqua Security",
"url": "https://www.aikido.dev/blog/top-cloud-security-posture-management-cspm-tools#2-aqua-security"
},
{
"@type": "ListItem",
"position": 3,
"name": "BMC Helix Cloud Security",
"url": "https://www.aikido.dev/blog/top-cloud-security-posture-management-cspm-tools#3-bmc-helix-cloud-security"
},
{
"@type": "ListItem",
"position": 4,
"name": "Check Point CloudGuard",
"url": "https://www.aikido.dev/blog/top-cloud-security-posture-management-cspm-tools#4-check-point-cloudguard"
},
{
"@type": "ListItem",
"position": 5,
"name": "CloudCheckr (Spot by NetApp)",
"url": "https://www.aikido.dev/blog/top-cloud-security-posture-management-cspm-tools#5-cloudcheckr-spot-by-netapp"
}
]
}
]
}



