With modern software shipping daily whilst most pen tests happen every six months, organizations have long had limited visibility into their security posture.
Continuous pentesting flips the old model on its head. Instead of waiting for consultants to drop a PDF twice a year, security teams can now get ongoing attacker-style testing powered by automation and AI.
This is a game changer that will drastically reduce the number of exploitable vulnerabilities, such as Broken Access Control issues, including IDORs, which, according to the 2025 OWASP Top 10, are the #1 most critical risk and are present on average in 3.73% of all applications.
Below, we compare the top continuous pentesting tools and what they offer so you can choose the right fit for your stack and risk profile.
TL;DR
Among the continuous pentesting solutions reviewed, Aikido Security's Infinite stands out for its plug-and-play onboarding, robust compliance support, and the ability to run continuous attack simulations across the entire SDLC within development workflows.
Its agentic AI continuously performs attacks against source code, APIs, cloud resources, and containers, correlating vulnerabilities to identify attack paths.
By removing the traditional hurdles of pentesting, like scheduling, specialized security teams, and workflow disruption, Aikido Security allows teams to focus on building software while maintaining constant, automated security coverage.
What is Continuous Pentesting?
Continuous penetration testing or Continuous Attack Surface Penetration Testing (CASPT) as some people know it is a security practice that involves the ongoing attempts to find and exploit vulnerabilities in an organization's IT estate.
Often referred to as agile pentesting due to mirroring the iterative nature of agile development, continuous pentesting shift lefts pentesting throughout the development process.
Continuous pentesting is not about repeatedly scanning the entire application.
Modern continuous pentesting platforms track what has changed between deployments and focus testing effort only on new or modified code, workflows, and infrastructure. This allows enterprises to run attacker-style testing continuously without reintroducing noise, cost, or operational risk on every deployment.
The goal: Identify vulnerabilities before real attackers do, and do it earlier, more frequently, and at scale.
Continuous Pentesting vs Traditional Pentesting
Traditional penetration testing assumes a relatively static system. Tests are scheduled periodically, findings are delivered as a report, and results age quickly as code changes.
Continuous pentesting differs in three key ways:
- Testing runs automatically or on change, not just annually or quarterly
- Assumptions are revalidated continuously, not just discovered once
- Findings reflect current behavior, not historical snapshots
The goal is not to replace traditional pentests, but to close the gap between them, where risk often accumulates unnoticed.
Continuous Pentesting vs AI Pentesting
A common question teams have is what’s the difference between Continuous penetration testing and AI penetration testing. In a nutshell, continuous pentesting is all about when and where testing happens while AI pentesting, on the other hand, is more about how the testing is done; using AI to simulate an attacker’s behaviour and chain issues together.
In mature platforms, continuous pentesting also builds system memory over time. Instead of treating each test as a clean slate, the platform reuses learned workflows, permissions, and attack paths from previous runs. This allows testing depth and accuracy to increase as the application evolves.
Why Continuous Pentesting Matters for Modern Applications
- Continuous retesting and fix validation: Continuous pentesting doesn’t stop once an issue is fixed. Attack simulations automatically reattempt previously discovered exploit paths and actively try to bypass applied mitigations. This helps teams catch regressions and weak fixes that would otherwise survive until the next scheduled audit.
- Detection of emergent and intermittent vulnerabilities: Modern applications are probabilistic and stateful. Some vulnerabilities only appear after specific sequences of actions, depend on timing or state transitions, or emerge when features interact. Continuous pentesting increases the likelihood of detecting these issues by repeatedly exercising real attacker behavior instead of relying on one-off assessments.
- Continuous evidence for compliance and assurance: Continuous pentesting generates an ongoing record of testing activity, reproducible findings with validation steps, and evidence that controls are exercised consistently.
Instead of relying on static, point-in-time PDFs, continuous pentesting creates an evolving evidence trail:
- tested attack paths,
- validated exploit steps,
- timestamps, and
- retest history.
This gives security teams defensible proof that controls are continuously exercised, which aligns better with how modern auditors and regulators assess risk.
Benefits of continuous penetration testing
Implementing continuous penetration testing offers measurable advantages that go beyond simple risk reduction:
- Increased visibility and real-time posture: Continuous pentesting gives you a near real-time view of possible attack paths. Instead of wondering whether last night’s deployment introduced a critical flaw, you get rapid feedback as vulnerabilities appear which drastically reduce mean time to remediate (MTTR) compared to in-frequent pentests.
- More cost-effective than breach-driven security: Yes, moving to continuous testing is an investment. But it’s cheaper than incident response, legal fees, and reputational damage. The long term savings from remediation, developer productivity, and uptime far outweigh the upfront costs.
- Continuous compliance, not last-minute audit panic: The cost of non-compliance is enormous and I know your organization won’t want to spend their profits on fines. Regulatory frameworks such as HIPAA, PCI-DSS, and GDPR increasingly demand rigorous and regular security assessments. Continuous pentesting helps you achieve that.
- Better alignment with DevOps and platform engineering practices: DevOps and platform engineering practices require shift-left. Continuous pentesting enables you to shift-left pentesting, which is the most comprehensive type of software testing. A secure internal developer platform results in secure applications in production.
Continuous Pentesting vs Other Types of Penetration Testing
Automated scanners identify signals. AI pentesting reasons about system behavior. Continuous pentesting ensures that reasoning is applied as the system changes. Any approach missing one of these layers will struggle to keep pace with modern application risk.
What to Look for in Continuous Pentesting Tools
Selecting the right continuous pentesting tool isn't just about features, it's about finding the solution that fits your team's workflow and security needs.
Continuous pentesting platforms must be explicitly designed for safe, scoped execution, with built-in controls to prevent unintended impact while still validating real attacker behavior.
Here are a few criteria you should consider when choosing one:
- End-to-End Coverage: Continuous pentesting should run in the pipeline and your tool of choice must provide end-to-end attack path analysis.
- Workflow and state awareness: Some vulnerabilities only appear after specific sequences of actions happen, depend on timing or state transitions, or emerge when features interact. Your choice continuous pentesting tool should be able to chain these actions together to give better results over time in every system change.
- Hosting Options: Can you choose the region your tool is hosted? Look for tools that offer multi-region hosting. Remember you want a tool that helps you stay compliant, not break laws.
- Deployment: How long does it take to deploy? Do you need a dedicated solutions architect to configure it?
- Risk Prioritization: Can it apply context when analyzing risks? How frequent are its false positives? Platforms like Aikido Security filter out over 90% of false positives.
- Product Maturity: How many organizations use the tool? What do they have to say about it? The shining new kid on the block with all the hype and no track record might not be the best choice for you.
- Integration: Is it platform agnostic? Does it fit into your current DevOps workflow? For example, CI/CD pipeline security is crucial for rapid deployments.
- Pricing: Can you predict how much it will cost you in the next 1 year?
- User Experience: Is it intuitive for both devs and security professionals? Look for tools that are built with a dev-first mindset.
Why continuous pentesting is typically adopted by enterprises
Continuous pentesting requires sustained system context, workflow awareness, and safe execution at scale. While startups often use AI pentesting on demand for fast feedback or compliance, enterprises benefit most from continuous programs that validate risk across frequent deployments, complex permissions, and long-lived systems.
Top 6 Continuous Pentesting Tools
1. Aikido Security
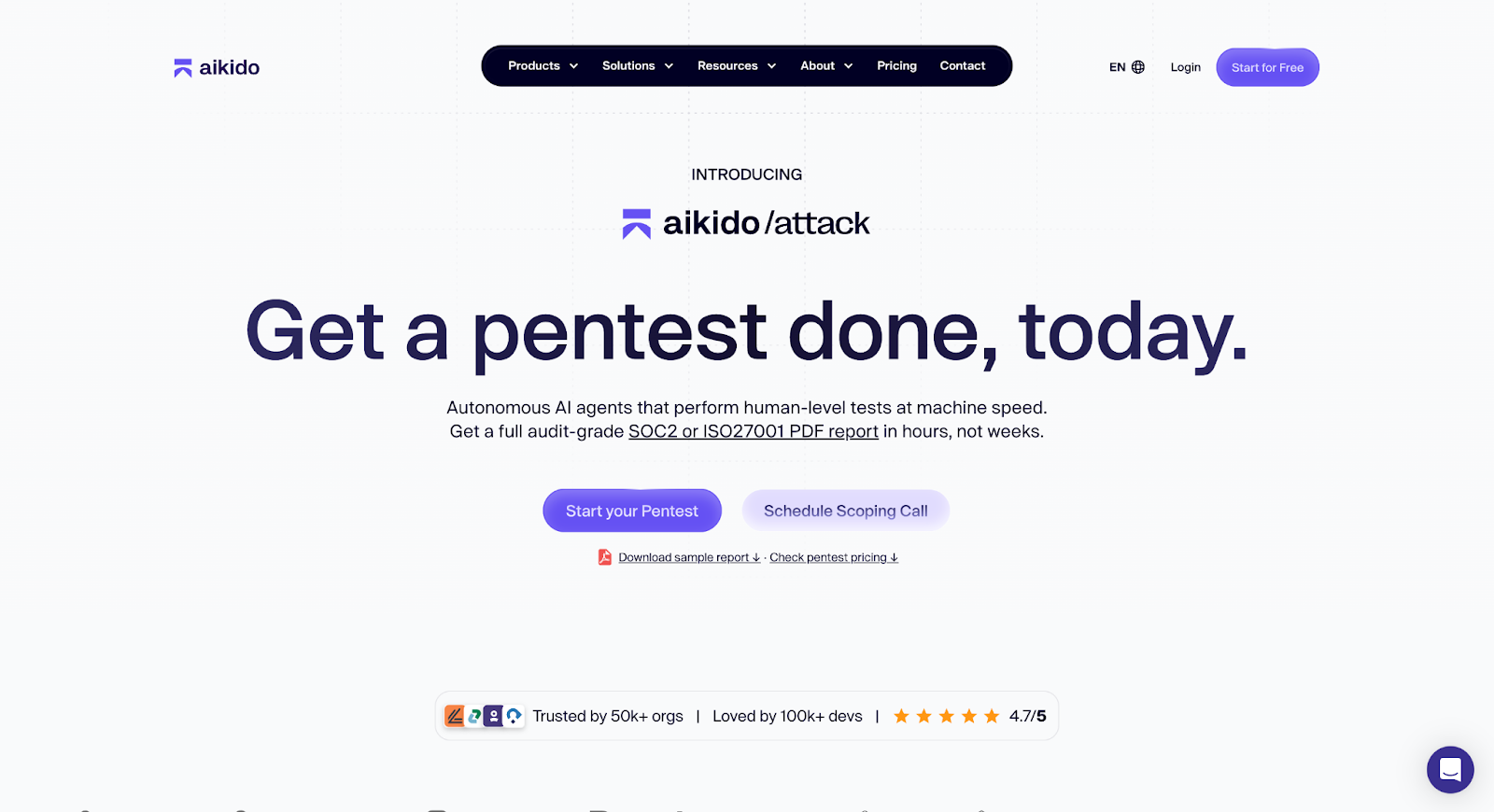
Aikido Security’s continuous pentesting offering Aikido Infinite is built directly on its AI pentesting engine.
Aikido Infinite continuously reduces exploitable risk at every software release by automatically testing applications, validating findings, and fixing issues as part of the software lifecycle. Instead of producing reports or backlogs, Infinite closes the loop between attack and remediation so security work no longer interrupts engineering teams.
Because Aikido’s platform has a unified view across code, cloud, and infrastructure, Infinite has the context and access required to accurately test real-world attack paths and resolve issues at release speed — without manual intervention.
Aikido Infinite represents Aikido's vision for self-securing software: systems that protect themselves as they are built and deployed, so teams no longer have to choose between shipping quickly and shipping safely.
Key characteristics of this approach include system-level reasoning across runs, validation of chained attack paths rather than isolated alerts, safety designed for continuous execution, validation-first output, and audit-ready evidence.
Aikido Security goes further by offering auto-remediation features such as automated pull requests, one-click fixes, inline security suggestions, and built-in compliance mapping (HIPAA, SOC 2, ISO 27001 and much more).
Every attack simulation is instantly converted into audit-ready reports, and when it’s time for formal certification, you can work with a trusted Aikido Security partner to validate and rubber-stamp the findings at a fraction of the usual cost.
With all of this in place, Aikido Security ensures your attack surface stays protected at all times, with or without a dedicated pentesting team.
Key Features:
- Agentic AI: Aikido Security simulates attacker tactics to validate exploitability, prioritize real attack paths, and produce reproducible exploit proofs.
- Broad coverage: Covers every aspect of the SDLC from cloud configuration scanning to advanced secrets detection.
- Noise reduction: Aikido auto-triages results to cut out the noise. If an issue isn’t exploitable or reachable, it’s silenced automatically.
- Developer-friendly UX: Provides clear, actionable dashboards your team will actually use.
- Compliance mapping: Supports major frameworks like SOC 2, ISO 27001, PCI DSS,GDPR, and much more.
- AI-driven Risk Prioritization: Uses context-aware filtering and AI triaging to suppress up to 90% of false positives.
- Product maturity: Aikido Security has established itself as a mainstay in the cybersecurity market, with 50,000+ customers already across their well-established base of code, cloud and runtime security.
- Agentless Setup: Connects to GitHub, GitLab, or Bitbucket using read-only APIs. No agents, installations, or code changes required.
- End-to-End Attack Path Analysis: Aikido Security uses AI to correlate related vulnerabilities and surface the highest-risk attack paths across your environment.
Pros:
- Developer friendly UX
- Centralized reporting and compliance templates
- Mobile and binary scanning support (APK/IPA, hybrid apps).
- Predictable pricing
- Agentic Pentesting
- Broad language support
- AI-powered filtering
- Cross-platform support
Continuous Pentesting Approach:
Aikido Security’s continuous pentesting approach continuously simulates attacker workflows across the SDLC without disrupting development. It offers teams auto-remediation, AI-powered vulnerability correlation, and audit-ready reporting for all identified vulnerabilities.
Pricing:
Aikido Security’s plans begin at $300/month for 10 users.
- Developer (Free Forever): Supports teams of up to 2 users. Includes 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Covers 10 repos, 25 container images, 5 domains, and 3 cloud accounts.
- Pro: Ideal for mid-sized teams. Includes 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Includes support for 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Offers are also available for startups (with a 30% discount) and enterprises.
Gartner Rating: 4.9/5.0
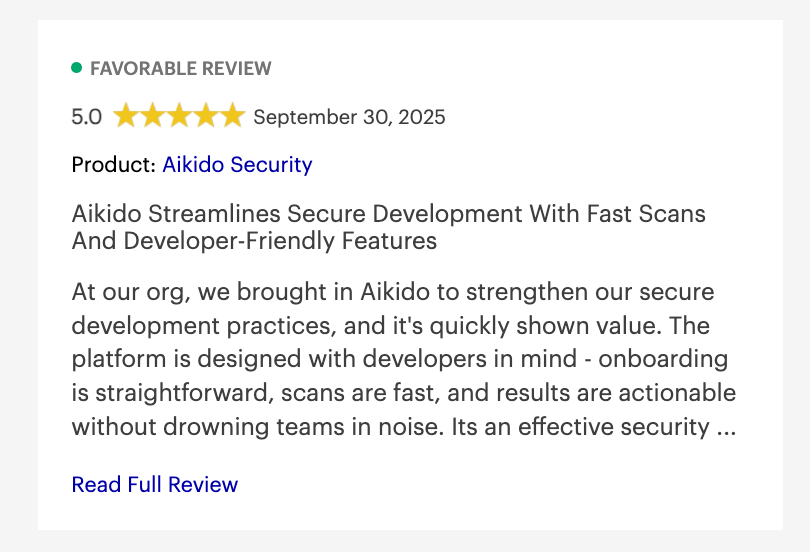
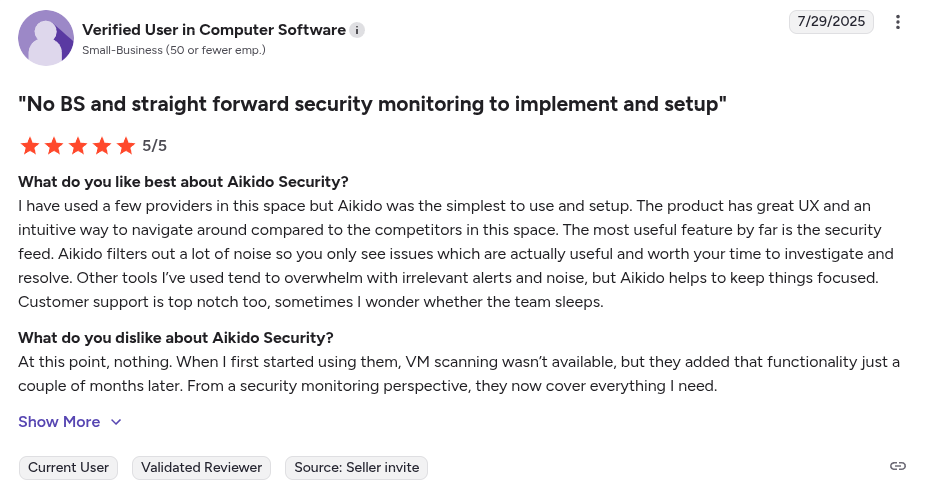
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra, Getapp and SourceForge
2. Hadrian
Hadrian is an autonomous continuous pentesting security platform that uses AI agents to perform reconnaissance, vulnerability discovery, and exploitation simulation on external attack surfaces in real time.
Key Features:
- Autonomous Agents: Hadrian uses AI models trained by expert pentesters to mimic real attacker thought processes and TTPs (Tactics, Techniques, and Procedures).
- Automated Attack Surface Management (ASM): Continuously scans domains, assets, subdomains, cloud services, and exposed interfaces.
- Integrations: Provides API-based integrations for ticketing tools and development workflows
Pros:
- Agentless setup
- Event-based pentests
Cons:
- Less suited for internal pentesting
- Primarily enterprise focused
- Its initial scans can be slow
- Users have reported gaps in its documentation
- Users have reported performing additional tuning to reduce noise
Continuous Pentesting Approach:
Hadrian continuously discovers new or changed external assets with its continuous attack surface management tool, and automatically runs AI-driven pentests against them, validating exploitable paths and updating findings in real time.
Pricing:
Custom pricing
Gartner Rating:
No Gartner review
Hadrian Reviews:
No independent user generated review.
3. Cobalt
Cobalt is a continuous pentesting platform that allows development teams to spin up pentests on demand, as soon as code changes or new releases occur, and provides access to a vetted community of pentesters.
Key Features:
- Comprehensive and Agile Testing: Teams can request full‑scope pentests or smaller, focused ones, targeting changes, new releases, or recent code updates.
- Collaboration Support: It provides a dashboard for findings, reports, retests, and communications.
- Integration: Integrates with common developers and issue‑tracking tools ,and supports API‑based workflows.
Pros:
- Attack surface management
- Strong customer support
Cons:
- Enterprise focused
- Pricing can become expensive
- Lacks automated remediation
- Users have reported its API integration as lacking when compared to other solution
- Limited filtering and report export features
Continuous Pentesting Approach:
Cobalt’s continuous pentesting approach lets development teams trigger targeted pentests at every major code update or deployment. And offers a vetted community of pentesters for more comprehensive pentests
Pricing:
Custom Pricing
Gartner Rating: 4.5/5.0
Cobalt Reviews:
4. Evolve Security
Evolve Security is a security platform that provides continuous penetration testing as a managed service (PTaaS). It is primarily known for its proprietary continuous pentesting platform, “Darwin Attack”.
Key Features:
- Collaboration Portal: Its Darwin Attack platform serves as a central hub for communication between a client's team and pentesters
- Risk Acceptance: It allows teams to mark specific, low-risk vulnerabilities as "risk accepted" preventing the same issue from being re-evaluated in future assessments.
Pros:
- Context-Aware records
- Supports common CI/CD platforms
- Strong customer support
Cons:
- Enterprise focused
- High alert volume
- Steep learning curve
- Initial setup and configuration is complex
- Lacks automated remediation features
- Users have reported it as feeling more like a vulnerability scanner than a pentesting tool
Continuous Pentesting Approach:
Evolve Security’s continuous pentesting approach combines automated monitoring with human expertise. It constantly maps external attack surfaces to detect changes, and prompts pentesters to investigate and validate high‑impact findings.
Pricing:
Custom pricing
Gartner Rating: 4.1/5.0
Evolve Security Reviews:
5. BreachLock
BreachLock is a continuous security testing platform that uses automation scanners and expert pentesters to help organizations identify vulnerabilities across their systems.
Key Features
- Attack Surface Management (ASM): BreachLock continuously discovers and maps both internal and external internet-facing assets.
- Integration: Its findings can be fed into common issue trackers and CI/CD platforms
- Hybrid Testing Model: It combines AI-powered automation with certified human experts to detect complex business logic flaws and validate all findings.
Pros:
- Broad coverage
- Clear Remediation Guidance
- Compliance support
Cons:
- False positives
- It can be expensive when scaling
- It can be difficult to track attack surface monitoring findings
- Users have reported its interface as slow and clunky
- Users have reported limited customization options for reports
Continuous Pentesting Approach:
BreachLock’s continuous penetration testing approach combines automated monitoring and human-led validation to perform ongoing context-aware pentests of web applications, APIs, and cloud assets
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
BreachLock Reviews:
6. Terra Security
Terra Security is an agentic-AI powered continuous penetration-testing platform (PTaaS). It combines specialized AI agents with expert pentesters to run continuous, context-aware web application and API penetration tests.
Key Features:
- Agentic AI Swarm: Terra Security uses specialized AI agents that are designed to think and act like human ethical hackers to autonomously explore and test applications.
- Change-Based Testing: Its scans are triggered by events like deployments, code modifications, or new endpoints
Pros:
- Context-Aware tests
- Actionable remediation insights
Cons:
- Steep learning curve
- Primarily enterprise focused
- Limited scope beyond web applications
- It is a relatively new platform
Continuous Pentesting Approach:
Terra Security's continuous penetration testing approach uses a hybrid model of agentic AI and human expertise to provide real-time, context-aware web-application pentests.
Pricing:
Custom pricing
Gartner Rating:
No Gartner review
Terra Security Reviews:
No independent user generated review.
Comparing the Best 6 Continuous Pentesting Tools
To help you compare the capabilities of the continuous pentesting tools above, the table below summarizes each tool's strengths and limitations along with their ideal use case.
Conclusion
Continuous pentesting is becoming essential because static security testing no longer matches dynamic systems.
The future of penetration testing is not simply faster or cheaper assessments. It is continuous, context-aware validation of how applications behave under real attacker pressure.
By combining AI pentesting with continuous execution, platforms like Aikido Security enable security teams to move from snapshot-based assurance to ongoing understanding of risk.
Want less noise and more real protection? Start your free trial or book a demo with Aikido Security today.
FAQ
Why is continuous pentesting becoming important in modern cybersecurity?
Continuous pentesting helps teams keep up with constantly changing cloud environments, shifting attack surfaces, and rapid deployment cycles. Instead of waiting for quarterly tests, organizations get ongoing validation, real-time detection of exploitable risks, and faster remediation loops.
Modern platforms like Aikido Security make this process automatic and developer-friendly so security testing happens continuously without slowing engineering teams down.
What are the common challenges faced during continuous pentesting?
Teams often struggle with high false-positive rates, incomplete coverage, environment drift, production safety concerns, and the operational overhead of managing multiple tools. There’s also the issue of prioritizing which findings truly matter. Solutions like Aikido Security address this by using its AI engine to correlate findings, reducing noise, and focusing on truly exploitable vulnerabilities so teams work on the highest-priority issues first.
What is the difference between AI penetration testing and continuous penetration testing?
Both approaches use AI. AI penetration testing focuses on automating tasks traditionally performed by human pentesters to make individual tests more efficient and thorough. Continuous pentesting on the other hand, goes further by automating the frequency of tests, allowing organizations to continuously assess their security posture and remain secure at all times.
How do continuous pentesting tools integrate with DevOps or CI/CD pipelines?
They plug into pipelines as automated steps that run pre-merge, post-deploy, or on a scheduled basis. Results are then pushed directly into pull requests, issue trackers, or dashboards so developers can remediate within their existing workflows. Platforms like Aikido Security are designed around this workflow-first approach, offering CI/CD integrations, API triggers, and automated gating for high-risk vulnerabilities.
How do open-source continuous pentesting tools compare to commercial ones?
Open-source continuous pentesting tools offer flexibility and lower cost but require more manual configuration, tuning, and maintenance. Commercial platforms on the other hand typically provide stronger automation, deeper attack simulation, better reporting, and a cleaner developer experience. Many teams combine both approaches, using open-source tools for specific checks while relying on commercial solutions like Aikido Security for risk correlation, automation, and noise reduction.
What metrics and reports do top continuous pentesting tools provide to track vulnerabilities?
Common metrics include vulnerability counts by severity, exploitability, asset coverage, MTTR (mean time to remediate), and trend lines for new and resolved findings. Robust platforms also provide remediation guidance, compliance-ready reports, and attack-path visualizations. Tools like Aikido Security surface these insights in streamlined dashboards and development workflow so teams can track their threat landscape and prioritize effectively.
You Might Also Like:



