For decades organizations relied only on manual penetration testing to secure their applications. But as software development moved past the waterfall methodology, the idea of automated pentesting came into existence.
Sadly, automated pentesting tools never lived up to the "automated" tag and are merely scanners that don't come close to the effectiveness of manual penetration testing methods.
With the recent advancement in AI however, we can finally replicate the context-aware depth of human pentests while maintaining the speed and consistency of automated scans.
According to Aikido Security's 2026 State of AI in Security & Development report, 97% of organizations are considering adopting AI in penetration testing, and 9 out of 10 believe AI will eventually take over the penetration testing field.
In this guide, we’ll break down the strengths and limitations of manual and automated pentesting, and examine how AI-powered pentesting help teams achieve deeper coverage, faster results, actionable insights and improved security posture.
TL;DR
Aikido Security stands out in head-to-head comparisons against manual pentesters, automated pentest tools, and other AI-pentesting platforms in technical evaluations and real-world pilots.
Aikido Security’s Attack module uses agentic AI to simulate attacker behavior across applications, APIs, cloud environments, containers, and runtime. It not only identifies exploitable vulnerabilities but also analyzes how they can be linked together into full attack paths, all without requiring full source-code access.
Side-by-side tests show Aikido Security's is more efficient than human pentesters, delivering deeper coverage, faster detection, and more consistent results.
Aikido Security Attack is available in three fixed tiers— Feature pentest, Standard pentest, and Advanced pentest—with the Advanced pentest providing the most thorough coverage.

What is Penetration Testing?
Penetration testing (also known as pentesting) is the process of simulating authorized cyberattacks against systems, networks, or applications to identify exploitable vulnerabilities (such as cross-site scripting, outdated software versions, insecure communication channels).
The goal: Find security vulnerabilities before real attackers can exploit them.
By staging these controlled attacks, pentesters help teams uncover critical vulnerabilities, analyse system behaviour during breaches, and improve their overall security posture.
There are three different types of penetration testing:
- Manual Pentesting: Pentesters use their experience and intuition to explore systems for complex or business logic vulnerabilities.
- Automated Pentesting: Uses software tools and predefined scripts to scan for known vulnerabilities.
- AI Pentesting: Leverages machine learning to automate vulnerability discovery and threat simulation.
What is Manual Penetration Testing?
Manual penetration testing is a hands-on security assessment carried out by offensive security experts called pentesters or ethical hackers. These pentesters employ various tactics, techniques, and procedures (TTPs) that malicious hackers might also use to analyze the target of evaluation (ToE): systems, applications, and networks, and simulate attack scenarios to identify vulnerabilities and security flaws..
This process typically consists of the following phases:
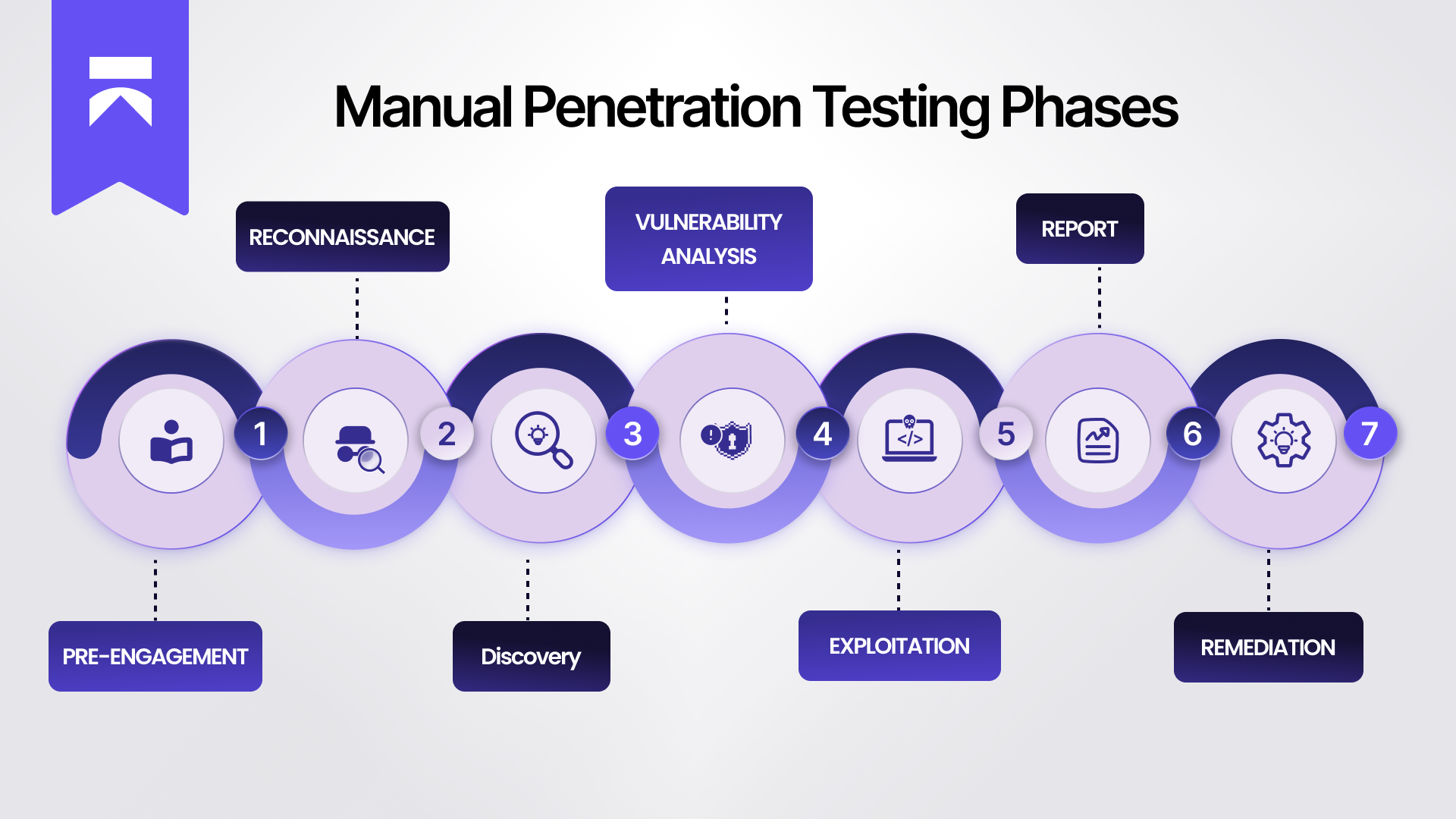
1. Pre-Engagement
The pentester works with the client to define the scope, objectives, rules of engagement, and information about the target.
2. Reconnaissance
The pentester gathers as much information as possible about the target from public and private sources (e.g., network details, employee information, technology stack) to map out the potential attack surface.
3. Discovery
Pentesters use various tools and techniques to interact with the target and identify specific issues such as open ports, exposed services, outdated software versions, and other attack surfaces.
4. Vulnerability Analysis
This phase involves both static analysis (SAST) on codebases and dynamic analysis (DAST) on running systems to identify potential weaknesses.
5. Exploitation
Using information gathered from the earlier phases, the pentester attempts to exploit identified weaknesses in a controlled manner to validate real-world risk and impact.
6. Reporting
The pentester documents all findings, including the vulnerabilities identified, the exploitation steps taken, and any data accessed, and presents a clear report to the organization.
7. Remediation
The pentester removes any tools, backdoors, or configurations left behind during testing to ensure the system is returned to a secure state. The organization’s security team then fixes the identified issues, after which a retest may be conducted to verify that all vulnerabilities have been successfully resolved.
Core Strengths of Manual Penetration Testing:
- Contextual Understanding: Pentesters can analyse complex business logic errors, user behavior, and unique configurations for flaws (complex access control issues, multi-step attack chains)
- Intuition: Human pentesters can adapt their methods in real-time, to mimic an actual attacker, and develop custom exploits (zero-day vulnerabilities).
- Accuracy: Findings are human-validated, resulting in fewer false positives and more in-depth remediation guidance.
Key Weaknesses of Manual Penetration Testing:
- Tests can be time-intensive taking weeks for reports
- It is not scalable
- Comprehensive pentests are expensive
- Pentests are usually conducted once or twice a year, meaning organizations are only conducting them as a checkbox rather than a strategic initiative.
- Limited coverage of large, dynamic environments
- Results vary between testers and projects
- Misses vulnerabilities outside pre-defined test scopes
What is Automated Penetration Testing?
The so-called automated pentesting with scanners improved efficiency but never delivered true intelligence. It is fast but superficial. They rely on signatures and rules, detecting known issues without understanding how vulnerabilities connect or what’s actually exploitable.
Automated pentesting can be useful, but it ultimately isn’t pentesting. Proper pentesting relies on human intuition and expertise to simulate real attacks not checklist of vulnerabilities. It involves:
- Connecting vulnerabilities to identify attack chains
- Exploiting logic and configuration errors
- Stress-testing authorization and workflows
- Adjusting tactics as new information (vulnerabilities, threat vectors) are confirmed
Seeing automated penetration testing as we know has no “intelligence”, it can’t fulfil the requirements of a penetration test.
Core Strengths of Automated Penetration Testing:
- Cost Effective: Costs per scans are low, making it sustainable for frequent scans
- Consistency: Follows predefined scripts, ensuring consistent and reproducible scans
- Integrations: Supports integration with common CI/CD platforms such as GitHub, GitLab and BitBucket
Key Weaknesses of Manual Penetration Testing:
- High false-positive rates
- Lacks the ability to simulate real attack behavior
- Limited reasoning and prioritization
- Focuses only on predefined vulnerability types
- It is more of a vulnerability scanner than pentesting tool
- Does not provide detailed remediation guidance
Manual vs Automated Pentesting: When to Use AI
What is AI Penetration Testing?
AI-powered pentesting has replaced both manual and automated approaches by combining the depth of human reasoning with the speed and precision of automation.
It uses Artificial intelligence to simulate hacker-like behaviour and automates key parts of penetration tests such as reconnaissance, vulnerability discovery, exploit simulation, and risk prioritization.

Unlike traditional pentesting, AI-driven pentests run continuously, adapting to your environment in real-time. They automatically map your attack surface (domains, IPs, cloud assets, APIs), then attempt a series of safe attacks: SQL injection attempts, weak password exploits, privilege escalation in networks, to validate risks and their exploitability.
Core Strengths of AI Penetration Testing:
- Detects vulnerabilities that human testers may miss
- Simulates realistic, end-to-end attack paths across code, containers, and cloud
- Context-aware analysis automatically filters out false positives
- Continuously learns and adapts in real-time
- Scales instantly across complex, fast-changing infrastructures
When to Use Each Approach to Pentesting
Manual Pentesting
- Still occasionally required for regulatory or compliance reasons (e.g., PCI DSS, government mandates).
- Useful for highly specific, human-driven scenarios such as social engineering or physical security testing.
- Final verification of critical systems such as banking systems and databases
Automated Pentesting
- Suitable for quick, routine scans when teams only need surface-level visibility.
- Can supplement continuous integration workflows but lacks depth or reasoning.
- Environments with large attack surfaces that require frequent scans
- Immediate feedback in the development workflows
AI-Powered Pentesting
- The replacement for both manual and automated approaches.
- Delivers attacker-level reasoning with full context across code, infrastructure, and cloud.
- Continuously adapts to new threats and environments.
- Scales without sacrificing accuracy or requiring human triage.
- Complex attack path mapping and prioritization
- Verifiable, exploit-backed proofs
- Continuous pentests with context-aware remediation guidance
In Practice:
AI pentesting tools like Aikido Security now cover everything manual and automated pentesting were designed to do,only faster, more accurately, and at scale.
The Pentesting Future Is AI
With all this said, it’s clear that penetration testing can no longer rely solely on manual or scripted approaches. Modern software environments demand continuous analysis that keeps pace with development cycles, not hinders it. AI-powered pentesting addresses this by providing human-like insight while scaling across applications, APIs, and cloud workloads.
Aikido Security supports this shift by combining agentic AI for attack simulation, automated vulnerability linking, and automated recommendations, helping teams achieve stay ahead of threat without slowing down development.
Want to see how AI can elevate your pentesting workflow? Try Aikido Security in minutes.
FAQ
How do manual and automated pentesting approaches compare in terms of accuracy?
Manual pentesting provides deeper, context-driven insights because skilled testers can spot logic flaws, chain common vulnerabilities (cross-site scripting, access controls), and interpret behaviors in ways automated tools often cannot. However, its accuracy depends heavily on the tester’s expertise and available time. On the other hand, automated pentesting is more scalable and consistent, but may introduce false positives or miss complex, multi-step attacks.
How does automated penetration testing work?
Automated pentesting relies on scanners, crawlers, and scripted attack modules that simulate known attacker techniques across applications, systems, and networks. These tools identify outdated software, misconfigurations, exposed services, and common vulnerabilities at high speed and across large environments. When paired with AI- pentesting platforms like Aikido Security, automated workflows become more intelligent and adaptive.
What are the common tools used in automated pentesting?
Automated pentesting often involves tools like OpenVAS, Nikto, Nmap, and other vulnerability discovery engines. These tools detect known vulnerabilities, configuration issues, and exposed services across large environments. However, they still require careful interpretation to separate meaningful risks from noise. AI-driven pentesting like Aikido security helps filter results, improving prioritization.
What skills are required for manual penetration testing?
Manual pentesting requires mastery of networking, operating systems, web technologies, scripting, exploitation techniques, reconnaissance strategies, and advanced security tooling. Despite its depth, manual testing benefits significantly from automation by reducing repetitive tasks especially when paired with platforms offering AI-powered pentesting capabilities like Aikido Security.
How can combining manual and automated pentesting improve security assessments?
Combining manual and automated pentesting produces thorough and reliable assessments. Automation delivers continuous, broad coverage, while manual testers uncover logic flaws, chained exploits, and high-impact vulnerabilities that automated scanners often miss. AI-driven pentesting like Aikido Security this combination through increased speed and depth by correlating findings, reducing false positives, and identifying patterns that neither method can fully capture alone
You Might Also Like:



