Application security holds significant importance as cyber threats grow more sophisticated. Developers must protect applications from vulnerabilities and attacks that threaten sensitive data and disrupt business operations.
Perimeter-based solutions such as web application firewalls (WAFs) and network intrusion detection systems (IDS)may fail to protect against zero-day exploits or complex attack vectors targeting application runtime environments. This may sound far-fetched until you take into account that 32% of exploited vulnerabilities are zero-days.
Runtime Application Self-Protection (RASP) tools address these challenges. RASP tools proactively secure applications by monitoring behavior and blocking attacks in real-time, without major code changes or performance impact.
In this post, we’ll walk through runtime application security, what it is, how it differs from traditional web application firewalls, why developers still need it in 2026, and some of the best tools on the market right now.
TL;DR
Among the RASP solutions reviewed, Aikido Security secures the #1 spot thanks to its ability to provide real-time threat detection with near-zero latency, while its AI engine correlates and prioritizes issues at runtime. This allows teams to detect active threats and fix issues at the source across microservices, APIs or containerized workloads.
The result? Continuous runtime protection that proactively prevents exploits without impacting application performance.
For both startups and enterprises Aikido Security’s Zen pilots consistently stand out thanks to its AI driven risk prioritisation, continuous runtime protection and minimal impact on application performance.
What is a RASP Tool?
Runtime Application Self-Protection (RASP) tools are in-process security mechanisms that instrument application runtimes to observe execution flow and prevent exploitation.
This approach enables real-time detection and blocking of attacks based on actual application behavior rather than predefined signatures alone.
By embedding security controls into the application, RASP detects and prevents various vulnerabilities and threats in real-time. This includes common attacks like SQL injection, cross-site scripting (XSS), and remote code execution.
RASP tools also defend against zero-day exploits that leverage host-level vulnerabilities such as the file system, installed libraries, or underlying system components, threats that past perimeter defenses were not designed to account for.
WAF vs RASP
WAFs were built in a time where applications sat behind a clear network perimeter and deployments happened infrequently. This worked well when infrastructure was static and predictable.
RASP, on the other hand, was built with modern application architecture in mind. By embedding directly into the application runtime, RASP understands execution context from the inside, seeing what the code is doing, what's normal, and what's not.
Differences between WAF and RASP
Why Developers Need RASP Tools in 2026
Cybersecuritypresents unique challenges in 2026. As threats evolve, traditional security measures often lack the agility to address emerging vulnerabilities, as well as zero-day exploits. This gap calls for solutions capable of offering real-time protection. RASP tools embed security controls directly within applications, allowing immediate detection and interception of malicious actions.
These tools play a vital role in safeguarding applications through active threat monitoring during runtime. By analyzing application behavior and identifying potential threats, RASP tools strengthen security frameworks and help developers meet compliance mandates. In sectors with strict data protection regulations, RASP tools are crucial for mitigating risks associated with data breaches and unauthorized access.
Incorporating RASP tools into the development lifecycle enables developers to innovate without compromising security. These tools integrate smoothly with existing development environments, ensuring security enhancements do not disrupt workflow. As a result, development teams can focus on creating advanced applications, confident that security needs are managed and maintained.
In a previous study we evaluated various firewalls, measured latency as well as false positives
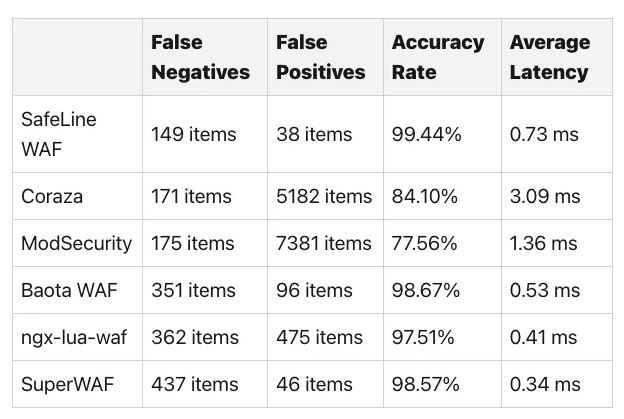
While we love to dive into the differences and tradeoffs between WAFs, developers shouldn't need to. RASP tools enable developers to focus on shipping while their runtime stays secure. Checkout our full evaluation of defending against zero-day vulnerabilities in Nodejs
Top 6 RASP Tools
1. Aikido Security

Aikido Security's RASP solution, Zen, uses advanced machine learning to enhance application defense, instantly identifying and mitigating threats to ensure robust security. It provides deep visibility into potential vulnerabilities and attack vectors, enabling developers to strengthen security measures effectively. Integration with popular development environments is smooth, allowing developers to bolster security features without interrupting their development process.
Key features:
- Runtime Behavior Analysis: Continuously monitors in-process application behavior to detect anomalous execution patterns and active exploitation attempts in real time.
- Active Attack Prevention: Automatically blocks common application-layer attacks such as injection flaws, insecure deserialization, and remote code execution before they impact application logic.
- Context-Aware Detection: Uses runtime context to distinguish between legitimate application behavior and malicious activity, helping reduce false positives compared to rule-based approaches.
- Developer-Friendly Integration: Integrates directly into development and runtime environments, enabling security controls to be applied without requiring significant code changes or workflow disruption
Pros:
- Developer focused, meaning developers can easily integrate into existing codebases
- Runtime aware
- Supports major programming languages
- Zero third party key access, respects your privacy
- Embedded libraries for reduced false positives
- Reduced setup time via one command install
- Minimal performance impact
- Can form part of a broader security platform that collapses traditional boundaries between SAST, DAST, SCA, and other security acronyms.
Pricing:
All paid plans starting from $300/month for 10 users
- Developer (Free Forever): Free for up to 2 users. Supports 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Supports 10 repos, 25 container images, 5 domains and 3 cloud accounts.
- Pro: Supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Supports 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Custom offerings are also available for startups (30% discount) and enterprises.
Gartner Rating: 4.9/5.0
2. Contrast Protect
Contrast Protect by Contrast Security, is a versatile RASP solution supporting a broad range of programming languages and frameworks. It uses machine learning techniques to detect emerging threats and adjust defenses, reducing false alerts. The platform offers comprehensive analytics and reporting, equipping developers with the information to address vulnerabilities swiftly and improve application fortification.
Key features:
- Continuous Runtime Protection: Provides in-process security monitoring across supported languages and frameworks, observing application behavior throughout execution in production environments.
- Active Exploit Detection and Blocking: Automatically identifies exploitation attempts and blocks malicious activity in real time, helping prevent successful attacks before they impact application logic.
Pros:
- Broad language support reduces tool sprawl across your tech stack
- Integrates with CI/CD pipelines
Cons:
- Sophisticated monitoring may introduce performance overhead in high-throughput applications
- Cross-language coverage might require more initial configuration than single-ecosystem tools
- Initial configuration could increase learning curve
Pricing:
Contact support
Gartner Rating: 4.7/5.0
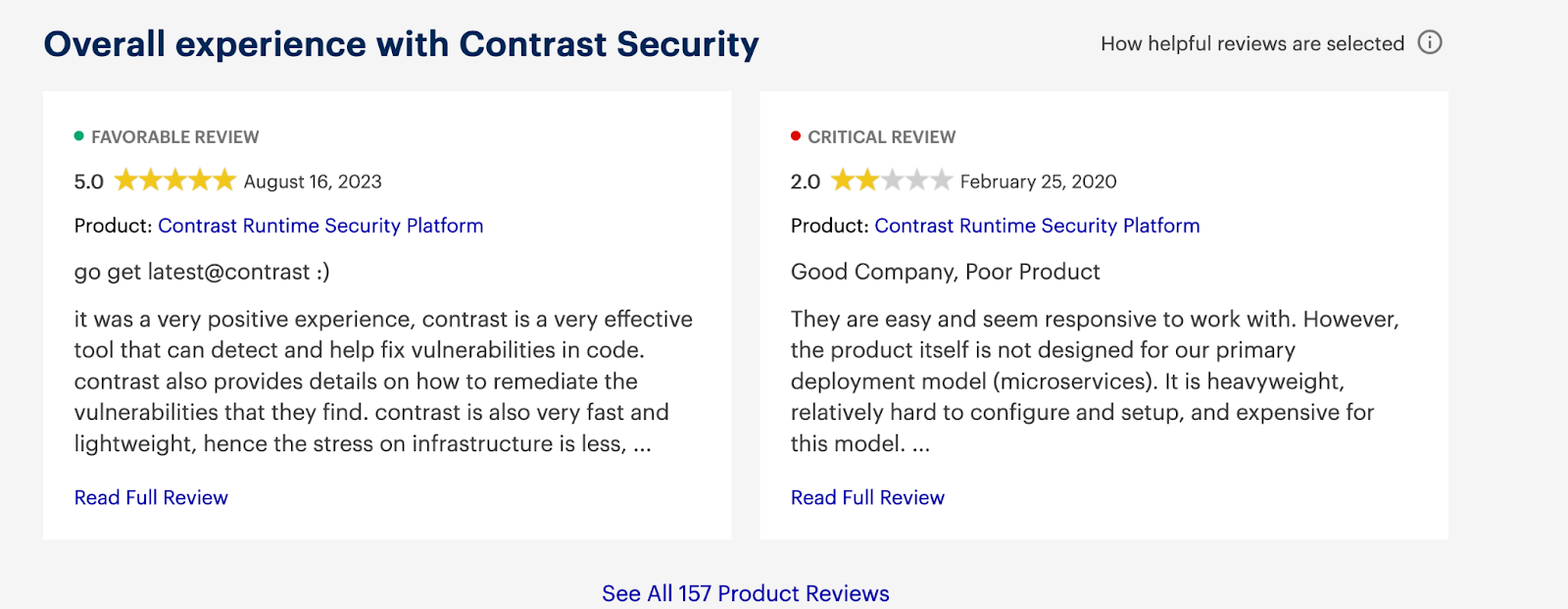
Contrast Protect Reviews:
3. Imperva RASP
Imperva RASP by Imperva, operates on a cloud-based infrastructure, delivering protection against various vulnerabilities, including those identified by OWASP. It efficiently detects and blocks harmful traffic in real-time, ensuring applications remain protected without sacrificing performance.
Key features:
- Continuous Runtime Protection: Provides in-process security monitoring across supported languages and frameworks, detecting threats as applications execute in production.
- Active Exploit Detection and Blocking: Automatically identifies exploitation attempts such as injection attacks or unsafe execution paths and blocks them in real time.
- Adaptive Threat Analysis: Uses runtime intelligence to adapt detection logic based on observed application behavior, improving accuracy over static or rule-based approaches.
Pros:
- Cloud-based deployment simplifies scaling and centralized management
- Strong coverage for OWASP Top 10 and common application-layer attacks
Cons:
- Heavy reliance on OWASP-style vulnerability categories may limit detection of application-specific or logic-based attacks
- Limited in-process visibility compared to agent-based RASP solutions
- Not purpose built for RASP
- Limited language support
Pricing:
Contact sales
Gartner Rating: 4.8/5.0
Imperva RASP Reviews:
4. Dynatrace
While most known as an observability solution, Dynatrace offers a product called Runtime Application Protection (RAP), which provides RASP capabilities for Java, .NET, and Go applications. RAP leverages Dynatrace's existing runtime instrumentation to deliver security monitoring .
Key features:
- Native Dynatrace Integration: Seamlessly integrates with the Dynatrace platform, allowing runtime security data to be correlated with metrics, logs, traces.
- Language-Specific Runtime Protection: Provides runtime application protection for services written in Go, Java, and .NET, leveraging existing instrumentation already deployed for observability.
- Unified Visibility Across Domains: Enables security events to be viewed alongside performance and reliability signals, supporting faster root cause analysis and incident response.
Pros:
- Leverages existing Dynatrace runtime instrumentation for security monitoring
- Tight integration with the broader Dynatrace observability ecosystem
Cons:
- Security capabilities are tightly coupled to the Dynatrace platform
- Limited language support compared to dedicated RASP solutions
- Needs adoption into Dynatrace ecosystem
- Limited runtime security capabilities
Pricing:
Consumption-based pricing model
Gartner Rating: 4.6/5.0
Dynatrace Reviews:
5. Next-Gen agent (formerly Signal Sciences agent)
Acquired by Fastly in 2020, Signal Sciences stands out as a next-gen web application firewall with runtime security capabilities. Built specifically with Microsoft environments in mind, Signal Sciences offers deep integration with Windows IIS, .NET Framework, and .NET Core applications.
Key features
- On-Premise Deployment Support: Can be deployed in on-premise environments, making it suitable for organizations with strict data residency or regulatory requirements.
- Windows Ecosystem Integration: Provides tight integration with the Windows application stack, including IIS, .NET Framework, and .NET Core–based services.
- WAF-Centric Runtime Protection: Operates primarily as a web application firewall, rather than deep in-process runtime security.
Pros:
- Strong integration with Windows-based application stacks such as IIS and .NET
- Flexible deployment options support both on-premise and hybrid environments
Cons:
- Primarily WAF-centric, with limited in-process runtime visibility compared to true RASP solutions
- Less suitable for non-Windows stacks
- Not suitable for API’s or Microservices
- Not developer focused
Pricing:
usage-based pricing model
Gartner Rating: 4.8/5.0
Next-Gen Agent Reviews:
6. Doverunner (formerly Appsealing)
A standout for its focus on mobile applications, Doverunner (formerly known as Appsealing) is a RASP solution designed specifically to protect Android and iOS apps from runtime threats. It prevents reverse engineering and tampering of Android app code and APK files at runtime.
Key features:
- Mobile Runtime Protection: Provides in-app runtime protection for mobile applications, detecting and mitigating threats while the application is executing on the device.
- CLI-Based Tooling: Offers command-line access for integrating security controls into mobile build, signing, and release pipelines.
- Threat Analytics Dashboard: Centralized dashboard for visibility into runtime threats, tampering attempts, and attack trends targeting mobile applications.
- Cross-Platform Mobile Support: Supports both iOS and Android platforms,
Pros:
- Purpose-built for securing mobile applications on Android and iOS platforms
- Strong defenses against reverse engineering, tampering, and application repackaging
Cons:
- Limited to mobile platforms; not applicable to backend or web applications
- Focused on binary and runtime protection rather than business logic security
- Silos developers outside of core mobile development
- Adoption learning curve
Pricing ranges from Dollar 129 per app per month for 15000 active devices
Gartner Rating: 4.6/5.0
Doverunner Reviews:
Choosing the Right RASP Tool for Your Application
Modern applications demand security that matches a distributed architecture, plays nicely in a containerized environment, and is context-aware.The right RASP tool should protect applications from the inside out, understanding what your code is doing rather than just inspecting traffic at the perimeter.
However, many RASP solutions remain limited to specific ecosystems supporting only Java, .NET, or mobile platforms, which falls short of what teams need in 2025 when applications span multiple languages, clouds, and deployment models.
In general, your key selection criteria should include:
- Multi-Language Support: Prioritize tools that cover your entire tech stack rather than forcing you to deploy multiple security solutions.
- Context-Aware Protection: Look for solutions that surface actionable data like stack traces and execution context, and not just alerts. Developers need to understand why something is a threat to respond effectively.
- Zero-Day Defense: Evaluate the tool's ability to detect and block unknown threats through behavior analysis rather than relying solely on signature-based detection.
- Deployment Flexibility: Ensure the solution works across your cloud, edge, and on-premise environments without requiring different configurations or agents for each.
Staying ahead at Runtime
When integrating RASP into your security strategy, embed it within your application's architecture to enhance protection. Integrating RASP at the core ensures continuous monitoring and immediate threat detection. This proactive approach allows for adaptive security measures that evolve alongside your application, providing robust defense without delaying development.
To strengthen security, implement RASP alongside real-time threat intelligence services. This combination enriches your security framework, offering insights into emerging threats and enabling preemptive actions. Real-time intelligence complements RASP by providing external perspectives on potential vulnerabilities, ensuring a comprehensive security approach.
Regularly update your RASP configuration to maintain effectiveness. Conduct thorough audits of settings and performance metrics to refine operations and address gaps. By keeping your RASP tool up-to-date with the latest threat data and security protocols, you can effectively intercept threats and maintain high application security standards.
Finally, cultivate a security-focused environment. Equip your team with the knowledge to use RASP effectively, emphasizing its role in the broader security landscape. Encourage continuous learning and adaptation to new security trends, ensuring your team remains informed and prepared for evolving cybersecurity challenges.
By adopting RASP tools and integrating them into your development process, you strengthen applications against evolving threats. As you tackle application security challenges in 2025, remember that proactive measures and continuous adaptation are vital to staying ahead of potential vulnerabilities. If you're ready to enhance your application security, start for free with Aikido - we're committed to simplifying your security journey and empowering you to build confidently.
FAQ
What are common challenges developers face when integrating RASP tools?
Common challenges include complex instrumentation, limited framework support, and the need for extensive tuning to avoid false positives. Many RASP tools operate as standalone agents, making it difficult for developers to understand why a request was blocked or how it maps back to the code. Platforms like Aikido Security, make identifying triggers easier by correlating runtime signals with application-level context.
How can developers troubleshoot common issues encountered with RASP tools?
Developers typically troubleshoot RASP issues by validating agent deployment, reviewing runtime logs, and gradually adjusting detection thresholds. Running RASP in monitor-only mode during early stages also helps prevent unintended disruptions.
What are the performance and latency concerns when deploying RASP in production environments?
RASP tools can introduce runtime overhead when inspecting requests and application behavior in real time. In high-traffic or microservice-based systems, this may lead to increased latency or resource consumption. Platforms like Aikido Security reduce this impact by prioritizing actionable signals instead of applying heavy, always-on runtime inspection.
How does RASP impact application stability and compatibility with modern frameworks and microservices?
Because RASP relies on runtime instrumentation, it may cause compatibility issues with newer frameworks, language updates, or containerized workloads. Poorly maintained agents can also affect application stability.
What are the limitations of traditional RASP tools compared to modern, AI-driven application security solutions?
Traditional RASP tools often lack broader context, relying on static rules and isolated runtime signals. This can result in noisy alerts without clear guidance on real risk. Modern platforms like Aikido Security address these limitations by using AI to correlate runtime findings with code, dependencies, and cloud exposure to focus on exploitable issues
You Might Also Like:
- Top 13 Container Scanning Tools in 2026
- Best Tools for End-of-Life Detection: 2026 Rankings.
- The Top 13 Code Vulnerability Scanners in 2026
- Top Infrastructure as Code (IaC) Scanners in 2026
- Top Cloud Security Posture Management (CSPM) Tools in 2026
- Top 10 Software Composition Analysis (SCA) Tools in 2026
- Top 10 AI-Powered SAST Tools in 2025



