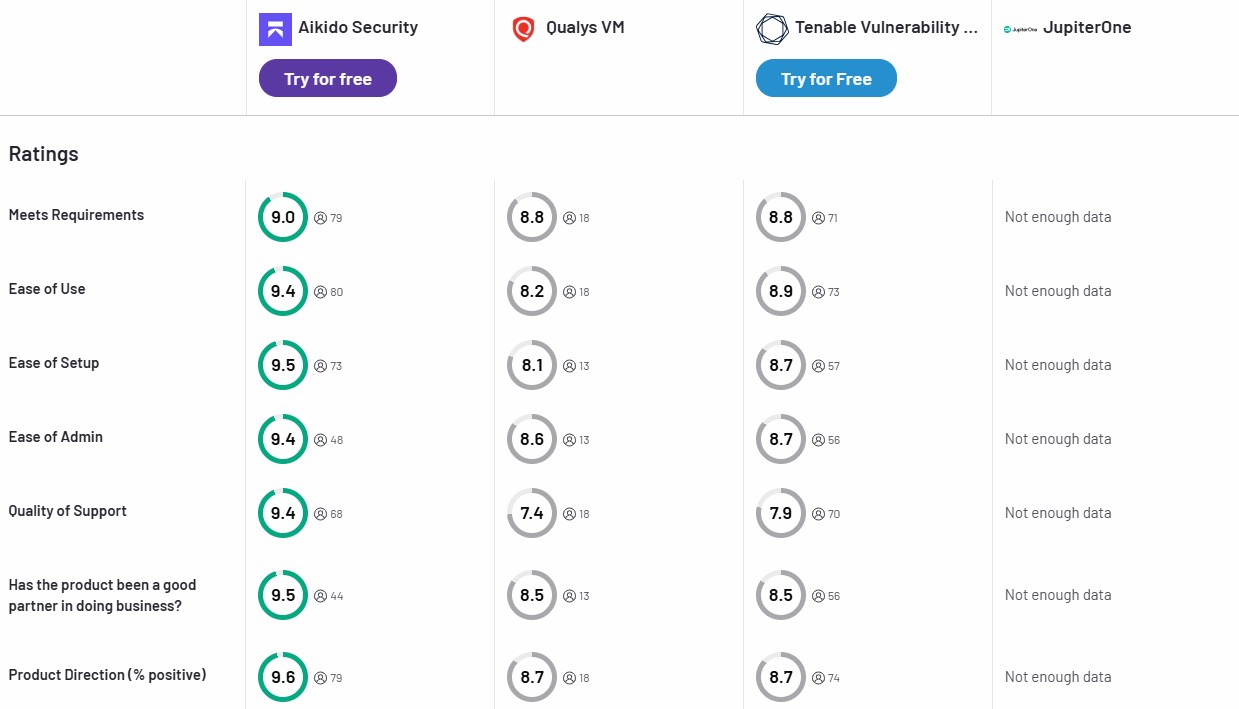
Finding vulnerabilities is like discovering rats in your house – the real challenge isn't spotting them, it's getting rid of them efficiently and making sure they don't come back. Traditional vulnerability scanning tools excel at the discovery part but leave teams drowning in thousands of findings with no clear path to resolution. Modern vulnerability management platforms solve this by orchestrating the entire lifecycle: detect, prioritize, remediate, and verify fixes.
The numbers tell a sobering story. Organizations typically carry a backlog of over 100,000 unresolved vulnerabilities on average, with security teams able to patch only 7-15% of identified issues each month. Without proper management systems, vulnerability discovery becomes an exercise in security theater – impressive dashboards showing thousands of findings that nobody has time to fix.
This guide explores the vulnerability management landscape in 2025, covering platforms that transform security chaos into manageable workflows. Whether you're a developer tired of alert fatigue, a startup CTO building your first security program, or an enterprise CISO managing risk across thousands of applications, there's a combination of tools that can streamline your vulnerability management process.
- 3 Best Vulnerability Management Tools for Developers
- 4 Best Vulnerability Management Tools for Enterprises
- 3 Best Vulnerability Management Tools for Startups
- 4 Best Integrated Vulnerability Management Platforms
TL;DR
Aikido Security transforms vulnerability management with advanced detection, AI-powered prioritization, and automated fixes. Unlike traditional platforms that overwhelm teams, Aikido cuts noise by over 90% and offers one-click solutions for common vulnerabilities. It unifies source code, dependencies, containers, infrastructure, and runtime security into one platform, simplifying workflows and providing actionable insights developers can use.
What is Vulnerability Management?
Vulnerability management is the comprehensive process of identifying, evaluating, prioritizing, and addressing security weaknesses across an organization's digital assets. Think of it as the difference between having a smoke detector (vulnerability scanning) versus having a complete fire safety system with detection, prioritization, suppression, and monitoring.
Effective vulnerability management platforms orchestrate multiple activities:
- Continuous scanning across different asset types,
- Intelligent risk scoring that considers exploitability and business impact,
- Workflow automation that assigns remediation tasks to appropriate teams, and verification systems that ensure fixes actually resolve the underlying issues.
Why Comprehensive Vulnerability Management Is Critical
Modern software environments are deeply interdependent. So interdependent that a single security weakness can cascade across multiple systems in minutes. Remember the 2025 npm debug and chalk packages vulnerability that affected millions of JavaScript applications all over the world.
More of that can and will happen in the future, hence you need to be agile and implement comprehensive vulnerability management because:
- Prioritization becomes survival:. Security teams face an impossible choice: attempt to fix everything (and accomplish nothing) or risk missing the critical vulnerabilities that lead to breaches. Effective vulnerability management platforms use threat intelligence, exploitability analysis, and business context to focus remediation efforts where they matter most.
- Compliance requirements demand systematic approaches:. Regulations like PCI DSS, SOC 2, and GDPR require organizations to demonstrate continuous vulnerability monitoring and timely remediation. Manual processes can't provide the documentation and consistency needed for audit success.
- Developer productivity depends on actionable insights:. Teams that receive clear, prioritized vulnerability reports with specific remediation guidance resolve issues 3x faster than those working from generic scan reports. The best management platforms integrate directly into development workflows, providing security feedback at the moment it's most actionable.
How to Choose the Right Vulnerability Management Platform
When selecting a vulnerability management platform, you should look for the following 5 key features:
Comprehensive Coverage
Comprehensive coverage determines how complete your security posture becomes. Look for platforms that manage vulnerabilities across source code, dependencies, containers, infrastructure configurations, and runtime environments. Gaps in coverage become gaps attackers exploit.
Intelligent Prioritization
Intelligent prioritization separates useful platforms from alert-generating noise machines. The best systems combine multiple risk factors: vulnerability severity, exploit availability, asset criticality, and business context. CVSS scores alone don't provide sufficient prioritization for modern environments.
Workflow Integration
Workflow integration affects how quickly vulnerabilities actually get fixed. Platforms that integrate with development tools (Git repositories, issue trackers, CI/CD pipelines) enable seamless handoffs between security detection and developer remediation. Tools that require context switching get ignored.
Automation Capabilities
Automation capabilities determine scalability and consistency. Advanced platforms can automatically assign vulnerabilities to appropriate teams, generate remediation pull requests, and verify that fixes actually resolve the underlying issues. Manual vulnerability management doesn't scale beyond small teams.
Compliance and Audit Support
Compliance and audit support becomes essential for regulated environments. Look for platforms that provide audit trails, policy enforcement, and reporting templates that align with your compliance requirements. Some platforms can even automate evidence collection for security audits.
Top 6 Vulnerability Management Tools for 2026
Here's how leading vulnerability management platforms compare across key capabilities:
1. Aikido Security
Aikido Security transforms vulnerability management by combining comprehensive detection with intelligent prioritization and automated remediation in a single, developer-friendly platform.
Key Features:
- Unified asset coverage: Aikido manages vulnerabilities across source code, dependencies, containers, infrastructure configurations, and runtime environments. This eliminates the complexity of correlating findings from multiple security tools. Giving a single pane of glass view for all your IT estate vulnerabilities.
- AI-powered risk intelligence: Reduces alert fatigue by over 90% through advanced deduplication and contextual analysis. The platform understands which vulnerabilities actually affect your specific deployment patterns and configurations.
- Automated remediation workflows: Generate pull requests with specific fixes for common vulnerability types, turning security findings into actionable development tasks that can be resolved in minutes rather than hours.

- Developer workflow integration: Provides vulnerability feedback directly in IDEs, pull requests, and CI/CD pipelines, ensuring security information reaches developers at the moment they can act on it most effectively.
- Compliance automation: Generates audit documentation and evidence collection for SOC 2, ISO 27001, PCI DSS, and other regulatory frameworks, reducing the manual effort required for security audits.

Best for
- Development teams that want comprehensive vulnerability management without the operational overhead of managing multiple security tools.
- Particularly effective for organizations prioritizing developer productivity alongside security outcomes.
Pricing:
- Transparent per-developer pricing with generous free tier.
- No hidden costs or surprise charges as teams scale.
2. Rapid7 InsightVM

Rapid7 InsightVM provides enterprise-grade vulnerability management with strong analytics and reporting capabilities for infrastructure-focused environments.
Key Features:
- Comprehensive asset discovery automatically identifies and profiles systems across on-premises, cloud, and hybrid environments, providing complete visibility into potential attack surfaces.
- Threat intelligence integration incorporates real-world exploit data and threat actor behavior to prioritize vulnerabilities based on active exploitation patterns rather than theoretical risk scores.
- Remediation orchestration integrates with patch management systems and configuration management tools to streamline the vulnerability resolution process across large environments.
- Executive reporting provides risk-based dashboards and compliance reporting designed for security leadership and audit requirements.
Pain points:
- Users frequently report that InsightVM can be complex to configure and tune effectively, with one reviewer noting "the initial setup requires significant time investment to achieve optimal results."
- The pricing model can also become expensive for organizations with large numbers of assets.
Best for:
Enterprise security teams that need comprehensive vulnerability management for complex, multi-environment infrastructures with dedicated resources for platform management.
Pricing:
Subscription-based with costs scaling based on assessed assets and advanced feature requirements.
3. Qualys VMDR

Qualys VMDR (Vulnerability Management, Detection & Response) combines traditional vulnerability management with advanced threat detection and automated response capabilities.
Key Features:
- Cloud-native architecture: Qualys provides scalable vulnerability assessment across global infrastructures without requiring on-premises management infrastructure.
- Threat-based prioritization: Incorporates active threat intelligence and exploit kits to focus remediation efforts on vulnerabilities being actively exploited in the wild.
- Automated patch deployment: Integrates with system management tools to streamline vulnerability remediation from detection through resolution verification.
- Compliance dashboard: Provides audit-ready reporting for multiple regulatory frameworks with automated evidence collection and policy compliance tracking.
Pain points:
- Users report that Qualys can generate overwhelming numbers of findings, with limited built-in prioritization beyond basic scoring.
- One enterprise reviewer noted "the volume of alerts requires significant manual triage to identify actionable items."
Best for:
Large enterprises with dedicated security operations teams that need cloud-delivered vulnerability management with comprehensive compliance reporting capabilities.
Pricing:
Subscription-based pricing with costs determined by number of assets and feature modules selected.
4. Tenable.io
Tenable.io provides comprehensive vulnerability management with advanced risk scoring and extensive integration capabilities for complex security environments.
Key Features:
- Predictive prioritization: Tenable uses the Vulnerability Priority Rating (VPR) system to forecast which vulnerabilities are most likely to be exploited based on threat intelligence and technical analysis.
- Asset criticality assessment: This features incorporates business context and asset importance into risk calculations, ensuring remediation efforts focus on protecting the most valuable systems first.
- Extensive integration ecosystem: Connects with over 40 security and IT management tools, enabling vulnerability data to flow seamlessly into existing operational workflows.
- Advanced analytics: Provides trend analysis and risk metrics that help security teams measure improvement over time and demonstrate security program effectiveness.
Pain points:
- The platform can be overwhelming for smaller teams, with users reporting "too many features and configuration options for straightforward vulnerability management needs."
- Some reviewers also note challenges with false positive rates in certain scan types.
Best for:
Security-mature organizations with dedicated vulnerability management teams that need advanced analytics and extensive tool integrations.
Pricing:
Tiered subscription model based on assets scanned and advanced feature requirements.
5. JupiterOne
JupiterOne takes a unique approach to vulnerability management by mapping security findings to asset relationships and business context through graph-based analysis.
Key Features:
- Asset relationship mapping: JupiterOne creates a comprehensive graph of how systems, applications, and data connect, providing context for understanding vulnerability impact across interconnected environments.
- Query-driven analysis: Enables security teams to ask complex questions about their environment and vulnerability exposure using a powerful graph query language.
- Compliance automation: Maps security controls and vulnerability findings to regulatory requirements, automating much of the compliance reporting process.
- Risk correlation: Identifies how individual vulnerabilities combine to create compound risks across interconnected systems and applications.
Pain points:
- The graph-based approach has a steep learning curve, with users noting "requires significant time investment to understand the query language and data model effectively."
- The platform is also more focused on analysis than hands-on remediation.
Best for:
Security architects and mature security teams that need to understand complex relationships between assets and vulnerabilities in large, interconnected environments.
Pricing:
Contact-based pricing focused on enterprise customers with complex infrastructure requirements.
6. ServiceNow Vulnerability Response
ServiceNow Vulnerability Response integrates vulnerability management directly into IT service management workflows, providing seamless handoffs between security detection and operational remediation.
Key Features:
- ITSM integration: Connects vulnerability findings directly to change management, incident response, and asset management processes within the ServiceNow platform.
- Risk-based prioritization: Incorporates business context, asset criticality, and threat intelligence to focus remediation efforts on vulnerabilities that pose the greatest business risk.
- Automated workflow orchestration: Creates tickets, assigns responsibilities, and tracks remediation progress using ServiceNow's workflow automation capabilities.
- Executive dashboards: Provide risk metrics and compliance status designed for business stakeholders and audit requirements.
Pain points:
- Users report that the platform can be complex to customize and configure, particularly for organizations without existing ServiceNow expertise.
- The licensing model can also become expensive for smaller teams.
Best for:
Organizations already using ServiceNow for IT service management that want to integrate vulnerability management into their existing operational workflows.
Pricing:
ServiceNow platform licensing with additional costs for vulnerability management modules and integrations.
3 Best Vulnerability Management Tools for Developers
Developers need vulnerability management platforms that integrate seamlessly into coding workflows without disrupting productivity. The most effective tools provide actionable feedback with clear remediation guidance directly in the tools developers already use.
Developer priorities:
- IDE and Git integration for real-time vulnerability feedback during development
- Automated remediation with pull requests containing specific fixes
- Clear prioritization that focuses attention on vulnerabilities that actually matter
- Fast feedback loops that don't slow down development cycles
- Learning resources that help developers understand and prevent security issues
Top 3 Vulnerability Management Tools for Developers
1. Aikido Security
Aikido Security leads developer experience with comprehensive IDE and Git integration with intelligent filtering. Developers receive vulnerability feedback directly in their coding environment with one-click fixes that resolve issues without requiring deep security expertise.
2. Synk
Snyk provides Git integration with developer-friendly interfaces that make vulnerability management feel more natural in development processes.
3. GitHub Advanced Security
GitHub Advanced Security offers seamless integration for teams already using GitHub, providing vulnerability management capabilities directly within familiar development workflows.
4 Best Vulnerability Management Tools for Enterprises
Large organizations value scalability, maturity, compliance, and seamless integration. They often have multiple applications, teams, and a mix of architectures (some legacy on-prem, some cloud-native).
An ideal enterprise vulnerability management tool must be:
- Scalable across hybrid and multi-cloud environments
- Align with compliance frameworks like SOC 2, ISO 27001 and PCI DSS
- Integrate with ticketing, ITSM, and CI/CD pipelines for smooth workflows
- Prioritize with business context, exploit intelligence, and asset criticality
- Automate remediation across distributed teams
Here are four vulnerability management platforms that often show up on enterprise shortlists:
1. Aikido Security
Aikido Security delivers an enterprise-ready vulnerability management platform designed for scale, accuracy, and developer productivity. It unifies vulnerability detection across source code, dependencies, containers, infrastructure, and runtime to eliminate the silos that often slow down large organizations.
What sets Aikido apart is its AI-powered triage that cuts alert noise by over 90%, ensuring that security and engineering teams focus only on actionable risks. Its automated remediation system can generate pull requests for common vulnerabilities, turning security fixes into a continuous, scalable process.
And unlike legacy enterprise scanners, Aikido’s developer-first approach means it fits into the tools your teams already use.
2. Veracode
Veracode is a well-known name in enterprise application security. It is recognized for its mature scanning capabilities, extensive governance features, and wide compliance coverage.
However, it’s important to note that choosing Veracode, though might feel like the “safe” enterprise choice now (because it’s familiar), doesn't always mean better security or future-proof technology.
The platform’s legacy architecture and slower scanning workflows can sometimes make it less adaptable to modern DevSecOps pipelines.
3. Checkmarx
Checkmarx has built a strong reputation for deep static analysis and policy-driven vulnerability management, earning its place in many enterprise security programs. Its SAST capabilities are among the most granular in the market, giving security teams fine control over rules, policies, and language coverage.
Like Veracode, Checkmarx benefits from being a known and trusted vendor often making it the “easier” choice for enterprise procurement. Yet, ease doesn’t always equal innovation. The platform’s complexity, slower scan performance, and limited workflow automation can make it cumbersome in agile or hybrid DevOps environments.
4. Snyk
Snyk began as a developer-friendly open-source dependency scanner but has expanded aggressively into the enterprise market through a series of acquisitions covering containers, IaC, and cloud security.
While this growth broadened its feature set, those acquisitions haven’t yet been seamlessly integrated into a single cohesive platform. Enterprises often report fragmented workflows between modules and inconsistent reporting across different components.
Other enterprise-grade platforms like Tenable.io, Qualys VMDR, and Rapid7 InsightVM remain staples in large-scale security operations. These tools excel at infrastructure-level visibility, risk-based prioritization, and compliance reporting across hybrid and multi-cloud environments.
However, they typically require heavier operational overhead and less developer-centric integration compared to newer platforms like Aikido.
3 Best Vulnerability Management Tools for Startups
Startups need vulnerability management platforms that provide enterprise-grade protection without the operational overhead or cost complexity of traditional enterprise solutions. When you're juggling fundraising, product development, and customer acquisition, security can't become another full-time job.
Startup priorities:
- Cost-effectiveness with transparent pricing that scales predictably
- Easy implementation that doesn't require dedicated security personnel
- Automated operation with minimal ongoing management requirements
- Growth accommodation that scales seamlessly as teams expand
- Developer focus that enhances rather than hinders development productivity
Vulnerability Management Tools for Startups
1. Aikido Security
Aikido Security offers exceptional value for startups with comprehensive vulnerability management capabilities, transparent pricing, and minimal operational overhead. The platform grows seamlessly with expanding teams while maintaining simplicity. You get enterprise-grade detection across code, dependencies, containers, and infrastructure without needing a security team to manage it.
2. Synk
Snyk provides dependency management capabilities with a freemium model that works well for early-stage companies heavily reliant on open source libraries. However, be prepared for potential alert fatigue as your codebase grows.
3. GitHub Advanced Security
GitHub Advanced Security offers integrated vulnerability management for GitHub-native development workflows, eliminating the need for additional tool procurement and management. The downside? It's only available with GitHub Enterprise, making it expensive for smaller teams.
Other Startup-specific considerations:
- Budget predictability matters more than feature completeness: Choose tools with transparent per-developer pricing over complex usage-based models. Aikido's straightforward pricing eliminates budget surprises as you scale from 5 to 50 developers.
- Time-to-value beats feature depth:. Startups need security wins measured in days, not months. Tools that require extensive configuration or dedicated personnel slow down more than they protect. Look for platforms that work out of the box with intelligent defaults.
- Developer adoption drives success:. Security tools that developers ignore become an expensive compliance theater. The best startup-focused tools integrate seamlessly into existing workflows, providing value without disrupting productivity patterns your team has already established.
4 Best Integrated Vulnerability Management Platforms
Modern organizations benefit most from unified platforms that integrate vulnerability management with broader security operations, eliminating the complexity of managing multiple disparate security tools. Instead of juggling five different dashboards, you get a single source of truth.
Integration advantages:
- Unified visibility across all security domains and asset types
- Correlated intelligence that connects vulnerabilities to broader security context
- Streamlined workflows that eliminate handoffs between different security tools
- Cost efficiency through consolidated licensing and reduced tool sprawl
- Simplified management with single training requirements and operational processes
Leading Integrated Vulnerability Management Platforms
1. Aikido Security
Aikido Security provides the most comprehensive integration, combining vulnerability management with SAST, DAST, secret scanning, cloud security, and compliance automation in a single developer-friendly platform. Think of it as the Swiss Army knife of security tools, but actually good at everything instead of mediocre at many things.
For enterprises, Aikido offers each product best-in-class, so you can pick which module you need and unlock the platform when you're ready.
2. Microsoft Defender for Cloud DevOps
Microsoft Defender for Cloud DevOps integrates vulnerability management into the broader Microsoft security ecosystem, providing unified visibility across development and production environments. If you're already invested in the Microsoft ecosystem, this offers excellent value and seamless integration.
3. GitLab Ultimate
GitLab Ultimate includes integrated vulnerability management alongside the complete DevOps lifecycle, offering seamless security feedback throughout development workflows. The challenge is that vulnerability management becomes just one feature among many, sometimes leading to less specialized capabilities.
4. JFrog Xray
JFrog Xray focuses on software supply chain security with vulnerability management integrated into artifact and dependency management workflows. Excellent for organizations heavily invested in JFrog's DevOps platform.
Beyond Vulnerability Management: How Aikido Redefines DevSecOps in 2026
The best vulnerability management platform is the one your team actually uses consistently. Perfect security that sits unused loses to good security that runs automatically every day.
Which is why Aikido set out to build a security platform that's worth more than it cost.
If you’re a startup, you get one suite with everything you need to stay secure from day 1. For enterprises, Aikido offers each product best-in-class, so you can pick which one you need and unlock the whole platform whenever you're ready.

You might also like:
- Top SAST Tools in 2026 – Secure your source code with static analysis
- Top Container Scanning Tools – Protect containerized applications
- Top AppSec Tools – Complete application security coverage



