Veracode is a well-known application security platform, popular for its combination of static code analysis, dynamic testing, and software composition analysis in one service. Teams use Veracode to catch security flaws during development and comply with security requirements. It shines in comprehensive coverage and enterprise-grade policies.
However, many developers and security engineers have grown frustrated with Veracode’s downsides – from its clunky UX and high price tags to its overly complex setup, frequent false positives, noisy results and scans that just slow down CI pipelines, and that's naming a few. As a result, some users feel Veracode delivers more security theater than actionable security.
TL;DR
Aikido Security stands out as the top Veracode alternative, providing security solutions with a modern developer-first experience. The platform covers everything from code to cloud, to protect (automate application protection, threat detection and response) and attack (detect, exploit and validate your entire attack surface, on demand).
You can benefit from one suite with everything covered or you can get each best-in-class product (SAST, SCA, DAST) and expand and integrate as you wish.
Also, it ties into your pipelines and IDEs to scan code, dependencies, containers, IaC, and more,in the background, then uses AI triage to kill ~85% of the noise.
See How Veracode Compares To Aikido Security
Here are a few reviews from Veracode users:
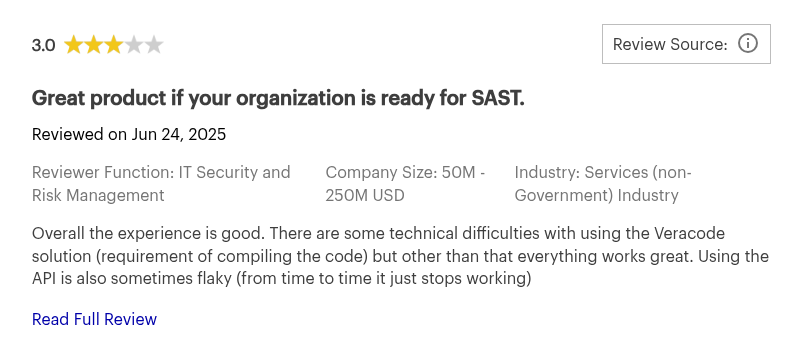

Users also shared:
- “The UI seems out of date and cumbersome at times.” — Gartner Peer Insights reviewer
- “We installed Veracode Greenlight… it never caught anything, and whatever it reported was incorrect. It felt like a waste of time and didn’t add value to keeping our code secure.” — Reddit user
If this sounds familiar, then, you’re likely ready to explore alternatives. In this article, we’ll walk you through the best Veracode alternatives that provide real protection without the fluff. We’ll look at:
Also comparing SAST tools? Check out our Top 10 AI-powered SAST tools in 2025 for a full breakdown of the modern static analysis platforms teams are using today.
What Is Veracode?
Veracode is an application security platform that offers SAST, DAST, and SCA to help teams find vulnerabilities across their applications.
In practice, Veracode is used by enterprises to scan for vulnerabilities in source code and web apps, often as part of compliance or risk management programs. It integrates with CI/CD pipelines and developer tools to embed security checks into the software development lifecycle.
In a traditional AppSec model, Veracode acts as a one-stop shop to find known coding flaws, insecure dependencies, and web app vulnerabilities before they reach production. Its support for a broad range of languages and report generation has made it a go-to for security teams. Veracode’s platform also includes governance features like policy management and compliance reporting, which appeal to larger organizations with strict security requirements.
Why Look for Veracode Alternatives?
Despite Veracode’s capabilities, many teams start looking for a better solution once they encounter its friction:
- Slow Scans and Workflows: Veracode’s scans can be time-consuming (often 30+ minutes, even for moderate sized apps), slowing down development and CI/CD pipelines. With users also reporting long upload times and wait times for results.
- High False Positives: Veracode often flags issues that aren’t real vulnerabilities. Teams waste effort triaging “noise” or have to involve Veracode support to mark false positives. This leads to alert fatigue.
- Mobile First Testing: Veracode’s focus on binary SAST for compiled apps and web apps limits its ability to fully address the security needs of modern mobile applications – native binaries (APK/IPA), run-time telemetry, mobile SDKs and hybrid frameworks.
- SAST Customization: Veracode’s rule-set customization is limited. In today’s ecosystem modern teams need more than just scans, they need flexibility and control.
- Poor Developer Experience: Veracode’s outdatedUI and clunky processes make it unpopular with developers. Onboarding new projects or mitigating findings isn’t as straightforward as it should be. The heavy enterprise feel can frustrate agile teams.
- Pricing and Licensing: Veracode is expensive, with pricing that scales by features and number of apps/users. Small and mid-sized teams find the cost prohibitive and the licensing model confusing.
- Integration Limitations: While Veracode can integrate with dev tools, it’s not as seamless or as developer-centric as newer alternatives. For example, Veracode requires uploading builds (it scans binaries), which is less convenient than scanning sources in real time. Its remediation guidance is also considered weaker compared to some dev-first tools like Aikido.
- Slow Updates: Being a legacy platform, Veracode’s support for new languages or frameworks can lag behind. Some users notice the engine doesn’t keep up with the latest tech (e.g. newer language versions or modern frameworks).
- Post-deployment Monitoring: Reports from users indicate Veracode’s post-deployment and runtime services are not as robust as its SAST and SCA offerings. Post-deployment services like automated pentesting and continuous monitoring remain unavailable.
- Support and Flexibility: Users have cited less-than-stellar support and rigid workflows. Customizing rules or getting help with unique use cases might require extra services.
In short, teams want to “shift left” and empower developers to fix issues quickly but Veracode slows them down. Searching for a suitable Veracode alternative means finding tools that aren’t only faster but more accurate, easier to use, and cost-effective.
Top 6 Alternatives to Veracode
Below is a quick list of the top Veracode alternatives we’ll be covering, with a sneak peek at why each is on the list:
- Aikido Security – Code-to-cloud security platform with low false positives and a dev-first experience. (Our top Veracode alternative.)
- Checkmarx –SAST and AppSec platform (Checkmarx One) known for broad language support and on-premise options.
- GitHub Advanced Security – Native security features in GitHub (CodeQL code scanning, secret scanning, Dependabot) seamlessly integrated into pull requests.
- GitLab Ultimate – GitLab’s highest tier with built-in SAST, DAST, container scanning, and more, all automated in CI for those already using GitLab.
- Snyk – Security platform offering SCA, container, IaC, and code scanning with easy fixes and robust integration into dev tools.
- SonarQube – Popular code quality platform that also flags security issues (“code smells” and vulnerabilities) in many languages; great for code health and cleanliness.
Now, let’s see how each tool stacks up against Veracode.
1. Aikido Security
Aikido Security is the ultimate security platform that covers everything from code to cloud and even runtime security. It’s designed for software teams that want real protection without the noise. The goal: give developers a single pane of glass for security without the usual friction, while giving engineering and security leaders peace of mind.
Aikido offers best-in-class static code analysis (SAST), open-source dependency scanning (SCA), container scanning, infrastructure-as-code (IaC) scanning, dynamic testing (DAST), API testing, and more. Each module can be selected as a standalone solution that can compete with alternatives, or can be integrated to create a complete code to cloud to runtime security platform.
Unlike Veracode, Aikido offers cloud security and within the code security space it offers: code quality, malware detection, end-of-life runtimes, on-premise code scanning, AI Autofix for IaC and custom SAST rules. Meanwhile, it has superior coverage for container security (end of life runtimes for containers, AI Autofix), and it also offers Zen, a firewall for bot, attack and geo-blocking and rate-limiting.
Other capabilities that are not available in Veracode include reachability analysis, deduplication and AI Auto-Triage, which all contribute to making Aikido far superior.
The standout feature, however, is that Aikido can do what Veracode does, but better: reducing false positives, enabling developers to more easily find what they need, providing actionable guidance and automated fixes.
Key Features:
- Best-of-breed scanners: Aikido offers best-in-class scanners for any part of your IT estate. Code scanning, IaC scanning, API scanning, etc. And compared with other scanners, Aikido has shown better reachability analysis and auto remediations.
- Connected “code-to-cloud” coverage: Aikido links code, cloud, and runtime in one seamless workflow. You can start with the module for (code scanning, container/IaC scanning, API security, and runtime protection) and scale to gain deeper context as you expand.
- Noise Reduction by Design: Aikido auto-triages results to cut out the noise (something that Veracode does not do). If an issue isn’t exploitable or reachable, it’s silenced automatically. You get real signals, not just alerts.
- Built for Devs: Integrates deeply with GitHub, GitLab, Bitbucket, Jira, Slack, and much more. You can run scans locally, in pull requests, or as part of your release process.
- Auto-Fix Where It Matters: Its AI-powered autofix suggests or applies remediations with context. Even when manual fixes are needed, you get clear steps—not just vulnerability dumps.
- Fast, Continuous Feedback: Scans run in minutes, not hours..
- Flexible Deployment: Cloud-native by default, but also offers an on-premises scanning option for teams with stricter security requirements.
Why Choose It:
If you're fed up with bloated dashboards, false positives, and disconnected tools, Aikido is built for you. It unifies scanners, simplifies triage, and speaks “developer”.
Whether you're a lean startup or scaling security across a large engineering org, Aikido gives you full-stack protection that fits how modern teams actually build software. It’s everything Veracode promises minus the legacy friction.
Pros:
- Developer-focused approach with numerous integrations and mitigation guidance.
- Customizable security policies and flexible rule tuning for any kind of needs.
- Centralized reporting and compliance templates (PCI, SOC2, ISO 27001).
- Mobile and binary scanning support (APK/IPA, hybrid apps).
- Agentic Pentesting (Human-Level Pentesting, Automated by AI) that delivers results in hours.
Pricing:
- Free: $0 (2 users, full scanner suite, 10 repos)
- Basic: $350/month (ideal for small teams, 10 users, 100 repos)
- Pro: $700/month (growing teams, custom rules, 20 million reqs/month)
- Advanced: $1050 (enterprise feature set)
Custom offerings are also available for startups (30% discount) and enterprises
Gartner Rating: 4.9/5.0
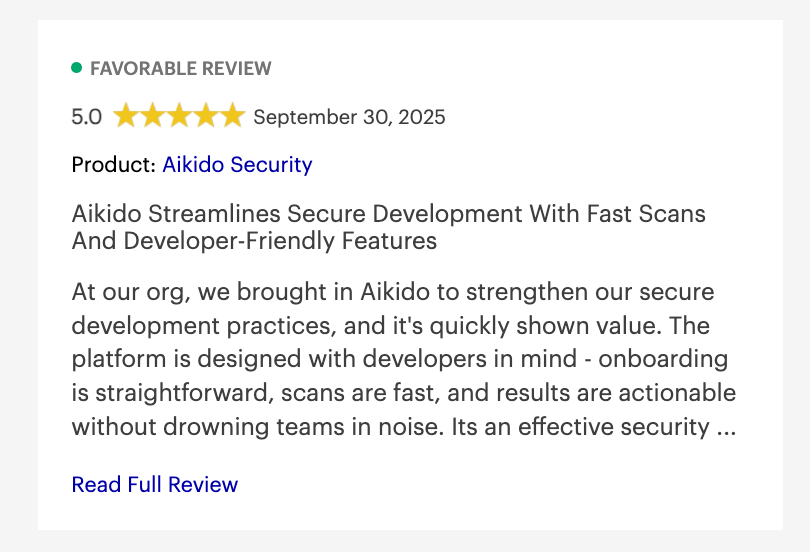
Aikido Security Reviews
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra and SourceForge
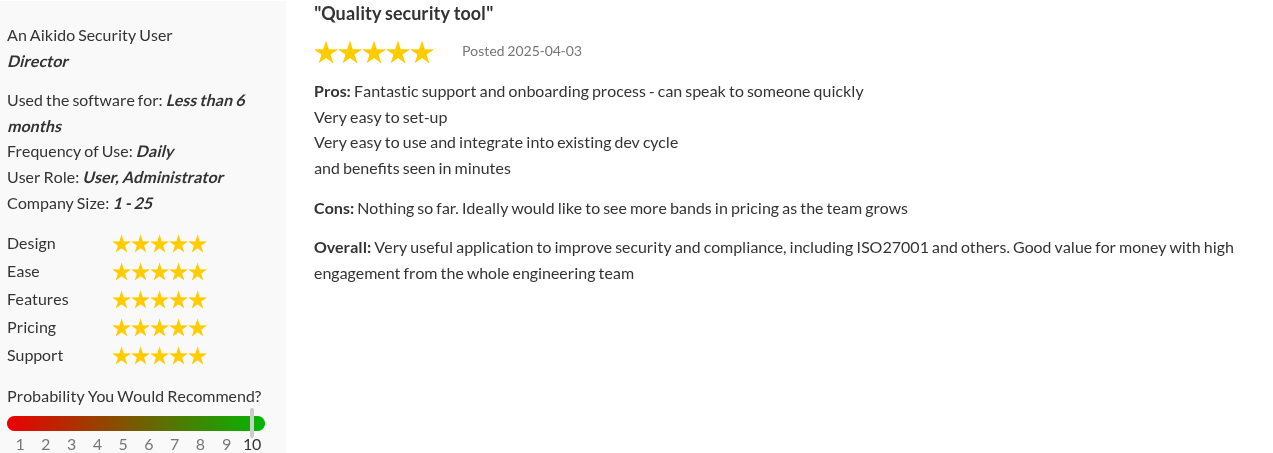
2. Checkmarx

Checkmarx is a long-established name in application security, best known for its static application security testing (SAST) capabilities. Its modern platform—Checkmarx One—is a unified, cloud-native AppSec suite that includes SAST, software composition analysis (SCA), API security, infrastructure-as-code (IaC) scanning, container scanning, and even some DAST features.
Where Veracode scans compiled binaries, Checkmarx scans source code directly, which makes it more flexible and easier to integrate into dev workflows. Enterprises often choose it for its deep language coverage, ability to customize rules, and optional on-premise deployment.
Key Features:
- Comprehensive SAST Engine: Checkmarx supports dozens of languages and offers deep, path-sensitive analysis without requiring builds. Incremental scanning improves performance in large codebases.
- Unified Platform:Checkmarx One brings together SAST, SCA, IaC, containers, and APIs under one interface. Like Aikido, it aims to eliminate tool sprawl.
- Developer-Centric Workflow:With integrations for popular IDEs (VS Code, IntelliJ, Eclipse), Git providers, and CI/CD systems, Checkmarx makes it easy for developers to get results inside their normal flow.
- Custom Rules with CxQL:Security teams can write their own detection rules using Checkmarx Query Language (CxQL), making it easier to tailor scans to specific coding practices or frameworks.
- Flexible Deployment Options: Checkmarx offers full on-premise deployments for teams with strict compliance or data residency needs—something Veracode doesn’t.
Why Choose It:
Checkmarx is a solid Veracode alternative if your top priority is robust static code analysis, especially for large, regulated codebases. It’s also ideal if you want full control over where scans run or need highly customizable rules.
While it still has a learning curve and can generate false positives without tuning, its flexibility, broad language support, and enterprise readiness make it a strong pick for security teams that want depth and configurability over simplicity.
Here a few details you should note if considering Checkmarx as your Veracode alternative:
Pros:
- Broad language and framework coverage
- Strong SAST engine with deep analysis
- Enterprise-ready compliance and reporting
- Robust security research and threat intel
Cons:
- Limited agility for smaller dev teams
- Primarily enterprise focused
- Heavier administration for CI/CD pipelines
- Separate pricing for each security module
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
Checkmarx Reviews
Checkmarx One is rated 3.9/5, based on over 50 reviews on Capterra
3. GitHub Advanced Security
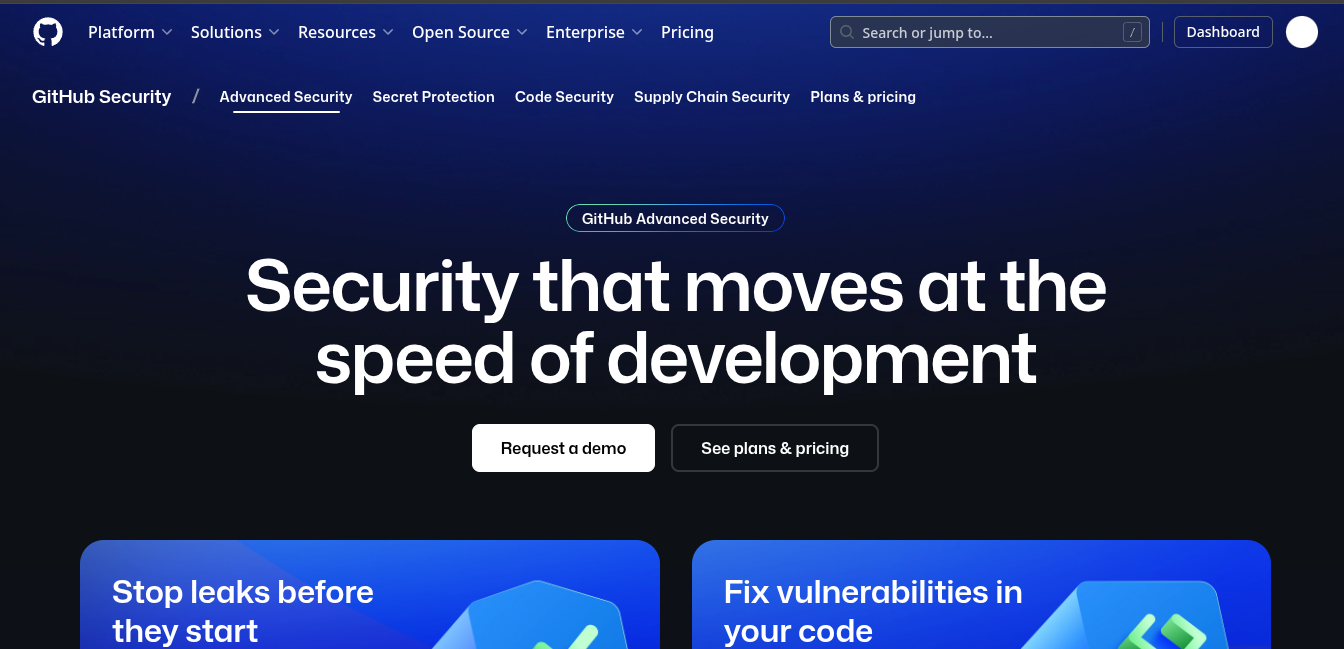
GitHub Advanced Security (GHAS) is GitHub’s native suite of security features designed to scan code directly within the GitHub ecosystem. It includes CodeQL-based static analysis, secret scanning, and open-source dependency scanning (via Dependabot). It’s not a standalone platform, but rather a fully integrated experience for teams already building on GitHub.
GitHub Advanced Security (GHAS)
Its strength lies in blending security checks seamlessly into the developer workflow—findings appear directly in pull requests, with no need for context switching. For teams already using GitHub, it turns the repo itself into a secure development platform, but it does not offer the same coverage as other platforms on this list.
Key Features:
- CodeQL Static Analysis:CodeQL allows security queries that treat code as data. It detects vulnerabilities like SQL injection or XSS with context-aware rules. You can use default query sets or customize your own.
- Secret Scanning:GHAS scans for exposed credentials like API keys and passwords. It can even block secrets from being committed, and works with many third-party providers to revoke keys automatically.
- Dependency Scanning & Dependabot:GHAS alerts on vulnerable libraries and automatically opens pull requests to update them, keeping your stack safer with minimal effort.
- Native Dev Integration:Code scanning results appear right in pull requests, inline with code. Developers see warnings just like any other CI check, making adoption frictionless.
- No Setup Overhead:There’s no separate tool to install. Security checks run via GitHub Actions or hosted infrastructure. For GitHub-native teams, this means security is enabled with a few config tweaks.
Why Choose It:
GHAS is a top choice for teams already building on GitHub. It doesn’t require additional infrastructure or licenses beyond GitHub Enterprise, and developers love how security feedback fits neatly into their existing workflow.
The main tradeoff? It’s GitHub-only. If your org spans multiple platforms or needs more advanced features like DAST or IaC scanning, GHAS won’t cover it all. Still, for most use cases, it’s a fast, developer-friendly way to catch vulnerabilities early—without buying another product. Let’s breakdown what GHAS offers even more:
Pros:
- Native GitHub integration (alerts directly in PRs and repos)
- Secret scanning & push protection
- Dependabot SCA for automated dependency updates
Cons:
- Narrower configurability and scan customization
- Less emphasis on mobile/binary (APK/IPA) testing
- Fewer built-in runtime/DAST and post-deployment features
- Active-commiter pricing can be costly at scale
Pricing:
- Free for public repositories (code and secrets scanning)
- GitHub Secret Protection: $19 per active committer/month
- GitHub Code Security: $30 per active committer/month
Gartner Rating: 4.5/5.0
GHAS Reviews
Peerspot rates GHAS a solid 4.⅘
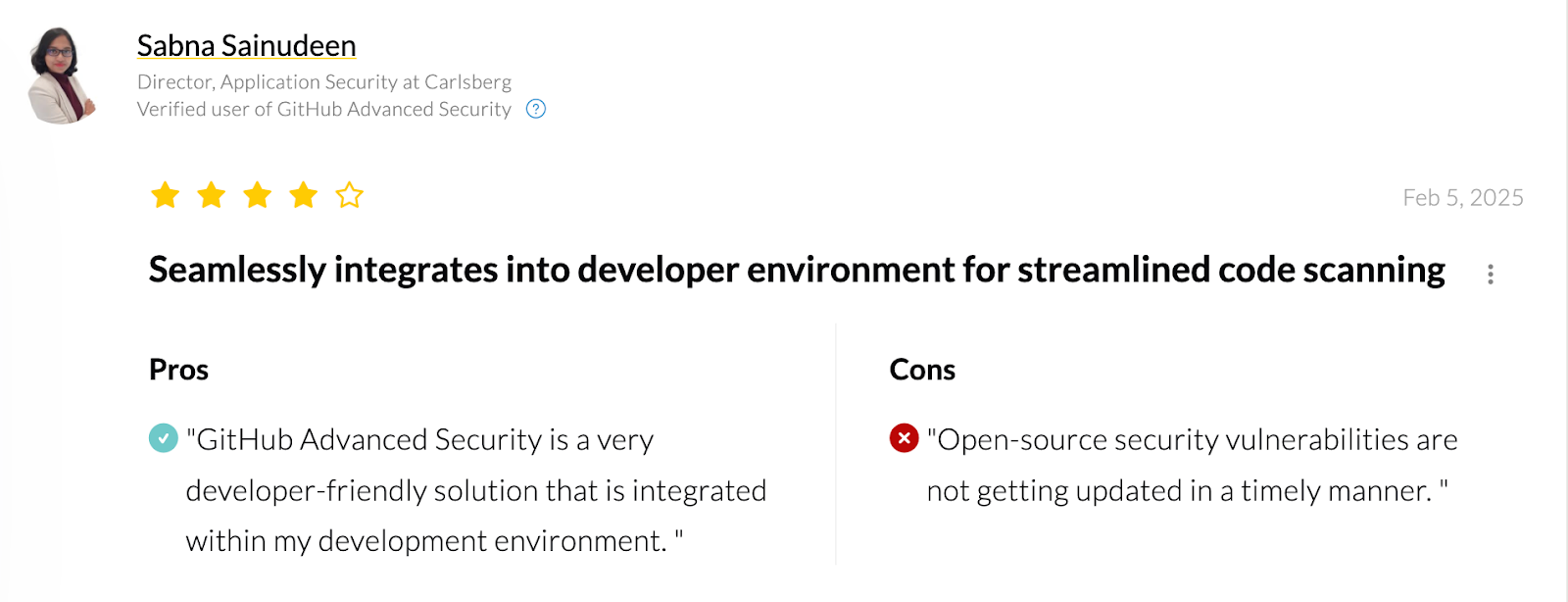
4. GitLab Ultimate

GitLab Ultimate is GitLab’s top-tier plan, bundling a wide array of built-in security features into its DevOps platform. It includes SAST, DAST, container and dependency scanning, secret detection, and infrastructure-as-code checks—all triggered natively through GitLab CI pipelines.
Rather than building custom integrations or using separate scanners, GitLab Ultimate enables security right out of the box for teams already using GitLab for version control and CI/CD.
Key Features:
- SAST via Templates:Built-in templates run language-specific linters and analyzers (e.g. Bandit, ESLint, Brakeman) on your code. Scan results appear directly in merge requests.
- DAST via ZAP:GitLab’s dynamic testing spins up your app and scans it using OWASP ZAP, catching real-time web vulnerabilities like SQLi or XSS.
- SCA & Container Scanning:Tools like Gemnasium and Trivy scan for known vulnerabilities in open-source dependencies and Docker images, feeding results into GitLab’s security dashboard.
- Secret Detection & IaC:Scans code for credentials and checks Terraform or CloudFormation configs for insecure patterns—automatically, with no manual setup required.
- Security Dashboard:A single view shows all active vulnerabilities across projects. Teams can create issues, triage risks, and validate fixes from the same interface they use to ship code.
Why Choose It:
GitLab Ultimate is a solid pick for teams already deep in the GitLab ecosystem. It automates security without adding tools or workflow complexity. You don’t get the same depth as an End-to-End Security platform, but for many teams, “good enough + built-in” beats “powerful but external.”
Ideal for small-to-medium engineering teams who want to stay secure without overloading their stack—or their security budget.
Pros:
- Secret detection and push protection within repos
- Built-in CI/CD
- Integrated vulnerability management dashboards
- Container image scanning and dependency scanning
Cons:
- Platform lock-in
- Post-deployment posture features are less emphasized
- Per-user pricing at scale can be costly
- Heavier platform complexity (longer onboarding and admin overhead)
Pricing:
Custom pricing
Gartner Rating: 4.4/5.0
GitLab Ultimate Reviews
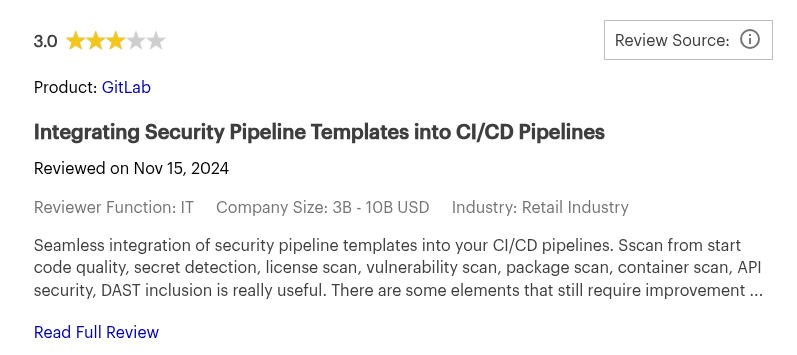
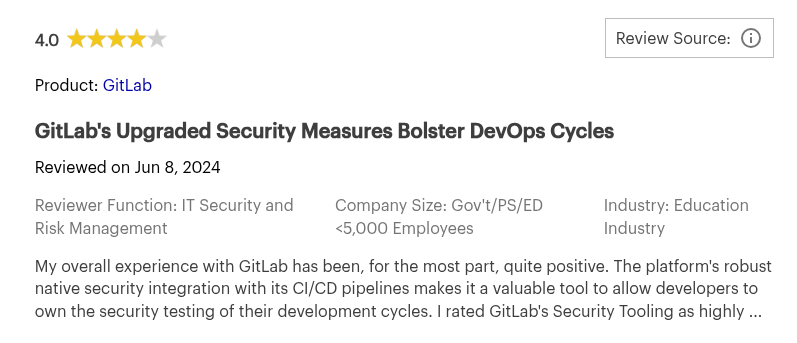
5. Snyk

Snyk is a security platform that originally gained traction through its intuitive open-source vulnerability scanning and ease of use. Over time, it has expanded to include Snyk Code (SAST), Snyk Container, and IaC scanning.
Key Features:
- Open Source Vulnerability Scanning (SCA): Snyk checks your libraries (npm, Maven, PyPI, Docker, etc.) against its vulnerability database and notifies you of issues.
- Snyk Code (SAST): Acquired from DeepCode, this fast, AI-powered static analyzer flags issues like command injection, insecure APIs, and hardcoded secrets—with real-world examples.
- Container and IaC Scanning: Snyk Container scans Docker images for OS-level vulnerabilities. IaC support covers Terraform, Kubernetes, and CloudFormation, catching misconfigurations like open ports or public cloud buckets.
- CI/CD and Dev Tool Integrations: Works natively with GitHub, GitLab, Bitbucket, and IDEs like JetBrains and VS Code. You can even set it to auto-create pull requests that patch outdated libraries.
Why Choose It:
Snyk is ideal for engineering teams who want security tools that feel like part of their workflow. However, Snyk’s SAST engine may lag behind with large codebases like Checkmarx. Also generates a lot of false positives.
Pros:
- Open-source vulnerability database
- Lightweight scans
- Developer centered integrations
Cons:
- Pricing can escalate quickly
- Reliance on manual vetting for vulnerabilities which may delay updates for newly discovered threats.
- Reports of weaker support for certain languages or build systems (e.g., Gradle, Xcode)
Pricing:
- Free: $0 per contributing-developer/month
- Premium: $25 per contributing-developer/month. Minimum of 5 developers and a maximum of 10.
- Ultimate: Custom pricing
Gartner Rating: 4.3/5.0
Snyk Reviews
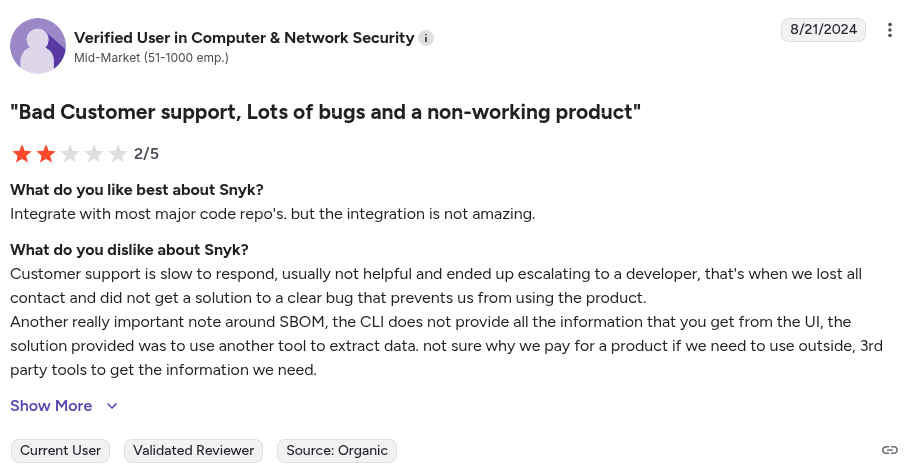
6. SonarQube
SonarQube is best known for improving code quality and cleanliness, but it also includes an expanding set of security-focused rules especially in its Developer and Enterprise editions. Built by SonarSource, it's often used internally by dev teams to enforce consistent code, detect bugs, and catch security issues early.
Many organizations already use it for quality gates and test coverage, so enabling its security features is often a natural next step. It supports 20+ languages and offers both on-prem and cloud-based SonarCloud versions.
Key Features:
- Static Code Analysis for Security and Quality: SonarQube scans code for logic flaws, code smells, and security vulnerabilities aligned with OWASP Top 10 and CWE. It flags SQL injection, hardcoded secrets, and misuse of cryptographic APIs.
- SonarLint for IDE Integration: Developers can catch issues in real time while writing code, thanks to its plugins for VS Code, JetBrains, Eclipse, and more.
- Secrets Detection: In recent updates, SonarQube added support for detecting API keys, credentials, and other sensitive data in code to prevent accidental exposure.
- Code Quality Gates: Teams can enforce rules like “no new critical vulnerabilities” or “maintain 80% test coverage,” helping maintain clean, secure codebases over time.
- Centralized Reporting: Its dashboard shows trends over time, so you can visualize improvements (or regressions) in your security posture release over release.
Why Choose It:
SonarQube is perfect for teams looking to combine code quality and basic security in one tool. While it doesn’t offer dynamic analysis or deep open-source scanning, it reliably catches many of the most common and dangerous vulnerabilities early, and it’s easy to set up and manage.
If your team already uses SonarQube for quality control, enabling security checks adds minimal overhead. And for security-light organizations or teams wanting a cost-effective Veracode alternative, the Developer Edition packs in plenty of value.
Pros:
- Developer-friendly feedback in real-time.
- Provides code quality checks and security scanning in one tool.
- Customizable rule-sets and quality gates.
- Free community edition
Cons:
- Limited depth in security scanning (misses runtime, DAST, SCA breadth)
- Advanced security features and language support locked behind higher plans.
- Reports of increased false positives for certain codebases
Pricing:
SonarQube’s pricing comes in two categories: cloud-based and self-managed.
Gartner Rating: 4.4/5.0
SonarQube Reviews
Besides Gartner, Capterra also rates SonarQube a 4.5/5
Comparing Veracode Alternatives
To make the decision easier, below is a comparison of Veracode and these top alternatives on key aspects:
Comparing Veracode Alternatives
Note: All tools above (except SonarQube Community) offer commercial plans. False positive levels are relative assessments; actual results may vary by project.
Use the comparison table to identify which alternative aligns with your priorities – for instance, Aikido excels in breadth and low noise, GHAS wins on integration, Snyk on open-source coverage, etc. Next, we’ll address some common questions when choosing a Veracode alternative.
Conclusion
Veracode helped define application security. But for modern teams, it's no longer enough. Today’s best alternatives focus on speed, clarity, and developer experience.
If you’re tired of security theater—scans that generate alerts but no action— and looking for a tool that prioritises real outcomes: fewer false positives, faster fixes, and seamless CI/CD integration, Aikido Security is your solution.
Aikido Security stands out for offering full-stack coverage (from SAST and code quality, to cloud config scanning) with a developer-first interface and near-zero noise. It’s built to be used—not avoided.
Most of the tools in this guide offer free trials or community plans. Try a few. See what fits your workflow. The best AppSec solution is the one your team actually enjoys using.
Ready to move on from Veracode’s legacy friction? Schedule a demo or start your free trial today—no credit card required.
Note: False positive levels are relative assessments; actual results may vary by project.
Use the comparison table to identify which alternative aligns with your priorities. For instance, Aikido excels in breadth and low noise, GHAS is great for existing Github users.
You Might Also Like:



