If you work in AppSec, chances are you’ve heard of Snyk and Aikido Security, and even weighed them against each other to see which one best fits your organization's security needs.
This guide summarizes verified third-party reviews of Aikido Security and Snyk from G2, the world’s largest and most trusted software marketplace, with over 100 million professionals relying on it each year to make software decisions.
We’ll evaluate each tool across key criteria such as functionality, developer experience, customer satisfaction, and much more.
If you’d like to explore further, you can view the full reviews directly on G2, including individual listings for Aikido Security and Snyk, as well as comparison reviews that position Aikido Security as a Snyk alternative.
TL:DR
Aikido Security is an AI-driven application security) platform designed to secure every aspect of the software development lifecycle from source code and dependencies to APIs, cloud configurations, and runtime environments, all within a developer friendly workflow.
It offers best-in-class, modular scanners across SAST, SCA, DAST, API security, cloud scanning, secrets detection, and runtime protection. Each scanner can be used as a standalone solution and enabled as your team’s security needs grow.
The result? end-to-end application security, faster remediation, and seamless integration into existing development workflows.For startups and enterprises, Aikido Security consistently ranks at the top in pilots thanks to its ease of onboarding, transparent flat-rate pricing, and its ability to correlate and prioritize vulnerabilities across the entire SDLC.
What is Aikido Security?
Aikido Security website
Led by serial CTO and CEO Willem Delbare, Aikido Security is an AI-driven security platform for developers. After many years using other overly complex application security products, Delbare founded Aikido Security to fix security for CTOs and developers with a code-to-cloud security platform designed to help engineering teams get security done.
Engineering teams execute faster with Aikido Security thanks to its developer-friendly features such as: centralized scans, AI-driven false positive reduction, developer-native UX, automatic risk triage, risk bundling, easy step-by-step risk fixes, and LLM-powered autofixes for different issue types.
What is Snyk?
Snyk is a well-known security company that positions itself as a “developer-oriented” security tool, for teams to identify and fix vulnerabilities in their code, open-source dependencies, and container images. Snyk is an early player in the “shift left” security movement and was founded 10 years ago in Tel Aviv and London and is currently headquartered in Boston, USA.
Aikido vs Snyk Alternative at a Glance
- Aikido Security:
- G2 Rating : 4.7/5.0
- Market Segments: SMBs to Enterprises
- Entry-Level Pricing: Free forever tier
- Snyk:
- G2 Rating : 4.5/5.0
- Market Segments: Mid-Market to Enterprise
- Entry-Level Pricing: Free
Overall, Aikido Security is heavily favored by small to medium-sized businesses and enterprises, while Snyk has broader adoption among mid-market organizations, especially enterprises. Both platforms offer free plans, making them accessible for individual developers and smaller teams.
Category Ranking Overview
User Experience
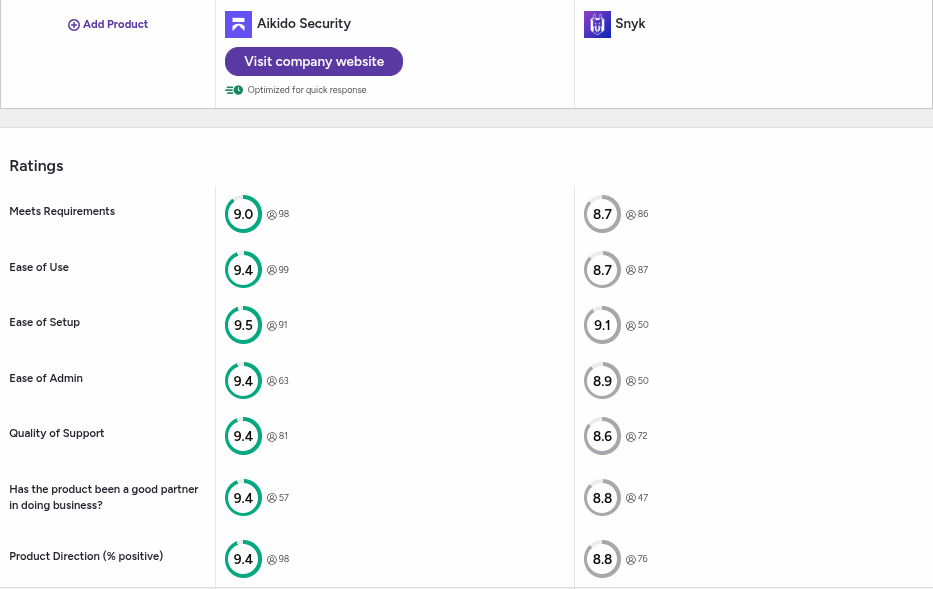
Ease of Use
- Aikido Security: Rated 9.4, users praise its intuitive interface and streamlined workflows. It’s designed with a developer-friendly approach, ensuring minimal friction when integrating into existing CI/CD pipelines and workflows.
- Snyk: Rated 8.7, while still user-friendly, some reviewers note a steeper learning curve, especially for teams unfamiliar with DevSecOps tools.
Ease of Setup
- Aikido Security: With a score of 9.5, users love Aikido Security’s quick onboarding process and minimal configuration requirements.
- Snyk: Rated 9.1, Snyk’s setup is straightforward, but users have reported occasionally encountering challenges integrating with less common tools.
Ease of Administration
- Aikido Security: Scoring 9.4, system administrators find it simple to manage teams, permissions, and integrations.
- Snyk: Rated 8.9, administration is effective but can become complex in larger organizations.
Support and Product Direction
Quality of Support
- Aikido Security: With a score of 9.4, users frequently commend its support team as responsive and knowledgeable . Most testimonials highlight fast support from the Aikido Security team and founders.
- Snyk: Rated 8.6, support is OK, generally reliable but sometimes slower for free-tier users.
Product Direction
- Aikido Security: Users rank Aikido with a 9.4 score, reflecting user confidence in its innovative roadmap and consistent feature updates.
- Snyk: Rated 8.7, appreciated for its focus on open source and developer-centric tools but slightly lagging in comprehensive feature rollouts.
Aikido vs Snyk Alternative Feature Comparison
If you are looking for a Snyk alternative, it is important to note the specific functionalities that each platform offers. While Snyk offers SAST, IaC, Software Composition Analysis, and vulnerability scanning, Aikido Security offers more functions and features within its platform.
Snyk offers a total of 4 products, While Aikido Security offers over 10 products , including SAST, DAST, Software Composition Analysis (SCA), IaC, container image scanning, secret scanning, malware scanning, API scanning, license risk scanning, local custom scanning, cloud (CSPM) security and much more. Aikido Security’s products are designed as modules, allowing teams to enable them as their needs grow.
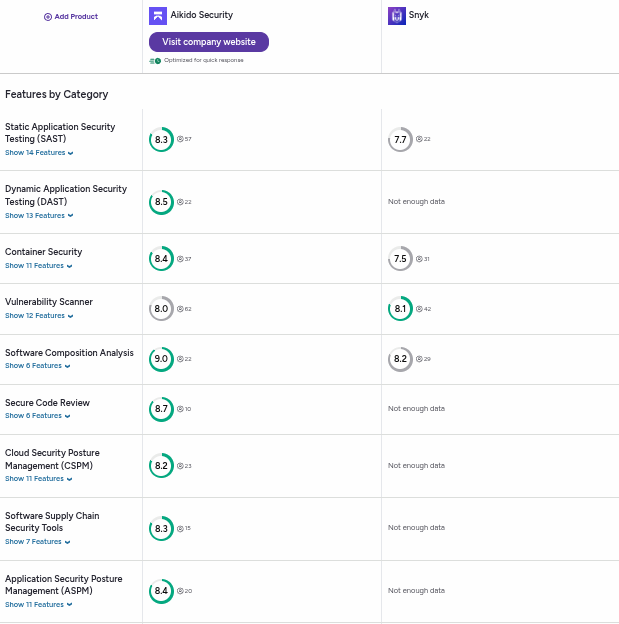
Static Application Security Testing (SAST)
What is it? SAST is a method used to identify vulnerabilities in source code before deployment.
- Aikido Security: Rated 8.3, Aikido Security excels at identifying and linking vulnerabilities in source code, and presenting actionable insights.
- Snyk: Rated 7.7, Snyk is effective but is often criticized for generating more false positives compared to competitors.
Dynamic Application Security Testing (DAST)
What is it? DAST is a technique that scans live applications to detect runtime vulnerabilities.
- Aikido Security: Scoring 8.5, users appreciate its ability to identify runtime vulnerabilities with minimal configuration.
- Snyk: Not enough data available to assess Snyk’s DAST capabilities.
Container Security
What is it? Container Security is the process of identifying vulnerabilities in containerized applications and images.
- Aikido Security: Rated 8.7, it provides deep insights into container images and vulnerabilities across registries.
- Snyk: Rated 7.5, strong for basic container scanning but less comprehensive in advanced scenarios.
Software Composition Analysis (SCA)
What is it? SCA is the practice of detecting vulnerabilities in open-source dependencies and third-party libraries.
- Aikido Security: Scoring 9.0, it combines open-source dependency scanning with enhanced malware detection, ensuring robust protection.
- Snyk: Rated 8.2, Snyk is effective at detecting known vulnerabilities in open-source libraries but less advanced in identifying malicious packages.
Secure Code Review
What is it? Secure Code Review is the process of analyzing source code to detect vulnerabilities, bugs, and quality issues before deployment.
- Aikido Security: Rated 8.3, users highlight Aikido Security’s Code Quality module with its AI-assisted risk prioritization and automated remediation features, such as one-click fixes and automated fix pull requests..
- Snyk: Not enough data available to assess Snyk’s code review capabilities.
Application Security Posture Management (ASPM)
What is it? ASPM is a framework for managing and improving the security posture of applications across their lifecycle.
- Aikido Security: Scored 8.4, thanks to its proactive approach to identifying and resolving security risks in application environments.
- Snyk: Not enough data available to assess ASPM capabilities.
Software Supply Chain Security (SSCS) Tools
What is it? Software Supply Chain Security (SSCS) is the practice of securing every aspect of the software lifecycle, from code to deployments.
- Aikido Security: Rated 8.3, users trust Aikido Security’s to secure their SDLC thanks to its AI-driven risk correlation, malware detection engine and track record of identifying new malware campaigns (such as Shai Hulud 2.0 and September NPM outbreak) before competitors.
- Snyk: Not enough data available to assess Snyk’s SSCS capabilities.
Cloud Security Posture Management (CSPM)
What is it? CSPM is a toolset for monitoring and securing cloud environments by identifying misconfigurations and compliance issues.
- Aikido Security: Rated 8.2, Aikido Security integrates seamlessly into multi-cloud environments(AWS, GCP, Azure), providing clear misconfiguration insights.
- Snyk: Not enough data is available to evaluate Snyk’s CSPM features.
Vulnerability Scanner
What is it? A Vulnerability Scanner identifies and evaluates security vulnerabilities in systems and software.
- Aikido Security: Rated 8.0, Aikido Security is effective at pinpointing vulnerabilities with clear remediation guidance.
- Snyk: Scored 8.1, valued for its extensive library of known vulnerabilities but criticized for frequent noise in results.
To help you compare the capabilities of both platforms, the table below summarizes it for you.
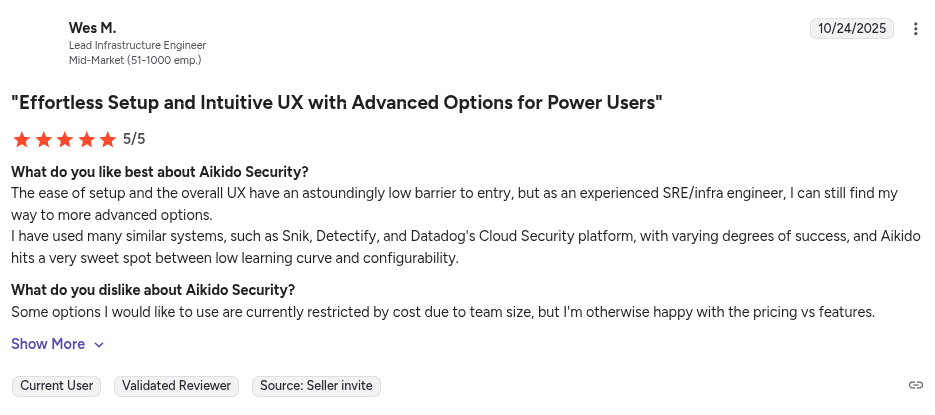
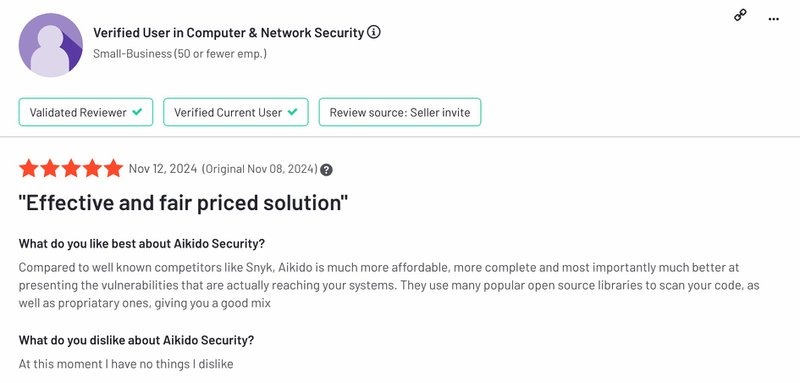
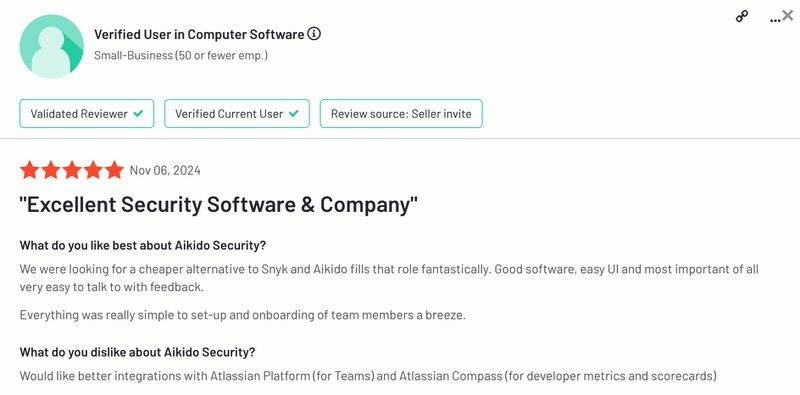
Verified Snyk vs Aikido customer testimonials:
Below are the reviews from verified users that have used both Aikido Security and Snyk.
Users also Shared:
“...really like that they made it easier to do local CLI, kinda a big part of what i’m missing from Snyk…” - G2 Reviewer
We hope this snapshot of G2 user feedback helps you evaluate your options when considering Aikido Security as an alternative to Snyk. If you’re curious to see Aikido Security in action, you can get started right away and run your first scan in as little as 32 seconds. No credit card required.
Ready to improve your application’s security? Start your free trial or book a demo with Aikido Security today.
FAQ
How effective is Snyk in detecting open-source vulnerabilities based on user reviews?
According to G2 reviews, Snyk is effective at identifying open-source vulnerabilities, especially in dependencies, and integrates well into CI/CD workflows. Users appreciate its large vulnerability database and timely alerts, though some note that high volumes of findings can require extra triage. Teams seeking context-based prioritization and reduced alert noise often explore alternatives like Aikido Security thanks to its AI-driven risk prioritization and reachability.
What are common challenges users face with Snyk as reported in G2 reviews?
Users frequently report challenges such as alert fatigue, limited context on exploitability, and scaling costs, along with a learning curve when configuring policies across multiple repositories. These pain points have led some teams to evaluate platforms that automatically correlate findings and offer automated remediation features, such as Aikido Security.
Is Snyk recommended by users on G2 for application security?
Snyk is generally recommended for application security, with reviewers citing strong dependency scanning and good integrations. However, its recommendations often come with side-notes about false positives, high volume alert and complexity, prompting some teams to consider more streamlined, end-to-end solutions like Aikido Security.
What are the overall user reviews for Snyk on G2?
Overall, Snyk receives positive ratings on G2 for its vulnerability detection and DevSecOps alignment. While trusted and widely used, teams looking for lower noise, broader coverage, and actionable insights often consider platforms like Aikido Security.
You Might Also Like:



