Modern applications are complex, distributed, and constantly changing, which makes security testing harder than ever. As different components are validated at different stages of the software lifecycle, some vulnerabilities can be caught before an application is deployed, while others only surface at runtime.
Understanding where and when vulnerabilities appear in an application is essential to securing it effectively. Two of the most widely used approaches to address this challenge are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
In this article, we’ll explore how both approaches work, their strengths and limitations, and provide a clear side-by-side comparison to help you choose the right approach for your security needs.
SAST vs. DAST
SAST analyzes the internal part of your code from the inside out, while, DAST tests from the outside in.
You can think of it this way:
- SAST tools examine your source code before your application is deployed, to catch issues such as insecure functions, hardcoded credentials, or logic flaws during development.
- DAST tools, on the other hand, runs security tests while the application is live, probing it like an attacker would to identify exploitable weaknesses such as SQL injection, XSS, or authentication bypasses.
Both are essential, but they serve different purposes at different stages of the SDLC.
If you’re looking for a trusted security platform that provides category-leading SAST and DAST, Aikido Security is the top choice. Organizations that use Aikido for SAST and DAST can catch vulnerabilities early in development and validate security once applications are running.
Aikido security’s SAST module uses AI to reduce false positives by up to 85%, by continuously refining rules and linking findings. Teams can also create custom rules to detect risks unique to their codebase. Each finding is then ranked based on context and risk level ensuring teams focus on the most critical vulnerabilities first,with AI-generated fixes provided to speed up remediation.
On the other hand, Aikido’s DAST module gives developers clear visibility into their attack surface. It scans both public and self-hosted applications for common vulnerabilities, and with authenticated DAST, it validates whether logged-in users can bypass controls or access sensitive data. Findings are further explained in plain language, allowing teams to analyze issues without in-depth security expertise.
Beyond SAST and DAST, it also offers SCA, API security, cloud scanning, secrets detection, AI pentesting and much more, all available as standalone scanners or combined into a suite.
Along with its modular architecture, Aikido Security uses AI to correlate and prioritize findings across the entire SDLC, reducing noise and highlighting vulnerabilities that are truly exploitable.
What Is Application Security Testing?
Application security Testing (AST), is the practice of identifying, fixing, and preventing vulnerabilities at every stage of the software development lifecycle (SDLC), from initial design to production. It combines techniques such as code analysis, runtime testing, and attack simulation to uncover security flaws before attackers can exploit them.
Application security testing has several categories such as SAST, DAST, RASP, IaC scanning, pentesting, SCA, and much more, with SAST and DAST being some of the most widely adopted due to their coverage of pre-production and runtime environments.
What is SAST?
SAST, or Static Application Security Testing, is a “white-box” testing technique that analyzes an application's source code in a static or non-running state. a.
SAST allows developers to identify vulnerabilities early in the development (SDLC) process, like code development or code review phases. SAST tools integrate seamlessly into CI/CD pipelines and IDEs, so developers can secure their code as it's written and scan for vulnerabilities before committing changes to the repository.
What Can SAST Detect?
SAST can detect a broad range of vulnerabilities such as injection flaws (SQL injection (SQLi), cross-site scripting), hard-coded credentials, insecure data handling, and other OWASP Top 10 vulnerabilities. Some SAST tools, like Aikido Security, also scan and compare source code to databases of known security vulnerabilities like the National Vulnerability Database (NVD) and use AI to prioritize issues.
Think of it as having an expert review your code with a fine tooth comb, who gives you immediate feedback on issues they discover.
That being said, SAST tools are limited to the language they support and cannot be used to detect runtime or environment specific vulnerabilities, like configuration errors or runtime dependencies.
Pros of SAST
- Early Detection: Static analysis identifies vulnerabilities during development and build phases, long before software is deployed.
- IDE and CI/CD Integration: Most modern SAST tools integrate directly into IDEs and CI/CD pipelines, providing feedback on every commit or pull request.
- No Running Application Required: It works on static source code, making it ideal for early development, code reviews, and pull request checks.
- Precise Remediation Guidance: It can identify exact file paths and line numbers for vulnerabilities, often with data-flow context.
- Supports Secure Coding Practices: Flags insecure patterns and anti-patterns, improving overall code quality and long-term secure development habits.
- Comprehensive Code Coverage: It scans the entire codebase, including unexecuted or “dead” code paths that runtime testing may not reach.
- Compliance and Audit Support: Helps meet regulatory and industry requirements (PCI DSS, SOC 2) by providing evidence of secure development practices.
Cons of SAST
- No Exploitability Proof: SAST identifies potential weaknesses but not whether they are exploitable in real-world conditions.
- Limited to known Patterns and Rules: Most SAST tools rely heavily on predefined rules, which means it may miss complex logic flaws or attack techniques.
- Lacks Runtime Coverage: It cannot detect issues that only appear during execution, such as misconfigurations, authentication weaknesses, or environment-specific vulnerabilities.
- Language and Framework Dependent: It is limited to supported languages and frameworks; newer or less common stacks may be unsupported.
- Limited Visibility into Data-as-Code (DaaC) Risks: Generative AI-driven application inputs like prompts or RAG sources can influence behavior like executable logic. Traditional SAST tools are blind to indirect injection.
Why Does SAST Matter?
SAST’s early detection is crucial as it allows developers to address issues before the application is deployed, making it easier and less costly to fix problems early.
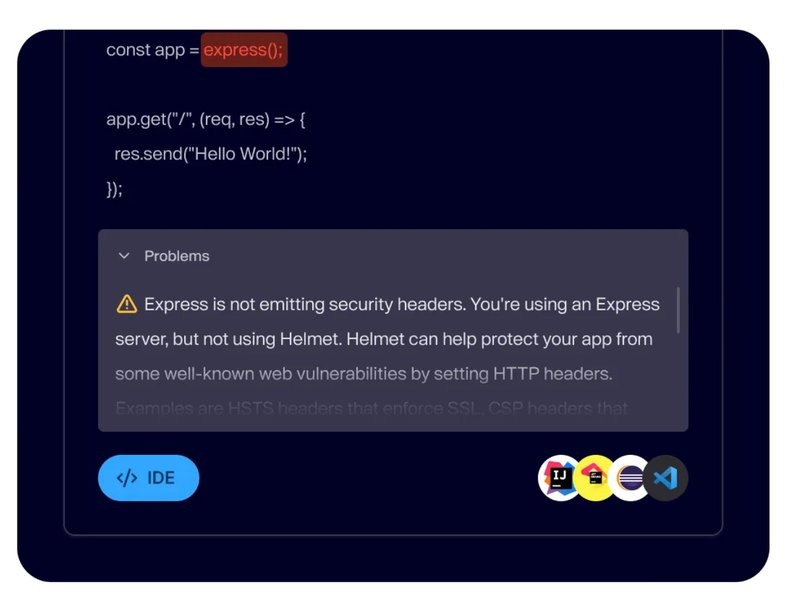
What is DAST?
DAST, or Dynamic Application Security Testing, is a “black-box” testing method that evaluates an application while it is running. DAST does not require source code access, rather, it takes an outsider approach to testing your applications security by simulating attacks on the application much like a hacker would.
DAST can also be called “surface monitoring” as it tests the surface or front-end of the web applications.
What Can DAST Detect?
DAST tools interact with the application via the user interface, testing various inputs, and observing the outputs to identify vulnerabilities such as authentication issues, server misconfigurations, cross-site request forgery, and other runtime vulnerabilities.
As DAST works at runtime, that means you need a working application before DAST tests make sense, which is usually around the pre-production and production phase.Because DAST works externally, and uses standardized protocols like HTTP to connect to your app,DAST is not tied to a specific programming language.
Pros of DAST
- No Source Code Access Required: Dynamic testing works from outside the application, using standard protocols (such as HTTP, gRPC)
- Detects Runtime and Configuration Issues: It identifies vulnerabilities that only appear during execution, such as authorization issues, and server misconfigurations.
- Language and Framework Agnostic: DAST is not tied to specific programming languages or frameworks since it tests application behaviour.
- Lower False-positive Rate Findings are based on behavior, which often results in fewer false positives compared to static analysis.
- Validates Security Controls: Dynamic testing confirms that security measures actually work as intended when the application is deployed.
Cons of DAST
- Limited Visibility into Root Causes: It cannot pinpoint the exact source code responsible for the issue.
- Late Stage Detection: DAST requires a fully functional, running application. This can make fixes more expensive and time-consuming as its running later in the SDLC
- Limited Coverage of Application Logic: It may miss vulnerabilities in unexposed or hard-to-reach application paths, especially those requiring complex user interactions.
- Potential Impact on Live Environments Aggressive testing against production systems can cause performance issues.
Why Does DAST Matter?
DAST is important for detecting issues that you cannot detect before deployment such as server or database misconfigurations, authentication and encryption issues that allow unauthorized access, or risks from web services that your application connects to..
Comparing SAST vs DAST
To help you compare both approaches, the table below summarizes it for you.
Using SAST and DAST Together
In this article, we covered the differences between SAST and DAST, and why both are essential for securing your applications. However, they only address a portion of AppSec, leaving other areas such as IaC, RASP, penetration testing, SCA, and more unprotected.
This means any security solution you choose needs to provide comprehensive coverage for not only SAST and DAST, but the entire application stack.
Aikido Security helps address this challenge with its developer-friendly, AI-driven AppSec platform. It offers modular scanners for SAST, DAST, Infrastructure-as-code configs, RASP, penetration testing, secrets detection and much more, while using AI to correlate issues across all scanners, reducing noise, and speeding up triage and remediation. All at an affordable, flat price.
By combining broad coverage with intelligent prioritization, Aikido makes it easier for teams to secure applications at every stage of the SDLC.
Ready to improve your application security? Start your free trial or book a demo with Aikido Security today.
FAQ
Why is application security testing important for developers?
Application security testing helps developers catch vulnerabilities early in the software development lifecycle, when fixes are faster, cheaper, and less disruptive. It reduces the risk of exploitable issues reaching production and encourages secure coding practices by providing continuous feedback during development. Tools like Aikido Security support this by embedding security checks with AI-assistance directly into developer workflows.
Is DAST specifically for web applications?
DAST is most commonly used for web applications and APIs because it tests applications over network protocols such as HTTP. Any application that exposes a network-accessible interface can benefit from DAST, including internal services and APIs.
What are common types of vulnerabilities detected by SAST and DAST?
SAST typically detects code-level vulnerabilities such as SQL injection, XSS attacks, insecure deserialization, and hard-coded secrets by analyzing source code and comparing insecure patterns against known vulnerability signatures, including data from CVE databases. While, DAST focuses on runtime issues like authentication flaws, authorization bypasses, and security misconfigurations.
Is penetration testing the same as DAST?
Penetration testing and DAST are not the same. DAST is an automated, repeatable testing method used throughout the SDLC, while penetration testing is usually a manual, time-boxed assessment performed periodically.
You Might Also Like:
- Top 10 AI-powered SAST tools in 2026
- Top 14 AppSec Tools in 2026
- Top 12 Dynamic Application Security Testing (DAST) Tools in 2026
- Best 10 Pentesting Tools for Modern Teams in 2026
- Best Tools for End-of-Life Detection: 2026 Rankings.
- The Top 13 Code Vulnerability Scanners in 2026
- Top Infrastructure as Code (IaC) Scanners in 2026

Secure your software now



.jpg)


