Orca Security is a cloud-native security platform (often classified as a CNAPP) that made its name with agentless scanning across AWS, Azure, and GCP. By reading cloud configuration and workload data directly from the hypervisor, Orca gave security teams a full-stack view of risks from exposed storage buckets to vulnerable OS packages all without installing agents. This one-shot visibility largely contributed to Orca’s popularity amongst enterprises needing quick cloud coverage.
However, over time, many developers and security leads have grown frustrated and are exploring alternatives. Common pain points include high alert noise (some call it “cloud security spam” due to endless low-priority findings), false positives or unactionable alerts, gaps in coverage like no code scanning, and pricing that feels out of reach for smaller teams.
As one reviewer put it:
"Orca provides a lot of information and can result in alert fatigue. There are some areas with vulnerability management that they can do better on." – G2 reviewer
Another gripe is that Orca’s enterprise focus comes with a hefty price tag:
"…might be a little expensive for small businesses." – G2 review
In short, teams appreciate Orca’s comprehensive approach but want leaner, more dev-friendly solutions that cut the noise and cost. The good news is that in 2026, several strong Orca alternatives address these gaps. In this post, we have selected the very best to enhance your CNAPP journey in 2026.
TL;DR
Aikido Security stands out as a compelling Orca Security alternative by unifying application and cloud security in one developer-friendly platform. While Orca offers solid CSPM and VM scanning coverage, Aikido matches that cloud security foundation and goes further with capabilities built for engineering teams: comprehensive code scanning (SCA, SAST, IaC),
Additionally, developers can leverage its AI-powered autofix that generates remediation code directly in your workflow, and runtime protection via Aikido Zen. The result is significantly less alert noise, faster time-to-fix, and frictionless flat-rate pricing.
Skip ahead to the Top 5 Alternatives:
- Aikido Security – Developer-first, security platform
- Aqua Security – Enterprise-grade cloud and container security
- Check Point CloudGuard – CSPM and network security for compliance-focused teams
- Palo Alto Networks Prisma Cloud – Broad cloud-native security suite (CNAPP)
- Sysdig – Runtime-focused container and Kubernetes security
Looking for more CNAPP and CSPM tools? Check out our Top Cloud Security Posture Management (CSPM) Tools in 2026 for a complete comparison.
What is Orca?
Orca Security is an agentless cloud security platform focused on cloud security posture management (CSPM) and cloud infrastructure risk visibility. It scans cloud environments to identify misconfigurations, vulnerabilities, and exposed assets without deploying agents.
The primary appeal of Orca is that security teams can go from zero to one hundred without having to manage installations across potentially hundreds of resources, saving multiple engineering hours, but that alone was not enough.
Why Look for Alternatives?
- Stalled innovation:
Orca was a category leader several years ago and helped define the CSPM and early CNAPP space. However, the platform has seen limited innovation compared to newer entrants, allowing competitors to move faster in areas like risk prioritization, usability, and developer experience. - Displacement by newer platforms:
As the market matured, more modern CNAPPs have emerged with broader coverage and better user experience. Tools like Wiz, Prisma Cloud, and Aikido now offer stronger correlation, shift-left capabilities, or developer-first workflows, reducing Orca’s differentiation. - Reliance on partnerships for code security:
Orca does not provide native code scanning. Instead, it relies on partnerships, such as integrations with Snyk, to extend into application security. This increases tool sprawl and makes Orca less attractive to teams looking for a unified platform. - High alert volume and noise:
Orca often generates large numbers of findings with limited built-in suppression, leading to alert fatigue and making it harder to focus on truly critical risks.
Key Criteria for Choosing an Alternative
When evaluating Orca Security alternatives, prioritize solutions that offer:
- Comprehensive Coverage: Aim for platforms that cover cloud misconfigurations (CSPM), container image scanning, and ideally code scanning too. The goal is to avoid juggling five different tools for each layer of your stack.
- Low Noise, High Signal: The best alternatives minimize false positives by adding context. For example, they might flag a vulnerability only if it’s exploitable in your environment. Fewer but more actionable alerts mean less burnout for your team.
- Developer-Friendly Workflow: Choose tools that meet devs where they work – look for CI/CD pipeline integration, IDE plugins for real-time code feedback, and even AI-powered auto-fix features. A solution that fits into your DevOps process will see much higher adoption.
- Fast Deployment & Performance: Modern teams move fast, and your security tool should too. Prefer agentless or lightweight solutions that you can deploy in minutes and that won’t slow down your CI/CD pipeline or runtime environment.
- Transparent Pricing & Scalability: Security budgets aren’t infinite. Favor alternatives that offer clear, predictable pricing (flat or per-user plans) and a scalable architecture. You want something you can start small with and grow into – not a tool that requires six figures and a six-month POC to even get started.
- Compliance & Reporting: If compliance is a big driver (SOC 2, ISO, etc.), ensure the alternative provides built-in compliance checks and easy reporting. Orca does this well, so an alternative should match or exceed those capabilities.
With these criteria in mind, let’s explore the top Orca Security alternatives and how they compare.
Top Alternatives to Orca Security in 2026
Below are five of the best alternatives to Orca Security. Each takes a different approach to cloud and application security.
1. Aikido Security
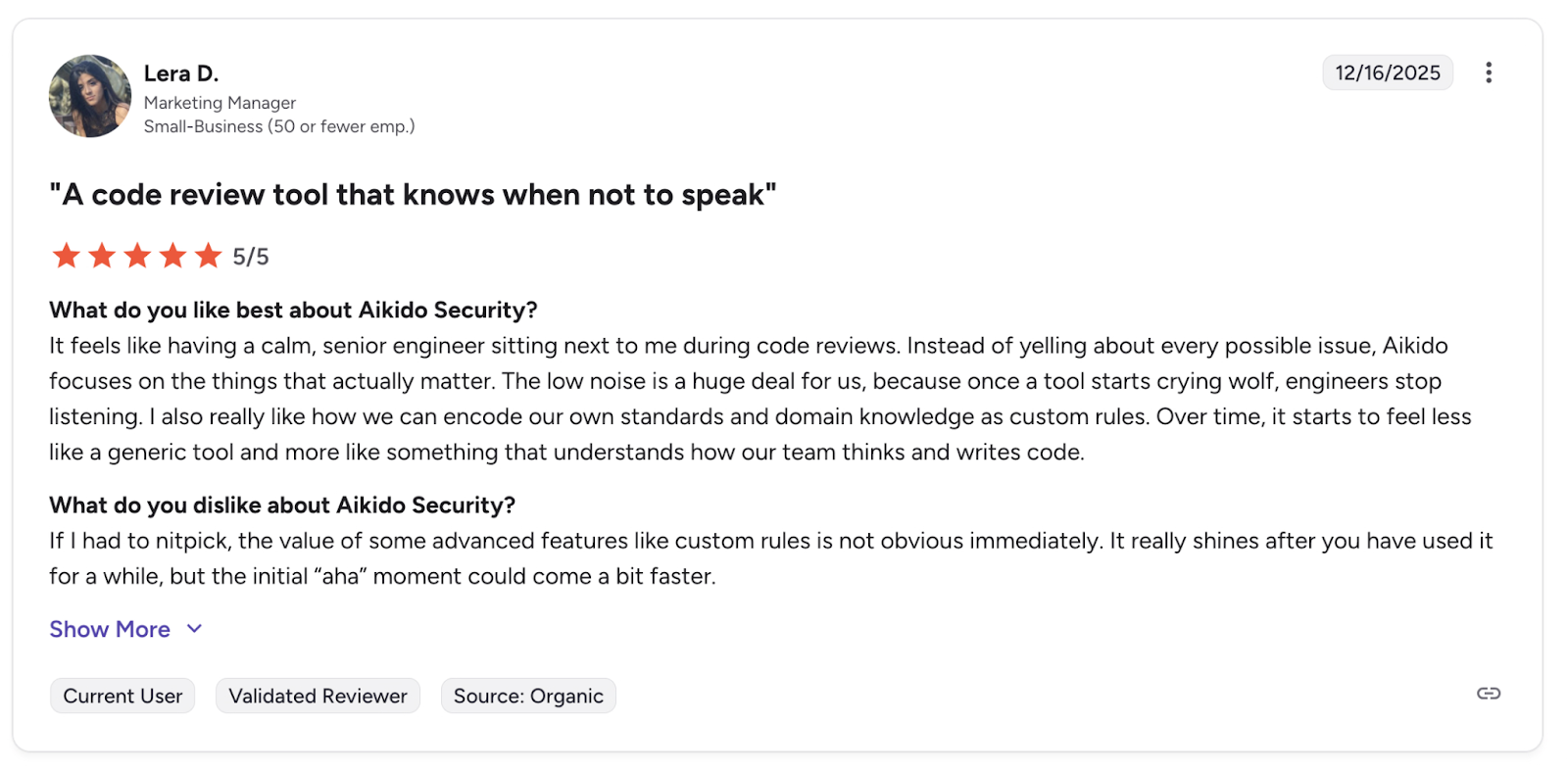
Aikido Security is a security platform, natively integrating security functions that engineering teams actually need, such as code scanning , container image scanning, and Infrastructure-as-Code (IaC) analysis all without relying on third-party partnerships or bolted-on integrations.
This matters because platforms like Orca have increasingly turned to partnerships (e.g., with Snyk for code security) to fill gaps in their offering. That means you're left deciding whether Orca alone is enough, or whether you need to juggle multiple vendors, contracts, and dashboards.
In addition, Aikido has better usability and developer experience, and comes equipped with AI Autofix for SAST & IaC, and AutoTriage.
Key Features
- Unified code and cloud security:
Provides CSPM for AWS, GCP, and Azure alongside native SAST, secrets detection, SCA, IaC scanning, and container image scanning, all within one platform. - AI Autofix for SAST and IaC:
Automatically suggests one-click fixes for code and configuration issues, helping developers remediate vulnerabilities faster without deep security expertise. - Developer-first workflows:
Integrates directly into CI/CD pipelines and IDEs, delivering immediate, actionable feedback where developers already work. - Alert suppression and prioritization:
Uses contextual analysis to reduce noise, surface real risks, and prioritize issues based on exploitability and impact. - Advanced application protection:
Includes API security, next-generation DAST, and optional runtime application self-protection through Aikido Zen.
Pros
- Native code scanning without third-party integrations
- AI-powered remediation for faster fixes
- Strong alert noise reduction and issue prioritization
- Clear, human-readable findings with solution guidance
- Built by developers for developers, with strong usability
- Short evaluation cycle with fast onboarding
- Transparent, developer-based pricing with a lower total cost
Ideal Use Case
Developer-led teams and DevSecOps organizations that want to secure code, infrastructure, and applications early and continuously without managing multiple vendors. Aikido is particularly well suited for teams moving away from Orca due to alert fatigue, lack of code security, or enterprise pricing complexity.
Pricing
Flat, per-developer pricing with a free tier and a fully functional free trial. No per-asset or per-cloud charges.
G2 rating: 4.6/5
2. Aqua Security
Aqua Security is a cloud native application protection platform that originated with container and Kubernetes security and later expanded into a broader CNAPP offering. The platform focuses heavily on container image scanning, runtime workload protection, and cloud posture management, making it a common choice for organizations running Kubernetes and serverless workloads in production.
Key Features
- Container and Kubernetes security:
Scans container images for vulnerabilities and misconfigurations and enforces security at runtime by detecting anomalous behavior in running workloads. - Runtime workload protection:
Uses agents to monitor containers and hosts, enabling real-time threat detection and policy-based enforcement in production environments. - Cloud security posture management:
Monitors AWS, Azure, and GCP for misconfigurations, compliance gaps, and risky configurations, with prioritization informed by runtime context. - Software supply chain security:
Integrates Trivy for vulnerability and IaC scanning, covering Terraform, Kubernetes manifests, and Dockerfiles. Focus remains on infrastructure and container artifacts rather than application code.
Pros
- Strong container and Kubernetes runtime protection
- Deep visibility into running workloads
- Well suited for Kubernetes-heavy environments
Cons
- Heavier operational overhead due to agent-based runtime monitoring
- Limited depth in application code scanning compared to developer-first platforms
- Less emphasis on SAST, SCA, and developer remediation workflows
- Can be complex to manage at scale without dedicated platform or DevOps teams
Ideal Use Case
Organizations running large-scale Kubernetes or containerized workloads that require runtime enforcement and production workload protection. Aqua is best suited for platform and DevOps teams focused on securing cloud workloads rather than application code.
Pricing
Custom pricing based on environment size, workloads, and enabled modules. Pricing details are not publicly listed and typically require a sales engagement.
3. Check Point CloudGuard
Check Point CloudGuard is a cloud security platform focused on cloud security posture management and cloud network protection. It is commonly adopted by large enterprises with strict compliance requirements, particularly those already using Check Point firewalls in on-prem or hybrid environments. Compared to Orca, CloudGuard offers more active prevention and policy enforcement, but with greater operational complexity.
Key Features
- Cloud security posture management and compliance:
Continuously scans AWS, Azure, and GCP for misconfigurations and compliance violations, with built-in policies for standards such as PCI-DSS and HIPAA. Supports automated remediation and provides network topology visualization to identify exposed assets. - Cloud network protection:
Inspects cloud traffic using virtual gateways with IDS and IPS capabilities, applying real-time protections against intrusions and malware using Check Point threat intelligence. - Unified security management:
Centralized management through the Check Point Infinity portal, enabling consistent policy enforcement and automated response across cloud and on-prem environments.
Pros
- Strong CSPM and compliance enforcement
- Deep network security capabilities
- Centralized management for hybrid and multi-cloud environments
Cons
- Higher operational complexity than agentless CNAPP platforms
- Less developer-focused than modern application security tools
- Limited depth in application code scanning
- Heavier setup and maintenance requirements
Ideal Use Case
Large enterprises with compliance-driven security programs that require strong CSPM, network-level threat prevention, and centralized governance across cloud and on-prem environments. CloudGuard is particularly suitable for organizations already invested in the Check Point ecosystem.
Pricing
CloudGuard pricing is module-based and typically requires a sales engagement. Costs vary based on cloud footprint, enabled features, and deployment model.
4. Palo Alto Networks Prisma Cloud

Prisma Cloud is a comprehensive cloud-native security platform from Palo Alto Networks, combining cloud security posture management, workload protection, identity security, and code/IaC scanning. It is often adopted by large enterprises seeking end-to-end visibility and full-stack protection. Compared to Orca, Prisma Cloud offers broader coverage including code repository and runtime security.
Key Features
- Cloud posture and IAM security:
Monitors AWS, Azure, and GCP for misconfigurations, overly permissive access, and compliance violations. Supports enforcement of least-privilege IAM and flags unused access keys, going beyond standard CSPM. - Code and IaC security (shift-left):
Scans Infrastructure-as-Code templates (Terraform, CloudFormation, Helm) and code repositories for vulnerabilities, policy violations, and hardcoded secrets. Provides integrated application security posture management (ASPM) checks. - Enterprise management:
Offers granular RBAC, multi-tenant dashboards, and integration with SIEM and SOAR tools. Benefits from Palo Alto’s ecosystem for unified cloud and network visibility.
Pros
- Full-stack protection across cloud, code, and runtime
- Shift-left scanning for IaC and code repositories
- Enterprise-grade governance and multi-tenant capabilities
- Strong integration with Palo Alto security ecosystem
Cons
- High operational complexity and resource requirements
- Expensive compared to smaller CNAPPs or developer-focused platforms
- Overkill for small or dev-centric teams
- Can require significant effort to manage and tune policies
Ideal Use Case
Large enterprises seeking a single platform for comprehensive cloud and application security, including runtime, code, and identity. Prisma Cloud is suited for organizations with the resources to manage a full-stack CNAPP and the need for enterprise-grade visibility and compliance.
Pricing
Custom pricing based on cloud footprint, enabled modules, and enterprise features. Requires engagement with Palo Alto Networks sales.

5. Sysdig
Sysdig is a container and cloud security platform focused on real-time runtime protection for containers and Kubernetes. It is best known for its use of the open-source Falco engine to detect suspicious behavior at runtime. Compared to Orca’s agentless, snapshot-based scanning, Sysdig emphasizes continuous visibility and live threat detection in production environments.
Key Features
- Real-time threat detection:
Uses agents or Kubernetes instrumentation to monitor container and host activity continuously. Falco rules detect suspicious behavior such as shell execution in containers or unauthorized file system changes. - Runtime risk prioritization:
Correlates vulnerabilities with runtime usage to identify which issues are actively exploitable, reducing noise by focusing on vulnerabilities that are actually in use. - Incident response and forensics:
Captures detailed runtime activity using kernel-level tracing, enabling investigation and replay of incidents for forensic analysis and compliance purposes.
Pros
- Strong real-time runtime security for containers and Kubernetes
- Effective prioritization using runtime context
Cons
- Requires agents and runtime instrumentation
- Limited focus on application code security
- Less coverage of SAST, SCA, and developer workflows
- Better as a complementary tool than a standalone platform for full coverage
Ideal Use Case
Teams running production Kubernetes environments that require real-time threat detection and runtime visibility. Sysdig is well suited for DevOps and platform teams focused on live workload protection and is often paired with developer-first tools for code, IaC, and cloud security.
Pricing
Sysdig pricing is usage-based and depends on monitored workloads, hosts, and enabled features. Pricing details typically require a sales engagement.
6. Wiz
Wiz is a cloud security platform focused on agentless cloud security posture management and risk prioritization across cloud environments. It is widely adopted for its ease of deployment and fast time to value, particularly in large multi-cloud environments. Compared to Orca, Wiz offers a more modern user experience and stronger risk correlation, but remains primarily cloud-infrastructure focused rather than application- or developer-centric.
Key Features
- Agentless cloud security posture management: Scans AWS, Azure, GCP, and Kubernetes environments without agents to identify misconfigurations, exposed assets, and compliance violations.
- Risk graph and attack path analysis: Correlates misconfigurations, vulnerabilities, identities, and network exposure into attack paths, helping teams prioritize the most critical risks based on real-world exploitability.
- Vulnerability and container image scanning: Identifies vulnerabilities in VMs, container images, and cloud workloads, with contextual prioritization based on exposure and permissions.
- Cloud identity security: Analyzes IAM roles, permissions, and relationships to detect excessive privileges and risky access paths across cloud environments.
Pros
- Fast deployment with no agents required
- Strong risk prioritization and attack path visualization
- Well suited for large, complex cloud environments
Cons
- Limited depth in application code security
- No native SAST or developer-focused remediation workflows
- Shift-left capabilities are weaker than developer-first platforms
- Relies heavily on infrastructure context rather than code-level insight
Ideal Use Case
Security teams managing large multi-cloud environments that need fast visibility, strong risk prioritization, and minimal operational overhead.
Pricing
Custom pricing based on cloud footprint and enabled modules.
Comparison Table
Conclusion
Many teams in 2026 are rethinking their reliance on Orca Security. Whether it’s the volume of unfiltered alerts, the gaps in coverage (no code insight), or the high cost of scaling Orca, the reality is that modern security requires a more tailored approach.
Platforms like Aikido Security show that you can have comprehensive cloud and application securitywithout the bloat. Other alternatives cater to specific needs (containers, compliance, etc.), so choose what fits your priorities. Teams are discovering that by switching to leaner, developer-friendly solutions, they can boost security visibility and velocity at the same time.
FAQ
You Might Also Like:

Secure your software now






