Wiz.io is a Cloud Native Application Protection Platform (CNAPP) with an integrated Cloud Security Posture Management (CSPM) solution. It helps organizations identify vulnerabilities, misconfigurations, and risks across their IT landscape, from “code to cloud.” Its rapid adoption and $10B valuation are due its agentless, graph-based scanning approach, which gives security teams deep visibility into issues without requiring agents.
However, despite its popularity, many organizations are now reevaluating Wiz.io’s “code-to-cloud” capabilities. While Wiz has expanded into application security with Wiz Code (offering SAST, SCA, and IaC scanning), teams report that these capabilities still lag behind dedicated AppSec tools. The platform lacks DAST beyond API-focused scanning, has no code quality analysis, and requires third-party integrations for deeper coverage.
Additionally, Wiz’s built-in secrets scanner and Software Composition Analysis (SCA) tools still fall short compared to alternatives, lacking important features like automated dependency upgrades that are standard in dedicated AppSec tools (its SCA currently operates only at runtime).
Here’s what teams using Wiz have to say:
“We use Wiz. There's a lot of features in there and I'm overall pretty impressed with it, but it's mostly the security team using it and me keeping an eye on things…” – Platform engineer on Reddit
“While Wiz excels in many areas, its pricing can be on the higher side for smaller teams or organizations, and the vast amount of data and alerts can sometimes feel overwhelming without proper tuning.” – G2 reviewer (Head of Engineering)
In this guide, we’ll explore the top Wiz.io alternatives and provide in-depth comparisons to help you choose which tools best meet your team's application and cloud security needs.
You can skip directly to any of the Wiz.io Alternatives below:
- Aikido Security
- Aqua Security
- Check Point CloudGuard
- Lacework
- Orca Security
- Palo Alto Networks Prisma Cloud
TL;DR
Among all the Wiz.io alternatives reviewed, Aikido Security earns its place as the leading alternative, combining full CNAPP capabilities with a developer-first workflow that natively integrates SAST, SCA, IaC, secrets scanning, and CSPM, all at a transparent, flat price. Its agentless design, AI-driven remediation, and CI/CD integration make it easy to deploy and maintain, without the alert fatigue or pricing complexity that many teams face with Wiz.
Several organizations have already replaced Wiz with Aikido Security, and numerous others have selected Aikido Security after head-to-head POCs with both companies.
Comparison Between Wiz.io and Aikido Security
Looking for more cloud-native security platforms? Check out our article on the Top Cloud Security Posture Management (CSPM) Tools in 2026.
What Is Wiz.io?

Wiz.io, also known as Wiz, is a Cloud Native Application Protection Platform (CNAPP). It's primarily known for its agentless, graph-based approach to securing cloud environments from configuration to runtime. It includes:
- Cloud Security Posture Management (CSPM): Continuously scans cloud assets for vulnerabilities
- Vulnerability Management: Detects and prioritizes risks across virtual machines, containers, and cloud workloads.
- Agentless Architecture: Uses API-based scanning for quick setup.
- Security Graph: Displays findings across identities, workloads, and configurations in the form of graphs.
- Integration: Support for CI/CD and SIEM tools.
- Basic SAST, SCA, and IaC Scanning (via Wiz Code): Scans application code, dependencies, and infrastructure-as-code templates
Who uses Wiz?
Wiz is primarily used by mid-sized to large enterprises managing complex multi-cloud environments. Its detailed dashboards, compliance reports, and infrastructure visibility make it a favorite among cloud security teams and CISOs.
However, it wasn’t built with developers in mind. DevOps teams can use Wiz to catch misconfigurations, but when it comes to code and pipeline security, it falls short. Although its recently introduced “Wiz Code” module adds some SAST and Infrastructure-as-Code (IaC) scanning, it falls short when compared to dedicated SAST, SCA, or CI/CD pipeline security tools.
These limitations, combined with pricing concerns and alert fatigue, have led many organizations to explore more integrated, “code-to-cloud” alternatives.
Why Look for Alternatives?
Even with Wiz’s popularity teams often run into these friction points:
- Cloud Asset Search: Its cloud asset search has been known to underperform.
- Complex Setup: Setting up Wiz across AWS, Azure, and GCP can be time-consuming, especially when managing permissions and policies across accounts.
- Alert Fatigue and False Positives: Wiz’s broad scans can overwhelm teams with alerts.
- Limited Code-Level Security: While Wiz Code now offers SAST and SCA, these features are newer and less refined than dedicated AppSec tools. The DAST offering is primarily API-focused rather than full web application testing. If you want deep coverage for app code, dependencies, secrets, and containers, you’ll need to integrate third party tools, or use alternatives that natively integrate these, like Aikido Security.
- Poor Developer Experience: Wiz lacks native IDE plugins, a modern user interface, actionable fixes, and developer-friendly UX.
- Enterprise-Only Pricing: Wiz’s pricing is opaque and often out of reach for startups or smaller teams. It charges teams based workload which can be hard to predict, with many users reporting unpredictable quotes for features they don’t use.
Key Criteria for Choosing an Alternative
When evaluating alternatives, focus on these key traits:
- “Cloud to Code” Coverage: Choose platforms that combine CSPM with developer-first tools like IaC scanning, container scanning, and open-source dependency checks.
- Accurate, Prioritized Alerts: Does it use AI to filter alerts? Look for tools with contextual risk scoring and low false positives.
- CI/CD & IDE Integration: Effective tools should integrate into your existing developer workflow, not complicate it.
- Developer-Friendly UX: What is it designed with developers in mind? Does it provide clear remediation guidance and features, such as AI autofix.
- Transparent Pricing: Opt for solutions with self-serve trials and flat-rate, per-developer pricing over opaque enterprise-only models.
- Deployment: How long does it take to deploy? Do you need specialists to configure it?
Top 6 Wiz.io Alternatives
Below we examine the top six alternatives to Wiz.io. Each of the alternatives below addresses Wiz.io’s shortcomings in different ways.
1. Aikido Security
Aikido Security is a modern security platform that stands out with clear differentiation from traditional CNAPP platforms like Wiz.io. Aikido Security unifies code and cloud protection into one developer-centric workflow, combining SAST, SCA, IaC, secrets detection, and CSPM with AI-powered risk correlation.
Rather than overwhelming users with endless alerts, Aikido uses graph-based correlation to pinpoint real attack paths across code, containers, and cloud resources, reducing noise while exposing exploitable risks.
Now with all these findings what next?
Aikido Security gives developers everything they need to fix issues quickly:
- Clear explanations
- Suggested fixes in their IDE or PRs
- AI-powered Autofix
It also turns every simulation into audit-ready reports that map directly to standards like SOC2 and ISO27001, and you can then use a trusted advisor and partner to Aikido to complete the certification at a much lower cost.
With all of this, teams move from detection to resolution in minutes, not days, securing their entire cloud-native stack with less noise and less friction.
Key Features:
- End-to-End Security Coverage: Includes CSPM for AWS/GCP/Azure, SAST, SCA, secrets detection, IaC scanning, and container scanning. This unification replaces multiple siloed tools.
- Developer-Centric Workflow: Offers Instant AI powered feedback in PRs and IDEs, IDE plugins for real-time feedback, AI-powered autofix and actionable remediation workflows.
- Low False Positives: Aikido Security uses contextual filtering and AI triaging to suppress up to 90% of false positives, reducing alert fatigue, unlike Wiz which still shows the issues after filtering
- Agentless Setup: Connects to GitHub, GitLab, or Bitbucket in minutes and scans both code and cloud without deploying agents
- Transparent Pricing: Unlike Wiz’s enterprise-only model, Aikido offers flat, per-developer pricing with a free-forever tier for small teams. No sales calls required to get started.
- Best-of-Breed Scanners: Offers the best-in-class scanners: SAST, SCA, secrets, IaC, containers, and cloud configs, and much more. No more context-switching.
- Built for Devs: Integrates deeply with GitHub, GitLab, Bitbucket, Jira, Slack, and much more. You can run scans locally, in pull requests, or as part of your release process.
- Fast, Continuous Feedback: Scans run in minutes, not hours.
Pros:
- Lower TCO
- Best-in-Breed scanners
- Shorter sales process/trial
- Auto-fix functionality for common issues and dependencies
- Broad language support
- Advanced filtering reduces false positives, making alerts actionable
- Cross-platform support (GitHub, GitLab, Bitbucket, Jenkins etc.)
- Provides context-aware remediation guidance and risk scoring
Hosting Model:
- Saas (Software-as-a-service)
- On-Premise
Pricing:
All paid plans starting from $300/month for 10 users
- Developer (Free Forever): Free for up to 2 users. Supports 10 repos, 2 container images, 1 domain, and 1 cloud account
- Basic: Supports 10 repos, 25 container images, 5 domains and 3 cloud accounts
- Pro: Supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts
- Advanced: Supports 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs
Custom offerings are also available for startups (30% discount) and enterprises.
Gartner Rating: 4.9/5.0
Why Choose It:
Aikido Security is the top choice for developer-led or DevSecOps-driven teams that want security integrated directly into their workflow. It’s especially valuable for small to mid-size businesses looking for broad coverage without managing multiple vendors. If you’re frustrated with Wiz’s alert volume, pricing opacity, or lack of code insight, Aikido offers a faster, dev-friendlier alternative.
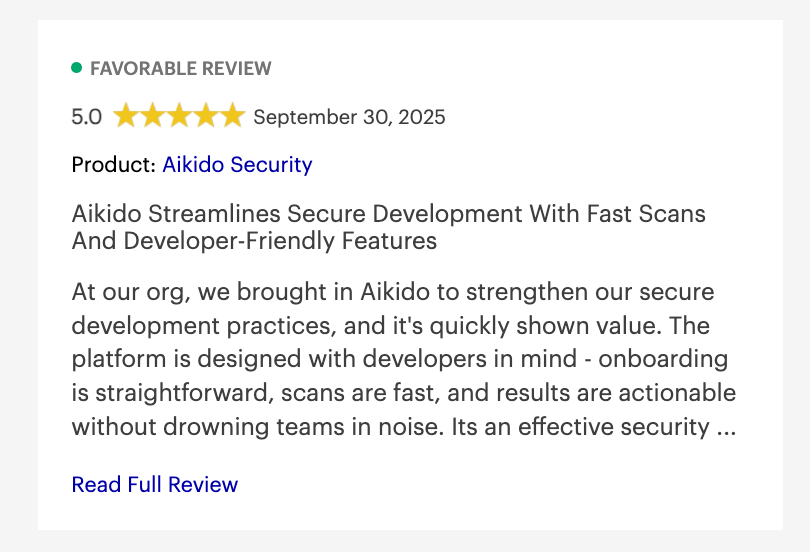
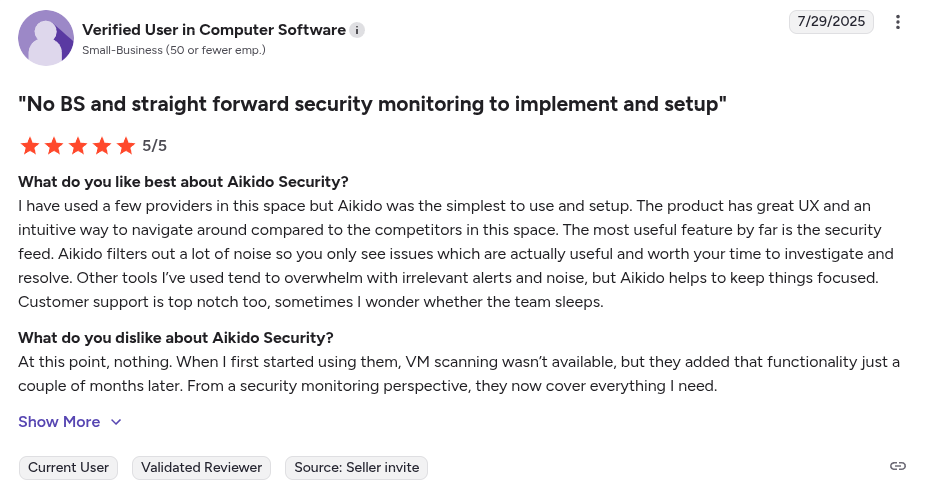
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra, Getapp and SourceForge.
2. Aqua Security

Aqua Security is a CNAPP platform with a strong focus on container and Kubernetes workloads. As a Wiz alternative, it shines in organizations that rely heavily on containerized and microservice-based architectures. offering.
Key Features:
- Container Image Scanning: Offers deep scanning for vulnerabilities, malware, and misconfigs in container images
- Cloud Security Posture Management: Continuously searches for misconfigurations in AWS, Azure, and GCP
- Compliance & Reporting: Maps findings to compliance frameworks like; PCI, SOC 2 and NIST
Pros:
- Strong container & Kubernetes protection
- CI/CD support
- Runtime protection
Cons:
- Primarily enterprise focused
- Steep learning curve
- Less developer-centric
- Setup can be complex compared to agentless tools like Aikido Security
- Users have reported high volumes of alerts
Why Choose It:
Pick Aqua Security if your team is running Docker, Kubernetes, or serverless workloads and you need robust runtime enforcement in production, something Wiz lacks.
Hosting Model:
- Saas (Software-as-a-service)
- On-Premise
Pricing:
Custom Pricing
Gartner Rating: 4.1/5.0
Aqua Security Reviews:


3. Check Point CloudGuard

CloudGuard is Check Point’s CNAPP offering. It combines cloud threat prevention, posture management, and workload protection and is often chosen by enterprises that already use Check Point firewalls and want a unified approach to both network and cloud security. As a Wiz alternative, it goes further into compliance enforcement, cloud network security, and policy-based automation.
Key Features:
- Cloud Posture Management: Continuously scans for misconfigurations and compliance violations across cloud environments
- Integration: Includes a CLI for IaC scans and basic CI/CD pipeline support
Cloud Network & Threat Prevention
Uses Check Point’s threat intelligence to inspect cloud traffic, detect intrusions and identify malware.
Pros:
- Comprehensive compliance coverage
- Strong automated remediation
- Integrated CIEM
Cons:
- Some of its features require installation agents
- Often requires specialist to setup
- Clunky User Interface
- Steep learning curve
- More security-team focused than developer-first
Why Choose It:
CloudGuard is ideal for large, security-mature organizations, particularly those already using Check Point’s on-prem solutions.
Hosting Model:
- Saas (Software-as-a-service)
- On-Premise
Pricing:
- Pay-As-You-Go (PAYG)
- Bring Your Own License (BYOL)
- Enterprise Agreements
Gartner Rating: 4.6/5.0
Check Point CloudGuard Reviews:


4. Lacework (by Fortinet)
Lacework by Fortinet is a CNAPP built around anomaly detection and behavioral analytics. Its core “Polygraph Data Platform”maps the relationships between cloud entities (users, services, data flows) and learns “normal” behavior to detect anomalies, misconfigurations, and potential attacks. Unlike Wiz, which surfaces static misconfigs, Lacework adds context by identifying deviations and attack paths based on behavioral data
Key Features:
- Behavioral Anomaly Detection: Tracks process activity, user behavior, and API usage to identify suspicious deviations.
- Multi-Cloud Support: Provides CSPM coverage across AWS, Azure, and GCP.
- Agentless Workload Protection: Uses both API-based (agentless) and agent-based data collection methods to access cloud environments.
- Provides deep visibility (containers, VMs)
Pros:
- Context-aware risk prioritization
- Integration with Fortinet ecosystem
- Behaviour anomaly detection
Cons:
- Complex setup
- Steep learning curve
- Potential vendor lock-in
- Clunky User Interface (UI)
- Installation agents are required to access all its features
Why Choose It:
Lacework is a strong fit for enterprises that need continuous behavioral monitoring and rely heavily on the Fortinet ecosystem.
Hosting Model:
- SaaS (Software-as-a-Service)
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
Lacework Reviews:

5. Orca Security

Orca Security is a cloud-native application protection platform (CNAPP). It uses its patented “SideScanning” approach to reconstruct workload files from block storages to find vulnerabilities, misconfigurations, exposed secrets, and sensitive data.
Key Features:
- Agentless Scanning: Orca scans VM disks, containers, and cloud storage to detect OS vulnerabilities, exposed credentials and malware.
- Sensitive Data Detection: Scans for plaintext secrets, keys, and PII across cloud buckets and storage volumes.
Prioritized Risk Mapping: Constructs a graph of your cloud assets and ranks findings by potential impact.Pros:
- Multi-cloud visibility
- Runtime protection
Cons:
- Pricing can become expensive when scaling
- It doesn’t scan application source code
- Limited support beyond cloud and runtime environments
- Primarily enterprise focused
- Users have reported experiencing alert fatigue, during large scale data ingestion
Why Choose It:
Orca is ideal for cloud security teams that want comprehensive cloud and workload visibility without managing agents.
Hosting Model:
- SaaS (Software-as-a-Service)
- BYOC (Bring Your Own Cloud)
Pricing:
Custom pricing
Gartner Rating: 4.6/5.0
Orca Security Reviews:
6. Palo Alto Networks Prisma Cloud
Prisma Cloud by Palo Alto Networks is a comprehensive platform that combines CSPM, CWPP, CIEM, and AppSec capabilities under a single brand. As a Wiz alternative, Prisma Cloud covers more ground, but also requires more configuration and typically targets large security teams.
Key Features:
- Cloud Posture & IAM Security: Monitors for misconfigs, excessive IAM roles, and compliance violations across all major cloud providers.
- Container & Host Security: Provides runtime defense, sandboxing, image scanning, and anomaly detection for containerized and virtualized environments.
- Web App & API Protection: Includes Web App and API Protection (WAAP) functionality that protects APIs and cloud functions from abuse
Pros:
- AI-powered risk prioritization
- Multi-cloud support
- Anomaly detection
Cons:
- Enterprise focuses
- Steep pricing
- Outdated user interface and console
- Deployment processes in large environments can become complex and length
- Steep learning curve
Why Choose it:
Prisma Cloud is ideal for enterprises with security teams looking to consolidate multiple tools into one
Hosting Model:
- Saas (Software-as-a-service)
- On-Premise
Pricing:
Custom Pricing
Gartner Rating: 4.2/5.0
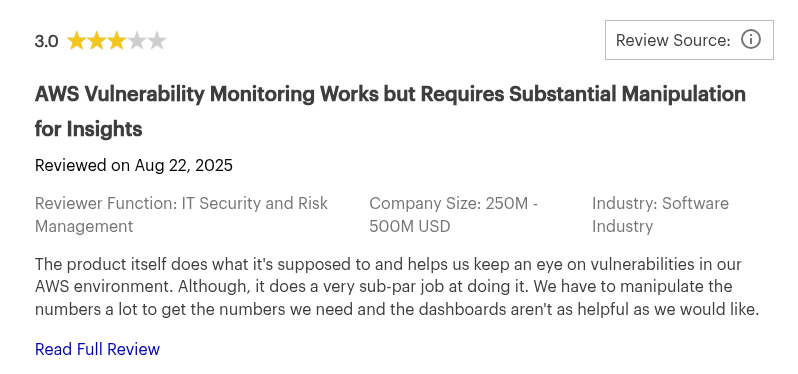
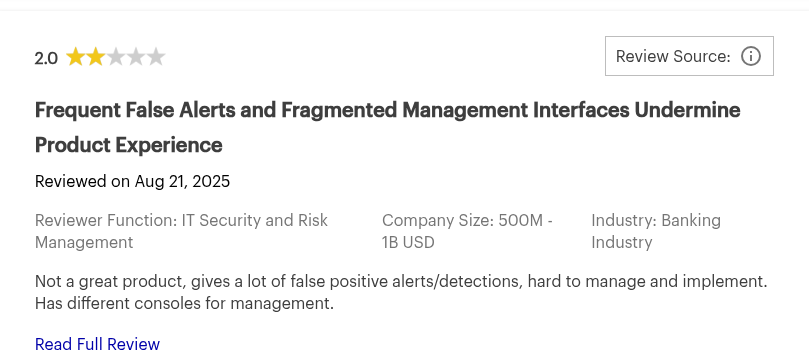
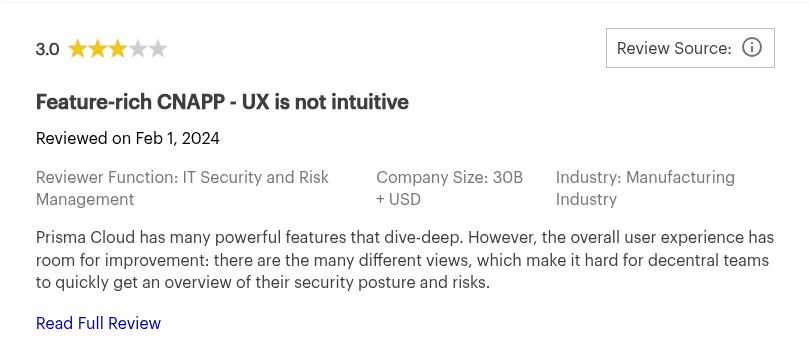
Palo Alto Networks Prisma Cloud Reviews:
Comparison Table
To help you compare the capabilities of the alternatives above, the table below summarizes each platform's coverage across key areas.
Conclusion
Wiz.io helped define modern cloud security posture management. But as teams expand their “code to cloud” coverage, its lack of developer centred workflow and limitations such as alert fatigue, code coverage gaps, and complex pricing have pushed teams to explore better alternatives.
Aikido Security positions itself as the leading alternative for both startups and enterprises, by delivering a truly developer-first CNAPP. It offers; SAST, SCA, IaC and secrets scanning, CSPM, AI remediation and CI/integration all at an affordable and transparent price. No agents, no third-party scanners, no noise.
Ready to move beyond tool sprawl? Start your free trial or schedule a demo with Aikido Security today.
You Might Also Like:



