The hype around AI-driven security has turned into genuine adoption. From AI code reviews to incident response, teams are now exploring how far AI-native intelligence can go in replacing manual work. And nowhere is that shift more visible than in penetration testing. What used to take weeks and only carried out twice a year, can now be autonomous and continuous.
In fact, 97% of CISOs, AppSec engineers and developers shared in the Aikido's 2026 State of AI in Security & Development report that they would consider AI penetration testing and 9 in 10 believe AI would take over the penetration testing field. The promise is irresistible: faster tests, deeper coverage, and continuous insight into your attack surface without waiting weeks or depending on consultants.
That’s where tools like XBOW entered the conversation. Positioned as a human-level AI penetration testing tool, promises to automatically discover, exploit, and prioritize vulnerabilities across your environment. In theory, it should replace manual penetration testing and give you real-time visibility into your attack surface.
In practice? Teams report limited coverage and depth, data sovereignty concerns (hosted in US only), and limited integrations with existing CI/CD pipelines to compliance tools.
That’s why security leaders are now asking a different question. Not “Is AI pentesting real?” but “Which AI pentesting tools actually deliver?”.
In this guide, we’ll explore the top XBOW alternatives in 2026. You’ll see how options like Aikido Security and others compare in scope, usability, and coverage, so you can choose the right fit for your security maturity and speed.
TL:DR
Aikido Security stands out as the #1 XBOW alternative, offering the best-in-class AI penetration testing tool for start-ups to enterprises, coming out on top in technical comparisons and POC head-to-heads. Aikido’s breadth of offensive testing uses agentic AI and reactive exploitation simulations that go beyond traditional passive analysis.
50,000+ organizations already use Aikido security across their code, cloud and runtime security. And this primarily because Aikido achieves deep coverage without forcing codebase access, with faster onboarding and fewer obstacles.
Unlike XBOW, customers get value early for free without having to commit before proof of value. After commitment, Aikido’s pricing stays predictable and continuous without forced credit bundles.
Also with EU and US hosting options, you don’t have to worry about compliance and legal requirements.
Aikido Security vs XBOW
What is XBOW?
XBOW markets itself as an AI-powered penetration testing platform that delivers human-level security testing at machine speed. Founded by former GitHub Copilot and GitHub Advanced Security engineers, XBOW’s mission is to transform application security with AI-powered continuous offense.
In essence, XBOW AI promises to think like a hacker by automatically mapping your environment, finding exploitable paths, and simulating real-world attacks. To achieve this, it uses hundreds of AI agents that work in parallel to discover, validate, and exploit vulnerabilities without human intervention.
Its features at a glance:
- Autonomous AI Agents
- Complete Coverage
With all these, you may ask, why look for alternatives?
Why Look for XBOW Alternatives
While XBOW’s approach has been dedicated to using AI from the outset , feedback from early adopters paints a more nuanced picture.
Here are the five most common reasons teams start exploring XBOW alternatives:
- Product maturity: XBOW AI was announced in July 2024 and came out of waitlist one year later in June 2025. There are little to no reviews of continued usage unlike its competitors. Many XBOW competitors like Aikido Security have are mainstays in the security market with thousands of customers.
- Lack of developer-first integrations and workflows: Real DevSecOps means developers are part of the fix loop, not just the report loop. XBOW currently offers limited integration with IDEs, CI/CD pipelines, or pull requests. They only offer compliance integrations (Vanta & Rhymetec). Alternatives like Aikido Security provide feedback directly where developers work.
- Data sovereignty & compliance concerns: XBOW is only hosted out of the US which can be an issue for EU organizations that need to be hosted in EU for compliance reasons.
- Opaque results & High false positives: Early users report that XBOW’s findings can feel like black boxes. This is no good as modern teams now expect explainable results, exploitability scoring, and reachability analysis that pinpoints which issues are actually exploitable.
- Pricing and scalability: It’s 2026, but you guessed it, “Talk to sales” still isn’t going anywhere. XBOW’s setup often requires repo-level access and manual configuration, with no true self-service option. Add to that a per-repo scaling model that can quickly drive up costs through recurring credit charges, and many new users find themselves facing unexpected bills before their first full test run.
- Struggles with complex business logic flaws: When it comes to identifying common vulnerabilities like XSS or SQL injection, XBOW does well, however it frequently misses business logic flaws and race condition errors, despite AI now racing ahead of human pentesters for these requirements.
In short, XBOW delivers on vision, but not yet on completeness. It represents where AI pentesting is headed but not necessarily where it needs to be for today’s developer-first security programs.
Don’t take it from us, here are a few reviews from XBOW users:


Top 5 XBOW Alternatives
1. Aikido Security
When compared side-by-side with XBOW, Aikido Security consistently comes out ahead, offering a more mature, transparent, and technically advanced AI pentesting platform.
Where XBOW focuses on surface-level automation, Aikido delivers true attacker-style simulations that mirror how real adversaries operate.
Aikido’s Security Attack module uses agentic AI to run dynamic exploit simulations across your environments, validating which vulnerabilities are truly exploitable and how they can be chained into full attack paths. This goes beyond simply listing issues, but also providing proof of exploitability, helping teams focus on what really matters.
Unlike XBOW, which often produces opaque results and requires manual validation, Aikido automatically filters out noise, reducing false positives by up to 95%. This results in no endless lists, just verified, exploitable risks.
Aikido also makes remediation seamless:
- Clear explanations of each finding
- Suggested fixes directly in your IDE or pull requests
- AI-powered Autofix for instant remediation
Every scan automatically produces audit-ready reports mapped to frameworks like SOC 2, ISO 27001, and OWASP Top 10, cutting down certification effort and cost.
With its fully autonomous AI pentesting model, Aikido helps organizations complete human-level pentests in hours and not weeks. It replaces repetitive manual testing with continuous, intelligent validation that scales across codebases and deployments.
For compliance-driven teams, Aikido supports custom region hosting in the EU or US, ensuring full data sovereignty, which is a flexibility XBOW currently lacks. And with transparent, predictable pricing (no “talk to sales” roadblocks), organizations can start testing in minutes and know exactly what they’ll spend in a year.
That combination of technical depth, speed, and developer-first design is why 50,000+ teams already trust Aikido Security across their applications and infrastructure.
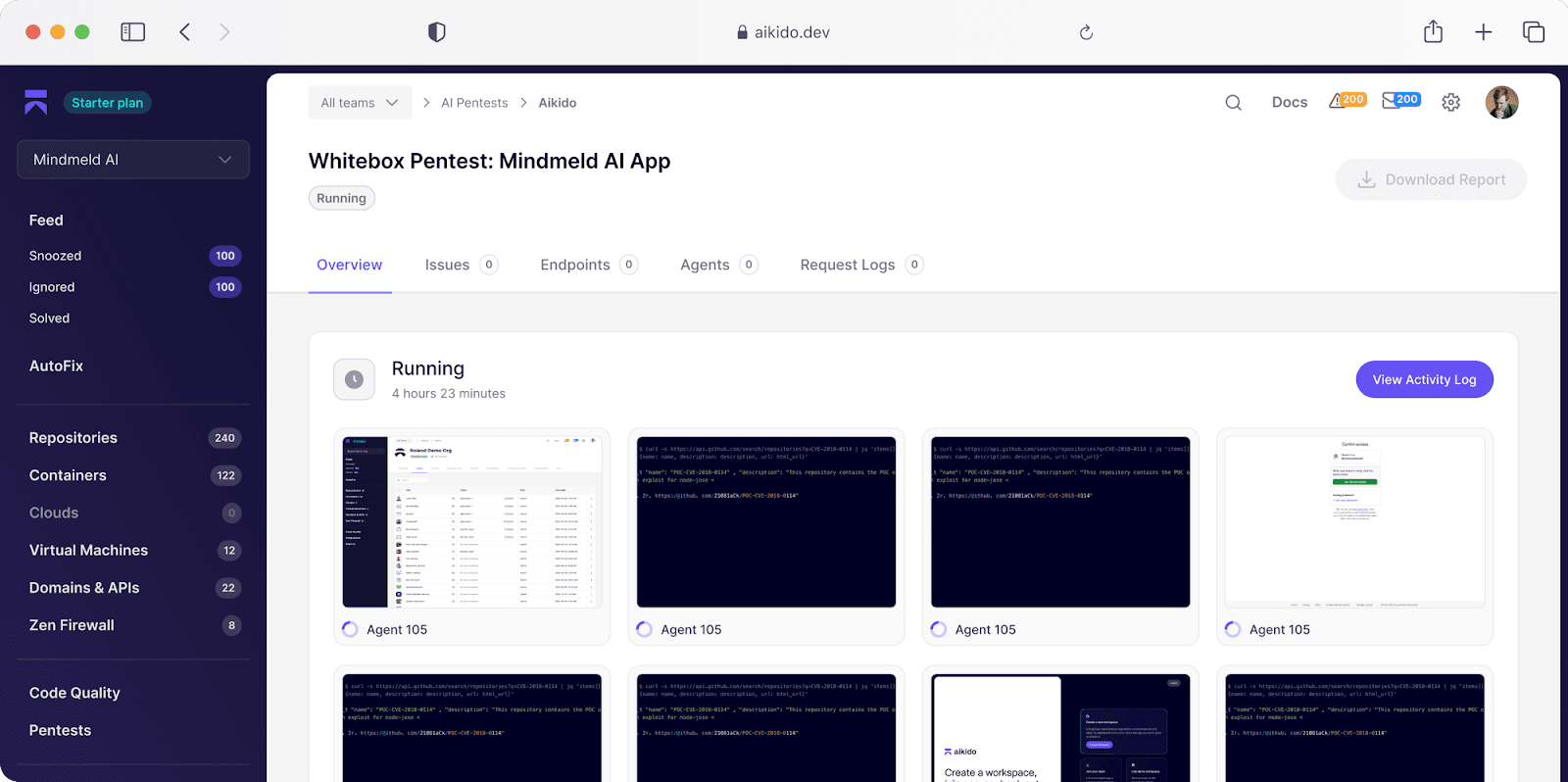
Coming out on top in technical comparisons and POC head-to-heads, Aikido’s breadth of offensive testing is why it’s trusted by 50,000+ customers, and is already proven across code, cloud, and runtime security.
Key Features:
- Product maturity: Unlike XBOW that just came out of waitlist in mid 2025, Aikido has established itself as a mainstay in the cybersecurity market, with 50,000+ organization already across their well-established base of code, cloud and runtime security.
- End-to-end attack path analysis: Aikido Security simulates attacker tactics to validate exploitability, prioritize real attack paths, and produce reproducible exploit proofs.
- Noise reduction: Aikido auto-triages results to cut out the noise. If an issue isn’t exploitable or reachable, it’s silenced automatically. You get real signals, not just alerts.
- Seamless developer focused integration: XBOW only supports compliance tools whilst Aikido integrates deeply with IDEs, Version controls, compliance tools and much more.
- Developer-friendly UX: Clear, actionable dashboards your team will actually use and it can be fully deployed in under an hour.
- Supports OWASP Top 10: Aikido Security maps to OWASP Top 10 and compliance standards so security teams can trust what’s covered.
- Custom Region Hosting: Aikido Security is hosted in your region of choice (EU or US). This is one of many reasons European companies opt for Aikido as their cybersecurity partner.
Pros
- Developer-focused approach with numerous IDE integrations and mitigation guidance.
- Customizable security policies and flexible rule tuning for any kind of needs.
- Centralized reporting and compliance templates (PCI, SOC2, ISO 27001).
- Mobile and binary scanning support (APK/IPA, hybrid apps).
- Predictable pricing
- On-demand testing
- AI-powered whitebox, graybox, and blackbox pentests
Hosting/Data Residency
Aikido Security supports hosting in the US and EU.
Testing Approach
Aikido map end-to-end attack paths and surface real vulnerabilities with a 3 step approach:
- Discovery: When the pentest begins, features and endpoints of the applications are mapped.
- Exploitation: 100’s of agents are deployed on those features and endpoints, each going in-depth, focused on their attack vector.
- Validation: For each finding, additional validation is performed to avoid false-positives and hallucinations.
Pricing:
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra and SourceForge.
2. RunSybil
RunSybil uses an autonomous orchestrator AI agent named “Sybil” to control specialized AI agents, each tailored to a particular pentest phase. Its aim is to mimic hacker intuition and perform reconnaissance, exploit simulation, and vulnerability chaining. With a promise to execute all pentesting phases without any human intervention.
Key Features:
- Orchestration agent: Uses an orchestrator AI agent to manage multiple specialized AI agents in parallel.
- Report generation: Report agents generate detailed findings on exploits and reproducibility in real-time.
- Continuous Coverage: Runs continuously performing automated pentests.
- Attack Replay: Enables team replay identified attack paths.
- CI/CD Integration: Supports common CI/CD platforms.
Pros:
- Simulates red-team behavior
- Continuous automated testing
- Users can replay attack paths
Cons:
- High False positives
- Low product maturity (still in early-access)
- May miss complex business-logic
- No human-verification to spot hallucinations
Hosting/ Data Residency:
Not publicly available
Testing Approach:
RunSybil’s testing approach involves coordinating fully autonomous AI-agents to map applications, probe inputs, and attempt chained exploits.
Pricing:
Custom pricing
Gartner Rating:
N/A (early-access only)
RunSybil Reviews:
No independent user generated review.
3. Cobalt.io
Cobalt is a pentesting-as-a-service (PTaaS) tool that connects companies with pentesters via crowdsourcing. It provides on-demand access to its community of security experts "Cobalt Core." Automated tools are used to map a customer's attack surface, and then a specialized pentesting team is assigned to them.
Key Features:
- Real-time Collaboration: Provides real-time communication between internal teams and pentesters.
- Pentesting-as-a-service (PTaaS): Connects companies to experienced pentesters across the globe.
- Compliance Support: Provides support for compliance frameworks.
Pros:
- Access to experienced pentesters
- Data residency options
- Real-time communication
Cons:
- Not an AI pentesting tool
- Pricing can become expensive
- Workflow friction may exist when onboarding pentesters
- Customers must define clear objectives
- Pentest quality varies based on the pentesters
- Not ideal for long-term, continuous pentests
Hosting/ Data Residency:
Cobalt supports hosting in the US and EU
Testing Approach:
Cobalt’s testing approach uses a "human-led, AI-powered" approach to run its Pentest-as-a-Service (PTaaS) model that pairs vetted human pentesters with companies.
Pricing:
Custom Pricing
Gartner Rating: 4.5/5.0
Cobalt Reviews:


4. Astra Security

Astra Security is a Pentest-as-a-Service (PTaaS) platform that uses a hybrid approach of cloud-based vulnerability assessments and manual penetration testing to identify flaws in web applications, cloud environments, and networks.
Key Features:
- Compliance-ready reporting: Astra maps to standards like ISO 27001, SOC 2, HIPAA, GDPR, PCI-DSS.
- Dashboard & collaboration: Offers real-time visibility of findings, communication with pentesters and developers, retest verification.
- Web Application Firewall (WAF): Actively filters incoming traffic in real-time for malicious attacks and requests.
- Blacklist monitoring: Monitors search engine blacklists and informs users if their website has been flagged.
Pros:
- Expert-human review + AI-driven testing
- Remediation guidance
- Compliance support
- Comprehensive WAF
Cons:
- Enterprise focused only. Not accessible to startups.
- Steep learning curve
- Frequent false positives in initial scans
- Steep pricing
- Certain functions need customer support help
- Users reported communication delay outside India's time-zone
Pricing:
- Pentest: $5,999/year (for 1 target)
- Pentest plus: $9,999/year (for 2 targets)
- Enterprise: Custom pricing
Hosting/ Data Residency:
Astra Security supports hosting in the US and EU
Testing Approach:
Astra Security uses a hybrid testing approach that combines its automated vulnerability scanner with manual expert penetration testing for continuous discovery, reporting, and remediation.
Gartner Rating: 4.5/5.0
Astra Security Reviews:


5. Terra Security

Terra Security is an Agentic-AI PTaaS platform. It combines autonomous AI agents with expert pentesters to continuously perform web-app penetration testing.
Key Features:
- Business-context aware attacks: Terra’s AI agents adapt testing based on application logic and business impact, ensuring that critical risks (like privilege escalation or financial data exposure) are prioritized.
- AI orchestration: Uses multiple specialized AI agents to crawl, map, and exploit vulnerabilities.
- Human Validation layer: Provides security experts to verify findings from automated AI scanners.
Pros:
- Context-aware testing
- Continuous coverage
Cons:
- Limited scope beyond web applications
- Enterprise focused
- Automated scanners may struggle with deep business-logic
- Steep pricing
Hosting/ Data Residency:
Terra Security supports hosting in the US and Israel
Testing Approach:
Terra Security’s testing approach involves using autonomous agentic AI’s with human-in-the-loop validation to run continuous, context-aware web-application penetration testing.
Pricing:
Custom pricing
Gartner Rating:
No Gartner review.
Terra Security Reviews:
No independent user generated review.
Comparing XBOW Alternatives
Choosing Your XBOW Alternative
The rise of AI penetration testing tools has completely reshaped how security teams think about offensive testing. Tools like XBOW, Terra Security, and Astra have pushed the industry forward. But not every team needs a black-box AI or enterprise-only setup to get real results.
The best choice is the one that fits your workflow, compliance needs, and security maturity, not just the one with the loudest AI claims. For most organizations, that means balancing automation with clarity, coverage, and developer-first design.
That’s exactly where Aikido Security stands out.
Aikido brings the same cutting-edge AI power as XBOW, but with the transparency, flexibility, and maturity modern teams need.
Whether you’re a startup scaling fast or an enterprise with a mature environment, Aikido delivers continuous, autonomous, and auditable AI security.
If you’re serious about replacing XBOW with a platform that actually fits your team’s speed and security goals, start your pentest in 5 minutes.
FAQ
Will XBOW or AIs be able to replace Pentesters?
AI tools can handle the breadth and speed of testing, but humans are still needed for depth, business-logic flaws, and context-aware validation. It’s essential to understand that AI is an augmentative tool, not a replacement for human expertise. YET!
What is the best alternative to Xbow?
For most teams, the best XBOW alternatives in 2026 are Aikido Security for its full-stack pentest coverage, EU/US hosting flexibility and predictable pricing. Unlike XBOW, Aikido offers value early rather than having to commit before proof of value.
Is AI penetration testing suitable for compliance audits?
Partially — but not on its own. Most compliance frameworks (SOC 2, ISO 27001, PCI DSS) still require human validation or independent assurance. However, AI pentesting tools like Aikido Security are closing that gap by mapping results to OWASP Top 10, CWE, and major compliance standards, producing audit-ready reports that accelerate certification prep and evidence collection.
How accurate are AI pentesting tools like XBOW compared to human-led tests?
AI pentesting tools have made huge strides in speed and automation, but accuracy still depends on context. While AI agents can identify common vulnerabilities faster than humans, most often struggle with business-logic flaws, chained exploits, or environment-specific edge cases.



