Cyberattacks have evolved beyond sporadic interruptions to become a systemic risk.
Today, a single compromise can ripple across the entire digital ecosystem from suppliers and upstream libraries to software vendors and cloud services, often faster than most organizations can respond.
Because of this growing interdependence, the UK is no longer treating cybersecurity as something organizations can approach with goodwill and informal best practices.
The rise in supply chain breaches, compromised components, and insecure-by-default products has made it clear that voluntary security efforts are not enough to protect a highly connected digital economy. Too many outages, data breaches, and resilience failures have shown how quickly a single weak link can disrupt entire industries.
The Cybersecurity and Resilience Bill responds to this reality with requirements that are simple to state but demanding to implement:
- You must design software with security built in from the start.
- You must be transparent about the cyber risks in your supply chain.
- You must ship products with secure defaults that do not rely on user vigilance.
- You must have a working process for identifying, triaging, and fixing vulnerabilities.
- You must be able to show regulators real evidence that you are meeting these expectations.
This shift makes one thing clear: You can no longer rely on spreadsheets, siloed scanners, or reactive checklists. Continuous visibility, automation, and rigor are now a baseline expectation, not an optional improvement.
TL;DR
Aikido Security gives you the tools you need to comply with the UK Cybersecurity and Resilience Bill. The Bill is enforceable and requires secure-by-design development, secure-by-default configurations, full transparency of SBOMs, mandatory vulnerability management, supply chain security assurance, and evidence-based reporting to regulators.
Here, we explain why the Bill was introduced, how it differs from the EU Cyber Resilience Act, what it means for developers and security teams, and why meeting these requirements is difficult without unified visibility and automation.
Aikido helps you meet these obligations through continuous scanning, automated risk correlation, SBOM generation, supply chain analysis, audit-ready reporting, and integrated remediation workflows across GitHub, GitLab, Bitbucket, Azure and more.
If you need continuous compliance that keeps pace with UK and EU security expectations, Aikido gives you a clear path forward.
Why the UK Cybersecurity and Resilience Bill Was Introduced
The Cyber Security and Resilience Bill is a reform and expansion of the 2018 NIS Regulations. It was introduced to strengthen national cyber resilience and address gaps emerging as digital systems, cloud services, and dependency chains became more complex. The Bill aims to deliver a “fundamental step change in the UK’s national security,” responding to cyberattacks that are increasing in scale, sophistication, and economic impact. Many attacks exploit upstream suppliers, software dependencies, or managed service providers, showing how weaknesses in one organisation can cascade across sectors.
Essential public services such as energy, water, healthcare, transportation, and finance, now rely heavily on digital systems. A single cyber incident can affect millions of people. The Bill explicitly seeks to “protect the services the public rely on,” from turning on the lights to accessing the NHS. The rise of cloud computing, SaaS ecosystems, and interconnected supply chains also revealed regulatory blind spots, particularly around managed service providers.
High-profile incidents across telecoms, finance, healthcare, and local government highlighted systemic weaknesses, including insecure defaults, unpatched vulnerabilities, and limited visibility into third-party risk. Voluntary security practices were no longer sufficient to address these evolving threats.
In response, the Bill shifts from guidance to enforceable obligation. It sets clearer security expectations, increases incident reporting, enhances regulatory oversight, strengthens supply chain assurance, and updates enforcement powers. In short, it provides updated, enforceable foundations to safeguard the UK’s essential services and maintain economic stability in a more interconnected digital landscape.
What the Bill Means for Developers and Security Teams
The Cybersecurity and Resilience Bill does more than set broad policy goals. It changes what day-to-day work looks like for the people who build and secure software. Below are the expectations for both developers and security teams.
What It Means for Developers
Developers sit closer to the software supply chain than any other group, which means the Bill directly affects how you write, maintain, and release code.
1. Clear expectations around secure coding: The Bill expects secure-by-design principles to show up in your codebase. This means regular code reviews, input validation, safe default configurations, and predictable, secure patterns across all services.
2. Required vulnerability remediation timelines: The days of fixing security issues “when time allows” are over. You are expected to patch vulnerabilities within defined time windows and show evidence that these timelines are being met.
3. Increased responsibility to track dependency risks: Modern applications rely heavily on open-source libraries. You are now responsible for understanding the security posture of those dependencies, not only the code you write yourself.
4. A need for SBOM awareness: Software Bills of Materials are becoming a compliance requirement. You need to know what is in your codebase, including transitive dependencies, and keep that inventory accurate.
5. Evidence-based coding and commit hygiene: Your work must be traceable. This includes clean commit histories, documented changes, and clear justification for security-related decisions. If an auditor reviews your repository, they should be able to understand how vulnerabilities were managed and why certain changes were made.
What It Means for Security Teams
For security teams, the Bill raises expectations from advisory oversight to enforced accountability. Compliance becomes a continuous workflow rather than an annual exercise.
1. Continuous compliance expectations: Security teams must maintain up-to-date visibility across all systems, repos, dependencies, and infrastructure. Controls must operate continuously and not only during audit cycles.
2. More pressure for automated vulnerability workflows: Manual scanning is not enough. You will need automated pipelines that detect issues, prioritise them, notify the right people, and track remediation through to completion.
3. Mandatory reporting structures: You are expected to maintain a clear vulnerability intake process, promote information sharing across teams, and produce documentation that can be handed to regulators on request.
4. The burden of proving reasonable security measures: It is no longer sufficient to say you have a process. You must show metrics, timelines, ticket histories, logs, SBOMs, and audit trails that demonstrate real operational security.
5. Stronger collaboration with engineering teams: Security controls now influence delivery pipelines and engineering velocity. The Bill encourages tighter alignment between DevOps, platform engineering, and security functions.
6. Security posture becomes a regulatory matter: Security is no longer a best practice. Under the Bill, resilience and secure development are legal expectations. Decisions that were once internal now have regulatory consequences.
UK Cybersecurity and Resilience Bill vs the EU Cyber Resilience Act (CRA)
Many organizations assume the UK Cybersecurity and Resilience Bill is just a regional counterpart to the EU Cyber Resilience Act.
Both aim to strengthen the security of digital products and services, yet they regulate different responsibilities. Confusing the two can result in teams applying the wrong controls, producing the wrong reports, or relying on evidence that does not satisfy either regime.
What the EU Cyber Resilience Act Covers
The EU CRA centres on products with digital elements and applies across the EU single market. It focuses on manufacturers, importers, and distributors, ensuring that products meet the same security expectations before and after release.
1. Security-by-design and secure-by-default: Manufacturers must build products that are secure out of the box, without requiring user expertise.
2. Risk assessment obligations: Products must undergo structured risk assessments before being placed on the market.
3. Mandatory vulnerability handling processes: Vulnerability intake, risk scoring, and remediation must follow defined procedures.
4. Post-market monitoring duties: Manufacturers must monitor product security after release and continue to address vulnerabilities over the product’s full lifecycle.
Where The UK Cybersecurity and Resilience Bill And EU Cyber Resilience Act Overlap
Both frameworks share similar principles, even though they apply them differently.
- Secure development requirements
- Mandatory vulnerability management
- Transparency across the software supply chain
- Post-market or post-deployment security monitoring
- Documentation and evidence-based compliance
For example, if a third-party dependency introduces a critical CVE, both frameworks expect rapid visibility, coordinated remediation, and verifiable documentation.
Key Differences
Why Meeting The UK Cybersecurity & Resilience Bill is Difficult
The expectations in the Cybersecurity and Resilience Bill sound straightforward on paper. In practice, most organizations struggle because their engineering environments are complex, fast-moving, and heavily dependent on third-party components. Even mature teams find it difficult to maintain continuous compliance when every commit, deployment, and dependency update introduces new risk.
Below are the core reasons these requirements are difficult to meet in real environments:
- Modern applications rely on vast networks of open-source libraries. Most teams cannot track the security posture of every dependency and transitive dependency without automation.
- Security coverage often stops at code scanning. Container images, infrastructure definitions, and runtime workloads are not monitored with the same precision, which creates blind spots.
- Teams use different scanners that produce conflicting severity levels and inconsistent guidance. This slows remediation and makes prioritization unreliable.
- Audit spreadsheets and periodic checklists cannot keep pace with daily code changes, dependency updates, and new vulnerabilities released each week.
- Teams must prove not only that vulnerabilities were fixed, but also when they were reported, who responded, how long remediation took, and what decisions were made. Most organizations lack this documentation.
- Architectural choices, coding patterns, and configuration decisions need to be backed by traceable justification. Without structured documentation, this becomes difficult to present during compliance reviews.
- Findings often sit in one tool while tickets live in another. This makes it difficult to verify that issues were triaged, prioritised, assigned, and resolved on time.
These challenges explain why organizations need a unified way to monitor risk, coordinate remediation, and produce evidence automatically. This is also the natural point where Aikido Security becomes relevant as a central visibility and compliance engine.
How Aikido Enables You to Comply with the UK Cybersecurity and Resilience Bill Requirements
To meet the requirements in the Cybersecurity and Resilience Bill, organizations need more than periodic scans or isolated security tools. They need a platform that offers them best-in-class tools for continuous visibility, consistent risk scoring, and evidence they can hand to regulators without scrambling through spreadsheets. Aikido Security fits into this space by providing a central control point for modern engineering teams.
Aikido is a cloud-native security platform that brings all of your security signals into one place. It provides visibility across your codebases, open-source dependencies, infrastructure as code templates, container images, secrets, and continuous integration pipelines.
Instead of forcing teams to manage separate scanners, Aikido correlates vulnerabilities across these layers, highlights what is actually exploitable, and removes noise that slows down remediation.
While Aikido can help satisfy a large number of requirements, there are a number of requirements that would need to be met with other suppliers such as incident reporting and ongoing operational resilience expectations.
Below is a breakdown of how Aikido helps you meet the core obligations in the UK Cybersecurity and Resilience Bill.
1. Requirement: Secure-by-Design Practices
The problem: You are expected to design software that is secure from the first line of code. This means identifying insecure configurations early, reducing dependency risk, and ensuring developers are not drowned in irrelevant findings.
How Aikido solves it
- Performs continuous scanning of your codebases, dependencies, and infrastructure configurations.
- Applies secure default scanning scopes so you do not miss critical areas.
- Correlates issues across multiple sources to reduce developer noise and highlight real risk.
- Enforces secure workflows in CI and CD pipelines so vulnerabilities cannot silently move into production.
2. Requirement: SBOM Transparency and Accurate Software Inventory
The problem: You must maintain an accurate, up-to-date Software Bill of Materials. Manual tracking breaks instantly when new dependencies are added or transitive libraries shift.
How Aikido solves it
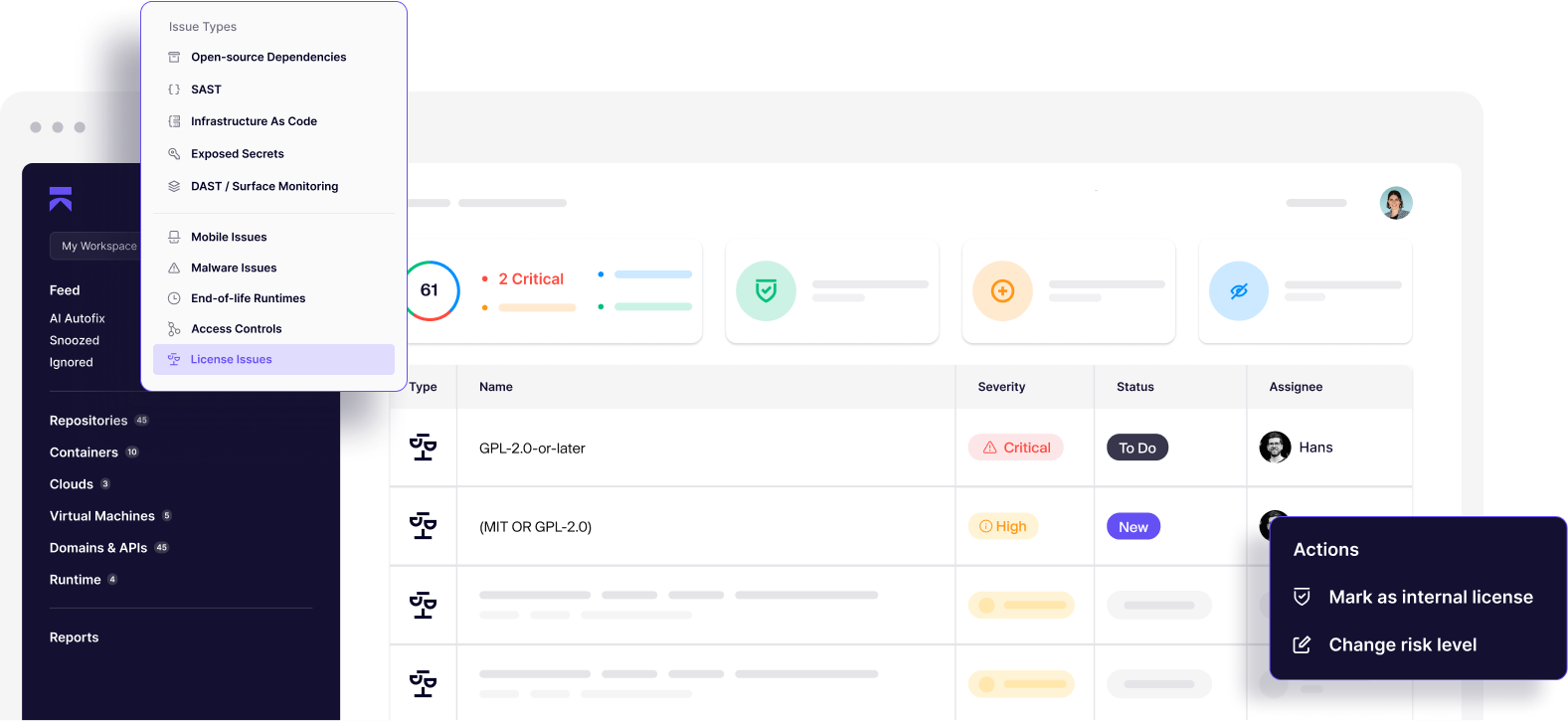
- Generate an SBOM in one click
- Builds a complete SBOM for each repository through Aikido’s SBOM Generator for clear dependency visibility.
- Provides full visibility into direct and transitive libraries.
- Alerts you when SBOM components receive new CVEs.
- Allows you to export SBOMs for auditors or internal reviews with a single action.
3. Requirement: Mandatory Vulnerability Handling Process
The problem: The Bill expects you to detect vulnerabilities, prioritise them, assign ownership, and prove that you met remediation timelines. Fragmented tools make this almost impossible without automation.
How Aikido solves it
- Detects vulnerabilities across repositories, container images, and registries.
- Prioritises findings using exploitability data, CVSS, and threat intelligence so teams focus on what matters.
- Automates remediation workflows through Jira or Slack integration.
- Timestamps and logs every action, creating a clear evidence trail for auditors.
- Documents remediation timelines automatically, supporting regulator expectations.
4. Requirement: Supply Chain Security Assurance
The problem: Most organizations rely heavily on upstream packages and third-party dependencies. You remain accountable for risks introduced by these components, even if you did not create them.
How Aikido solves it
- Identifies and analyses malware compromises early, often before they spread. Aikido is the first to detect malicious package behaviour, compromised releases, or suspicious dependency changes that could have a devastating impact on your supply chain.
- Scores dependency risk based on security history, maintenance patterns, and ecosystem reputation.
- Detects potentially malicious packages or typosquatting attempts before they enter your codebase.
- Flags abandoned, outdated, or compromised libraries so teams can replace them before they expose production workloads.
- Provides end-to-end traceability, allowing you to show exactly where a dependency came from, which services it touches, and how it was remediated during compliance checks.
5. Requirement: Evidence-Based Assurance to UK Regulators
The problem: It is not enough to claim that you have good security practices. You must prove it through structured evidence, historical records, and transparent risk reporting.
How Aikido solves it
- Produces automated, compliance-ready reports that map findings to regulatory expectations.
- Shows historical vulnerability timelines that demonstrate long-term risk management.
- Documents remediation activity so auditors can understand what changed and why.
- Provides a clear view of the reasonable security measures taken across your organisation.
- Aggregates risk information into leadership-friendly views that help executive teams meet their accountability obligations.
Beyond ISO27001, SOC2, NIS2, and CIS: What the UK Cybersecurity and Resilience Bill Adds
Most organisations already maintain compliance with established frameworks such as ISO 27001, SOC2, CIS Benchmarks, NIS2, or PCI. These frameworks focus on organisational security management. They define how you should manage risk, document policies, control access, monitor events, and respond to incidents.
Aikido already supports these standards:
- ISO 27001:2022 Compliance
- SOC2 Compliance
- OWASP Top 10 Compliance
- CIS Compliance
- NIS2 Compliance
- NIST 800-53 Compliance
- PCI Compliance
- HIPAA Compliance
- DORA Compliance
- HITRUST
- LVL3 Compliance
- ENS Compliance
- GDPR
The UK Cybersecurity and Resilience Bill introduces a different kind of requirement. It moves beyond organisational controls and places strict expectations on the security of the software and services you build and operate. It requires secure-by-design development, secure default configurations, verifiable SBOM transparency, continuous vulnerability handling, supply chain assurance, and evidence of remediation timelines. These obligations apply directly to your engineering practices, CI pipelines, codebases, dependencies, containers, cloud assets, and operational workflows.
This creates a new gap: you can meet ISO 27001 or SOC2 and still fall short of UK Bill requirements if your product ships with exploitable vulnerabilities, outdated libraries, weak supply chain controls, or undocumented remediation flows. Traditional frameworks do not cover these areas deeply enough.
Aikido helps close this gap by providing the technical controls, automation, and real-time visibility required to satisfy the bill’s product and service-level obligations.
Aikido Security: Your Path to Confident, Continuous Compliance
The UK Cybersecurity and Resilience Bill marks a clear shift in how organizations are expected to approach security. It is enforceable, not advisory, and it requires teams to demonstrate resilience with evidence, not intention. The EU Cyber Resilience Act sits alongside it with different scopes and responsibilities, which means organizations operating across regions need a nuanced approach that respects both frameworks rather than treating them as interchangeable.
Aikido gives you the operational foundation to meet these expectations. You gain continuous visibility across your code, dependencies, infrastructure, and pipelines. You receive consistent risk scoring, automated remediation workflows, and audit trails that regulators can trust. Compliance becomes something you maintain every day, rather than a stressful annual checkpoint.
With the right level of automation and the right level of observability, you reduce risk, improve delivery speed, and remove the uncertainty that surrounds typical regulatory preparation. Aikido helps you turn complex requirements into manageable, repeatable processes that scale with your engineering teams.
If you want compliance that keeps pace with the UK Bill, aligns with EU CRA expectations, and fits naturally into your development workflow, get started with Aikido Security today.
You might also like:
- Why European Companies Choose Aikido as Their Cybersecurity Partner EU companies and their cybersecurity choices
- How Aikido and Deloitte Are Bringing Developer-First Security to Enterprise — Aikido and Deloitte partnering for better enterprise developer experience and security
- Complying with the Cyber Resilience Act (CRA) using Aikido Security — Comply to the EU’s CRA with Aikido Security

Secure your software now






