Hard-coded secrets in code are a leading cause of data breaches—and the numbers are alarming. Developers push new secrets to Git every 8 seconds (GitGuardian Report), contributing to over 10 million detected exposures in public repos in 2023 alone. Attackers routinely scan for these credentials, exploiting mistakes before teams even notice (Dark Reading).
Secret scanning tools are the modern answer to this growing threat: they continuously monitor code, CI/CD pipelines, and cloud infrastructure for sensitive tokens, passwords, and keys. These tools don’t just alert you—they automate detection and remediation, helping teams close security gaps before they become incidents.
This guide spotlights the top secret scanning tools for 2025, showing you which solutions fit best for developers, startups, and enterprises.
- Best Secret Scanning Tools for Developers
- Best Secret Scanning Tools for Enterprises
- Best Secret Scanning Tools for Startups
- Best Free Secret Scanning Tools
- Best Open Source Secret Detection Tools
TL;DR
Aikido Security stands out as an all-in-one platform with reliable, low-noise secret detection and easy remediation, making it a top choice for teams of any size.
What Are Secret Scanning Tools?
Secret scanning tools search code, configs, and infrastructure for passwords, API keys, or other sensitive data that may have been accidentally exposed. They use pattern recognition, entropy checks, and sometimes machine learning to spot secrets in git repos, pull requests, and CI/CD pipelines before they reach production. Given that researchers found over 10 million secrets leaked on GitHub in 2023, these tools are vital for defending against breaches and achieving compliance. Top solutions not only discover secrets, but also automate remediation and integrate directly into developer workflows. For more background, see GitHub’s guide to secret scanning and OWASP’s Cheatsheet on Secrets Management.
How to Choose the Right Secret Scanning Tool
When choosing a secret scanning tool, focus on accuracy, workflow integration, remediation capability, and reporting features. For a more detailed evaluation checklist, check out OWASP’s Secrets Management Cheat Sheet.
With these essentials in mind, let’s explore the top secret scanning tools of 2025.
Top Secret Scanning Tools for 2025
(Listed alphabetically below; each tool offers unique approaches to secret detection and management.)
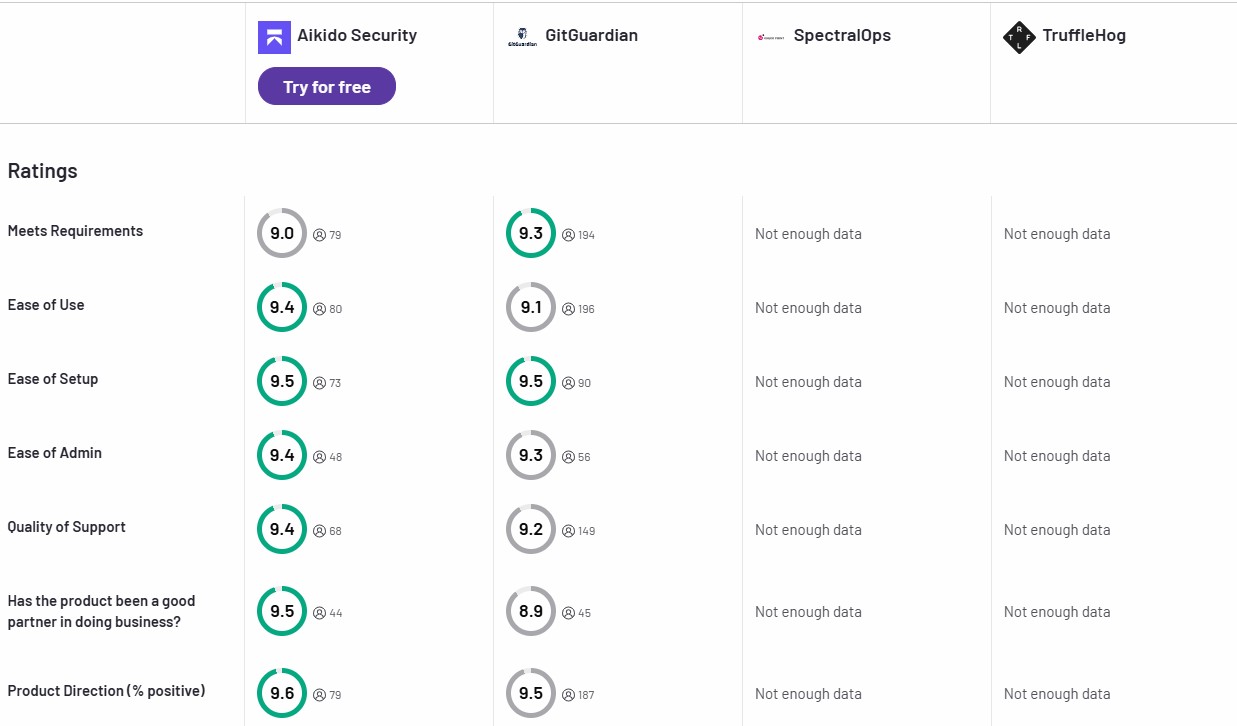
Here's a quick comparison of the top 5 secret scanning tools based on detection accuracy, integration capabilities, and remediation features:
1. Aikido Security
Aikido Security stands out as a comprehensive application security platform that includes sophisticated secret scanning as part of its unified approach. Unlike point solutions that only handle secrets, Aikido provides context-aware detection that understands how secrets relate to your broader security posture.
Key features:
- Multi-layered detection engine combines pattern recognition, entropy analysis, and AI to catch both obvious and obfuscated secrets. The system learns from your codebase patterns to reduce false positives while maintaining high sensitivity for actual credentials.
- Unified security context means secret findings are correlated with code vulnerabilities, cloud misconfigurations, and dependency issues. You can see if an exposed API key also has SAST findings in the same service, helping prioritize remediation.
- One-click remediation for many secret types. Aikido can automatically generate pull requests to remove hardcoded secrets, update CI/CD variables, and even rotate certain cloud credentials through API integrations.
- Development workflow integration includes IDE extensions, pre-commit hooks, and pull request checks. Developers get immediate feedback about secrets before they're committed, making prevention the first line of defense.
- Comprehensive scanning scope covers Git repositories, container images, infrastructure-as-code templates, CI/CD configurations, and even runtime cloud environments. This breadth ensures secrets don't slip through coverage gaps.
Best for: Development teams wanting comprehensive security with minimal overhead. Aikido is particularly valuable for organizations that need secret scanning as part of a broader security program, not as an isolated tool.
Pricing: Free tier available with generous limits, then transparent per-developer pricing that includes all security features, not just secret scanning.
2. GitGuardian
GitGuardian has built a reputation as the secret scanning specialist, focusing exclusively on detecting and managing exposed secrets across development workflows. Their platform is particularly strong at historical analysis and enterprise-grade secret lifecycle management.
Key features:
- Deep Git history analysis can scan your entire repository history to find secrets in old commits. This is crucial because simply removing a secret from the latest commit doesn't remove it from Git history – attackers can still access it.
- Advanced secret classification goes beyond simple detection to categorize secrets by type, sensitivity level, and potential impact. You can see the difference between a development API key and production database credentials.
- Automated incident response workflows can trigger secret rotation, send alerts to security teams, and create tickets with detailed remediation steps. For certain services, GitGuardian can automatically revoke exposed credentials.
- Compliance dashboard provides audit-ready reports showing secret detection coverage, incident response times, and policy compliance metrics. This is particularly valuable for enterprises that need to demonstrate security controls.
- Developer education features help teams understand why certain patterns are flagged as secrets and provide training to prevent future exposures.
Pain points: Some users report that costs can rise quickly for organizations with a large number of repositories, making it challenging for scaling teams on a budget. Others mention occasional false positives, requiring manual review and tuning to avoid alert fatigue.
For more firsthand feedback, see GitGuardian reviews on G2.
Best for: Security teams that need specialized secret management capabilities and comprehensive audit trails. GitGuardian excels in enterprises with strict compliance requirements and complex secret lifecycle needs.
Pricing: Freemium model with limited scanning, paid tiers based on repository count and advanced features.
3. GitHub Advanced Security

GitHub Advanced Security provides native secret scanning for GitHub repositories, making it the natural choice for teams heavily invested in the GitHub ecosystem. The integration depth is unmatched since it's built directly into the platform.
Key features:
- Native GitHub integration means secret scanning results appear directly in your repository's security tab, pull requests, and can trigger GitHub Actions workflows. No external tools or additional authentication required.
- Community-powered detection leverages patterns contributed by security researchers and service providers. When new secret formats are discovered, they're quickly added to GitHub's detection database.
- Partner integrations with major service providers mean that when GitHub detects their secrets, the providers are automatically notified and can revoke the credentials. This happens for AWS, Google Cloud, Microsoft Azure, and dozens of other services.
- Custom pattern support allows organizations to define their own secret patterns for internal services or proprietary authentication systems.
- Enterprise policy enforcement lets administrators set organization-wide rules for secret scanning, including blocking pushes that contain secrets.
Pain points: GitHub Advanced Security's capabilities are largely limited to repositories hosted on GitHub – if you host code elsewhere or work with hybrid environments, you’ll need additional tooling. Detection depends heavily on community-contributed rules, which may lag behind less common or newer secret types. Several users also note that false positives can require manual review, and custom pattern creation is less intuitive than in some competitors. Its secret scanning features are gated by GitHub’s higher-tier paid plans, which could impact cost-sensitive teams.
For more user experiences and feedback, see GitHub Advanced Security reviews on G2.
Best for: Teams using GitHub Enterprise that want comprehensive security features with zero external dependencies. Particularly valuable for organizations that prioritize keeping their security tools within their existing platform ecosystem.
Pricing: Included with GitHub Enterprise subscriptions, pay-per-repository for individual features on other plans.
4. Spectral

Spectral positions itself as the context-aware security platform that understands not just what secrets look like, but how they're used within your applications and infrastructure. This contextual approach significantly reduces false positives.
Key features:
- Context-aware detection analyzes secrets in relation to their surrounding code and configuration. It can distinguish between a production database password and a test fixture, reducing alert fatigue.
- Multi-environment scanning covers code repositories, CI/CD pipelines, container registries, cloud configurations, and even runtime environments. This comprehensive coverage ensures secrets are caught regardless of where they're stored.
- Policy-as-code lets teams define custom rules for secret handling, including exceptions for specific contexts, severity levels based on environment, and automated remediation workflows.
- DevOps integration includes plugins for popular tools like Jenkins, GitLab CI, Azure DevOps, and Kubernetes. Spectral can scan container images, Helm charts, and infrastructure-as-code templates.
- Collaborative triage features help security and development teams work together on secret remediation, with clear ownership assignment and progress tracking.
Pain points: Spectral’s rich policy engine and customization options can be overwhelming for new users, leading to a potentially steep learning curve for teams that want to unlock its full capabilities. Smaller teams or startups may also find cost to be a barrier, as pricing is contact-based and often best suited for large-scale enterprise needs.
Read more on user experiences and challenges in Spectral reviews on G2.
Best for: DevOps teams that need sophisticated policy management and want to reduce the operational overhead of managing secrets across complex, multi-environment deployments.
Pricing: Contact-based pricing focused on enterprise customers with significant infrastructure complexity.
5. TruffleHog

TruffleHog represents the open-source approach to secret scanning, providing powerful detection capabilities without licensing costs. It's particularly popular among security researchers and teams that prefer self-hosted solutions.
Key features:
- High-entropy detection uses mathematical analysis to identify strings that look random enough to be secrets, catching credentials even when they don't match known patterns.
- Extensive pattern library includes detection rules for hundreds of services and secret types. The community actively maintains and expands this library.
- Flexible deployment options mean TruffleHog can run as a CLI tool, Docker container, or integrated into CI/CD pipelines. You control where and how the scanning happens.
- Git history analysis can scan through entire repository histories to find secrets in old commits, branches, and tags.
- Custom integrations are possible since the source code is available. Organizations can extend TruffleHog to handle proprietary secret formats or integrate with internal systems.
Pain Points: TruffleHog is powerful, but users often report higher false positive rates compared to commercial platforms, which can create noise and slow down remediation efforts. Additionally, it lacks built-in remediation workflows—teams are responsible for manually addressing detected secrets and creating their own playbooks for alerting or credential rotation. Less technical teams may find setup and tuning challenging.
For more user insights and feedback, see TruffleHog reviews on G2.
Best for: Security-conscious teams that prefer open-source tools and have the technical expertise to customize and maintain their secret scanning infrastructure.
Pricing: Free and open-source, with commercial support options available from Truffle Security.
6. Detect-secrets
Detect-secrets by Yelp takes a minimalist approach to secret scanning, focusing on high accuracy and low operational overhead. It's designed to integrate seamlessly into development workflows without creating friction.
Key features:
- Baseline approach creates a snapshot of known secrets in your codebase, then alerts only on new secrets. This prevents overwhelming teams with historical issues while catching new problems.
- Plugin architecture allows custom detection logic for specific secret types or formats. Teams can easily add detection for proprietary authentication systems.
- Pre-commit integration can block commits containing secrets before they reach the repository, providing the earliest possible prevention point.
- Low false positive rate through careful tuning of detection algorithms and contextual analysis. The tool prioritizes precision over recall to avoid alert fatigue.
- Audit mode helps security teams verify that secret scanning policies are being followed across all repositories.
Best for: Development teams that want effective secret scanning without complexity. Detect-secrets works particularly well for teams that prefer lightweight tools and don't need extensive enterprise features.
Pricing: Free and open-source with community support.
Best Secret Scanning Tools for Developers
Developers need secret scanning tools that fit naturally into their coding workflow without creating friction or slowing down development. The best developer-focused tools provide immediate feedback, clear guidance, and can be easily integrated into daily development practices.
What developers should look for:
- IDE integration for real-time feedback as you code
- Pre-commit hooks to catch secrets before they're committed
- Clear, actionable error messages that explain what was found and how to fix it
- Low false positive rates to avoid alert fatigue
- Easy setup that doesn't require extensive configuration
Top picks for developers:
Aikido Security leads the developer experience with its comprehensive IDE integration and intelligent filtering. The platform understands that developers want to focus on building features, not wrestling with security tools. Aikido provides context-aware alerts that explain not just what was found, but why it's dangerous and how to fix it properly.
GitHub Advanced Security is perfect for developers already living in GitHub. The native integration means secret alerts appear naturally in your pull request workflow, and the community-driven pattern database catches secrets from services you're likely using.
Detect-secrets appeals to developers who prefer lightweight, configurable tools. Its pre-commit hook integration means you catch secrets locally before they ever reach the remote repository, and the baseline approach prevents being overwhelmed by historical issues.
Best Secret Scanning Tools for Enterprises
Enterprise environments require secret scanning tools that can handle massive scale, provide comprehensive audit trails, and integrate with existing security and compliance frameworks. These tools need to balance automated detection with human oversight and policy enforcement.
Enterprise requirements:
- Scalability to handle thousands of repositories and millions of commits
- Role-based access control to manage who can see and respond to different types of secrets
- Audit logging for compliance demonstrations and incident investigation
- Policy enforcement to automatically block or remediate certain types of secret exposures
- Integration with existing security tools, SIEM systems, and ticketing platforms
Top enterprise picks:
Aikido Security provides enterprise-grade secret scanning as part of its unified security platform. The centralized dashboard gives security teams visibility across all repositories while allowing development teams to maintain ownership of their remediation efforts. Advanced features include automated risk scoring, batch remediation capabilities, and comprehensive compliance reporting.
GitGuardian excels in environments where secret management is a primary concern. Their platform provides detailed analytics on secret exposure trends, automated incident response workflows, and deep integration with enterprise identity providers for access control.
Spectral stands out for organizations with complex, multi-cloud deployments. Its context-aware approach reduces false positives in large environments where the same secret patterns might appear in multiple contexts with different risk levels.
Best Secret Scanning Tools for Startups
Startups need secret scanning tools that provide maximum protection with minimal overhead. Budget constraints, small teams, and rapid development cycles mean the ideal tools are either free or very cost-effective while still delivering enterprise-grade protection.
Startup priorities:
- Cost-effectiveness with generous free tiers or affordable pricing
- Easy setup that doesn't require dedicated security personnel
- Automatic operation with minimal ongoing maintenance
- Growth scalability that can expand as the team grows
- Developer-friendly interfaces that don't slow down development
Best startup choices:
Aikido Security offers a compelling value proposition for startups with its free tier that includes comprehensive secret scanning alongside other security features. As startups grow, the transparent per-developer pricing makes budgeting predictable without surprise costs.
GitHub Advanced Security is perfect for startups already using GitHub, as it provides powerful secret scanning capabilities with no additional tools to learn or maintain. The integration with GitHub's workflow means developers can stay focused on product development.
TruffleHog provides enterprise-grade detection capabilities at zero cost, making it attractive for cash-strapped startups. The open-source nature means you can customize it as needed without vendor lock-in concerns.
Best Free Secret Scanning Tools
Open-source and free secret scanning tools have reached impressive maturity levels, offering capabilities that rival commercial solutions. These tools are perfect for individual developers, small teams, or organizations that prefer self-hosted solutions.
Free tool advantages:
- No licensing costs regardless of repository size or team size
- Full source code access for customization and security auditing
- Community-driven development that responds quickly to new threat patterns
- No vendor lock-in concerns
- Educational value for understanding how secret detection works
Top free options:
TruffleHog leads the free category with sophisticated entropy analysis and an extensive pattern library. The community actively maintains detection rules, and the tool can handle both historical scanning and real-time monitoring.
Detect-secrets provides a more curated approach with lower false positive rates. Its baseline methodology is particularly clever for teams that want to focus on preventing new secret exposures rather than dealing with historical issues.
GitLeaks offers another strong open-source option with good performance characteristics and straightforward configuration. It's particularly popular in CI/CD environments where speed is important.
Best Open Source Secret Detection Tools
The open-source ecosystem provides several powerful secret detection tools that organizations can customize, extend, and deploy according to their specific needs. These tools offer transparency, flexibility, and community-driven innovation.
Open source benefits:
- Transparency in detection algorithms and pattern databases
- Customizability for organization-specific secret formats
- Security auditing ability to verify the tool's behavior
- Community contributions from security researchers worldwide
- Cost control with no licensing fees or usage restrictions
Leading open source tools:
TruffleHog remains the gold standard for open-source secret detection. Its combination of entropy analysis and pattern matching provides excellent coverage, and the active community ensures rapid updates when new secret formats emerge.
Detect-secrets excels in production environments where precision matters more than recall. The tool's focus on minimizing false positives makes it particularly suitable for teams that can't afford alert fatigue.
GitLeaks provides excellent performance for CI/CD integration scenarios. Its configuration system allows fine-tuning for specific environments while maintaining good out-of-the-box performance.
Secrets-patterns-db isn't a scanner itself but provides the pattern databases used by many other tools. Contributing to this project helps improve secret detection across the entire ecosystem.
These open-source tools form the backbone of secret detection for many organizations and often serve as the detection engines for commercial products. Their transparency and community-driven development ensure they stay current with evolving threat patterns.
Conclusion
Secret scanning is essential for protecting your code and data. With Aikido, you can automate checks early to ensure secrets don’t slip through. Aikido fits seamlessly into your workflow, scales with your team, and helps catch issues before they become risks.
- Top SAST Tools in 2025 – Secure your source code with static analysis
- Top Container Scanning Tools – Find secrets hidden in Docker images
- Top AppSec Tools – Complete application security coverage



