Semgrep is a popular open-source static analysis tool used by developers and security teams to quickly scan code for vulnerabilities. Its wide adoption is thanks to its lightweight “semantic grep” approach, enabling custom rule writing..
However, despite its popularity, many developers, CTOs, and CISOs are re-evaluating Semgrep due to its pain points such as, high false-positives, slow scan performance on large codebases, limited coverage of certain areas (SCA, DAST, cloud posture), challenges integrating into developer workflows and that's listing a few.
Here’s what Semgrep users have to say:
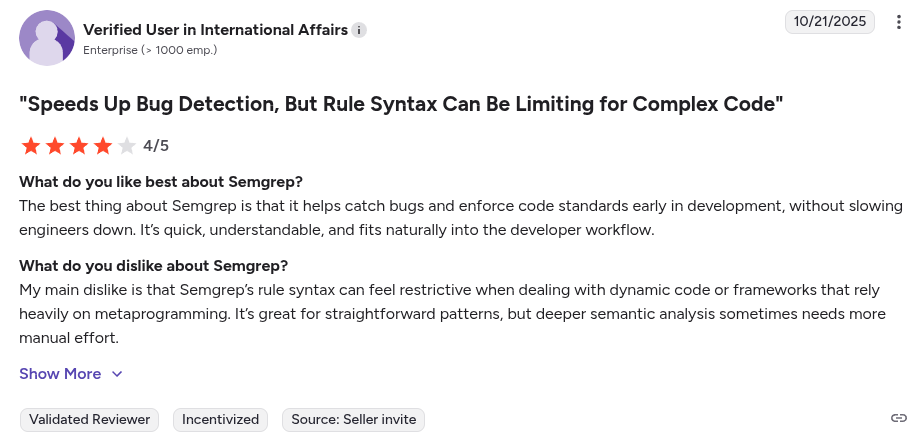
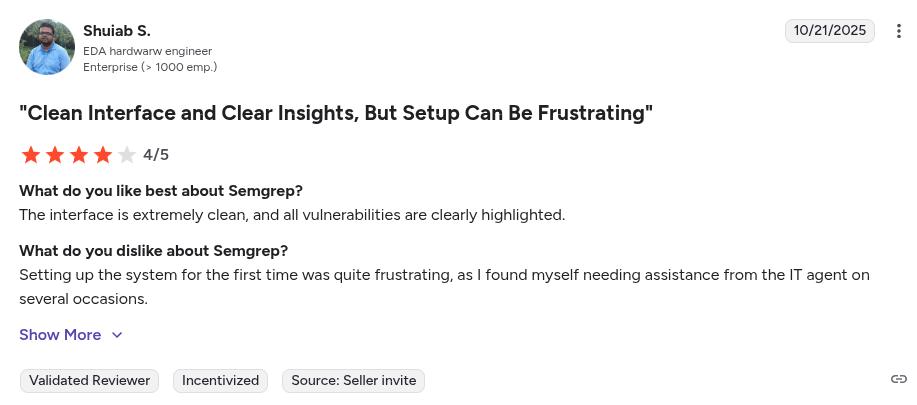
Users also shared:
“While Semgrep excels in static analysis, its narrow focus can be a limitation for organizations seeking a comprehensive application security platform. It does not natively offer integrated scanning for secrets, Infrastructure as Code (IaC), containers, or CI/CD posture, necessitating the use of additional tools for broader coverage… “ – G2 reviewer
“The initial setup for more advanced use cases can be tricky, especially when fine-tuning custom rules or managing large rule sets across multiple projects. Sometimes, there are false positives that require manual triage, and the learning curve for rule writing is a bit steep for newcomers…” – G2 reviewer.
With these limitations in mind, it becomes important to understand what other tools can fill the gaps Semgrep leaves behind. In this guide, we’ll explore the top Semgrep alternatives for static code analysis and provide in-depth comparisons to help you choose which tools best meet your team's security needs.
TL;DR
Aikido Security stands out as the top Semgrep alternative thanks to its modular,, AI-powered SAST engine, and full-stack security coverage.
Aikido forked Semgrep together with 10 other SAST security companies to leverage (and maintain) a better build of the previous Semgrep ruleset, after Semgrep changed its open-source packaging, removing critical features of its scanning engine behind a commercial license. Therefore Aikido benefits from the open-source code security engine Opengrep’s capabilities but can go beyond this with its own advanced feature set.
For instance, Aikido’s false positive reduction goes far beyond Semgrep where every issue is listed on the main feed.Its AI-driven static analysis engine goes beyond pattern matching by correlating findings to identify attack paths and surface truly exploitable vulnerabilities. Developers receive context-aware insights and clear remediation guidance directly in their workflow, making security reviews faster and more accurate.
Aikido also has seven additional language variants covered that Semgrep does not across both SAST and SCA.
Teams can start with the best-in-class SASTand enable SCA, IaC, secrets, or DAST scanning when needed, avoiding tool bloat while gaining deeper visibility.
Aikido Security consistently ranks higher in pilots when teams compare SAST depth, onboarding speed, and signal-to-noise ratios.
Comparison Between Semgrep and Aikido Security
You can skip directly to any of the alternatives below:
Curious how Semgrep compares to other modern scanners? Check out our article on The Top 13 Code Vulnerability Scanners in 2026.
What Is Semgrep?
Semgrep is a lightweight open-source static application security testing (SAST) tool designed to scan code for patterns and detect security vulnerabilities. Its key features include:
- Multi-Language Support: Supports over 20 programming languages.
- Flexible Integration: Can run in IDEs, as pre-commit hooks, or in CI/CD pipelines.
- Pattern-Based Vulnerability Detection: Flags common security issues such as SQL injection, XSS, and hardcoded credentials.
- Custom and Pre-Built Rules: Offers a library of pre-built rules, and the ability to write custom checks.
- Lightweight Scans: Fast, file-based scanning for quick developer feedback.
- Readable Rule Syntax: Allows developers to write rules that resemble actual code.
Why Look for Alternatives?
Even with Semgrep’s capabilities, teams often run into these friction points:
- Alert Fatigue and False Positives: Semgrep often floods teams with alerts that aren’t true issues, requiring significant effort to triage findings.
- Limited Analysis Depth: The free Semgrep engine lacks cross-file and multi-function data flow analysis meaning complex vulnerabilities spanning multiple files may be overlooked.
- Performance on Large Codebases: Running Semgrep on big monorepos or during CI can be resource-intensive and slow.
- Coverage Gaps: Semgrep primarily focuses on source code. It doesn’t natively cover other AppSec areas such as dependency scanning (SCA), cloud posture checks, or dynamic testing (DAST).
- Workflow & UX Challenges: While Semgrep is developer-focused, writing and maintaining custom rules has a learning curve, and its open-source version lacks a GUI or dashboards.
- Cost for Advanced Features: Semgrep’s core engine is free, but enterprise features like cross-file analysis, integrations, and team collaboration require its paid plan.
Key Criteria for Choosing an Alternative
When evaluating Semgrep alternatives you should keep these key criteria in mind:
- Signal-to-Noise Ratio: How well does the tool minimize false positives? Look for tools that use AI-assisted triage or vetted rule sets to surface what truly matters.
- Scan Speed & Performance: How long does it take to perform a scan? How accurate are its scans?
- Coverage & Security Depth: Does it scan only code or also includes SCA, IaC, API scanning, or runtime protection? Full-stack security platforms can save you from tool sprawl.
- Developer-Friendliness: Was it designed with developers in mind? . Look for options with AI-autofix, IDE plugins, inline PR comments.
- Integrations: Is it compatible with your current stack (version control systems, CI/CD, frameworks, languages).
- Pricing: Can you predict how much it will cost your team in the next 6 months or a year?
- Usability: Does it require installation agents to work? How long does it take to configure?
Top 6 Alternatives to Semgrep in 2026
Each of these tools takes a different approach to application security. Below, we break down what each alternative offers, their key features, and why you might choose it over Semgrep.
1. Aikido Security
Aikido Security is an AI-powered static code analysis and application security platform designed to secure the entire software Development Lifecycle (SDLC).
Unlike tools that generate hundreds of alerts per scan, Aikido Security uses graph-based intelligence and AI-assisted triage to automatically highlight real, exploitable vulnerabilities in your code, dependencies, containers, and cloud configurations.
Developers get everything they need to move from detection to resolution in minutes:
- Clear, context-based breakdowns of each vulnerability
- Fix suggestions directly in the developer’s IDE or pull requests
- Lets developers apply AI-powered remediations with a single click
Every scan automatically generates audit-ready compliance evidence mapped to frameworks like SOC 2, ISO 27001 and much more, helping teams stay audit-ready with minimal manual effort.
Aikido Security’s broader SAST coverage, AI-powered prioritization, and integrated remediation, allow development and security teams to secure applications faster, with less noise, and stronger confidence in their security posture.
Key Features:
- AI-Driven Static Code Analysis: Performs AI-assisted scans of repositories for vulnerabilities, misconfigurations, and code quality issues at both pre-commit and merge stages.
- Modular Scanning Suite: Covers everything from code and dependencies to cloud configs, containers and much more. You can start with a SAST module and expand as your team's needs grow. .
- Low Noise, High Signal: Aikido Security uses vetted rules and AI-based triage, to filter over 90% of false positives.
- Continuous Compliance Monitoring: Continuously tracks compliance posture across SOC 2, GDPR, HIPAA, and much more providing up-to-date, exportable compliance reports. Ideal for regulated industries where audit readiness is a constant concern.
- Agentless Setup: Integrates with GitHub, GitLab, or Bitbucket in minutes without requiring installation agents.
- Scalable Pricing: Offers a flat, per-developer pricing with a free-forever tier for small teams.
- Developer-Centric Workflow: Seamless IDE integration, CI/CD support, and one-click AI AutoFix make remediation fast and painless.
Pros:
- AI-powered static code analysis
- Predictable pricing
- Broad language support
- Advanced filtering reducing false positives
- Supports multiple repositories
- Supports custom rules
- Provides context-aware remediation guidance
Pricing:
Aikido Security’s paid plans start from $300/month for up to 10 users
- Developer (Free Forever): Ideal for small teams of up to 2 users. Includes 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Designed for growing teams, this plan supports 10 repos, 25 container images, 5 domains and 3 cloud accounts.
- Pro: Perfect for mid-sized teams. It supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Enterprise ready, with support for 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Tailored plans are available for startups (with a 30% discount) and enterprises.
Why Choose It:
Aikido Security is ideal for startups and enterprise teams that want full-stack security coverage without the complexity. As a Semgrep alternative, it offers broader coverage and less tooling friction through a modular developer-first workflow, letting teams add SAST, SCA, DAST, and IaC scanning modules as their needs grow, all under transparent, predictable price.
Gartner Rating: 4.9/5.0
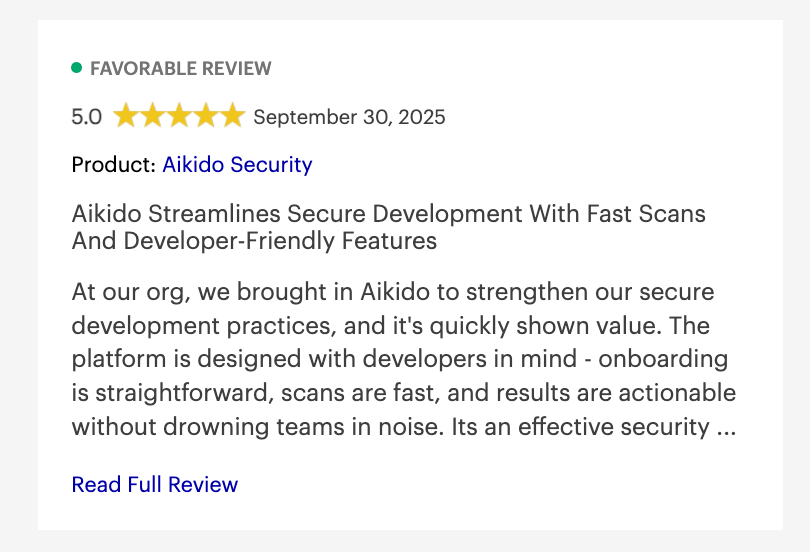
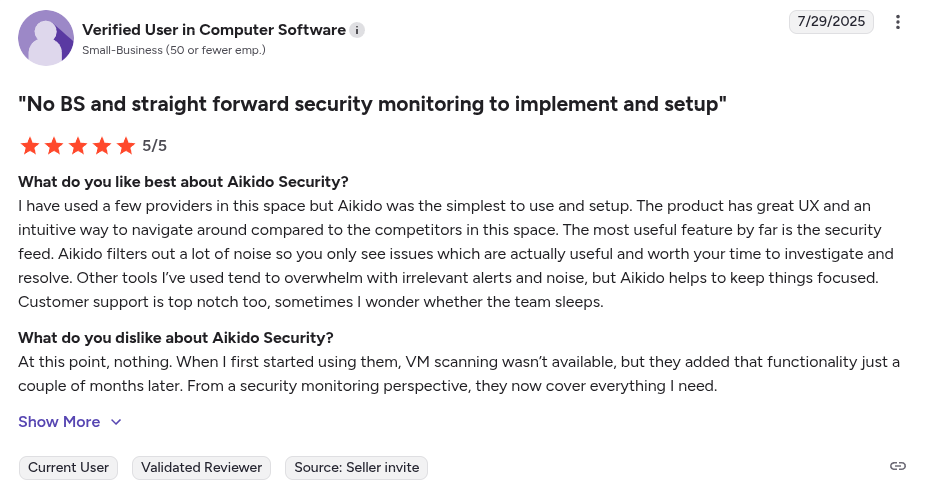
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra, Getapp and SourceForge
2. Fortify Static Code Analyzer
Fortify Static Code Analyzer (SCA), now owned by OpenText (formerly Micro Focus), is a static application security testing tool. It’s primarily used by enterprises due to its support for legacy languages, including COBOL and PL/SQL.
Key Features:
- Broad Language Support: Supports 10+ languages, from Python and JavaScript to ABAP and classic ASP.
- Robust Analysis Engine: Offers dataflow and control flow analysis across multiple files and functions.
Pros:
- Custom rules
- Legacy language support
Cons:
- Primarily enterprise focused
- Steep learning curve
- False positives
- High alert volume
- Initial configuration is complex
- Deep scans can be slow and resource intensive
Less developer-centric when compared to dev-first tools like Aikido Security
Pricing:
Custom pricing
Why Choose It:
Fortify SCA is ideal for enterprises with legacy-heavy codebases. As a Semgrep alternative, it suits teams that value robust, enterprise-grade scanning over lighter, highly customizable tools
Gartner Rating: 4.5/5.0
Fortify Static Code Analyzer Reviews:

3. GitHub Advanced Security
GitHub Advanced Security (GHAS) is GitHub’s native application security suite, fully integrated into the GitHub platform. It brings security scanning directly into your GitHub workflow.
Key Features:
- CodeQL Static Analysis: Uses its CodeQL engine to perform scans and detect vulnerabilities..
- Integration: Works natively with GitHub Actions, PR checks, and repo security dashboards.
Pros:
- Native GitHub integration
- Semantic queries
Cons:
- High False positives
- Steep learning Curve
- Lacks support beyond github
- Risk of vendor lock-in unlike platform agnostic tools like Aikido Security
- Requires specialist knowledge to write custom CodeQL queries
- Deep scans can be resource intensive and slow
Pricing:
- Free for public repositories
- GitHub Secret Protection: $19 per active committer/month
- GitHub Code Security: $30 per active committer/month
Why Choose It:
GHAS is best suited for organizations that operate entirely within GitHub. As a Semgrep alternative, it provides convenience for teams committed to GitHub-centric workflows rather than those needing broader flexibility.
Gartner Rating: 4.5/5.0
GitHub Advanced Security Reviews:


4. SonarQube
SonarQube is a code quality and security analysis platform. It started as a tool to catch bugs and code smells but has matured into a SAST solution..
Key Features:
- Multi-Language Support: Supports 10+ languages including Java, C#, JavaScript, and Python.
- CI/CD Integration: Integrates with common CI/CD platforms.
Pros:
- Provides code quality checks and security scanning in one tool.
- Free community edition
Cons:
- Primarily a code-quality platform
- Its scans are resource intensive
- Its “Lines of Code (LOC)” pricing model can become expensive
- Increased false positives for certain codebases
- Writing custom rules in SonarQube is complex
- Its advanced security features are only available on its paid plans.
Pricing:
SonarQube’s pricing comes in two categories: cloud-based and self-managed.
Why Choose It:
SonarQube works well for organizations focused on improving code quality while adding lightweight security scanning. As a Semgrep alternative, it suits teams who prioritize quality control rather than those needing deeper or more flexible SAST coverage.
Gartner Rating: 4.4/5.0
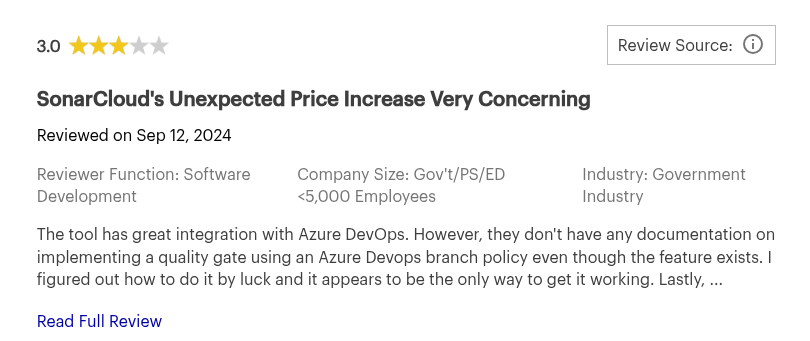
SonarQube Reviews:
5. Snyk
Snyk uses a combination of machine learning and semantic analysis to identify vulnerabilities in application source code.
Key Features:
- Rule Customization: Allows teams to define and implement their own custom rules.
- AI-driven Analysis: Searches through its open-source datasets to flag unusual or unknown bug patterns.
Pros:
- Comprehensive vulnerability database
- CI/CD integration
Cons:
- 1MB file size limit for SAST analysis
- Steep learning curve
- False positives
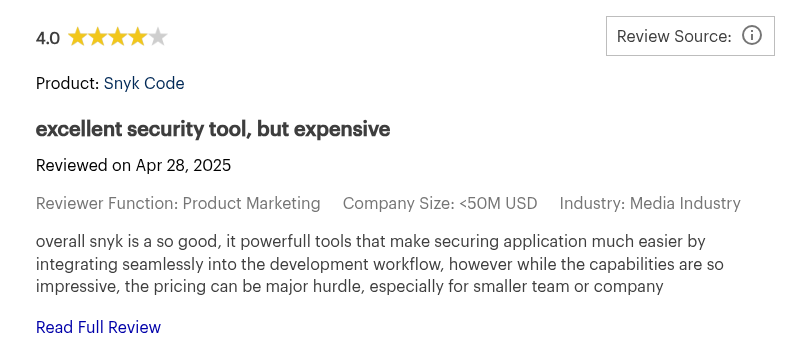
- Pricing can be become expensive
- Users have reported slow scans on large repositories
- Free plan is limited to 100 tests per month
- Remediation suggestions are sometimes generic
- Requires additional tuning for noise
- It can miss vulnerabilities in non-standard or proprietary codebases
Pricing
- Free
- Team: $25 per month/contributing developer (min. 5 devs)
- Enterprise: Custom pricing
Why Choose It:
Snyk is best suited for teams working heavily with open-source libraries. As a Semgrep alternative, it is better suited to structured scanning workflows than fast, developer-driven ones.
Gartner Rating: 4.4/5.0
Snyk Reviews:
6. Opengrep

Opengrep is an open-source static code analysis (SAST) tool designed to detect insecure code patterns and identify vulnerabilities. It’s a fork of the Semgrep Community Edition (formerly Semgrep OSS), created in response to their recent licensing changes. It is popularly known for its strong industry backing from platforms such as Aikido Security.
Key Features:
- Fully Open Source: Advanced analysis features such as, inter-file and intra-file cross-function taint analysis, and dynamic timeouts, are open and unrestricted.
- Intra-file Cross-Function Taint Analysis: When benchmarked against Semgrep, Opengrep’s intra-file, cross-function taint analysis performed better, detecting 7 out of 9 multi-hop taint propagation cases compared to Semgrep’s 4 out of 9.
- Community Governance: Its development is backed by the open-source community and leading security vendors.
Pros:
- Great for those dedicated to open source
- Broad language support
- Cross-platform integration
Cons:
- It is still in its early stages.
- Lacks built-in vulnerability mapping
- Its SAST engine is less comprehensive when compared to platforms like Aikido Security
Pricing:
Open-source
Why Choose It:
Opengrep is ideal for teams that want a fully open-source static analysis engine with strong pattern matching and flexible rule creation. As a Semgrep alternative, it suits teams seeking an open-source SAST engine that is customizable and can enforce security policies.
Gartner Rating:
No gartner review.
Opengrep Reviews:
No independent user generated review.
Comparing the Best 6 Semgrep Alternatives
To help you compare the alternatives above, the table below summarizes each tool's strengths, limitations and ideal use cases.
Conclusion
Semgrep is a strong option for quick, pattern-based code scanning, but as teams and organizations scale, they outgrow its limitations, whether that’s noise, shallow analysis depth, or the need for broader security coverage. Modern teams now expect accuracy, speed, and meaningful guidance, not just pattern matching.
Aikido Security delivers on that expectation with its AI-driven static analysis engine. It provides richer context, actionable results, and one-click fixes directly in developer workflows. It cuts through the noise, prioritizing vulnerabilities that are truly exploitable, allowing teams to stay focused on what matters.
Want less noise and more real protection? Start your free trial or book a demo with Aikido Security today.
FAQ
How do Semgrep alternatives handle custom rule creation compared to Semgrep?
Semgrep allows developers to write rules in a code-like syntax, making custom rule creation flexible but requiring manual effort. Alternatives, like Aikido Security, provide pre-built rule sets alongside AI-assisted creation, helping teams reduce manual configuration while still supporting tailored checks.
Which Semgrep alternatives offer better integration with CI/CD pipelines?
While Semgrep can run in CI/CD pipelines, alternatives like Aikido Security provide deeper, pipeline-aware integration. This includes automated scanning, AI-assisted remediation, and seamless pull request handling.
Are there any Semgrep alternatives specialized in detecting specific types of vulnerabilities?
Yes, certain tools focus on specific areas such as dependency vulnerabilities, secrets, or cloud misconfigurations. Aikido Security combines broad SAST, SCA, and targeted vulnerability detection, with AI-assisted analysis to catch complex cross-file issues.
Where can I find reliable open-source tools similar to Semgrep?
Open-source alternatives include tools like Opengrep, ESLint for JavaScript, Bandit for Python, and Brakeman for Ruby. For teams looking for a more comprehensive, developer-focused SAST and SCA platform, Aikido Security offers integrated scanning with AI-powered insights and remediation.
You Might Also Like:



