If you’ve worked with Node.js long enough, you realize something uncomfortable: your most significant security risks usually come from packages you didn’t write and maintainers you’ve never met.
Most teams rely on npm because it’s fast, familiar, and effective. The problem is that speed often hides risk. One small package with a known vulnerability can slip into your build, move into staging, and remain in production for an extended period before anyone notices. And when it finally blows up, you’re the one answering for it.
In the past year, Aikido Security has found numerous npm compromises that show how significant this can be:
- Shai Hulud, a stealthy malware campaign hidden in npm packages that exfiltrated credentials and tokens through transitive dependencies.
- S1ngularity, a dependency confusion operation that exploited naming collisions and internal mirrors to infiltrate developer workstations and CI.
- The September npm malware outbreak, where popular libraries such as chalk, debug, and ansi-regex were poisoned and downloaded millions of times before Aikido detected and escalated the compromise.
- The React-Native-Aria trojan, which inserted a remote access payload into legitimate npm releases and was caught early through Aikido Intel anomaly detection.
This is why you want to know what’s changing in your dependency tree, and you want to catch issues before they become a security story in your incident channel. This matters even more now because modern JavaScript projects often pull in hundreds of transitive dependencies without requiring any user intervention. You think your app uses 40 packages. In reality, it depends on 600.
As a result, tooling around audits, continuous checks, and more intelligent automation keep coming up in engineering conversations. You want something you can trust, something that plugs into your CI/CD, and something that doesn’t slow your team down.
If you want extra context on how dependency sprawl becomes a real supply-chain risk, this explainer is a solid starting point. However, in this article, we’ll focus on what npm audit actually does, where it falls short, and the extra layer your team still needs to stay secure.
TL;DR
Aikido Security gives your team the continuous protection, smarter prioritization, and real environment-aware insights that npm audit simply can’t provide. While an npm audit is a useful first check, it only catches known issues and misses zero-days, malware, misconfigurations, abandoned packages, and vulnerable transitive dependencies buried deep in your tree. A clean audit report doesn’t mean your project is actually safe.
Modern supply-chain incidents like Log4j and SolarWinds show how easily third-party code can compromise an entire stack. If you want real coverage instead of partial visibility, you need tooling that sees beyond what npm’s advisory database contains, and that’s exactly the gap Aikido fills.
What is an npm Audit?
npm audit is a built-in command that checks your project’s dependencies for known security issues. It looks at the packages listed in your package.json and package-lock.json, compares them against vulnerability data from the GitHub Advisory Database, and then tells you where the risks are. Nothing fancy. Nothing hidden. Just a straight check of what you’ve installed versus what the ecosystem knows is vulnerable.
Under the hood, the process is pretty straightforward. npm reads your dependency tree. It matches each package and version to the advisories published by GitHub. If there’s a match, the tool flags it with a severity level and a suggested fix.
Sometimes it’s an upgrade. Sometimes it’s a deeper dependency you didn’t even know you were using. And that’s why npm audit matters: it shines light on things you usually don’t track manually.
Here’s a quick example of running it and a very typical report:

It’s simple, but it tells you exactly where the problem sits.
One common misconception is that a clean audit means your project is fully secure. It only implies npm didn’t find issues in its own database. Another is assuming that every reported vulnerability must be fixed immediately. Some aren’t relevant to your environment or threat model, and understanding that difference is part of real security work.
So npm audit is helpful. It’s just not the whole story.
Why Auditing Your Dependencies Isn’t Optional
You might think dependency audits are something you run when you have time. They’re not. Modern software relies heavily on third-party packages, so ignoring them is essentially betting on luck. And in security, luck runs out fast.
Supply chain attacks made that painfully obvious. Log4j showed how a single library used by thousands of companies could expose the entire world in a weekend. SolarWinds proved that attackers don’t always go after your code; they go after code you trust. These weren’t niche incidents. They were global failures rooted in dependencies no one looked at closely enough. We still see this play out in recent supply-chain compromise cases across the JavaScript ecosystem.
And the numbers back this up. Most JavaScript projects pull in hundreds of indirect dependencies without any manual oversight. A significant proportion of security vulnerabilities in production environments originate from third-party packages, rather than the application code you write. It’s uncomfortable, but it’s true: your real attack surface is mostly invisible unless you check it.
That’s why npm audits matter. They give you a first line of defense by showing what’s already known to be unsafe. They highlight outdated packages, risky versions, and supply-chain weaknesses that may be hiding under your direct dependencies.
But here’s the part you shouldn’t ignore: An audit is only as good as the data it checks against. It won’t detect zero-days. It won’t warn you when a maintainer abandons a critical package. And it won’t stop malicious updates on its own.
So audits are essential. They’re just not complete. You still need continuous checks, smarter monitoring, and tools that catch what npm can’t see yet.
How to Run an npm Security Audit
Running an npm security audit report is straightforward, but doing it properly yields the most beneficial results. You start by making sure you’re on a recent version of Node.js and npm. Older versions sometimes miss newer advisories or mislabel issues, and that can hide real risks. So update first, and then move on.
Next, navigate to your project folder and run the command:
npm audit
That’s the entire workflow on the surface. But the report itself carries the real value.
npm groups findings into severity levels like low, moderate, high, and critical.
- Low: A low-severity issue might be a harmless edge case that barely affects your environment.
- Moderate: A moderate one could mean outdated logic that becomes risky under specific conditions.
- High & Critical: High and critical dependency vulnerabilities are the ones that can be exploited easily or remotely, and those are the issues you want to fix fast because attackers love low-effort, high-impact targets.
You’ll also see different vulnerability types. Examples include Regular Expression Denial of Service (ReDoS), where poorly written regex patterns freeze your service, and prototype pollution, which lets attackers modify JavaScript objects in ways your code never intended. When npm flags these, it also tells you how far down the dependency tree the issue sits and whether it’s in something you installed or something your dependencies pulled in silently.
Every audit result comes with remediation advice. Sometimes it’s a clean upgrade. Sometimes it’s a chain of upgrades because the vulnerable component sits five layers deep. And sometimes npm says there’s no fix yet, which means you decide whether to isolate the package, patch it manually, or wait for the maintainer.
If you want clearer output, you can run the audit in JSON format using npm audit --json:

or HTML using npm audit --json | npx npm-audit-html:
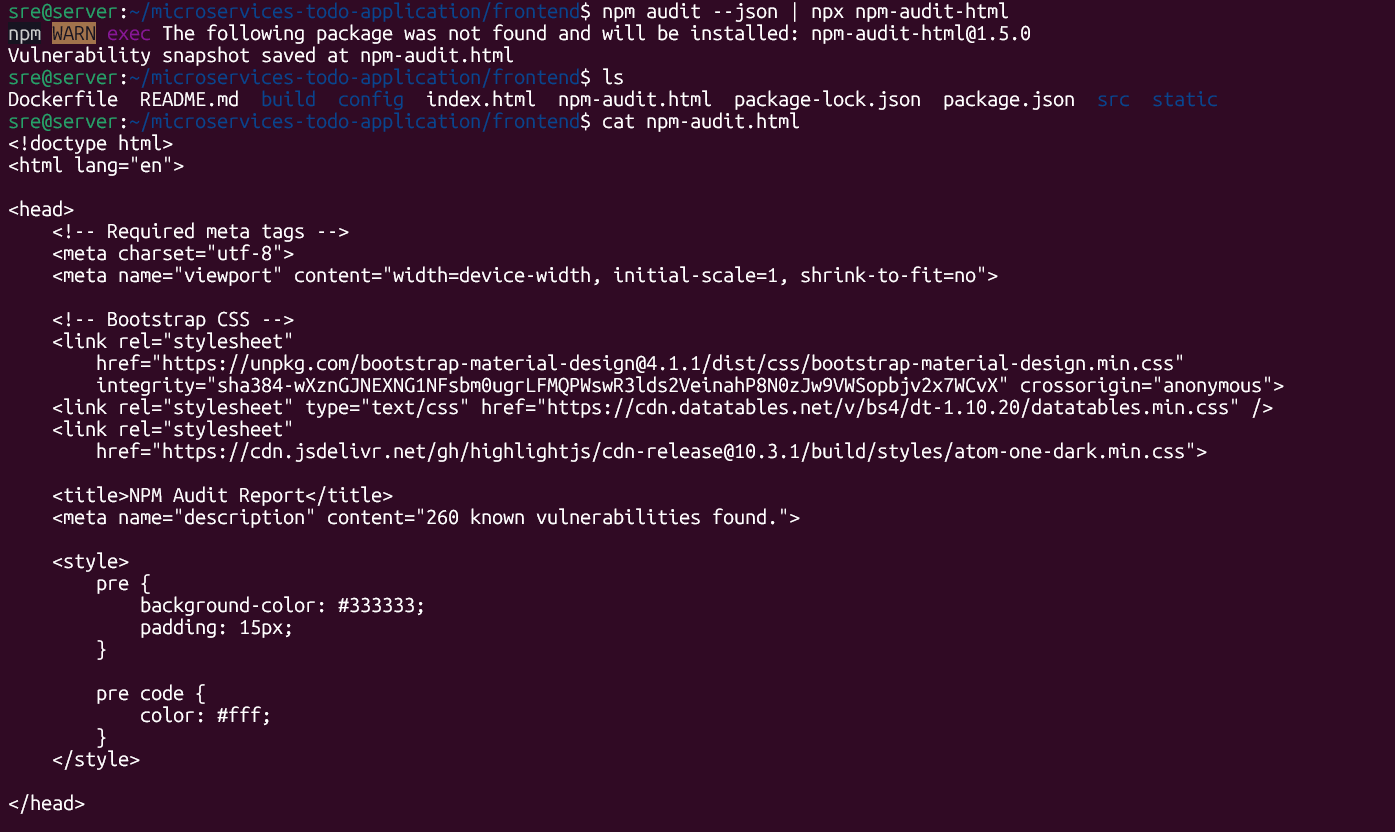
JSON gives you structured data for pipelines and automation.
HTML offers a visual report that’s easier to scan, especially when you need to share findings with teammates who don’t want to read a wall of CLI text. JSON is the better choice for CI/CD, but HTML is easier when presenting issues in reviews or security meetings.
Everything still starts with the same idea: run the audit, understand the output, and treat the results as actionable insight rather than noise.
Common npm Audit Commands and What They Do
Once you start using npm audits regularly, you realise the command itself isn’t all there is to it. There are different ways to run it, different levels of urgency behind each option, and different scenarios where one approach is safer than another. Understanding these commands helps you avoid accidental breakages while maintaining a clean and secure dependency tree.
npm Audit
This is the base command you run when you want a quick look at your project’s known vulnerabilities. It reads your package.json and package-lock.json, checks the GitHub Advisory Database, and prints out everything it finds. You’ll use this when you need a quick overview, such as before submitting a pull request or immediately after adding a new package. It’s the safest command because it only reports. It doesn’t change anything in your project.
npm auditnpm Audit Fix
This command takes things a step further by applying safe and compatible updates. It bumps dependency versions only when those updates won’t break your project. That’s why it’s the go-to command during routine maintenance or pre-deployment checks. You get automatic fix recommendations upgrades, but npm avoids anything risky. The process is straightforward: you run it, apply the fixes, and proceed without worrying about major version changes.
npm audit fix
npm Audit Fix --Force
This is where you need to be careful. --force installs the recommended fixes even when they require breaking changes. It might upgrade major versions, modify deep dependencies, or shift your lockfile in ways that affect runtime behaviour. You use this only when you understand the impact. For example, if your build is failing because of a critical vulnerability in a package that hasn’t been patched in a compatible version, --force might be your only option. However, it comes with the cost of retesting everything. You don’t run this in production pipelines without approvals, and you definitely don’t run it blindly.
npm audit fix --forcenpm Audit --JSON
This command is for automation, dashboards, or CI/CD workflows that need structured output. Instead of a human-friendly report, you get a JSON object with a predictable structure you can parse, store, or forward. Security teams love this because it plugs into scanners, dashboards, or alerting systems without friction. You’ll use it when generating audit logs, integrating with a monitoring stack, or feeding the results into an AI-powered security tool like Aikido Security for deeper analysis.
npm audit --json
Each command serves a different purpose. Some are safe. Some are aggressive. Some are designed for humans, while others are designed for machines. Knowing when to use each one keeps your workflow clean, maintains healthy builds, and prevents your dependency tree from growing into a silent security liability.
The limits of npm audit
npm audit is useful, but it’s far from complete. It provides visibility into known issues, but it doesn’t offer a comprehensive view of your dependency risks. And that’s where many teams get caught off guard. When you know what the tool can’t see, you start treating the audit as one step in your process rather than the whole process. The limitations are:
1. Coverage
npm audit struggles with transitive dependencies that have incomplete or missing metadata. If a package deep in the tree doesn’t publish its version history or advisory data correctly, the audit can’t map it. This means vulnerable components may sit five layers down without ever showing up in your results. You see a clean report, but it’s not actually clean.
2. Misconfigurations, Secrets, or Runtime Issues are Undetectable
If someone accidentally commits a token, npm won’t flag it. If your logging library is misconfigured or your app uses unsafe defaults, npm won’t say a word. The tool only checks package versions. It doesn’t understand how those packages behave in your environment.
3. Audit Works Only With Known Vulnerabilities
It cannot warn you about zero-days or emerging malware campaigns. When something new appears in the wild, there’s always a delay before it enters the advisory database. That gap is where attackers move fastest.
4. No Context-based Prioritization
npm audit can’t tell whether a vulnerable package is actually loaded in production or only used in tests. It treats everything as equal, which leads to noise. Teams often end up fixing issues that don’t matter, while missing paths that genuinely affect runtime behavior.
5. The Human Side
Audits need to be run manually or wired into scripts. If you don’t automate them, they pile up and create audit fatigue. This is evident in the latest State of AI in Security & Development 2026 report by Aikido Security, which reveals that 65% of teams admit to bypassing or delaying fixes due to noise and alert fatigue. Over time, important issues blend into background noise.
So npm audit helps, but it allows only within its boundaries. Knowing those boundaries is what lets you build a safer and more dependable security workflow.
Before You Ship Anything Else
Auditing your dependencies is no longer optional. It’s the baseline for keeping your Node.js projects healthy, even if npm audit doesn’t cover everything you need. You now understand where it helps, where it falls short, and why relying on it alone leaves you exposed. That’s where tools like Aikido Security step in.
You get continuous checks, zero-day detection, and deeper insight into how your dependencies behave across environments. Want real coverage instead of partial visibility? Get started with Aikido Security today!
You might also like:
- Top Code Vulnerability Scanners – Side-by-side comparison of static analysis tools
- Top ASPM Tools – End-to-end Application Security Posture Management
- OSWAP Top 10 2024 – Develop safer applications and tools



