On January 14th, 2026, I claimed a package on npm called react-codeshift.
I wasn't the author. I'd never written a line of code for it. The package had never existed. No one had ever published it. And yet, 237 GitHub repositories were already referencing it, instructing AI agents to install it. Some of them were actually trying. I was getting downloads for a package I'd just published, with nothing in them.
Where did the name come from? An LLM made it up. How did it spread to 237 repos? Agent skill files. Copy-pasted, forked, translated into Japanese, never once verified. I found it and claimed it before anyone else could.
The research
Back in July 2025, I started looking into npx confusion issues. These are npm package names that appear in documentation/code but were never actually published. The idea was simple: scrape package.json scripts and README files across all of npm for npx <package> patterns and check if those packages actually exist. Turns out, a lot of them don't.
Then the whole S1ngularity attack happened, so I shelved the research. Holiday season rolls around, I pick it back up. This post covers just one branch of that research. More to come.
Enter react-codeshift
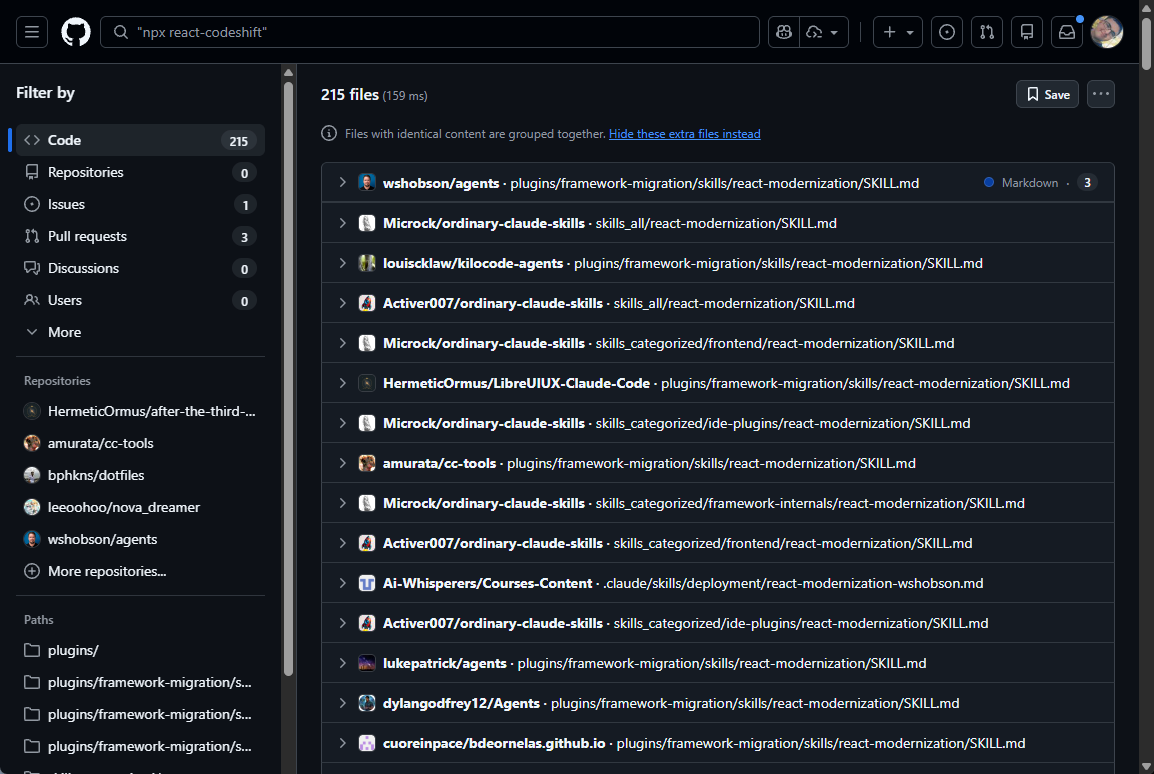
I picked up the research again in December, and decided to extend it to also index GitHub by scraping for references to npx commands. react-codeshift came up a lot. Over 200 repositories. By the time I claimed it, that number had grown to 237+.
The thing is, react-codeshift didn't exist. Not until I claimed it. But the name sounds legitimate. Two real packages do exist:
An LLM mashed these together and hallucinated react-codeshift. A plausible name for a tool that doesn't exist. A classic
The origin story
I traced it back to a single commit: 65e5cb0 in the wshobson/agents repository, dated October 17th, 2025.
That commit dumped 47 LLM-generated "Agent Skills" across 14 plugins. No apparent human review. At least two of those skills (react-modernization and dependency-upgrade) contained this:
npx react-codeshift --transform=react-codeshift/transforms/rename-unsafe-lifecycles.js ./src
npx react-codeshift --transform=react-codeshift/transforms/new-jsx-transform.js ./srcLooks legitimate. Sounds legitimate. The transform paths mirror the structure of real codemods.
Except it didn't exist.
Skills: The new attack surface
We've seen typosquatting and AI slop packages. This is a real case of slopsquatting in practice, not just speculation. And it's being spread through Skills.
Skills are a new standard: Anthropic's Agent Skills Specification, Claude Code plugins, MCP servers. They all use skill files to tell AI agents what to do. These files look like documentation: Markdown, YAML, plain text instructions.
But they're executable instructions. When an AI agent loads a skill file, it follows the commands. It doesn't verify that npx react-codeshift exists. It just runs it.
When npx can't find a package locally, it prompts:
Need to install the following packages:
react-codeshift
Ok to proceed? (y)The agent hits y. So would most people. Agents are just like us that way. The blind leading the blind, at scale.
Proof of active execution attempts
After claiming the package, I watched the download telemetry:
Normal packages see 60-100 downloads on day one (registry mirrors, security scanners), then zero afterward. Nobody's actually trying to use them.
But react-codeshift? That persistent trickle of 1-4 downloads per day? Those are real. Those are AI agents following skill instructions and triggering npx downloads.
The skills are being used. The hallucinated package is being executed. If I hadn't claimed it first, an attacker could have.
The spread pattern
All 237 repositories trace back to the same source. The pattern is almost entirely direct forks:
wshobson/agents(origin)- ~100 forks keeping the exact path:
plugins/framework-migration/skills/react-modernization/SKILL.md - One user copied it into 30+ of their own repos
- A handful of reorganizations into different directory structures
- Even a Japanese translation!
- One repo switched
npxtobunx. Same hallucinated package, different runner.
It's not just npx
The same pattern applies to every package runner:
npx react-codeshiftbunx react-codeshiftpnpm dlx react-codeshiftyarn dlx react-codeshift
They all resolve to the same npm registry. They all prompt before installing. They all get approved without a second thought. If an LLM hallucinates a package name in one form, it'll hallucinate it in others too.
It's viral, but shallow. No major repositories. No high-star projects. Just agents teaching agents to use a package that didn't exist. Agents all the way down. A self-improving system, in a way.
Why this matters
This wasn't a massive breach. Nobody got pwned. The package is now a safe placeholder.
But it's a useful case study in how these things spread:
- LLMs hallucinate plausible package names. Especially for domain-specific tooling where the naming conventions are predictable.
- Skills get copy-pasted without review. They look like documentation, so they don't get the same scrutiny as code.
- Agents follow instructions literally. That's their job.
- npx prompts, humans approve. The friction is low enough that most people just hit y.
- Unclaimed names are first-come-first-served. Anyone can register them.
I happened to find this one and claim it. The pattern is worth understanding.
What should you do?
If you maintain agent skills or AI tooling:
- Treat skills as code, not documentation. Review them. Audit them. Version control them with the same rigor as source code.
- Verify package names exist. Before committing any
npx <package>instruction, check that the package is real and published by who you think published it. - Search your codebase. Run
grep -r "npx react-codeshift"and fix any hits. Replace with the correct tools:npx jscodeshiftfor generic codemodsnpx react-codemodfor React-specific transforms
Indicators of Compromise
npm package: react-codeshift
The bigger picture
Skills are the new code. They don't look like it. They're Markdown and YAML and friendly instructions. But they're executable. AI agents follow them without asking "does this package actually exist?"
This was a hallucination. It spread to 237 repositories. It generated real download attempts. The only reason it didn't become an attack vector is because I got there first.
The supply chain just got a new link, made of LLM dreams. This is just one finding from the npx confusion research. More coming.

Secure your software now





.avif)
