Introduction
DevSecOps isn’t just a buzzword in 2026. It’s how modern teams build software without leaving security behind.
About 50% of DevOps teams have now adopted DevSecOps practices, meaning automated security checks are embedded throughout development. And for good reason: cyber threats are evolving, from surging open-source supply chain attacks (over 10,000 malicious packages were found in one quarter) to misconfigurations that attackers exploit in cloud infrastructure.
Old-school security gates and last-minute audits just can’t keep up. Developers need no-nonsense tools that catch vulnerabilities early and minimize the chaos of fixes later on.
In this article, we cut through the noise and highlight the top DevSecOps tools that actually make a difference. These platforms help you shift security left, thereby integrating code scanning, open-source dependency checks, cloud config auditing, and more into your CI/CD pipeline.
We’ll start with an overview of the leading tools (unranked, alphabetical), then break down the best choices for specific use cases like developer-friendly tools, enterprise platforms, startup budgets, open-source options, and cloud-focused solutions. Skip to the relevant use case below if you’d like.
- Best 4 DevSecOps Tools for Developers: Aikido Security · Snyk
- Best 5 DevSecOps Platforms for Enterprise: Veracode · Aikido Security
- Best 5 DevSecOps Tools for Startups & SMBs: Aikido Security · SpectralOps
- Best 5 Open Source DevSecOps Tools: Snyk (free tier) · SpectralOps
- Best 5 DevSecOps Tools for Cloud Infrastructure: Aikido Security · Snyk
TL;DR
Aikido is the ultimate DevSecOps platform, earning our top recommendation with its “shift-left on autopilot” approach. The platform covers code, cloud, protect (automate application protection, threat detection and response) and attack (detect, exploit and validate your entire attack surface, on demand). You can benefit from one suite with everything covered or you can get each best-in-class product (SAST, SCA, DAST) and expand and integrate as you wish.
Also, it ties into your pipelines and IDEs to scan code, dependencies, containers, IaC – you name it – in the background, then uses AI triage to kill ~85% of the noise.
The payoff: developers get security baked into their workflow (with fix suggestions at their fingertips), and technical managers get end-to-end coverage without hiring an army. Plus, Aikido’s free starter plan and flat pricing as you grow means you can scale DevSecOps without scaling costs unpredictably.
What is a DevSecOps Tool?
A DevSecOps tool is designed to weave security directly into the fabric of software delivery. These tools automate the tedious parts of security so that vulnerabilities, misconfigurations, and compliance gaps are caught early in development, not after deployment. In other words, they make “secure by design” a reality rather than a slogan.
The goal isn’t just to find issues, but to provide actionable insights developers can fix quickly, often right from their IDE or CI/CD pipeline.
Importantly, DevSecOps tools aren’t built only for security teams. They bridge the gap between developers, operations, and security by embedding guardrails into existing workflows. The best tools integrate seamlessly into DevOps toolchains, offering policy enforcement, automated testing, and real-time monitoring without slowing down innovation.
Top 7 DevSecOps Tools in 2026
(Listed alphabetically, each tool takes a unique approach to integrating security into development. From all-in-one platforms to specialty scanners, these solutions help teams code and deploy more securely without the typical security theater.)
First off, here’s a quick comparison of 7 standout DevSecOps tools and what they cover at a high level. We compare their support for code scanning, open-source dependency protection, and cloud/container security, as well as who they’re ideal for:
1. Aikido Security – One Suite DevSecOps Platform
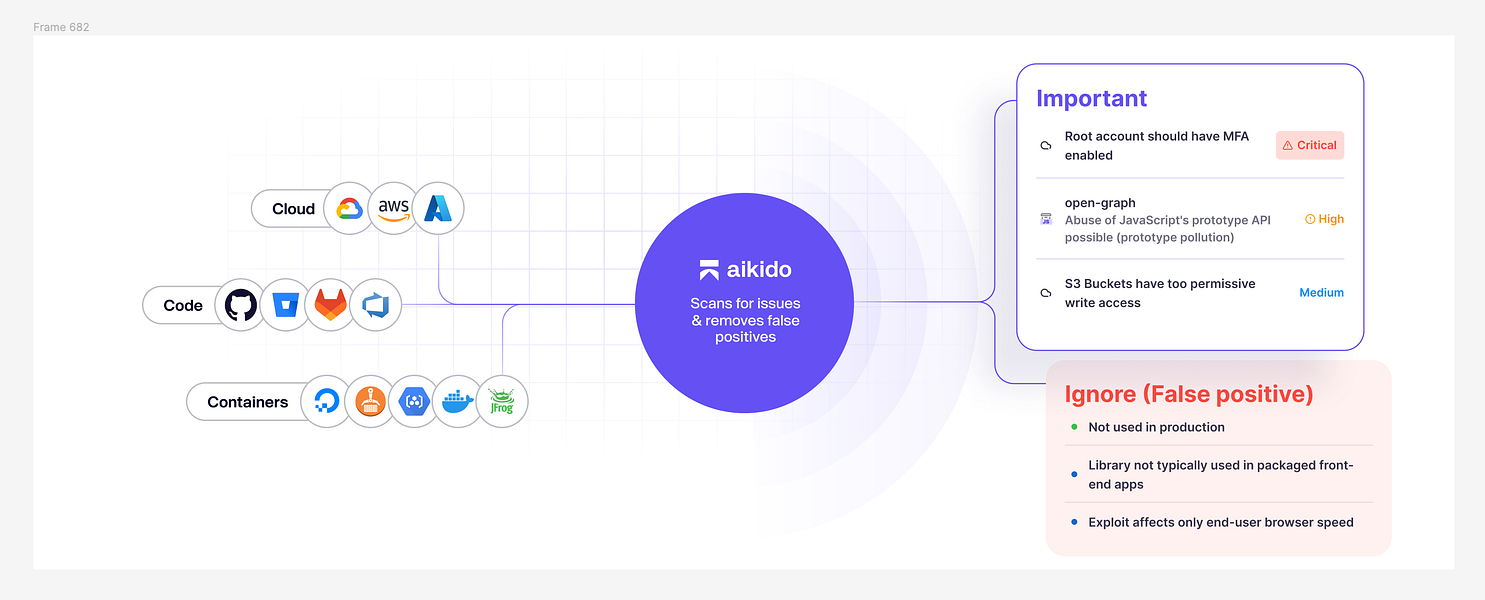
Aikido is a developer-first security platform. For organizations looking to cover one element of DevSecOps, Aikido offers best-in-class SAST, DAST, SCA, secrets detection, AI penetration testing, cloud security and other tools that integrate with any infrastructure.
You can also use Aikido as a complete DevSecOps platform that covers everything from code to cloud and even runtime security. The goal: give developers a single pane of glass for security without the usual friction.
Aikido’s secret sauce is automation and AI. It uses AI triaging to cut out ~85% of noise, so you’re not flooded with false positives. It even offers one-click fixes: for example, it can auto-generate a patch PR to upgrade a vulnerable library or Docker base image.
Key features:
- Best-of-breed scanners: Aikido offers best-in-class scanners for any part of your IT estate. Code scanning, IaC scanning, API scanning, etc. And compared with other scanners, Aikido has shown better reachability analysis and auto remediations.
- Connected “code-to-cloud” coverage: Aikido links code, cloud, and runtime in one seamless workflow. You can start with the module for (code scanning, container/IaC scanning, API security, and runtime protection) and scale to gain deeper context as you expand.
- AI AutoFix and triage: Automatically prioritizes real issues and suggests fixes. Aikido can literally fix some vulns for you via AI AI (saving you from hours of manual remediation).
- Dev-friendly integrations: Comes with 100+ integrations, like – VS Code, JetBrains IDEs, GitHub/GitLab, CI/CD pipelines, – so security checks run in the background of your normal workflow. No extra steps or “go log into this dashboard” nonsense.
- Noise reduction: Smart deduplication and context awareness mean you see one alert for one problem, not 500 duplicates. Less “cry wolf,” more real issues.
Customer review
Aikido integrates directly into devs’ daily work. For example, commit code with a new vulnerability, and you’ll get an alert (and even a fix suggestion) in your pull request within seconds.
One G2 reviewer highlighted that Aikido “offers a clean, intuitive interface… designed with developer workflows in mind, reducing noise and focusing on actionable issues.”
Best for: DevSecOps leads, CISOs that are aware of the needs of developers from large enterprises, developer-led teams, startups, and scaleups.
Aikido is like an automated AppSec expert that sets itself up in minutes.
It’s free for 2 users to get started (no credit card required), with paid plans as you grow, so startups and lean teams can immediately add security without blowing the budget.
2. Aqua Security – Cloud-Native App Protection

Aqua Security is an enterprise-grade platform for securing containers, Kubernetes, and cloud deployments. Aqua’s strength is full lifecycle container security from scanning images in CI and registries to locking down running workloads. Its vulnerability scanner checks your container images against one of the industry’s broadest CVE databases (drawing on sources like NVD plus Aqua’s research), so it finds known flaws in OS packages and libraries inside your images. Beyond that, Aqua provides cloud security posture management and even runtime defense (via agents that detect and block suspicious activity in containers).
Key features:
- Comprehensive image scanning: Integrates with CI pipelines and container registries to automatically scan images for vulns and misconfigs before deployment. Supports all major base images and languages.
- Kubernetes admission control: Can prevent pods from running if an image has too many issues. Policies ensure only compliant images get to production.
- Runtime protection: Aqua isn’t just “shift-left” – it deploys agents (or uses eBPF) to monitor containers at runtime, kill suspicious processes, and alert on attacks. This closes the loop if something slips by scanning.
- Compliance and benchmarks: Comes with templates for CIS benchmarks, PCI, etc., and can flag config issues (like a container running as root). Helps tick the boxes for enterprise compliance needs.
- Ecosystem integrations: Works with all the cloud providers and orchestration platforms. Aqua can pull in cloud asset info, integrate with SIEMs, and plug into CI/CD tools.
Customer review
One enterprise user notes that Aqua’s scanners are “very performant” under heavy workloads – “we throw so much load at [Aqua] and rarely see issues,” according to a G2 review. This is important for large orgs scanning thousands of images.
Best for: Large organizations running containers/K8s in production. If you need a bulletproof container security solution that also ties into cloud infrastructure, Aqua is a top choice. It is a paid platform (with a reputation for strong support).
For smaller teams or individual devs, Aqua’s open-source tools like Trivy can be a great starting point, while the full Aqua platform shines in enterprise environments.
3. Checkmarx – Enterprise Code Security Suite

Checkmarx is one of the OGs of static application security testing (SAST). It’s a heavyweight solution known for deeply analyzing code for vulnerabilities, supporting a huge range of languages and frameworks. Checkmarx’s SAST engine digs into your codebase to find issues like SQL injection, XSS, insecure config, and more, often with detailed path traces. Enterprises often like Checkmarx for its on-prem option and the ability to customize rules. It also offers SCA (open source library scanning) and IaC scanning as separate modules, plus IAST/DAST products, aiming to be a one-stop shop for AppSec.
Key features:
- Deep static analysis: Checkmarx excels in thorough code scanning – it scored 9.0/10 in “Static Code Analysis” on G2, with reviewers praising its detailed insights into vulnerabilities. It can handle big monolithic codebases and legacy languages that some newer tools might miss.
- Integration into CI/CD: You can automate Checkmarx scans in your pipelines (Jenkins, Azure DevOps, etc.) and set conditions to fail builds on certain findings. It also has an IDE plugin to catch issues as developers write code.
- Reporting & dashboards: The platform provides tons of data visualization – funnel charts, data flow graphs, and trend reports – which management and auditors appreciate. One G2 user specifically liked the “UI implementations… (data flow matrices) and suggestions for the best place to fix vulnerabilities.”
- Compliance and policy: Define security policies (e.g., “no high-severity vulns before release”) and track compliance over time. Checkmarx can map findings to standards like OWASP Top 10, PCI, etc., helping with governance.
- Extensibility: You can customize rules or write new ones if you have specific patterns to check for (useful for internal secure coding guidelines). Checkmarx also updates its vulnerability rulesets to cover newly discovered CVEs and CWEs.
Customer review
Now, the flip side: Checkmarx is powerful but can be complex. Scans are known to be slower than many modern tools, and it may throw a high volume of false positives if not tuned properly.
As one G2 reviewer put it, you get a lot of alerts and “have to carefully tailor it to each project” to avoid noise. It’s also not cheap, and usually requires a sales process and deployment of a server or cloud instance.
Best for: Enterprises with large, mission-critical codebases and dedicated AppSec teams. If you need extreme depth in code analysis and are okay with spending time on configuration (and budget on licensing), Checkmarx is a solid choice. It’s less suited to fast-moving startup environments due to the heavier setup and tuning required.
Consider using Checkmarx when security is a top priority and you have the resources to manage it (or if you’re stuck with a lot of older code that newer dev-focused tools struggle to scan).
4. GitHub Advanced Security – Built-In GitHub Code Security

GitHub Advanced Security (GHAS) turns GitHub into more than just a code hosting platform, it adds security superpowers to your repos. GHAS includes CodeQL code scanning (a SAST engine using CodeQL queries to find vulnerabilities in your code), secret scanning (to catch secrets/API keys before they leak), and dependency vulnerability alerts (powered by Dependabot). The big selling point: it’s native to GitHub. No new UIs to learn or external scanners to integrate your security alerts appear alongside your code and pull requests.
Key features:
- Code scanning with CodeQL: GitHub can automatically scan your code with CodeQL queries for many languages (C/C++, Java, JS/TS, Python, Go, C#, and more). These checks find things like SQL injection, XSS, etc., and the results show up in the Security tab of your repo or inline in PRs. You can use GitHub’s provided query sets or even write custom queries if you want to detect project-specific patterns.
- Secret scanning: GHAS will scan for patterns that look like secrets (API keys, tokens, credentials) in your commits and PRs. If it finds one, it can alert you or even block the git push (for really obvious ones). This helps prevent the classic “oops, we committed a password” mistake.
- Dependabot alerts & updates: GitHub already alerts all users about known vulnerable dependencies (thanks to its built-in advisory database). With GHAS, you get additional features like Dependabot security updates that automatically open a PR to bump a vulnerable library version. It’s like having a bot that watches your package.json or pom.xml and proactively suggests fixes.
- Integration into workflow: Because it’s part of GitHub, devs see security issues in the same place as code. For example, when you open a pull request, CodeQL can run and add comments if it finds a flaw in the changed code. This inline approach makes it easier to fix issues on the spot. GHAS also integrates with GitHub Actions for custom workflows (you can fail a build if certain alerts are present, etc.).
- Enterprise compliance: For companies that host their code on GitHub Enterprise, GHAS provides audit logs and can be a checkmark for compliance needs (since it helps enforce security policies across all repos).
Customer review
It’s worth noting that GHAS is an add-on for GitHub Enterprise. – iIt’s not free (aside from some features like Dependabot, which are free on public repos). Some users find its coverage is not as broad or deep as dedicated tools (CodeQL has great findings, but only for certain vulnerability classes and languages). However, teams love the convenience.
As one Reddit user said, using GHAS is “better than nothing” when you don’t have another security tool – it’s right there in your development flow.
Another liked that it has “good integration into PRs” for developers, even if other aspects felt a bit basic.
Best for: Organizations already on GitHub that want an easy, integrated way to add security. If your developers live in GitHub, GHAS brings security to them instead of making them go to a separate tool. It’s especially great for teams with limited AppSec staff; – you turn it on and get decent coverage out -of -the -box.
Just keep in mind it’s most effective for projects using the languages CodeQL supports, and it won’t cover things like runtime cloud security. For those, you’d complement GHAS with other tools.
5. GitLab Ultimate – DevSecOps in One Platform

GitLab Ultimate (the top tier of GitLab) is often touted as a complete DevSecOps platform. With GitLab, your repo, CI/CD pipelines, and security scanners are all in one application – a single DevOps platform that includes robust security testing. GitLab Ultimate comes with 15+ integrated security tools covering SAST, dependency scanning, container scanning, Dynamic App Sec Testing (DAST), secret detection, fuzz testing, and more. The idea is that developers and security teams can collaborate in one interface, and you don’t need to bolt on a bunch of external products to secure your CI/CD pipeline.
Key features:
- Built-in SAST/DAST: GitLab has its own SAST analyzers for many languages (or it can run popular open-source analyzers under the hood). It automatically runs these in CI if you include the provided templates. Similarly, it can run DAST scans against your web app (it even has an integrated ZAP scanner for DAST). Results show up in the merge request and in a security dashboard.
- Dependency and container scanning: As part of the pipeline, GitLab will scan your project’s dependencies (SCA) and any container images you build. It uses databases of known vulns to flag issues in your open-source libs (like an out-of-date lodash or a vulnerable Log4j). For container images, it checks OS packages and language packages in the image for CVEs.
- Coverage of other risk areas: GitLab Ultimate also includes IaC scanning (checking your Terraform or K8s configs for security issues), secret detection in code, and even license compliance checks. It’s a broad net to catch anything risky going through your pipelines.
- Single interface and repo-centric view: Developers see security findings right in the merge request where they can immediately take action (approve, create issue, dismiss as false positive, etc.). Security teams get an aggregate security dashboard across projects, showing all vulns and compliance status in one place. All findings can be managed and tracked in GitLab issues.
- Enterprise features: Since it’s aimed at larger organizations, you get things like role-based access control, integration with Jira for ticketing, compliance reports, and audit logs. GitLab can be self-hosted if you have compliance restrictions, or used in GitLab’s cloud.
Customer review
One advantage of GitLab’s approach is consolidation: It’s one system to maintain. Companies looking to simplify their toolchain appreciate this. However, the depth of each integrated scanner may not always match dedicated tools. For example, GitLab’s SAST might not be as advanced in some language as a specialized scanner, but it’s improving rapidly.
Best for gainful: Teams that already use GitLab for code and CI, and want security built into that same ecosystem. It’s particularly attractive to enterprises that value an all-in-one platform for DevOps and security – Dev, Sec, and Ops all collaborating in one application. Keep in mind that Ultimate is the highest tier (read: $$$). If you’re a smaller team, you might use GitLab’s free/cheap tiers and add external scanners instead. But for a large org, the cost of Ultimate can be justified by the breadth of features and reduced overhead of managing multiple tools.
6. Sonatype Nexus Lifecycle – Open Source Dependency Security

Sonatype Nexus Lifecycle is the go-to DevSecOps tool for many organizations when it comes to open-source component governance. In plain terms, Sonatype helps you track and secure the open-source libraries and packages in your applications. It constantly evaluates your dependencies (and even containers and infrastructure templates) for known vulnerabilities and license compliance issues. Sonatype has a rich data feed (drawing from public CVE databases and its own research like OSS Index) to identify risky components. If you’ve heard of Nexus Repository or Nexus IQ Server – Nexus Lifecycle is the scanning brain behind those, focused on policy enforcement for open source usage.
Key features:
- Software Composition Analysis (SCA): Nexus Lifecycle scans your application’s BOM (bill of materials) to find all open-source components and their versions. It then flags any with known vulnerabilities or license problems. This covers packages from package managers (Maven, npm, PyPI, Go modules, etc.) as well as container base images layers.
- Policy enforcement: You can set up rules (policies) about what is allowed. E.g., “fail the build if any critical vulnerabilities are present” or “warn if a dependency has a GPL license”. Sonatype will enforce these at different stages, in the IDE (warn the dev), in the CI pipeline (fail the build), or in the repository (quarantine an artifact) depending on how you configure it.
- Continuous monitoring: It’s not just a one-time scan. Sonatype will continuously monitor your apps for new vulns. If tomorrow a new CVE emerges that affects a library you use, it can alert you immediately (or even automatically create a Jira ticket, etc.). This “constant vigilance” means you don’t miss out on newly disclosed threats.
- Developer integrations: It plugs into many tools – there are IDE plugins that tell devs about vulnerable dependencies while coding, CI/CD integrations, and even GitHub pull request checks. The idea is to catch issues early (shift left) and make it easy for devs to replace a bad library with a safer one.
- Reporting and IQ dashboard: Nexus IQ (the dashboard) gives a clear view of the risk across all your applications. You can see which apps have the most severe issues, track remediation over time, and generate reports for compliance (e.g., an open-source license report for legal).
Customer review
Users often praise Sonatype for helping drive down risk from open-source. As one Reddit user shared, “we use Sonatype’s Nexus Lifecycle… it’s decent for identifying license issues and vulnerabilities, plus the vendor has been pretty responsive to our support requests.” The continuous improvements and data quality are strong points.
Be aware that Nexus Lifecycle is primarily about known vulnerabilities in third-party components. It doesn’t scan your proprietary code (that’s what SAST tools are for), and it’s not a runtime cloud security tool. It’s laser-focused on the supply chain aspect of your software.
Pricing-wise, it’s an enterprise product (licenses per app or dev seat typically), but the value can be high if you’re pulling in hundreds of libraries and need to manage that risk systematically.
Best for: Companies that heavily use open-source and need to enforce security and compliance standards around it (think fintech, healthcare, or any org with strict rules on what code can be used). If you’ve ever been burned by a vulnerable library or a license issue, a tool like Sonatype is your safety net.
For smaller teams or open-source projects, Sonatype might be overkill, so – you might start with free tools (like OWASP Dependency-Check or GitHub alerts). But at scale, Nexus Lifecycle is like an air traffic control for your open-source usage, ensuring every component in your dev pipeline is vetted.
7. Snyk – Developer-Focused Vulnerability Scanner

Snyk has made a name as one of the most dev-friendly security platforms. It started with a focus on finding vulnerabilities in open-source dependencies (SCA), but now Snyk offers a suite of tools: Snyk Open Source (dep scanning), Snyk Code (SAST for your code), Snyk Container (image scanning), and Snyk IaC (infrastructure-as-code checks). All are delivered as a service with tight integrations into developer workflows. Snyk’s philosophy is to empower developers to find and fix issues fast, with minimal fuss. Its UI and reports are clean, and it even suggests remediation (like upgraded package versions) and can automatically open PRs.
Key features:
- Open source dependency scanning: Snyk monitors your project’s dependencies for known vulns. It boasts a huge vulnerability database. When it finds an issue, Snyk not only alerts you but often tells you the nearest safe version to upgrade to.
- Snyk Code (SAST): Using a mix of proprietary analysis and some tech from their acquisition of DeepCode, Snyk Code scans your source for security bugs and code quality issues.
- Container and IaC scanning: Snyk Container will scan container images (looking at OS packages and app deps inside) for vulns, and even give base image upgrade suggestions (e.g., “You’re using node:14, switch to node:16-alpine to eliminate 50 vulns”). Snyk IaC scans config files like Terraform, CloudFormation, Kubernetes manifests for misconfigurations (like open security groups, etc.).
- Integrations galore: Snyk integrates with GitHub, GitLab, Bitbucket, Azure Repos, Jira, Slack, Docker Hub, and CI/CD pipelines. It’s designed so that devs see issues in the tools they already use. For example, you can get a Slack alert when a new high-severity issue is found, or see a badge on your repo. Snyk also has IDE plugins for VS Code, IntelliJ, etc., to highlight vulnerabilities as you code.
- Developer-centric UX: Snyk’s interface and approach is often praised for being intuitive. You get dashboards per project, pull request annotations, and the ability to ignore or snooze findings (with justification) to manage risk pragmatically. It focuses on actionable info and even gives you a risk score/priority to help triage.
Customer review
Developers often mention how easy Snyk is to adopt. As one Reddit user commented, “Snyk is one of the easier tools to set up, especially if you’re integrating with GitHub.” And they noted “the nice thing with Snyk is its other tooling (SCA, IaC) and how they work together.” Snyk’s strength is indeed the seamless combo of different scanners under one roof, with a consistent workflow.
On the flip side, Snyk is a commercial product with paid plans (the free tier is limited to small projects or a certain number of tests per month). Some have found its reporting for management less robust, and as your usage grows, costs can increase.
Snyk’s depth in each area (SAST, Container, etc.), while good, may not always beat a dedicated tool that focuses on one thing but the convenience of an integrated platform often outweighs that for most cases.
Best for: DevSecOps teams that want to enable developers to own security fixes. Snyk is ideal for CI/CD integration and for devs who will act on security issues if they’re presented nicely (versus dumping a PDF of findings on them). If you’re looking for a modern alternative to legacy scanning tools, Snyk is probably on your shortlist.
Now that we’ve covered the main players, let’s zoom in on which tools fit best for specific scenarios. Not every team has the same needs; a two-person startup, a 10,000-person enterprise, and an open-source project maintainer all approach DevSecOps differently.
Below, we break down recommendations by use case, so you can find the tools that will integrate best with your workflow and resources.
Best 4 DevSecOps Tools for Developers
Developers want security tools that blend into their workflow and catch issues early, without a ton of noise. The best DevSecOps tools for devs are ones that feel like a natural extension of coding, – think IDE plugins, git hooks, or super-fast CLI tools.
Key priorities include:
- Speed:No one will run a tool that takes 30 minutes every commit,
- Low false positives:Devs will ignore noisy tools, and
- Actionable output:Clear advice or auto-fixes so it’s easy to remediate within the code.
Essentially, dev-focused tools act like an assistant, not a nag.
Here are the top 4 DevSecOps tools tailored for developers:
1. Aikido Security – “Secure by default” for devs
Aikido was built by developers for developers. It’s perfect because it embeds security checks directly into the dev process. You get instant vulnerability alerts in your IDE and in pull requests, and its AI AutoFix can even generate patches for you.
It’s essentially a developer’s security sidekick, handling code scans, dependency checks, and even cloud config audits in the background so you can focus on coding.
With virtually zero setup and a no nonsenseUI, devs can adopt Aikido in minutes and start getting results (the free tier is a nice bonus for devs to try).
2. Snyk – Integration-rich
Snyk has earned a dev-friendly reputation. It also lets developers ignore or snooze certain issues via config, which is good for tuning out false positives or less relevant issues. With IDE plugins for immediate feedback, Snyk meets developers where they work.
2. GitHub Advanced Security – Native code scanning for GitHub users
If your team is on GitHub, GHAS is a very dev-centric option. It surfaces security alerts right in your pull requests and code view, so a developer discovers a security problem just like a code review comment. The tight integration with GitHub (and tools like Dependabot) means there’s almost nothing new to learn.
Developers get suggested fixes for vulnerable dependencies and can see code scanning results within minutes of opening a PR. It’s not the most comprehensive scanner out there, but for devs who want something lightweight and built-in, GHAS delivers a decent baseline without any context-switching.
3. Lightweight OSS tools (for the DIY dev)
Many developers also string together open-source tools to cover their bases. For instance, Trivy (by Aqua Security) is a super-fast CLI scanner that a dev can run locally to check their code and containers. It’s as simple as “trivy fs .” or “trivy image myapp:latest” and catches a lot of common issues.
Another example is Bandit (for Python security linting) or ESLint plugins for security rules in JavaScript. These won’t have big fancy UIs, but for a developer who loves automation, scripting a few open-source scanners into git hooks or CI can be a powerful, free way to get security feedback from day one.
Best 5 DevSecOps Platforms for Enterprise
Enterprises typically have broader requirements, think: scalability, governance, integration with other corporate systems, and multi-team coordination.
The best enterprise DevSecOps platforms must be flexible enough to offer centralized management and modularity.
- Centralized management security lead can see risks across hundreds of projects, enable role-based access control to manage who can do what, generate robust compliance reporting, and other features
- Modularity to pick a module (SAST tool) that meets their needs today, and either decide to add other modules, such as SCA or DAST, later, or integrate it seamlessly with other security vendor solutions.
Here are DevSecOps tools that shine for enterprise use:
1. Aikido Security – Scalable DevSecOps, Built for the Enterprise
Aikido Security stands out as one of the few DevSecOps platforms designed with both developer experience and enterprise governance in mind.
From its On-prem scanners to Monorepo splitting features for improved security issues management, Aikido enables enterprises to not just meet current security requirements, but innovate confidently for the future.
Its role-based access control (RBAC), SSO/SAML support, and audit logging make it compliance-ready out of the box for standards like SOC 2, ISO 27001, and GDPR.
Also, Aikido’s modular architecture lets enterprises roll out scanning capabilities progressively. Starting with, say, SAST or SCA and then expanding to other modules as the need grows.
Unlike legacy enterprise tools that often feel heavy and siloed, Aikido focuses on developer-friendly workflows and zero-noise results. That means fewer false positives, faster remediation, and tighter integration with tools enterprises already use.
2. Checkmarx – Proven SAST for the enterprise
Many large companies stick with Checkmarx for its depth and track record. It’s heavy but battle-tested. Enterprises with hundreds of applications use Checkmarx to enforce coding standards, often integrating it with centralized CI pipelines and quality gates.
Checkmarx’s reporting, auditing features, and the ability to customize rules cater well to enterprise governance needs. It also scales with support for scanning millions of lines of code and dozens of languages. If an enterprise has strict security SLAs for code (e.g., “no OWASP Top 10 issues in production code”), Checkmarx is a tool that can be configured to enforce that policy and produce evidence for auditors.
3. GitLab Ultimate – One platform for Dev, Sec, and Ops
Enterprises that have adopted GitLab for DevOps often leverage Ultimate to bring security into the same platform. The appeal for enterprise is having source code management, CI/CD, and security in a single system. This means easier administration and a consistent experience for all teams.
GitLab’s built-in security controls can be centrally managed: security directors can set project templates that automatically include security scans, and they can get group-level dashboards of all findings. Role-based access and audit logs in GitLab are strong, making it suitable for regulated industries. And because it’s self-hostable, enterprises can run it in their controlled environment if needed.
4. Aqua Security (Enterprise Platform)
While Aqua has open-source tools for devs, its enterprise platform is built for large-scale deployments. Big enterprises running thousands of containers or multi-cloud workloads choose Aqua for its comprehensive coverage and robust console.
It provides multi-tenant project structures (handy if you want to delegate some control to different teams but keep central oversight), and it integrates with SIEM/SOAR solutions to feed container and cloud security events into the bigger security operations picture.
Enterprises also value Aqua’s compliance reporting for frameworks like PCI, and its support for things like FedRAMP environments. Essentially, Aqua can serve as the enterprise’s container/cloud security hub, often replacing the need for separate vulnerability management and runtime tools.
5. Sonatype Nexus Lifecycle – Governance for open source
Enterprises worried about supply chain risk and license compliance often standardize on Sonatype. It’s used by Fortune 500 companies to ensure every open-source component in use is tracked and meets corporate policies.
In an enterprise, you might have thousands of apps pulling dependencies – Sonatype gives a centralized view of that landscape and can enforce rules (e.g., block builds that introduce a high-risk library). It also integrates with artifact management (Nexus Repo, Artifactory), adding another layer of control by preventing dangerous components from even entering the repository.
The result is a tightly governed software supply chain, which is increasingly a board-level concern. Enterprises also appreciate Sonatype’s customer support and data accuracy, as well as features like automatic pull requests for upgrades (reducing the manual effort to fix vulns across so many apps).
Honorable mentions: Veracode and Micro Focus Fortify (now OpenText Fortify) are also popular in enterprises. They provide similarly deep scanning and enterprise reporting, often as a service (Veracode) or on-prem (Fortify).
Many large organizations have used these for years in their SDLC. They weren’t in our main list, but if you’re evaluating enterprise AppSec, they’re worth knowing. Additionally, cloud-security focused platforms like Palo Alto Prisma Cloud or Lacework come into play for enterprises heavily leveraging cloud infrastructure, offering CSPM and workload protection at enterprise scale.
Best 4 DevSecOps Tools for Startups & SMBs
Startups and small-to-mid businesses need maximum security bang for minimum buck. They often don’t have dedicated security teams, so tools must be easy to use and preferably affordable (or free). The best DevSecOps tools for smaller teams are those that provide strong out-of-the-box security without requiring extensive tuning or maintenance.
These tools should be quick to set up (founders don’t have time for week-long deployments) and ideally scale with the company’s growth. Also, flexibility is key: a startup might pivot tech stacks or go from on-prem to cloud overnight, so a tool that covers multiple environments is a plus.
Here are great options for young companies:
1. Aikido Security – “Security team in a box”
For a startup, Aikido offers incredible value. It’s free to start and provides an immediate security blanket over your code, dependencies, containers, and cloud resources. Since Aikido combines many scanners in one, a small team can get SAST, SCA, container scans, and more without managing separate tools. It’s like hiring a whole security team in a box. Aikido’s 2026 State of AI, Developers & Security report found that one in four security leaders believe they’d likely suffer from a breach or an attack if they lost a single security engineer. That’s because many other security tools are so complex that a single security engineer takes with them their tribal knowledge when they leave; Aikido is the complete opposite of this.
The fact that it’s cloud-based and up and running in minutes fits a startup’s need to “just secure it” without fuss. As the startup grows, Aikido can scale and introduce more advanced checks, but on day one, it delivers a lot of protection with very low effort – perfect for a fast-moving company.
2. Snyk (Free Tier) – Quick wins in CI/CD
Snyk’s free tier is often a go-to for startups. It allows a decent number of scans and has no user limit, meaning your whole dev team can use it without paying until you hit certain project sizes. Startups also love that Snyk integrates with services they already use (like Vercel, Docker Hub, etc.), so it slides right into the existing toolchain.
3. GitHub Advanced Security (for those on GitHub)
If you’re a small team already paying for GitHub (or on a plan that includes GHAS for free on public repos), using GHAS is a no-brainer. It provides a baseline SAST and secret scanning without any new infrastructure.
Startups on GitHub can thus get some security checks “for free” as part of their development flow. It’s not exhaustive, but it will catch low-hanging fruit and is better than having nothing. This is especially relevant for open-source startups, since CodeQL scanning is free on public GitHub repositories – you can secure your open-source project without any cost.
4. Open-source solutions (budget-friendly DIY)
For cash-strapped teams, open-source DevSecOps tools can cover a lot of ground. Trivy is a fantastic choice because it’s free, open source, and simple. Even a two-person dev team can use Trivy locally or in CI to prevent obvious mistakes (like shipping a container with a critical CVE).
Another great free tool is Grype (by Anchore), which can be scripted into a build to fail if certain vulnerabilities are present. Startups often start with these because there’s no procurement or approval needed – just add the tool and go.
As long as you’re comfortable with command-line and maybe writing a few scripts, you can achieve a decent security baseline with open-source tools until you’re ready to invest in a platform.
Best 5 Open Source DevSecOps Tools
Not everyone has the budget or desire for commercial tools, and thankfully, there’s a rich ecosystem of open source DevSecOps tools. Open source solutions provide transparency (you can see what they’re scanning for) and flexibility (self-host and customize as needed).
The trade-off is typically convenience; you might not get a slick UI or integrated reports across tools. But for engineers who enjoy tinkering and want to avoid vendor lock-in, open source tools can cover most DevSecOps needs.
A few of the top open source DevSecOps tools include:
1. Opengrep
You might know Semgrep OSS!. Well, it's no longer open source and now called Semgrep Community Edition. Why? You can say “pressure from VCs”, “protecting against competition” or whatever.
Regardless, the community has been blessed with Opengrep, a fork of Semgrep CE, in response to its open-source clampdown.
Opengrep is a fast, open-source static analysis tool. It uses rules to find patterns in code – you can use hundreds of existing security rules or write your own with a simple syntax. Importantly, Opengrep is pretty language-agnostic and is loved by developers for its low false-positive rate.
If you’re looking for a transparent, scriptable security scanner that can adapt to your team’s workflows without the overhead of a full commercial suite, Opengrep is a solid starting point.
Backed by 10+ competing application security organizations including Aikido, Opengrep will only improve and grow.
2. OWASP ZAP (Zed Attack Proxy)
A staple for DAST, ZAP can be used to scan your web applications for vulnerabilities like SQL injection, XSS, and more. It’s completely free and maintained by the OWASP team. You can run it in an automated way (it even has a Docker image for CI usage) or use the desktop app for exploratory security testing. If you need to test your web app’s security in a QA environment without spending money, ZAP is a great choice.
3. Trivy
We’ve mentioned it before, but Trivy deserves a spot here. It’s an all-in-one scanner that covers container images, file systems, and now even Kubernetes configs and IaC. It’s open source (Apache 2.0 licensed) and very fast. Developers can run Trivy on their laptops or in CI to catch vulns in dependencies and container images. It’s essentially a Swiss Army knife of vuln scanning, and because it’s free, it’s widely adopted in open source projects and by small teams.
4. Grype
Another popular open source scanner (focused on vulnerabilities in containers and filesystems). Grype, backed by Anchore, can be easily integrated into scripts and CI pipelines. It has a growing community and is often used in tandem with Syft (an open source SBOM generator). The combo lets you generate a software bill of materials and then scan it for vulns – all with free tools. For those who prefer a modular approach (separate SBOM and scan steps), Grype is a solid component to include in a DevSecOps toolchain.
5. OWASP Dependency-Check
An older, but still useful, open source SCA tool. It scans project dependency files (Maven POMs, npm package.json, etc.) and reports known CVEs. While newer tools like Trivy or even GitHub’s built-in alerts have somewhat overtaken it, Dependency-Check can be run on-prem and can output reports that some compliance folks like. It’s a bit heavy and can be slow, but it’s free and covers a lot of ecosystems.
5. Semgrep (Community Edition)
Semgrep is a fast, open-source static analysis tool (though it also has a commercial SaaS version). It uses rules to find patterns in code – you can use hundreds of existing security rules or write your own with a simple syntax. Importantly, Semgrep is pretty language-agnostic and is loved by developers for its low false-positive rate. Using open source tools requires a bit of do-it-yourself assembly. You might, for example, use:
- ZAP for DAST,
- Semgrep for SAST,
- Trivy/Grype for containers, and
- OWASP Dependency-Check for SCA.
You won’t have one dashboard to rule them all, but you also won’t pay a dime. Many teams start this way and build internal scripts to glue results together (or use something like DefectDojo, an open source vuln management platform, to aggregate findings).
Open source tools also foster learning – your developers and DevOps engineers will gain security knowledge by working with them.
Best for: Teams with more time than money, or communities maintaining open-source projects. Also, organizations that are very sensitive about data and want everything in-house often prefer open source tools that they can host and control. Just remember the human cost – open source tools need updates and maintenance. But the flexibility and zero cost make them extremely appealing for many scenarios.
Best 5 DevSecOps Tools for Cloud Infrastructure
As infrastructure moves to the cloud, DevSecOps isn’t just about code. It’s about the configurations and resources in AWS, Azure, GCP, etc. Ensuring your cloud setup is secure (no wide-open S3 buckets, no leaked keys, proper IAM roles, etc.) is crucial.
The best tools in this category often fall under CSPM (Cloud Security Posture Management) or cloud infrastructure security. They continuously scan cloud configurations and sometimes even monitor at runtime for suspicious activity.
For DevOps teams heavily using Terraform, CloudFormation, or Kubernetes, infrastructure as code (IaC) scanning is also key – catching misconfigs before they go live.
Here are the top DevSecOps tools focused on cloud and infrastructure security:
1. Aikido Security – Code-to-Cloud visibility
Aikido is equipped with best-in-class cloud security posture management solution . It functions as a CSPM by scanning your AWS and Azure configs for misconfigurations continuously (like open security groups, publicly exposed storage, overly permissive IAM roles). It inventories cloud assets so you actually know what you have running.
What makes Aikido shine for cloud teams is how it correlates cloud findings with code. For example, it can tell you “this insecure S3 bucket is tied to these lines of code or this repo”, making it easier to fix at the source.
Aikido AI Cloud Search enables you to describe what you’re looking for. “Give me all VMs with CVE-2025-32433 that have port 22 open.”
For a DevOps team that wants an integrated view of app and cloud security, Aikido covers a lot, without needing a separate, expensive cloud security product.
2. Bridgecrew (Checkov) – IaC security as code
Bridgecrew (now part of Palo Alto’s Prisma Cloud) is focused on infrastructure-as-code scanning. Their open source tool Checkov is widely used to scan Terraform, CloudFormation, Kubernetes manifests, etc., for security issues (like an AWS security group allowing 0.0.0.0/0). Bridgecrew’s platform then adds on continuous cloud scanning and automated fixes.
For a startup or mid-size team, using the open source Checkov in CI can nip many cloud misconfigs in the bud. As you grow, the Bridgecrew SaaS gives a more centralized view and additional features like drift detection (comparing IaC to actual cloud).
3. Palo Alto Prisma Cloud – Comprehensive cloud security
Prisma Cloud (which now includes what was Bridgecrew, Twistlock, etc.) is an enterprise-level platform that covers cloud workload protection, container security, and CSPM. It’s a big beast with lots of features – from scanning IaC templates before deployment to monitoring running cloud resources for compliance and anomalies.
If you’re on a major cloud and need to enforce best practices (and have the budget), Prisma is often on the shortlist. It’s particularly good if you’re already using other Palo Alto products; it can integrate threat intelligence and network security with your cloud findings.
4. Lacework – AI-powered cloud threat detection
Lacework is a platform that not only checks configs but also uses behavioral analytics to detect suspicious activities in cloud and container environments. It’s known for reducing alert noise by learning what “normal” looks like in your cloud (e.g., usual API call patterns) and alerting when something deviates.
For DevSecOps teams, Lacework provides both build-time checks (IaC scanning, vulnerability scanning) and runtime monitoring. It’s a solid choice for cloud-native companies that want an all-in-one solution that’s smarter about distinguishing real threats from harmless anomalies.
5. Open Source & Cloud-Native Tools
If you don’t want to invest in a platform, there are open tools like Scout Suite (by NCC Group) or Prowler that can scan your AWS accounts for common issues. These are great free options to get a read on your cloud security posture.
Additionally, cloud providers offer native tools: AWS has Config, GuardDuty, Security Hub, etc., which can be wired up to provide continuous checks and alerts. Those require some assembly but are very useful.
For Kubernetes specifically, kube-bench (checks K8s clusters against CIS security benchmarks) and kube-hunter (does pen-test style discovery of K8s issues) are handy open-source additions to a cloud security toolkit.
In cloud infrastructure security, it’s often about coverage and context. A misconfiguration might not be a big deal unless it’s attached to a sensitive resource – the best tools can tell the difference. They also integrate with development: e.g., a good practice is using Terraform plan scans (with tools like Checkov) as part of your CI, so developers fix issues before deploying. Then use a continuous monitor to catch anything that slips through or changes out-of-band.
Best for: Teams using cloud services extensively, whether you’re automating everything via IaC or managing via cloud consoles. If your infrastructure lives in the cloud, you need at least some tool watching your configs and usage.
Smaller teams might start with open source scanners and cloud-native services (cheaper, piecemeal approach).
Larger teams or those with high sensitivity (fintech, etc.) often go for an integrated platform like Prisma, Lacework, or Wiz/Orca (two other big players in cloud security, which specialize in agentless monitoring and have gotten popular for their depth in cloud vuln detection – though note, we haven’t detailed them here due to focus on other tools).
The bottom line: don’t leave your cloud an unchecked Wild West. Even simple tools can catch the “OMG didn’t realize that was public!” mistakes before they become headlines.
Conclusion
DevSecOps isn’t achieved with a single tool, but by choosing the right tools that empower your developers and fit your organization’s needs. The tools we’ve discussed here represent the top options in 20265 to bake security into your software delivery pipeline.
Whether you’re a developer looking for a seamless security plugin, a CISO at an enterprise aiming to unify and scale AppSec, a startup founder needing quick protection, or an open-source maintainer on a budget – there’s a DevSecOps solution out there for you.
The common thread is automation and integration: the best tools operate in the background, catching issues continuously so your team isn’t firefighting late in the release cycle. Security becomes just another part of coding and deploying software, which is exactly where it should be in 20265.
You might also like:
- Top 7 ASPM Tools – Prioritize and triage results across scanners.
- Top Infrastructure as Code (IaC) Scanners – Secure your infra in the pipeline.
- Top Continuous Security Monitoring Tools – Enable continuous feedback and detection.



