Cloud-native applications provide the speed and scale modern teams need, but with this speed comes a new level of complexity. Cloud environments increase the IT landscape, making misconfigurations and vulnerable cloud components more common.
In an attempt to address these challenges, many teams are stuck between code security and cloud security. According to Aikido Security’s 2026 State of AI in Security & Development report, 93% of teams struggle to integrate application security with cloud security, resulting in higher incident rates and weaker overall protection. This disconnect leaves gaps where threats can slip through unnoticed.
The solution? Security should cover both code and cloud in a single platform.
Cloud-Native Application Protection Platforms (CNAPPs) do exactly this by consolidating multiple cloud security solutions, including cloud security posture management (CSPM), workload scanning, CI/CD integration, and runtime defense, into one unified platform. Instead of siloed tools and fragmented dashboards, teams get one pane of glass from development to production, enabling them to correlate security risks across code, containers, and cloud resources, reducing incidents and speeding up remediation.
In this guide, we’ll explore the top CNAPP tools organizations are using to secure their cloud-native applications. We’ll start with a comprehensive list of the most trusted CNAPP platforms, then break down which tools are best for specific use cases, whether for developers, enterprises, startups or multi-cloud environments.
You can jump to specific use cases below:
- Best 2 CNAPP Tools for Developers
- Best 5 CNAPP Platforms for Enterprise
- Best 2 CNAPP Tools for Startups & SMBs
- Best 4 CNAPP Tools for Multi-Cloud Environments
- Best 4 CNAPP Tools for AWS Cloud Security
- Best 3 CNAPP Tools for Azure Cloud Security
TL;DR
Aikido Security stands out among the CNAPP solutions reviewed, thanks to its comprehensive, cloud-native platform. It consolidates CSPM (cloud misconfiguration audits), SAST, SCA, IaC checks, secrets scanning, container security, and runtime protection into a developer-friendly workflow. It also provides end-to-end attack path analysis, AI-assisted risk prioritization, and superset policy enforcement across multi-cloud environments.
The result: End-to-end cloud security that covers code, containers, and multi-cloud infrastructure.
For both startups and enterprises, Aikido Security consistently ranks at the top in pilots thanks to its fast onboarding, modular architecture, AI-powered triage and autofix and cross-cloud visibility.
What Is a CNAPP (Cloud-Native Application Protection Platform)?
A Cloud-Native Application Protection Platform (CNAPP) is a unified cloud security solution designed to protect applications across their entire lifecycle from code to cloud to runtime. Rather than relying on separate security tools to detect misconfigurations, identity risks, runtime threats, and workload vulnerabilities, a CNAPP brings all these capabilities together into a single platform. A complete CNAPP solution typically includes:
- Cloud Security Posture Management (CSPM): Scans your cloud accounts (AWS, Azure, GCP) for misconfigurations, excessive permissions, and compliance violations.
- Cloud Workload Protection (CWPP): Secures workloads like VMs, containers, and serverless functions by scanning for vulnerabilities and malware, and monitoring behavior at runtime.
- CI/CD and IaC Scanning: Integrates into development pipelines and Infrastructure-as-Code templates (Terraform, CloudFormation, ARM/Bicep templates) to catch issues before deployment .
- KSPM (Kubernetes Security Posture Management): Analyzes Kubernetes clusters for insecure configurations, exposed dashboard endpoints and privilege escalation risks.
- Runtime Threat Detection: Continuously monitors cloud workloads and applications for attacks or anomalies.
Why You Need an Integrated CNAPP Solution
Here are a few things CNAPP’s ensure:
- Full-Stack Visibility: A CNAPP ties together code vulnerabilities, cloud configuration issues, and runtime threats in one view. Eliminating blind spots for developer and security teams.
- Fewer Alerts: By correlating issues across domains, CNAPPs prioritize what truly matters. They can suppress 100 minor alerts in favor of the one combination that could actually lead to a breach.
- DevOps Friendly Security: The best CNAPPs integrate seamlessly into your existing CI/CD pipelines, code repositories, and developer tools. This means security checks happen automatically as part of development, catching issues early without slowing down releases.
- Consolidation and Cost Efficiency: Instead of paying for 4-5 different products and trying to consolidate reports, organizations can invest in one platform, reducing tool sprawl and total cost.
- Continuous Compliance: CNAPPs provide out-of-the-box compliance policies (CIS benchmarks, GDPR, SOC 2) and audit reports to ensure you’re always in compliance even as cloud resources churn.
How to Choose the Right CNAPP
Not all platforms with the CNAPP label are equal. When evaluating which tool is right for you, keep these key criteria in mind:
- Integration: Does the platform integrate seamlessly with your existing DevSecOps and security tools (CI/CD pipelines, SIEMs, Slack, Jira)?
- Coverage: Does the platform cover all your cloud environments (AWS, Azure, GCP, hybrid) and workload types (VMs, containers, Kubernetes, serverless)?
- Deployment: Is it agentless, requiring no installation on workloads, or does it require agents for comprehensive coverage? Prioritize agentless solutions for faster deployment and reduced operational overhead.
- Risk Prioritization: How does it filter alerts? Does it perform context-aware analysis? Platforms like Aikido Security use AI to filter out over 90% of false positives
- Automation: Does it offer automated remediation features such as guided steps, one-click fixes , automated PRs, inline suggestions?
- Compliance Support: Does it provide out-of-the-box support for industry compliance frameworks (GDPR, HIPAA, PCI-DSS, ISO 27001 and SOC 2)? Does it generate audit ready reports?
- Ease of Use: Does it offer an intuitive interface for both development and security teams?
- Scalability: Does it support multicloud environments? How many cloud resources or microservices can it manage without dropping performance?
- Predictable Pricing: Are its plans transparent and easy to estimate? Can you predict how much it will cost your team in 6 months?
Top 9 CNAPP Tools
1. Aikido Security
Aikido Security is an AI-driven, cloud-native application protection platform (CNAPP) designed to secure every aspect of the cloud application lifecycle, from code and dependencies to containers, multi-cloud infrastructure, and runtime.
Aikido Security’s Attack Path Analysis gives teams end-to-end visibility of all connected and unconnected assets in a single, clean UI. It performs AI-assisted reachability analysis on publicly reachable resources, dynamically adjusting risk scores for SAST and SCA findings, so teams can focus on high-risk exposures.
In addition to its reachability analysis, Aikido Security protects the applications infrastructure by detecting toxic combinations as soon as infrastructure is connected, helping teams quickly identify cascading security risks. Findings can then be turned into superset rules that can be deployed across all teams, ensuring consistent security policies across projects and environments.
Teams get everything they need to resolve issues:
- AI-driven risk scoring and reachability-adjusted analysis highlights the most critical vulnerabilities first.
- Correlated findings so teams can focus on real threats.
- Visibility into what is or isn’t connected across code, containers, and multi-cloud infrastructure.
- Superset rules to apply consistent security standards across all projects and accounts.
- CNAPP agent monitoring across clouds and Aikido accounts for full observability.
Aikido Security’s combination of end-to-end scanning, centralized attack path analysis, reachability-aware risk prioritization, superset policy enforcement, and cross-cloud visibility ensures teams can secure their cloud-native applications and infrastructure efficiently.
Key features:
- Infrastructure Security: Aikido Security reduces the risk of incidents by 50% by securing the underlying cloud infrastructure of applications, eliminating the need for separate cloudSec and AppSec tools.
- Multi-Cloud Support: Provides a unified view and policy enforcement across AWS, Azure, GCP, and Kubernetes clusters.
- Superset Rules Deployment: Turn findings into deployable rules across all teams for consistent security policies.
- Modular Scanners: Provides AI-assisted scanners for SAST, SCA, secrets, IaC, containers, cloud configs, and much more.
- AI-powered Fixes: Provides automated pull requests for fixes, and one-click fixes for multiple findings.
- Toxic Combo Detection: Detects dangerous combinations in infrastructure as soon as it’s connected.
- Runtime Security (RASP): Aikido Security provides an in-app web firewall to block attacks in real time.
- Agentless Setup: Connects to assets using read-only APIs.
- End-to-End Attack Path Analysis: It uses AI to find links between vulnerabilities and highlights the most likely attack routes.
- AI Autotriage: Uses contextual filtering and AI triaging to suppress up to.
- Compliance Mapping: Supports industry compliance and security frameworks out-of-the-box such as SOC 2, ISO 27001, PCI DSS, GDPR, and much more.
- Developer-Friendly UX: Provides AI suggestions, autofixes, and clear guidance in IDEs and pull requests to help developers fix issues quickly.
Pros:
- Free forever tier for small teams
- Supports multi-cloud monitoring
- AI-powered filtering
- IaC scanning (for Terraform, CloudFormation, ARM templates)
- Cross-platform security policies
- Broad language support
- Comprehensive Software Bill of Materials (SBOM)
- Automated AI-powered fixes
- Developer-friendly user experience (UX)
- End-to-end attack path analysis
Pricing:
Aikido Security’s plans start from $300/month for 10 users, and provides dedicated offerings for startups (at a 30% discount) and enterprises
- Developer (Free Forever): For teams of up to 2 users. Supports 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Includes support for 10 repos, 25 container images, 5 domains and 3 cloud accounts.
- Pro: Ideal for mid-sized teams. Supports 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Best For:
Startups and enterprises seeking a comprehensive CNAPP solution that covers both cloud security and application security while eliminating tool sprawl.
Gartner Rating: 4.9/5.0
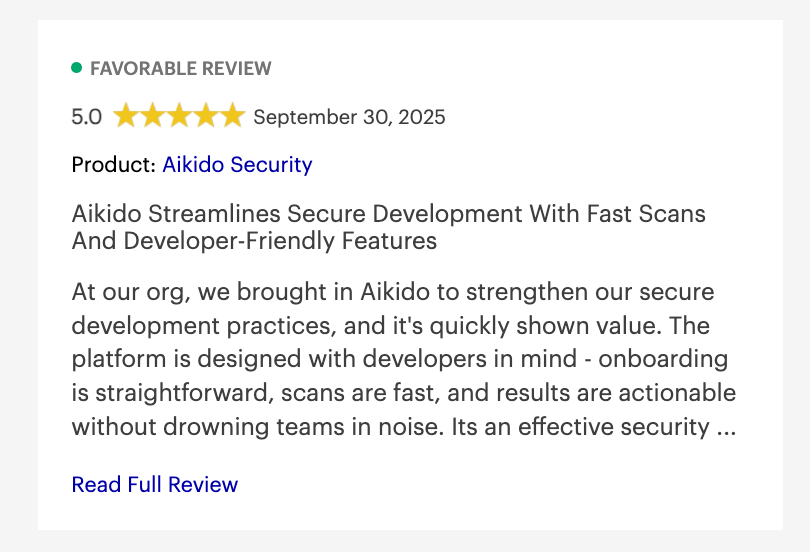
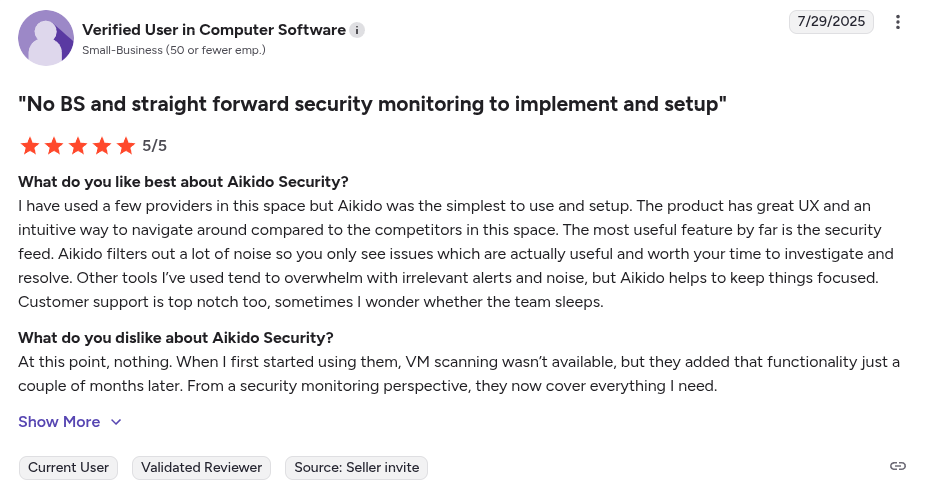
Aikido Security Review:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra, Getapp and SourceForge
2. Aqua Security
Aqua Security is an enterprise CNAPP platform with a strong focus on container and Kubernetes workloads. It is primarily known for its image inspection and Kubernetes cluster security capabilities.
Key Features:
- Vulnerability Management: Aqua Security scans images in registries, CI pipelines, and on hosts, flagging CVEs in OS packages and application libraries.
- Kubernetes and Runtime Security: It can enforce pod security policies, check images at admission and detect anomalies at runtime.
Pros:
- Strong container and Kubernetes focus
- Supports common CI/CD platforms
- Compliance automation
Cons:
- Primarily enterprise focused
- Steep learning curve
- High alert volume
- Users have reported its documentation as “outdated”
- Less developer-friendly
- Setup can be complex compared to agentless tools like Aikido Security
- Users have reported limitations for non-Linux/Windows container scenarios
Pricing:
Custom Pricing
Best For:
Enterprises running containerized workloads at scale and require strict compliance requirements enforcement.
Gartner Rating: 4.1/5.0
Aqua Security Review:


3. CrowdStrike Falcon Cloud Security
CrowdStrike Falcon Cloud Security is an AI-powered CNAPP platform that provides comprehensive protection across the entire cloud-native stack. It leverages both agent-based and agentless approaches.
Key Features:
- Attack Surface Management: It can track cloud assets and perform attack path analysis to show how a threat could move through cloud environments.
- Integration with CrowdStrike Falcon platform : CrowdStrike provides a single console for endpoint and cloud alerts, and it integrates with their broader XDR ecosystem.
Pros:
- Threat intelligence
- Built-in compliance support
- Strong runtime protection
Cons:
- Enterprise focused
- False positives
- Steep learning curve
- It requires its agents to be installed for comprehensive protection
- Limited on-premise options
- Initial configuration is complex
- Users have reported issues when managing container, serverless, and legacy workloads
- Users have reported customer support delays
Pricing:
Custom pricing
Best For:
Enterprises with dedicated security teams already using the CrowdStrike ecosystem
Gartner Rating: 4.7/5.0
CrowdStrike Falcon Cloud Security Review:

4. Lacework (Now Lacework FortiCNAPP)
Lacework (Lacework FortiCNAPP) is a data-driven CNAPP platform known for its patented “Polygraph” technology. Its Polygraph Data Platform maps behaviors across your cloud to surface threats and misconfigurations.
Key Features:
- Behavioral Anomaly Detection: Lacework’s Polygraph builds a model of your cloud activities and interactions, and monitors for any deviations.
- Cloud Security Posture Management (CSPM): It continuously evaluates cloud resource configurations against best practices and compliance standards.
- Vulnerability Scanning: Lacework scans container images and host OS packages for known CVEs.
Pros:
- Behaviour-based anomaly detection
- Strong customer support
- Integrates seamlessly with Fortinet ecosystem
Cons:
- Heavily enterprise focused
- Steep learning curve
- Initial configuration is complex
- Users have reported issues integrating alerts with third‑party systems (SIEM, Slack, Datadog)
- User have reported issues generating compliance reports
- Users have reported a slowdown in feature developments
Pricing:
Custom pricing
Best For:
Organizations running multi-cloud or Kubernetes environments, seeking an anomaly detection tool beyond traditional rule-based solutions.
Gartner Rating: 4.4/5.0
Lacework (Now Lacework FortiCNAPP) Reviews:
5. Orca Security

Orca Security is an agentless cloud-native application protection platform (CNAPP) solution. It is primarily known for its patented “SideScanning” approach to inspecting workload files by collecting metadata from block storages to find vulnerabilities, misconfigurations, and exposed secrets.
Key Features:
- Compliance and Reporting: Orca supports a range of compliance frameworks and continuously assesses your environment against them.
- Agentless Scanning: Orca scans VM disks, containers, and cloud storage to detect OS vulnerabilities, exposed credentials and malware.
- Sensitive Data Discovery: Orca can detect sensitive data such as Personal Identifiable Information (email addresses, names), secrets, keys across cloud assets and rank them by exploitability.
Pros:
- Agentless deployment
- No log sharing required
Cons:
- Primarily enterprise focused
- High alert volume
- Limited real-time runtime protection
- Users have reported its User Interfaces (UI) as “clunky”
- Limited customization options for specific Key Performance Indexes (KPIs)
- Pricing can become expensive when scaling
- It doesn’t scan application source code
Pricing:
Custom pricing
Best For:
Enterprise teams seeking fast, agentless, multi-cloud visibility without deployment overhead.
Gartner Rating: 4.6/5.0
Orca Security Review:
6. Prisma Cloud (Palo Alto Networks)
Prisma Cloud is Palo Alto Networks’ machine learning powered CNAPP offering. It is primarily used by enterprises to provide end-to-end coverage...
Key Features:
- Compliance and Governance: Prisma Cloud provides out-of-the-box support for more than 10 compliance standards.
- Web Application and API Protection: It offers Web App and API Protection (WAAP) functionality to protect APIs and cloud functions from abuse.
- Threat Intelligence: It uses Palo Alto Networks' threat intelligence capabilities, for proactive threat detection and prevention.
Pros:
- AI-powered risk prioritization
- Robus threat protection
- Multi-cloud support
Cons:
- Primarily enterprise focused
- Steep learning curve
- Initial configuration is complex and time-consuming
- Users have reported its User Interface(UI) and console as “outdated”
- Deployment processes in large environments can become complex and length
- Users have reported gaps in API documentation
Pricing:
Custom Pricing
Best For:
Large enterprises with dedicated security teams seeking a CNAPP solution that integrates deeply with their existing Palo Alto stack.
Gartner Rating: 4.5/5.0
Prisma Cloud (Palo Alto Networks) Reviews:
7. Sysdig Secure
Sysdig Secure is an enterprise CNAPP built on a "runtime-first" philosophy. It originated from the open-source Sysdig and Falco projects and is primarily used by organizations running kubernetes/container-heavy workloads.
Key Features:
- Image Scanning with Policy Enforcement: Sysdig Secure scans images for vulns and can enforce policies during build or deploy.
- Falco-Powered Runtime Security: Sysdig Secure uses Falco to detect a wide array of malicious or anomalous activities at runtime.
Pros:
- Deep runtime visibility
- Support for Kubernetes/container workloads
Cons:
- Steep learning curve
- Its CSPM is not as robust as other CNAPP platforms
- Manual remediation
- Users have reported lags in documentation
- Users have reported issues with navigating multiple dashboards for full context
Pricing:
Custom pricing
Best For:
Enterprises with a heavy container/Kubernetes focus that want both CI/CD scanning and runtime protection in one solution.
Gartner Rating: 4.8/5.0
Sysdig Secure Reviews:

8. Wiz

Wiz is a Cloud Native Application Protection Platform (CNAPP) with integrated Cloud Security Posture Management (CSPM) capabilities. It is primarily known for its agentless, graph-based approach to securing cloud environments.
Key Features:
- Cloud Security Posture Management (CSPM): Wiz continuously scans cloud assets for vulnerabilities
- Security Graph: Uses its patented context mapping graph to visualize the relationships between identities, workloads, data, and configurations
Pros:
- Security graph
- Cloud discovery and inventory
Cons:
- Primarily enterprise focused
- High alert volume
- It is more security team centric than developer centric
- Limited Real-Time Response
- Limited SAST capabilities
- Pricing can become expensive when scaling
- May require complementary tools for full AppSec coverage
- Users have reported issues integrating Wiz with complex hybrid environments or legacy systems
Pricing:
Custom pricing
Best For:
Enterprises requiring robust compliance automation for regulated industries, with continuous monitoring.
Gartner Rating: 4.8/5.0
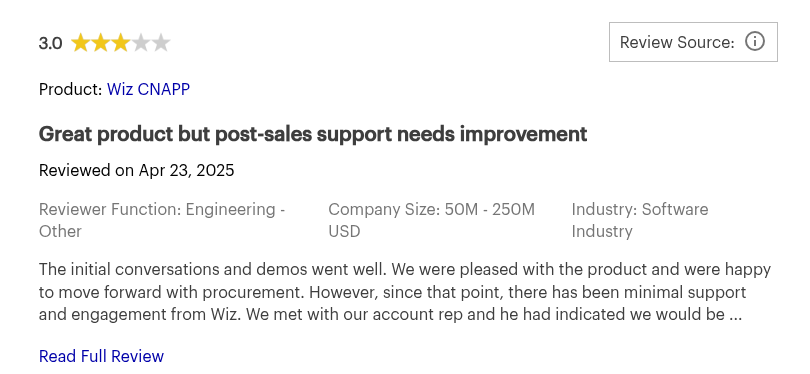
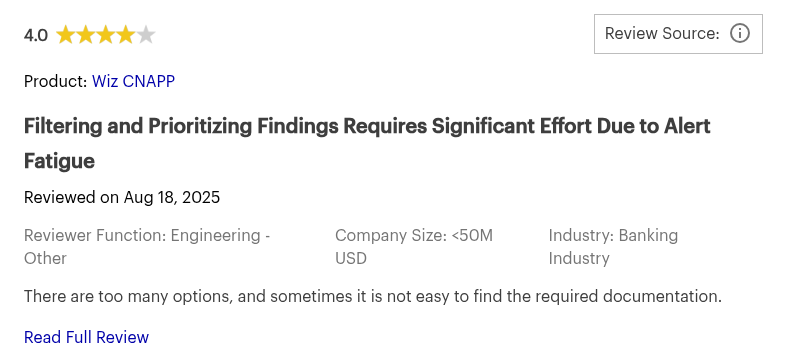
Wiz Review:
9. Singularity Cloud Security
Singularity Cloud Security is SentinelOne's AI-powered Cloud Native Application Protection Platform (CNAPP). It is designed to provide end-to-end security and compliance coverage across the entire cloud-native application lifecycle.
Key Features:
- AI-Powered Detection: It uses autonomous AI agents to detect and prevent threats like ransomware and zero-days in real-time.
- Secrets Scanning: Automatically identifies hardcoded credentials and sensitive data across repositories and cloud assets to prevent leakage.
- Cross-Stack Correlation: Performs context-based correlation on alerts across cloud, workloads and identity
Pros:
- Strong runtime protection
- Good customer support
Cons:
- Steep Learning Curve
- False Positives
- Users have reported documentation lags for feature updates
- Users have reported its user interface (UI) as “cluttered”
- It’s is more resource intensive when compared to agentless solution like Aikido Security
Pricing:
Singulatrity’s full CNAPP is available on its commercial and enterprise plans only
- Singularity Core: $69.99 per endpoint/year
- Singularity Control: $79.99 per endpoint/year
- Singularity Complete: $179.99 per endpoint/year
- Singularity Commercial : $229.99 per endpoint/year
- Singularity Enterprise: Custom Pricing
Best For:
Enterprises already leveraging SentinelOne's endpoint protection seeking to extend their security coverage to cloud workloads
Gartner Rating: 4.7/5.0
Singularity Cloud Security Reviews:

Best 2 CNAPP Tools for Developers
Key Criteria For Choosing a CNAPP Tool For Developers:
- Seamless workflow integration
- Fast and automatic scans
- Low noise and actionable alerts
- Developer-friendly UX
- Cost-effective (free tiers, transparent pricing)
Here are the Top 2 CNAPP Tools Tailored For Developers:
- Aikido Security: IDE and CI integration, Developer-friendly interface, AI-driven remediation, one-click fixed for vulnerabilities, agentless deployment.
- Wiz: Context-aware risk mapping, cloud graph analysis
Best 5 CNAPP Platforms for Enterprise
Key Criteria For Choosing a CNAPP Platform For Enterprises:
- Scalability
- Governance
- Strong integration with enterprise workflows (SSO, SIEM, ITSM)
- Centralized management
- Compliance and audit support
- Accuracy
- Vendor support
Here are the Top 5 CNAPP Platforms Tailored for Enterprises:
- Aikido Security: End-to-end coverage, SSO and RBAC support, optional on-prem deployment, Out-of-the box compliance controls, AI-driven noise reduction.
- Palo Alto Prisma Cloud: multi-cloud support, SOC workflow support,
- Aqua Security: container lifecycle protection (runtime defense, multi-cloud compliance
- Orca Security: Agentless deployment, multi-cloud visibility, , context-based risk prioritization
- Sysdig Secure: Kubernetes and container security, runtime threat monitoring
Best 2 CNAPP Tools for Startups & SMBs
Key Criteria For Choosing a CNAPP Tool For Startups and SMBs:
- Seamless workflow integration
- Fast and automatic scans
- Low noise and actionable alerts
- Developer-friendly UX
- Cost-effective / free tiers preferred
Here are the Top 2 CNAPP Tools Tailored For Startups and SMBs:
- Aikido Security: Agentless deployment, free forever tier, broad coverage (CWP, SCA, SAST, DAST, container/IaC scanning), AI-powered risk prioritization
- Orca Security: Agentless architecture, patented “SideScanning” technology,
Best 4 CNAPP Tools for Multi-Cloud Environments
Key Criteria For Choosing a CNAPP Tool For Multi-Cloud Environments:
- Unified visibility across all clouds
- Cloud-agnostic policy enforcement
- Multi-cloud risk identification
- Minimal configuration
- Scalability
Here are the Top 4 CNAPP Tools Tailored For Multi-Cloud Environments:
- Aikido Security: Cloud-neutral scanning across AWS, Azure, GCP, and Kubernetes, unified risk dashboard, Agentless deployment, AI-powered filtering
- Orca Security: context-aware cross-cloud alerts, combined risk dashboard
- Lacework: Behavioral monitoring across clouds, anomaly detection
- Prisma Cloud: Multi-cloud policy enforcement; dashboards per cloud for ownership
Best 4 CNAPP Tools for AWS Cloud Security
Key Criteria For Choosing a CNAPP Tool For AWS Cloud Security:
- Deep coverage of AWS services
- Integration with AWS-native security features (Security Hub, GuardDuty, Inspector)
- Detection of AWS-specific misconfigurations
- Rapid deployment and actionable alerts
Here are the Top 4 CNAPP Tools Tailored For AWS Cloud Security:
- Aikido Security: Dev-first AWS integration, permission remediation suggestions, ECR vulnerability checks, and security group exposure detection
- Prisma Cloud: Comprehensive AWS coverage;
- Orca Security: context-aware cross-service alerts; snapshot analysis and permission mapping
- Lacework: Behavior-based threat detection for CloudTrailand CloudWatch.
Best 3 CNAPP Tools for Azure Cloud Security
Key Criteria For Choosing a CNAPP Tool For Azure Cloud Security:
- Integration with Azure AD and Azure native services
- Detection of Azure-specific misconfigurations (ARM templates, Terraform for Azure)
- Early security feedback
- Ease of use for developers without deep Azure security expertise
Here are the Top 3 CNAPP Tools Tailored For Azure Cloud Security:
- Aikido Security: Developer friendly Azure integration ,CSPM coverage (App Services, Storage Accounts, AKS), Azure AD support, CI/CD support for Azure Repos/Pipelines
- Prisma Cloud: integrates with Azure Policy, Defender, Sentinel, and Azure AD; single view across subscriptions;
- Orca Security: Agentless posture management,multi-subscription Azure coverage
Conclusion
Cloud security is no longer optional, it’s essential for anyone running workloads in the cloud. The right CNAPP tools help teams bridge the gap between development, operations, and security by providing a single source of truth for security risks across code, containers, cloud infrastructure, and runtime.
By combining multiple security functions into a modular, cloud-native workflow, Aikido Security gives startups and enterprises end-to-end visibility of their cloud applications. It leverages AI-driven attack path analysis, reachability-aware risk prioritization, and superset policy enforcement to detect and remediate threats in real time, enabling teams to secure cloud workloads faster and more efficiently.
Want full visibility across your cloud-native applications and infrastructure? Start your free trial or book a demo with Aikido Security today.
FAQ
What are the main components of a CNAPP?
A Cloud Native Application Protection Platform (CNAPP) combines multiple cloud security functions into one solution. Key components include Cloud Security Posture Management (CSPM) to detect misconfigurations and ensure compliance, Cloud Workload Protection (CWP) for VMs, containers, and serverless workloads, IAM monitoring for risky permissions, and Software Composition Analysis (SCA) for vulnerable dependencies. Aikido Security covers all of these components, providing unified visibility and protection across code, cloud, and container environments.
How does CNAPP differ from traditional cloud security solutions?
Unlike traditional tools that focus on only one area such as, vulnerability scanning or workload protection, CNAPP platforms provide end-to-end security across cloud assets, workloads, and applications. Platforms like Aikido Security integrate multiple security functions into a single workflow, giving developers and security teams full visibility without needing separate tools or dashboards.
How can CNAPP tools improve cloud security for organizations?
CNAPP tools enhance cloud security by offering continuous monitoring, automated risk detection, and actionable insights. They help identify misconfigurations, vulnerable workloads, and insecure APIs early in the development lifecycle. Tools like Aikido Security implements this by integrating into CI/CD pipelines, providing AI-prioritized alerts, and even providing fixes so teams can remediate issues faster.
Why are CNAPP tools gaining popularity in cloud security management?
As organizations adopt multi-cloud environments and DevOps practices, managing security across disparate systems becomes complex. CNAPP tools are popular because they consolidate multiple security capabilities, reduce operational overhead, and provide a single source of truth. Platforms like Aikido Security achieves this by delivering developer-friendly, end-to-end coverage across code, containers, and cloud resources, making it easy for teams to secure environments consistently and efficiently.
You Might Also Like:

Secure your software now






