Our malware detection pipelines recently lit up on a small cluster of packages on npm that looked... familiar.
Packages like json-bigint-extend, jsonfx, and jsonfb were mimicking the popular json-bigint library: same functionality, an identical README file, and even an author name uncomfortably close to the original maintainer.
Most of the time, this pattern indicates common supply-chain attacks, such as typosquatting and dependency confusion, designed to compromise systems and exfiltrate secrets. But this one felt different almost immediately.
It was not trying to hit everyone. It was trying to hit something.
The hijack
At first glance, json-bigint-extend behaves exactly like the legitimate json-bigint library: it exports the familiar parse/stringify functions used to support large integers in JSON. In fact, most developers and organizations wouldn’t notice anything unusual. This payload is specifically engineered to stay quiet and only trigger when it detects it is running inside a specific target environment, by checking the value of a specific environment variable called SERVICE_NAME.
Once it detects it is in the right environment, it installs two backdoors:
First, it installs a targeted Express middleware, wired specifically into a payment route (/v1/pay/purchase-goods). This middleware is designed to dynamically execute additional code fetched from an endpoint. Upon further inspection of the fetched code, it seems to be a complex cashflow-rewriting system used to manipulate a gambling game.
const routeInjectionRules = {
'/v1/pay/purchase-goods': {
identify: function (handlers, fn, index) {
...
},
position: 'after',
extraMiddlewares: [function (req, res, next) {
// Translation: [Plugin] Mount risk middleware as post-payment success logic.
log('[插件] 支付成功后的后置逻辑挂载risk');
riskCode(req, res, next); // Executes dynamically fetched code
}]
}
};
Secondly, a prototype-level middleware that quietly monkey-patches Express.js, adding global middleware to every POST route. This middleware listens for a secret x-operation header and unlocks four types of commands to the operator:
- RunSQL: execute arbitrary SQL against the production database.
- RunFileList: list server-side files and directories.
- RunFileContent: download the contents of a chosen file.
- CompressDownload: download a directory as a zip file.
The operator dashboard
Inside the package, there is also an embedded HTML page for a “Directory compression download service” (Chinese title: 目录压缩下载服务).
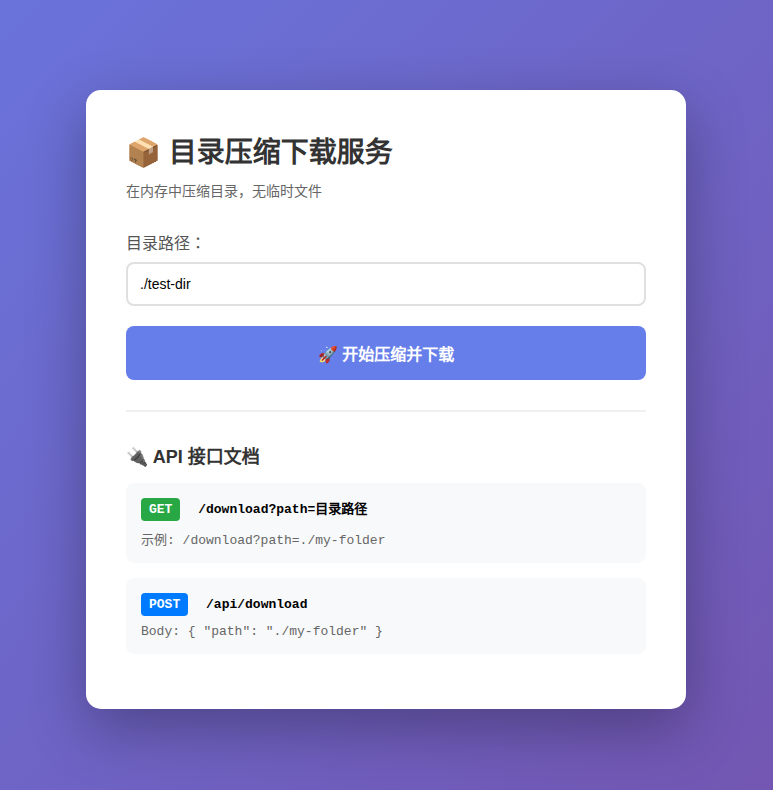
While this page was never hooked up anywhere in the backdoor code we observed, it appears to be an operator-facing UI for browsing and exfiltrating directories as zip files.
Manipulating gambling outcomes
The scary part: that riskCode(...) function called in the middleware is remote-controlled and updated every 30 seconds.
While the payload is not actively invoked (yet), we observed logic capable of retroactively adjusting a user's recent game history so their balance moves by a chosen amount, while rebuilding the full balance chain so the game logs still look internally consistent.
It's a sophisticated balance and history rewriter that:
- Reads recent cashflow rows for a user.
- Selects a window of game rounds.
- Adjusts bet/payout values to hit a target amount in a user's wallet.
- Rebuilds the full game logs so it remains internally consistent in the database.
That means the goal is not just fraud. It is fraud that survives internal consistency checks, fabricating wins and losses while keeping accounting consistent.
Some of the surrounding references point to a gambling app called Bappa Rummy, widely advertised online through referral programs and alternative app stores, but no longer available on the official Google Play store.
Detection and prevention
While we don't know who is behind the backdoor, the scary part is what it does once it lands in the right environment. This is not “just” a typical dependency implant that exfiltrates source code, secrets, or customer data.
Instead, it hooks directly into business logic, executes remote-controlled code on real traffic, and can rewrite database-backed financial history. If your monitoring assumes database logs are trustworthy, this kind of manipulation can stay invisible for a long time.
If you already use Aikido, this package would be flagged in your feed as a 100/100 critical finding.
Not on Aikido yet? Create a free account and link your repositories. The free plan includes our malware detection coverage (no credit card required).
Finally, having a tool that can stop malware in real time as it appears can prevent a serious infection. This is the idea behind Aikido Safe Chain, a free and open-source tool that wraps around npm, npx, yarn, pnpm, and pnpx and uses both AI and human malware researchers to detect and block the latest supply chain risks before they enter your environment.
Indicators of compromise
Packages and authors:
- jsonfb (by sidoraress)
- jsonfx (by sidoraress)
- json-bigint-extend (by sidoraress & infinitynodestudio)
The backdoor communicates with a remote host for both payload updates and logging.
Observed endpoints:
https://payment[.]y1pay[.]vip/v1/risk/get-risk-codehttps://payment[.]y1pay[.]vip/v1/risk/loghttps://payment[.]snip-site[.]cc
Other IOCs and huntable behaviors:
- Requests containing x-operation header with one of the four operation tokens:
- RunSQL (token: cfh2DNITa84qpYQ0tdCz)
- RunFileList (token: m3QiEkg8Y1r9LFTI5e4f)
- RunFileContent (token: Y3SrZjVqWOvKsBdpTCh7)
- CompressDownload (token: SJQf31UJkZ1f88q9m361)
- Runtime modifications to
express.Route.prototype.post



