Mend.io (formerly WhiteSource) is a popular application security platform used for managing open-source vulnerabilities and license compliance. Teams adopt Mend to scan their code dependencies (SCA) and custom code (SAST) for security issues.
However, many developers and security leads are now seeking better alternatives due to various pain points. Common complaints include its “clunky UI”, high false-positive rates, slow scans, limited coverage beyond SCA, and steep pricing.
Here’s what Mend.io users have to say:
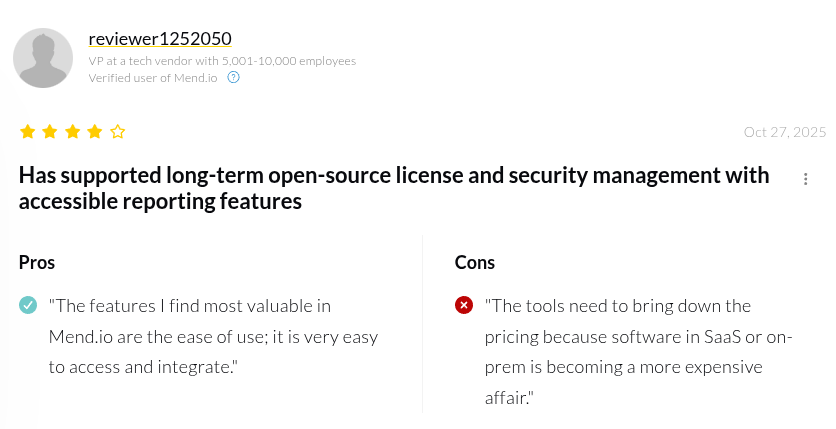
Users also shared:
- “We wanted to have certain reports based on our kind of scenario, but the tool did not allow us to create custom reports.” – PeerSpot Reviewer
- “It feels like a really old application… would be nice to have a modern UI that works well and is fast.” – PeerSpot Reviewer
- “Documentation isn't the best when it comes to showing how to integrate…Some of the documentation seems a bit out of date…” – Gartner Reviewer
Considering these limitations, it becomes important to understand what other tools can fill the gaps Mend.io leaves behind.
In this article, we’ll explore the best Mend.io alternatives in 2026, why teams are moving away from Mend.io, and what to consider when choosing a replacement.
TL;DR
Aikido Security is the top SCA pick for teams migrating away from Mend.io. It focuses on identifying exploitable dependencies by combining scanning beyond standard CVE databases with dependency reachability analysis and automatic noise reduction.
While Mend.io offers a mature SCA grouping and reporting, users often struggle with thousands of low-priority alerts, lack of support for GitLab Cloud, and heavy reliance on CVE-based data, which make it harder to identify silently patched or non-CVE vulnerabilities. In GitLab environments, Mend’s SAST capabilities are also limited, with only basic grouping, reporting and filtering.
Aikido Security addresses these gaps by prioritizing exploitable vulnerabilities and license risks using AI, offering one-click remediation, malware detection, and automated SBOM generation and compliance mapping.
As a result, more than five organizations have already replaced Mend.io with Aikido, to streamline their SCA workflows.
In addition to dependency scanning, Aikido Security comes with best-in-class modules such as IaC, secrets detection, runtime protection, DAST, AI penetration testing, and much more as needed, avoiding tool bloat while gaining deeper visibility.
Comparison Between Mend.io and Aikido Security
You can skip ahead to any of the alternatives below:
Comparing open-source security platforms? Check out our article on the Top 10 Software Composition Analysis (SCA) tools in 2026 is the place to start.
What is Mend.io?
Mend.io is an application security platform that helps organizations identify vulnerabilities and license risks in open-source and proprietary code.
Its key features include:
- Software Composition Analysis (SCA): Scans open-source dependencies to detect known vulnerabilities (CVEs) and manage license compliance risks.
- Static Application Security Testing (SAST): Analyzes proprietary source code to identify security flaws early in the development lifecycle.
- Vulnerability and License Management: Provides visibility into third-party components, helping teams enforce policies and reduce exposure to risky or non-compliant libraries.
- Integration: Integrates with CI/CD pipelines so security scans run automatically during builds and pull requests.
Why Look for Alternatives?
Despite its capabilities, Mend.io users cite several reasons for seeking an alternative dependency analysis solution:
- High False Positives: Users have reported spending additional time triaging “vulnerabilities” that aren’t actually exploitable, slowing down development. Its lack of reachability analysis or proof-of-concept links can make it hard to tell real issues from noise.
- Usability and UI Frustrations: Mend’s interface and overall developer experience have been described as “unintuitive” or “outdated”.
- Limited Coverage: It is primarily focused on SCA. Its newer SAST tool is still evolving, and offers basic SAST findings. It does not offer comprehensive coverage across other AppSec areas. .
- GitLab Integration: It offers support for only self-managed GitLab instances, limiting cloud-first teams.
- High Cost and Licensing: Mend.io’s pricing can be on the higher side, especially when scaling. .
- Vulnerability Grouping and Filtering: Grouping and filtering are stronger within Mend’s own UI for SCA, but weaker across other scan types. Advanced grouping and filtering are also lacking inside the GitLab UI.
- Lack of Developer-Friendly Features: Mend has made some strides ( with Renovate), but users still report it’s not as developer-friendly (IDE feedback, automated fix pull requests) as they’d like.
- Vendor Support: Users have raised concerns around responsiveness and support quality, particularly during onboarding and complex integrations.
Key Criteria for Choosing an Alternative
When evaluating Mend.io alternatives, here are a few criteria you should keep in mind:
- Developer-Friendliness: Developers will be the ones addressing the security issues. Does it integrate seamlessly into their developer workflows? Does it have a low learning curve? Look for options with AI-autofix, IDE plugins, inline PR comments.
- Breadth of Coverage: Consider the scope of security risks you need to cover. Does it only offer SCA or code-to-cloud coverage as well?.
- Accuracy: Security scanners are notorious for false positives. Aim for a solution with intelligent prioritization that filters out trivial issues and auto-triage.
- Automation: Does it offer automated remediation features such as one-click fixes or automated pull requests? Additionally,
- Integration: Does it integrate with your existing version control systems, build tools, container registries, and ecosystem?
- Cost-Effectiveness: Can you predict how much it will cost your team in 6 months? Consider vendors with transparent pricing and flexible plans.
Top 6 Alternatives to Mend.io
1. Aikido Security
Aikido Security provides full-stack visibility into open-source dependencies, license compliance, exploitable vulnerabilities, and malicious packages directly within development workflows. It also offers an Autofix tool teams can use to fix vulnerabilities in 3rd party dependencies.
Beyond standard databases, Aikido scans the NVD and GitHub Advisory Database, and goes further by extending coverage through Aikido Intel, which detects silently patched vulnerabilities without assigned CVEs.
Aikido Security applies dependency reachability analysis to determine whether identified vulnerable dependencies are actually being used and are reachable in your application. It also detects malicious packages that may not have been reflected in public vulnerability databases and provides SBOM generation ensuring teams know exactly what is in their application, along with actionable guidance.
Findings are instantly deduplicated to reduce noise, and dependency risks are mapped to compliance frameworks, ensuring that security, development, and compliance teams have the information they need to manage open-source risk effectively.
Aikido also identifies breaking changes introduced by dependency updates, helping teams avoid unexpected runtime or build failures. As a result of all it’s strong SCA capabilities, more than five organizations have already replaced Mend.io with Aikido Security.
Teams can start with Aikido’s category-leadingSCA module and expand coverage to additional modules such as SAST, IaC scanning, DAST, secrets detection, malware detection, container security and much more as their needs grow. The added context makes organizations’ security posture even stronger.
Key Features:
- Full-Stack Coverage: Along with SCA, Aikido Security offers end-to-end coverage across code, runtime, pentesting, and cloud.
- Comprehensive Dependency Scanning: Scans direct and transitive open-source dependencies across supported package managers.
- Reachability Analysis: It identifies whether vulnerable code paths are reachable in real attacks, surfacing only vulnerabilities that pose real-world risks.
- Context-Aware Risk Prioritization: Combines vulnerability severity, reachability analysis, and deployment context to rank risks.
- CI/CD Integration: Integrates seamlessly with GitHub, GitLab, Bitbucket, Azure DevOps, CircleCI, and much more.
- Agentless Setup: Uses read-only APIs to connect with GitHub, GitLab, or Bitbucket. No installation agents required.
- Software Bill of Materials (SBOM) Generation: Generates and ingests SPDX and CycloneDX SBOMs.
- License Compliance: Identifies open-source licenses, policy violations, and generates audit-ready license compliance reports.
- Robust Compliance Mapping: Supports major compliance and security frameworks like SOC 2, ISO 27001, PCI DSS, GDPR, and much more.
- Policy-Based Automation: Aikido Security allows teams to enforce custom security and license policies automatically during builds and deployments.
- Developer-friendly UX: Provides Instant AI powered feedback in PRs and IDEs, including dependency upgrade paths and prioritized remediation steps.
- Scalable: Aikido Security is optimized for large codebases, ensuring performances does not drop as your codebase grows
Pros:
- Predictable pricing
- Broad language and package manager support
- Dependency reachability analysis
- Malware detection
- Optimized for large codebases
- AI-powered risk prioritization
- Automated license detection
- Comprehensive Software Bill of Materials (SBOM) generation and ingestion
- Developer-friendly UX
- Context-aware remediation guidance
- Code-to-cloud coverage
Pricing:
Aikido Security’s plans start at $300/month for 10 users.
- Developer (Free Forever): Ideal for teams of up to 2 users. Includes 10 repos, 2 container images, 1 domain, and 1 cloud account.
- Basic: Supports 10 repos, 25 container images, 5 domains, and 3 cloud accounts.
- Pro: Designed for mid-sized teams. Includes 250 repos, 50 container images, 15 domains, and 20 cloud accounts.
- Advanced: Includes 500 repos, 100 container images, 20 domains, 20 cloud accounts, and 10 VMs.
Plans are also available for startups (with a 30% discount) and enterprises.
Why Choose It:
Aikido Security is ideal for startup and enterprise teams seeking an affordable developer friendly application security (AppSec) solution that not only addresses their SCA needs but the entire AppSec landscape.
Gartner Rating: 4.9/5.0
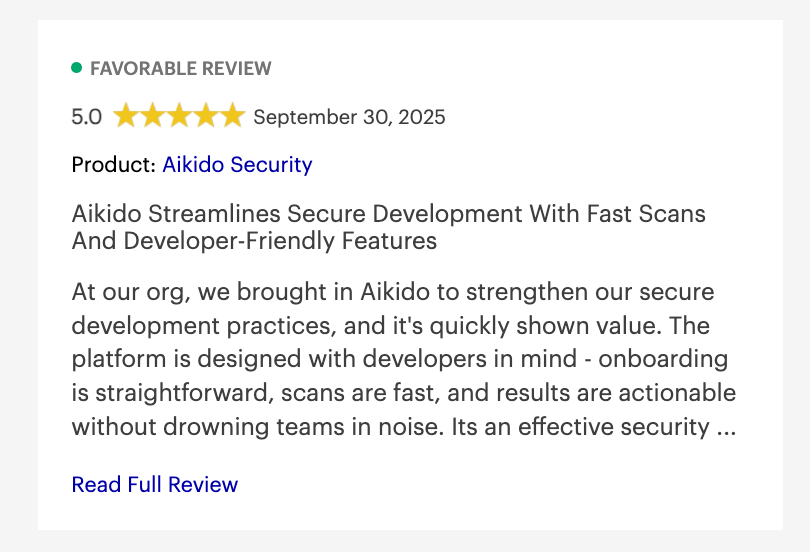
Aikido Security Reviews:
Beyond Gartner, Aikido Security also has a rating of 4.7/5 on Capterra, Getapp and SourceForge.
2. Black Duck
Black Duck by Synopsys specializes in open source vulnerability management and license compliance. It scans your projects to produce a detailed Bill of Materials (SBOM) of all open-source components and checks each component against a knowledge base of known vulnerabilities and license data.
Key Features:
- Comprehensive Open Source Database:It can detect obscure libraries and flags if they have known CVEs and continuously updates its vulnerability feed for new issues.
- License Compliance: It can identify open source licenses in your codebase and enforce policies.
- Integrations : Black Duck integrates with common development tools (build systems, repositories, CI servers) to automatically scan codebases and containers...
Pros:
- Broad language support
- Comprehensive vulnerability knowledge base
Cons:
- Primarily enterprise focused
- It is more security and compliance team-centric, than developer-centric
- High alert volume
- Steep learning curve
- False positives
- Scans on large codebases are slow
- Setup and initial configuration can be complex and time-consuming
Pricing:
Custom pricing
Why Choose It:
Black Duck is ideal for large enterprise compliance and security teams seeking an open-source risk management solution for their compliance needs.
Gartner Rating: 4.5/5.0
Black Duck Reviews:
3. FOSSA
FOSSA is an open source management platform, offering a modern and developer-centric approach to SCA and license compliance. It provides continuous scanning of your code repositories for both vulnerabilities in open-source dependencies and any license compliance issues. Key Features:
- Automated License Compliance: FOSSA automatically detects open-source licenses in your code and flags any that violate your policies.
- Vulnerability Scanning in CI/CD: It continuously scans your dependencies against vulnerability databases and integrates with common CI pipelines to catch issues before they hit production.
Pros:
- Robust license compliance
- Automated SBOM generation
- Strong customer support
Cons:
- It is more focused on compliance than security
- Users have reported incomplete documentation
- Users have reported delays in scan results reflecting in the UI.
- Large-scale scans can be slow
- It struggles with non-standard package managers and may fail to recognise libraries
- Users report that it sometimes fails to show the exact line of code where a vulnerability exists
Pricing:
- Free
- Business: $20 per project/month (Billed annually)
Enterprise: Custom pricing
Why Choose It:
FOSSA is a good option for teams that want fast, automated open-source management without the complexity of heavier legacy platforms.
Gartner Rating: 4.4/5.0
FOSSA Reviews:
4. JFrog Xray
JFrog Xray is a component of the JFrog DevOps platform and serves as a binary analysis and security tool. Xray scans artifacts (such as dependencies, Docker images, compiled binaries) for known security vulnerabilities and license issues..
Key Features:
- Deep Artifact Scanning: Xray can recursively scan all layers of a container image and all transitive dependencies of a package to find issues.
- Policy-Based Actions: Xray allows teams to define security and license policies that trigger automated enforcement.
- Integrations: Xray integrates with common build tools such as Jenkins, GitHub Actions, and GitLab CI.
Pros:
- Broad package type support
- Detects known malicious components
- Context-aware analysis
Cons:
- Initial setup can be complex
- False positives
- Steep learning curve
- Scanning large artifacts and nested dependencies is slow and resource intensive
- Users have reported its UI as cluttered, and hard to navigate
- Deep recursive scans can be slower than lighter SCA tools
- Users have reported challenges when changing configurations or tenants
Pricing:
- Pro: $150 per month
- Enterprise X: $950 per month
- Enterprise +: Custom pricing
Why Choose It:
JFrog Xray is ideal for teams already using the JFog ecosystem and want to shift security left, catching issues as soon as a dependency or image enters the pipeline.
Gartner Rating: 4.5/5.0
JFrog Xray Reviews:
5. Snyk
Snyk is a developer-first security platform that started with a focus on open source dependency scanning (SCA) but now includes SAST, container security, and Infrastructure as Code scanning.
Key Features:
- Developer Integrations: Snyk offers integrations for GitHub, GitLab, Bitbucket, and common IDEs..
- Vulnerability Database: Snyk’s proprietary database is enhanced with third-party and community feeds. It also prioritizes issues based on exploit maturity and reachability
Pros:
- Automated remediation
- Context-aware prioritization
Cons:
- Pricing can be become expensive when scaling
- High false positives
- Limited language support for reachability analysis
- 1mb file size limit for static code analysis
- Limited customization for security policies and scanning rules
- Developers must manually fix vulnerabilities found in transitive (indirect) dependencies
- For Go projects it analyzes at the module level rather than the package level increasing “noise”.
- It opens a separate Jira request for every single finding rather than grouping them by the required fix
- It can miss vulnerabilities in proprietary codebases
Pricing:
- Free
- Team: $25 per month/contributing developer (min. 5 devs)
- Enterprise: Custom pricing
Why Choose It:
Snyk is ideal for teams working heavily with open-source libraries and need security embedded into developer workflows. If
Gartner Rating: 4.4/5.0
Snyk Reviews:
6. Sonatype Nexus Lifecycle
Nexus Lifecycle is an enterprise security and compliance tool from Sonatype. It manages the entire lifecycle of open source components, from introduction to continuous monitoring,with strong enforcement features and proprietary component intelligence.
Key Features:
- Precise Component Intelligence: Nexus Lifecycle’s vulnerability feeds uses Sonatype’s OSS Index and custom research to flag malicious packages and zero-day threats.
- Policy Automation: It allows teams to define and enforce policies across their pipeline, blocking risky libraries at the repository, IDE, or CI level.
Pros:
- Automated Policy Enforcement
- SBOM Management
Cons:
- Steep learning curve
- False positives
- Users have reported its user interface is complex to navigate
- Self-hosted versions can be complex to manage
- Limited support for non-Java languages (e.g., C/C++ or specialized mobile stacks)
- Initial configuration can be complex
- It can struggle to automatically identify proprietary or internal libraries.
- Less developer-friendly when compared to than tools like Aikido Security
Pricing:
Sonatype's nexus lifecycle is only available on its paid plans
- Free
- Pro: $135 per month (billed annually)
- Premium: Custom pricing
Why Choose It:
Sonatype Nexus Lifecycle is ideal for Java centric teams seeking policy-first open source governance.
Gartner Rating: 4.5/5.0
Sonatype Nexus Lifecycle Reviews:
Comparing the Best 6 Mind.io Alternatives
Conclusion
Each of the alternatives covered in this article shines in its own way, but choosing the right Mend.io replacement ultimately depends on your team, existing workflows, and AppSec needs (both today and in the future).
Many teams move away from Mend.io in search of a more modern, developer-centric experience, broader security coverage, and fewer false positives, without managing multiple tools or trading simplicity for complexity.
Aikido Security stands out as an ideal Mend.io alternative by unifying AI-assisted dependency scanning with comprehensive AppSec coverage and developer-friendly workflows, all at a transparent, affordable price. By cutting through noise, prioritizing real risk directly in development workflows, Aikido helps teams secure their dependencies without adding operational overhead.
Ready to simplify your dependency security? Start your free trial or book a demo with Aikido Security today.
If you’re ready to simplify your security stack and start seeing actionable results in minutes, start your free trial or schedule a demo today.
FAQs
How can I migrate data from Mend.io to another platform without data loss?
To successfully migrate from Mend.io you’ll need to export your SBOMs, scan results, and license reports into standard formats (CSV, JSON, SPDX/CycloneDX), then import into the new platform. Remember to validate counts and relationships to ensure nothing is lost. Platforms like Aikido Security simplify migration with seamless ingestion and normalization of historical scan data (SBOMs).
What are the pros and cons of using open-source alternatives to Mend.io?
Open-source tools are cost-effective, customizable, and supported by active communities. However, they often lack enterprise-grade governance, advanced license compliance, and AI-driven prioritization, which can add significant manual triage. Platforms like Aikido Security provide automated triage and compliance reports, reducing noise and simplifying management all at an affordable, transparent price.
Which Mend.io alternative is best for small teams?
For small teams, ease of setup, actionable insights, and low maintenance are key. Aikido Security provides full-stack coverage, AI-driven triage to reduce noise, agentless deployment and seamless CI/CD integration, making it ideal for small teams that need effective vulnerability and license management without heavy configuration.
What features should I consider when choosing IT asset management software?
Key features include automated discovery, inventory tracking, license compliance, vulnerability mapping, CI/CD and cloud integrations, dashboards, alerts, and risk prioritization. Aikido Security combines these capabilities with AI-driven triage, giving teams actionable insights and helping them prioritize the most critical risks across their software and infrastructure.
You Might Also Like:
- Looking for an Endor Labs Alternative? These Tools Do It Better
- 5 Snyk Alternatives and Why They Are Better
- Top GitHub Advanced Security Alternatives for DevSecOps Teams in 2026
- Top 10 Software Composition Analysis (SCA) tools in 2026
- Top 12 Software Supply Chain Security Tools in 2026
- The Top 13 Code Vulnerability Scanners in 2026
- Top Infrastructure as Code (IaC) Scanners in 2026



