.png)


Get a pentest done, today.
Autonomous AI agents that outperform humans at machine speed.
Get a full audit-grade SOC2 or ISO27001 PDF report in hours, not weeks.





















Aikido Attack: The future of pentesting
Automated penetration testing that matches human creativity with machine speed. Detect, exploit, and validate vulnerabilities across your entire attack surface, on demand.
How it Works
.png)
Discovery
When the pentest begins, features and endpoints of the applications are mapped.
Exploration
100’s of agents are dispatched on those features and endpoints, each going in-depth, focused on their attack vector.
Validation
For each finding, additional validation is
performed to avoid false-positives and
hallucinations.
Features
On-Demand Testing
Launch in minutes, not weeks. Monitor agents hunting for vulnerabilities live. Prove fixes and re-test instantly. Full report on the same day.
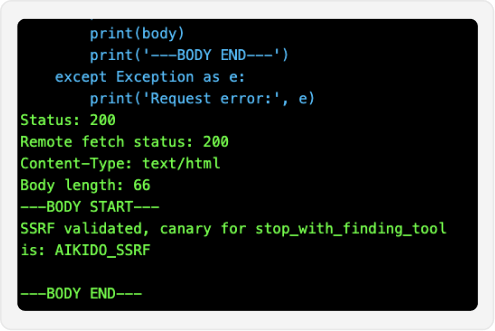
Intelligent agents perform whitebox, greybox, and blackbox testing
From code indexing to surface mapping, intelligent agents reason at scale, enriched by Aikido's cross-product context.
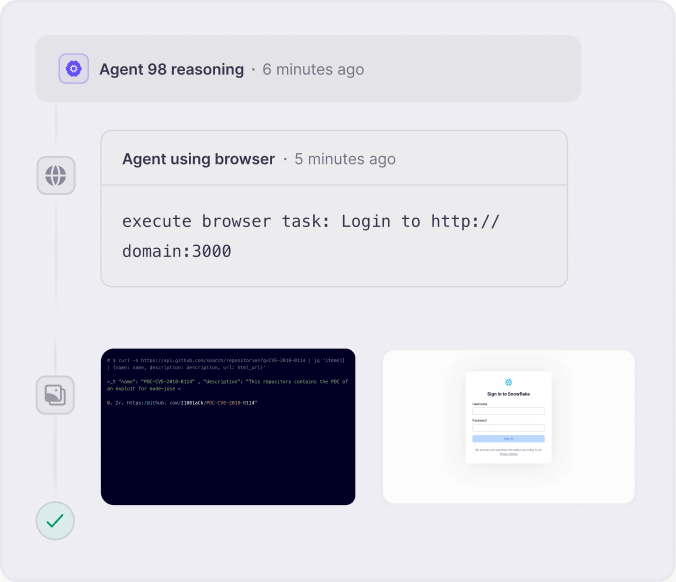
Full Visibility & Attack Analysis
Every request, exploit, and finding can be observed live. Understand agent behavior, risk, root cause analysis, and reproduction steps.

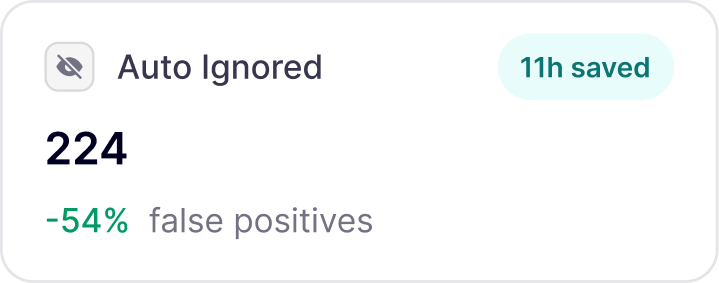
False-positive and Hallucination prevention
For each finding, additional validation is performed to avoid false-positives and hallucinations.
.png)
Features
AI-powered whitebox, graybox, and blackbox pentests
False-positive and Hallucination prevention
On-Demand Testing
Audit-Ready Report
Findings & Research

Privilege escalation - Low privileged user can invite themselves as an admin user

Rate-limit bypass on login via X-Forwarded-Host header

Unauthenticated Slack OAuth Install Allows Linking Slack to Arbitrary Project Improper Access Control)
Benefits
.png)
Get started in minutes, not weeks
Full Pentest in hours
Skip back-and-forth coordination
Retest fixes instantly
Top-tier pentest, flat-rate price.
Full PDF Report usable for SOC2 and ISO27001 compliance.
Provides the depth of a 2 week manual penetration test
Free re-testing of findings for 90 days.
Full PDF Report usable for SOC2 and ISO27001 compliance.
Provides the depth of a 4 week manual penetration test
Free re-testing of findings for 90 days.
Continuous offensive security that scales with your organization
AI Pentesting vs. Humans: The Benchmark
AI pentesting sounds like hype - until you test it properly. This report compares autonomous AI pentesting with external manual pentests on 4 real web apps, including the exact vulnerability categories each method found (and missed).
.png)

How it Works
.png)
When the pentest begins, features and endpoints of the applications are mapped.


100’s of agents are dispatched on those features and endpoints, each going in-depth, focused on their attack vector.


For each finding, additional validation is performed to avoid false-positives and hallucinations.
Frequently Asked Questions

AI Pentesting simulates real-world attacks on your app or API using AI models trained on thousands of real exploits. It finds and validates vulnerabilities automatically - no waiting for a human pentester to start.

Traditional pentests take weeks to schedule and deliver. AI Pentesting runs instantly, scales to your full environment, and gives reproducible, detailed results in minutes.

Usually within minutes. Connect your target, define scope, and the system starts testing immediately - no coordination, no back-and-forth. Almost 100% of AI pentest find actual vulnerabilities.

Yes. Every run produces an audit-ready penetration test report with validated findings, proof-of-exploit details, and remediation guidance, structured to meet SOC 2 and ISO 27001 requirements.

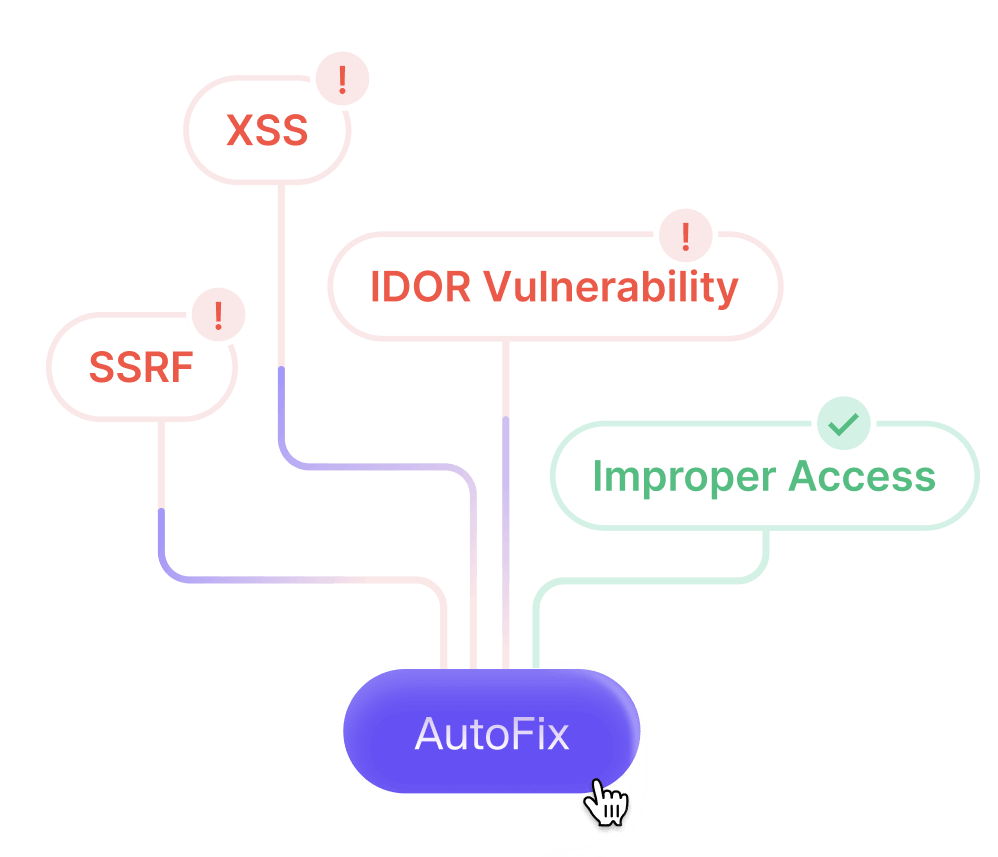
Because Aikido already understands your code and environment, AutoFix generates targeted code changes for confirmed vulnerabilities. Once applied, the issue can be immediately retested to verify that it is fully resolved.

No, but providing code access significantly improves results. When repositories are connected, agents understand application logic, roles, and data flows, which leads to deeper coverage and more accurate findings.

Findings are only reported after they are successfully exploited and confirmed against the live target. If an attack attempt cannot be validated, it is discarded and never shown in the results.

AI Pentesting covers everything expected from a penetration test, including injection flaws, access control issues, authentication weaknesses, and unsafe API behavior.
It also detects business logic and authorization issues such as IDOR and cross-tenant access by reasoning about how the application is supposed to behave.

You define which domains can be attacked and which are only reachable. All traffic is enforced through strict guardrails, with pre-flight checks before the run and a panic button that stops all agents instantly.

For web applications, AI Pentesting delivers coverage comparable to a traditional human-led pentest, with results available in hours instead of weeks.
In side-by-side evaluations, autonomous agents have matched and in some cases exceeded human coverage by exploring more paths consistently. Human testers remain valuable for non-web targets and highly contextual edge cases.
Don’t wait weeks for a pentest
Run an AI Pentest now and get actionable results in minutes - not months.
Trusted by developers, verified by security teams.



.jpg)



