.png)

Get an AI pentest, today.
Autonomous AI agents that think like hackers and move at machine speed.
Get full SOC2- and ISO27001-ready pdf report in hours, not weeks.





















How Aikido compares to Xbow
Aikido has transparent credit-based pricing. Small Pilot/PoC possible. Free retests included. XBOW forces heavy pre-commitment, no testing.












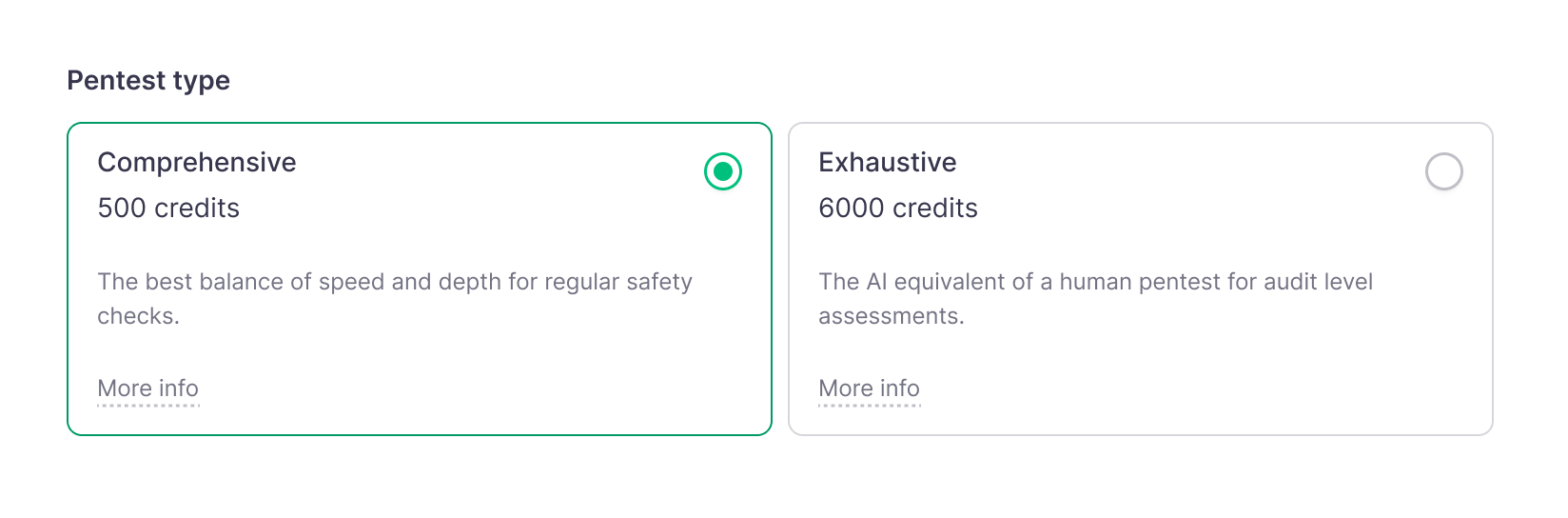
Top-tier pentest, flat-rate price.
Full PDF Report usable for SOC2 and ISO27001 compliance.
Provides the depth of a 2 week manual penetration test
Free re-testing of findings for 90 days.
Full PDF Report usable for SOC2 and ISO27001 compliance.
Provides the depth of a 4 week manual penetration test
Free re-testing of findings for 90 days.
Continuous offensive security that scales with your organization
Aikido Attack: The future of pentesting
Continuous, automated penetration testing that matches human creativity with machine speed. Detect, exploit, and validate vulnerabilities across your entire attack surface, on demand.
Features
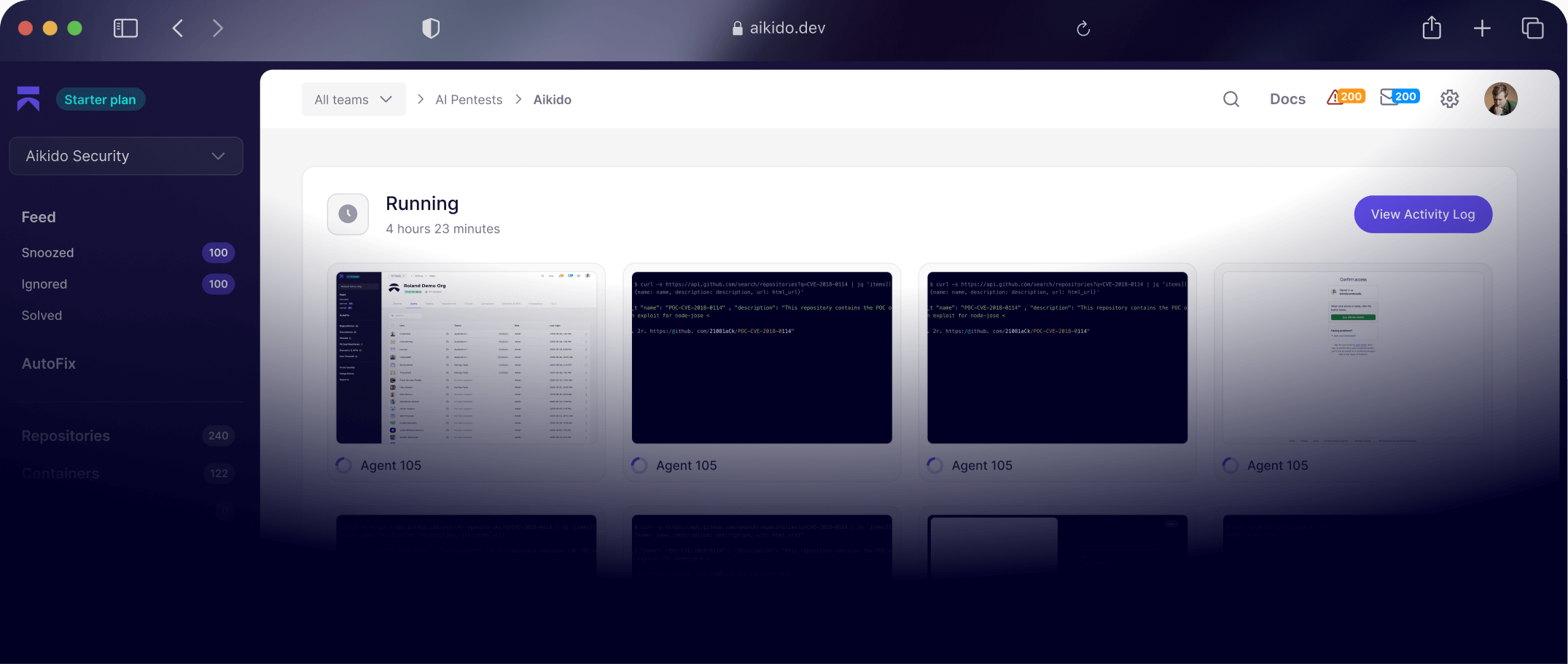
On-Demand Testing
Launch in minutes, not weeks. Continuous validation. Prove fixes instantly. Full report in days.
AI-powered whitebox, graybox, and blackbox pentests
From code indexing to surface mapping, agents unify white-, grey-, and black-box testing enriched by Aikido's cross-product context.
.jpg)
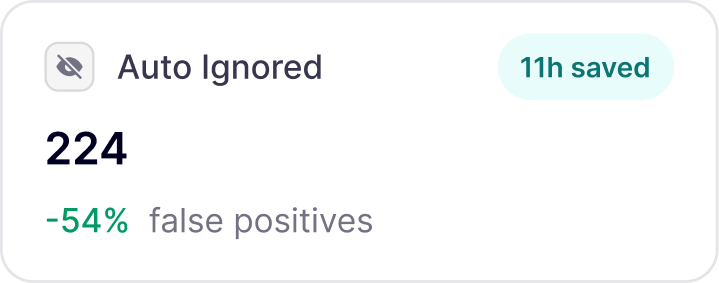
False-positive and Hallucination prevention
For each finding, additional validation is performed to avoid false-positives and hallucinations.
Audit-Ready Report
A full, audit-grade (SOC2, ISO27011, etc…) dossier equivalent to a manual pentest, with evidence, repro steps, and remediation guidance for certification.
.jpg)

Test your app today
Get a pentest done in minutes - not months.


.png)
Features
AI-powered whitebox, graybox, and blackbox pentests
False-positive and Hallucination prevention
On-Demand Testing
Audit-Ready Report
Benefits
.png)
Get started in minutes, not weeks
Full Pentest in hours
Skip back-and-forth coordination
Retest fixes instantly
How it Works
.png)
Discovery
When the pentest begins, features and endpoints of the applications are mapped.
Exploitation
100’s of agents are dispatched on those features and endpoints, each going in-depth, focused on their attack vector.
Validation
For each finding, additional validation is performed to avoid false-positives and hallucinations.
How it Works
.png)
When the pentest begins, features and endpoints of the applications are mapped.


100’s of agents are dispatched on those features and endpoints, each going in-depth, focused on their attack vector.


For each finding, additional validation is performed to avoid false-positives and hallucinations.
Don’t wait weeks for a pentest
Run an AI Pentest now and get actionable results in minutes - not months.
Trusted by developers, verified by security teams.


