The all-in-one Cycode alternative
Aikido Security is the next-gen code-to-cloud security platform.
.png)






















How Aikido compares to Cycode
Cycode is a solid all-round security platform, however it comes with a price tag.
Aikido matches functionality and uses transparent prices, no hidden charges for usage.
Median contract ~$65K/year.



- Reachability Analysis
- Malware Detection in Dependencies
- AutoFix For SCA
- License Compliance
- SBOM Support
- License PR Release Gating
- Noise Reduction (False Positive Filtering)
- More noisy



- SAST AI Autofix
- Multi-file Analysis
- Taint Analysis
- Custom SAST Rules
- SAST Issues Directly In IDE


- API Discovery/API Fuzz Testing
- Authenticated DAST
- Automated Swagger Creation
- IDOR Detection
- Attack Surface Management




- Extended Lifetime Support
- Autofix Container Images



- Virtual Machine Scanning
- Cloud & K8s Posture Management
- Infrastructure as Code Scanning
- Asset Inventory Management
- Attack Path Analysis





Everything You Wish Security Tools Actually Did
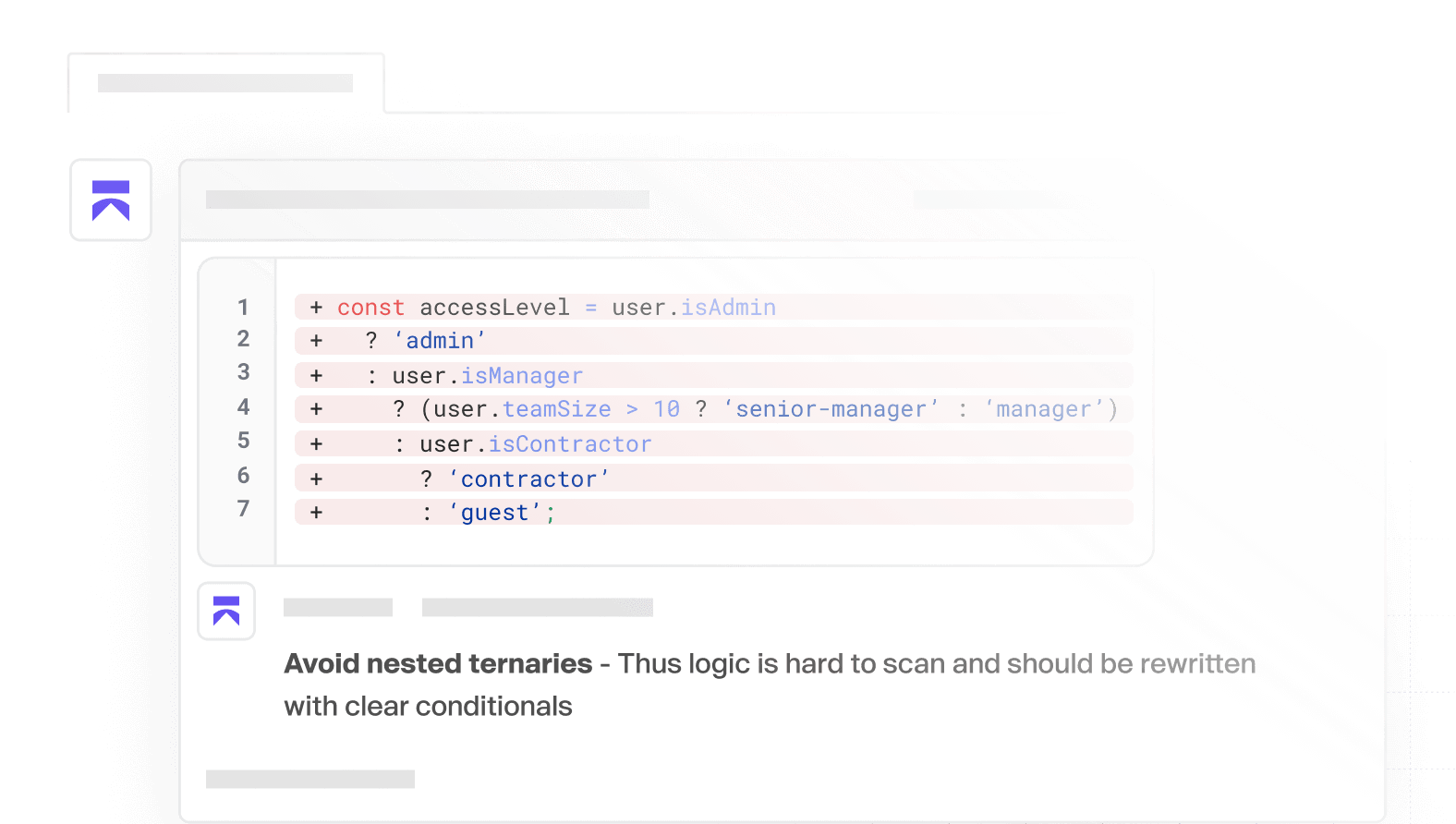
Static Application Security Testing (SAST)
Scans your source code for security vulnerabilities such as SQL injection, XSS, buffer overflows and other security risks. Checks against popular CVE databases. It works out-of-the-box and supports all major languages.

Software Composition Analysis
Analyse third-party components such as libraries, frameworks, and dependencies for vulnerabilities. Aikido does reachability analysis, triages to filter out false positives, and provides clear remediation advice. Auto-fix vulnerabilities with one click.

Infrastructure as code (IaC)
Scans Terraform, CloudFormation & Kubernetes Helm charts for misconfigurations.
- Catch misconfigurations that expose your infrastructure to risk
- Identify vulnerabilities before they reach your main branch
- Integrates in your CI/CD Pipeline

Container Security
Scan your container operating system for packages with security issues.
- Checks if your containers have any vulnerabilities (Like CVEs)
- Highlights vulnerabilities based on container data sensitivity
- Auto-fix your container images with AI

DAST & API Security
Monitor your app and APIs to find vulnerabilities like SQL injection, XSS, and CSRF, both on the surface and with authenticated DAST.
Simulate real-world attacks and scan every API endpoint for common security threats.
.avif)
Cloud & K8s Security Posture Management (CSPM)
Detect cloud infrastructure risks across major cloud providers.
- Scans Virtual Machines (AWS EC2 instances) for vulnerabilities.
- Scan your cloud for misconfigurations and overly permissive user roles/access
- Automate security policies & compliance checks for SOC2, ISO27001, CIS & NIS2

Secrets detection
Check your code for leaked and exposed API keys, passwords, certificates, encryption keys, etc…

Malware detection
The npm ecosystem is susceptible to malicious packages being published because of its open nature. Aikido identifies malicious code that may be embedded within JavaScript files or npm packages. (Scans for backdoors, trojans, keyloggers, XSS, cryptojacking scripts and more.)

AI Code Quality
Ship quality code, faster. Instant feedback, smart detection, and clear PR comments, so you can focus on building.
Trusted by thousands of developers at world’s leading organizations
FAQ
Has Aikido itself been security tested?
Yes — we run yearly third-party pentests and maintain a continuous bug bounty program to catch issues early.
Does Aikido require agents?
No! Unlike others, we're fully API based, no agents are needed to deploy Aikido! This way you're up & running in mere minutes & we're way less intrusive!
I don’t want to connect my repository. Can I try it with a test account?
Of course! When you sign up with your git, don’t give access to any repo & select the demo repo instead!
What happens to my data?
We clone the repositories inside of temporary environments (such as docker containers unique to you). Those containers are disposed of, after analysis. The duration of the test and scans themselves take about 1-5 mins. All the clones and containers are then auto-removed after that, always, every time, for every customer.
Get secure now
Secure your code, cloud, and runtime in one central system.
Find and fix vulnerabilities fast automatically.



.avif)





_FastestImplementation_Small-Business_GoLiveTime.svg)
_HighPerformer_EMEA_HighPerformer.svg)


_HighPerformer_Europe_HighPerformer.svg)





_EasiestToUse_Small-Business_EaseOfUse.svg)


_Leader_Europe_Leader.svg)
_BestEstimatedROI_Roi.svg)


