You have probably heard it a million times: "threats are evolving, security is constantly changing."
However, regardless of how true that statement is, staying ahead and protecting your infrastructure from threats requires more than just “knowing the landscape is shifting”; it requires knowing which tools actually fit your environment.
It also entails understanding how those threats affect organizations of every size and what you need to do about it.
In 2025, 78% of organizations worldwide reported experiencing a successful cyberattack, showing that attacks aren’t limited to big enterprises with deep security teams, they impact startups, small businesses, and global companies alike. With risks this widespread, it’s one thing to recognize you need protection and quite another to figure out which tools actually fit your stack, team, and risk profile.
In fact, choosing the right cybersecurity tools is often harder than the threats themselves: there are solutions for endpoint protection, network monitoring, cloud defense, identity security, and vulnerability management, but not every tool works the same way for every company.
Well, in this article, we walk through 10 cybersecurity platforms that handle threat detection across different domains: endpoint, network, cloud, identity, and vulnerability management. Before we go in depth into the tools on this list, here’s a highlight of the top 10 cybersecurity tools for 2026:
- Palo Alto Networks
- Aikido Security
- CrowdStrike
- Microsoft (Defender XDR)
- Sophos (XDR / MDR)
- Qualys
- IBM Security (QRadar Suite)
- Cisco (XDR / Security Cloud)
- Trend Micro (Vision One)
- Fortinet (Security Fabric)
What Is Cyber Security?
Cybersecurity is the practice of protecting software systems, applications, infrastructure, and data from unauthorized access, attacks, and misuse. It covers everything from securing application code and third-party dependencies to protecting cloud environments, APIs, containers, and live production systems. As organizations build and ship software faster, cybersecurity has evolved from a perimeter-based concern into a core part of how software is designed, built, and operated.
Modern cybersecurity focuses on identifying and reducing risk as early as possible while still protecting running systems from real-world attacks. This includes scanning code for vulnerabilities, monitoring open-source dependencies, preventing cloud misconfigurations, detecting exposed secrets, and stopping threats at runtime. The goal is not just to find issues, but to help teams fix the right problems quickly, without slowing down development or creating unnecessary noise.
Why Do Cyber Security Tools Matter?
Running workloads across different clouds and the various means by which we package and store data means there is a lot more room to choose how our applications are delivered.
At the same time, attackers now have more variety than ever when it comes to choosing where to strike. More deployment options mean more entry points. More data stores mean more places for sensitive information to leak. More integrations mean more trust boundaries to exploit.
Prevention alone can’t cover everything. Firewalls get bypassed, credentials get phished, and misconfigurations slip through. Building a comprehensive threat defense strategy requires teams to leverage tooling that can surface all their cloud assets and provide relevant insights that can catch attack vectors before threat actors do.
Benefits of Using Cyber Security Tools
With an understanding of why threat detection matters, here are some of the benefits of leveraging cybersecurity tools:
- Reduced detection time: Leveraging a cybersecurity tool means you can respond to threats in hours or days instead of months, limiting how far attackers can move through your environment before you respond.
- Lower breach costs: Faster detection reduces the blast radius of an incident, resulting in fewer compromised systems and lower remediation and recovery costs.
- Continuous visibility: Maintain round-the-clock monitoring of cloud workloads, endpoints, and identities without relying on manual log reviews.
- Compliance alignment: Support detection, reporting, and response requirements under regulations such as NIS2, DORA, SEC rules, and common cyber insurance policies.
- Improved team efficiency: Automated triage and alert correlation allow security teams to focus on real threats instead of spending time on false positives.
How to Choose a Top Cyber Security Tool
To make a meaningful comparison, it helps to evaluate cybersecurity tools based on criteria that reflect how modern systems are built and attacked. Not every platform needs to cover everything, but the best tools are clear about what they protect, how well they detect real threats, and how easily teams can act on the findings.
- Breadth of coverage: What parts of your environment does the tool protect? Does it focus on endpoints, networks, cloud infrastructure, identity, application code, or vulnerabilities? The right tool should align with your primary risk areas rather than claiming blanket coverage without depth.
- Depth of visibility: How deeply does the tool inspect its target surfaces? For example, does it understand cloud context and permissions, application logic, and runtime behavior, or does it rely on surface-level checks that generate noise?
- Deployment model: Does the tool require agents, sensors, or complex infrastructure to function, or can it operate with minimal setup? Agentless approaches often reduce operational overhead, while agents may provide deeper visibility in certain environments.
- Actionability and accuracy: How effectively does the tool reduce false positives and surface real, exploitable risks? Look for platforms that prioritize findings, provide clear remediation guidance, and automate triage instead of overwhelming teams with alerts.
- Ease of use: Can both security and engineering teams use the tool without extensive training? An intuitive interface and clear workflows often matter more than raw feature count.
- Scalability: Will the tool continue to perform as your organization grows? Consider how it handles increases in cloud resources, endpoints, applications, or data volume without degrading performance.
- Ease of integration: How well does the tool fit into existing workflows? Strong integration with CI/CD pipelines, cloud providers, identity systems, and ticketing tools can significantly improve adoption and response times.
- Automation: Does the platform support automated remediation, such as one-click fixes or automated pull requests? Automation reduces manual effort and helps teams respond faster to real threats.
- Total cost of ownership (TCO): Beyond licensing, consider the ongoing cost of deployment, maintenance, tuning, and staffing. Tools that require heavy customization or dedicated operators can become expensive over time.
10 Cyber Security Tools for 2026
1. Palo Alto Networks
Palo Alto Networks describe themselves as a combination of Chronosphere and Cortex AgentiX platform, which will deliver real-time, agentic remediation for the world’s leading AI-native companies.
Their solutions span threat detection at the network level and cloud security, a standout feature is their AI-driven SOC, which aims to continuously keep you compliant with the SOC2 standard
Key Features
- Autonomous SOC operations: ML-driven correlation reduces manual triage through automated incident grouping and response playbooks
- Cross-domain telemetry: Unified data ingestion from the network. cloud (Prisma), endpoint, and identity sources
- Threat intelligence integration: Unit 42 threat research feeds directly into detection rules and response recommendations
- SOAR built-in: Native orchestration and automation without requiring separate tooling
Pros
- Strong integration across Palo Alto's own product ecosystem
- Reduces alert fatigue through intelligent grouping
- Comprehensive coverage if already invested in Palo Alto infrastructure
Cons
- Third-party integrations are not as seamless as the native Palo Alto product integrations
- Steep learning curve for teams new to the platform
- Pricing can escalate quickly with data ingestion volumes
- Full value requires commitment to the Palo Alto ecosystem
Best For
Organizations with existing Palo Alto network infrastructure (Strata firewalls, Prisma Cloud) Looking to consolidate security operations into a single platform.
Pricing
Custom pricing based on data ingestion and endpoints. Contact sales for quotes. Generally positioned at enterprise price points.
Gartner rating: 4.6/5
2. Aikido Security
If you’re looking for code, cloud or runtime security, Aikido Security is thea modern security platform designed to help you.teams Its platform enables you to identify and remediate real application and cloud risks without excessive noise. It focuses on the most common attack paths in modern software, covering application code, open-source dependencies, infrastructure, containers, APIs, and runtime environments, while integrating directly into CI/CD pipelines. The platform is used by 50,000+ organizations including start-ups and enterprises, such as Revolut, Premier League, SoundCloud, and Niantic.
Across code and dependency scanning, Aikido prioritizes exploitable issues using techniques like reachability analysis, malware detection, license risk checks, and end-of-life package warnings. Instead of presenting scattered findings, it groups related issues and provides clear remediation guidance, including automated pull requests that make fixes fast and manageable.
The same risk-focused approach extends to infrastructure and cloud security. Aikido detects real misconfigurations in Terraform, Kubernetes, CloudFormation, and cloud environments, highlighting issues such as exposed resources, excessive permissions, and insecure defaults directly at the point where they are introduced. This allows teams to catch problems early, before they reach production.
For running applications, Aikido combines container scanning, DAST, API security, secrets detection, and runtime protection to surface meaningful risks and stop active threats. Automated triage reduces false positives across all scans, ensuring teams focus on what matters most.
Key Features
- Static and dependency analysis: Scans source code (SAST) and third-party dependencies (SCA) for vulnerabilities such as SQL injection, XSS, insecure deserialization, and known CVEs. Uses reachability analysis to reduce false positives and provides clear remediation guidance, including one-click autofixes where possible.
- Dynamic and API security testing: Performs DAST and API security scanning against live applications, including authenticated paths, to detect runtime vulnerabilities like SQL injection, XSS, CSRF, and exposed endpoints.
- Cloud and infrastructure security: Includes CSPM and IaC scanning to detect misconfigurations in cloud environments, Terraform, CloudFormation, and Kubernetes manifests, with support for compliance frameworks such as SOC 2, ISO 27001, CIS, and NIS2.
- Container and runtime coverage: Scans container images and underlying OS packages for vulnerabilities, prioritizing findings based on data sensitivity and exploitability.
- Secrets detection: Identifies leaked credentials, API keys, certificates, and encryption material in code and exposed surfaces, with CI/CD-native integration and noise reduction to avoid irrelevant alerts.
Pros
- Broad security coverage across code, cloud, containers, APIs, and runtime surfaces
- Fast setup with minimal configuration and low ongoing maintenance
- Strong signal-to-noise ratio through automatic triage and prioritization
- Developer-friendly workflows with CI/CD integration and actionable remediation
- Cloud-based delivery with a free tier that lowers adoption friction
Pricing: Free forever tier with flat-rate paid plans for additional users or advanced features.
Gartner Rating: 4.9/5
3. CrowdStrike
Now well known for their outage back in 2024, CrowdStrike is an endpoint protection and XDR platform with heavy emphasis on threat intelligence from their massive telemetry base.
With products spanning across endpoint detection, network monitoring, and detection
Key Features
- Threat Graph: Processes trillions of security events each week to identify attack patterns and uncover novel threats.
- Real-time threat hunting: The OverWatch managed service provides 24/7, human-led threat hunting.
- Lightweight agent: A single-agent architecture minimizes endpoint performance impact.
- Identity protection: Falcon Identity Threat Detection monitors Active Directory and other identity stores.
Pros
- Industry-recognized depth of threat intelligence
- Fast deployment enabled by a cloud-native architecture
- Strong endpoint visibility with behavior-based detection
Cons
- Primarily endpoint-centric; cloud and identity capabilities are newer additions
- Module-based pricing can become expensive for full platform coverage
- Network detection capabilities are less mature than endpoint detection
- Some users report high resource consumption during intensive scans
- Identity and cloud security modules require separate purchases
- Can generate a high alert volume without careful tuning
Best For
Organizations that prioritize endpoint visibility and behavioral threat detection, particularly those that value deep threat intelligence and prefer not to manage on-premises infrastructure.
Pricing
Billed per device, with custom plans available.
Gartner Rating: 4.7/5
4. Microsoft (Defender XDR)
Microsoft is a company that needs no introduction. Defender XDR (formerly Microsoft 365 Defender) is a unified XDR platform covering endpoints, email, identity, and cloud applications, with native integration across Azure and Microsoft 365.
Key Features
- Native Microsoft 365 integration: Correlates signals across Outlook, Teams, SharePoint, and Azure AD with minimal additional configuration.
- Automatic attack disruption: Can automatically isolate compromised assets and disable accounts during active attacks.
- Copilot for Security: AI-powered assistant for threat investigation and response (available at an additional cost).
Pros
- Seamless experience for organizations already committed to the Microsoft stack
- No additional agent required for Windows endpoints
- Included in many Microsoft 365 E5 licensing bundles
Cons
- Detection quality can vary outside the Microsoft ecosystem
- Gaps may appear in multi-cloud environments dominated by AWS or GCP
- Can be complex to configure for optimal results
- Confusing licensing model; full capabilities typically require E5 or add-ons
- Weaker alert correlation across non-Microsoft security tools
- Copilot for Security is a costly add-on
Best For
Microsoft-centric environments that rely heavily on Azure AD, Microsoft 365, and Intune. The value proposition diminishes significantly in heterogeneous or multi-cloud environments.
Pricing
Often bundled with Microsoft 365 E5 (approximately $57 per user per month). Defender for Endpoint P2 is available standalone at around $5.20 per user per month. Copilot for Security is priced separately.
Gartner Rating: 4.5/5
5. Sophos (XDR / MDR)
Originally focused on antivirus and endpoint protection. Over the past decade, the company has expanded into next-generation firewalls, cloud security, and managed detection and response, positioning itself strongly in the mid-market. Its XDR platform is complemented by a mature MDR offering, with recent additions including Identity Threat Detection and Response (ITDR).
Key Features
- 100% MITRE coverage: Achieved 100% detection coverage in the MITRE ATT&CK Enterprise 2025 evaluation.
- Managed threat hunting: The MDR service provides 24/7, human-led threat hunting and incident response.
- Identity threat detection: ITDR monitors for credential compromise, privilege escalation, and identity-based attacks.
- Dark web monitoring: Scans for leaked or compromised credentials associated with the organization.
Pros
- Strong MDR offering for organizations without a 24/7 SOC
- Competitive performance in independent evaluations
- Good fit for mid-market organizations with reasonable pricing
Cons
- XDR capabilities are newer compared to some competitors; Sophos is historically known for endpoint and firewall products
- ITDR launched in late 2025 and is still maturing
- Third-party integrations are improving but less extensive than larger vendors
- Some users report slower console performance at large scale
- Advanced features often require deeper buy-in to the Sophos ecosystem
- Reporting customization is limited compared to dedicated SIEM platforms
Best For
Mid-market organizations seeking strong detection and response capabilities without building a full internal SOC, particularly those concerned about identity-based attacks.
Pricing: contact sales
Gartner Rating: 4.5 / 5
6. Qualys
Best known for vulnerability management as a service. Its VMDR (Vulnerability Management, Detection, and Response) platform combines continuous asset discovery with vulnerability assessment, risk prioritization, and integrated remediation across IT, OT, cloud, and IoT environments.
Key Features
- TruRisk scoring: Goes beyond CVSS by factoring in exploit availability, active weaponization, asset criticality, and exposure context.
- Detection breadth: Covers over 103,000 CVEs, with claims of identifying critical vulnerabilities up to 16 hours earlier than competitors.
- Vulnerability detection sources: Identifies where each vulnerability was discovered, whether via agent, perimeter scan, or internal scanner.
Pros
- Deep and mature vulnerability detection coverage
- Risk-based prioritization helps reduce alert noise
- Unified asset visibility across hybrid and heterogeneous environments
Cons
- Primarily vulnerability-focused; not a replacement for XDR or SIEM for behavioral detection
- Agent deployment can be complex in large or highly segmented environments
- Scan performance may impact production systems if not carefully tuned
- UI and workflow have a learning curve
- Reporting setup often requires significant upfront effort
- Some integrations require professional services engagement
Best For
Organizations where vulnerability management is central to the security program, particularly those requiring comprehensive visibility across hybrid infrastructure spanning ITand IoT environments.
Pricing: contact sales
Gartner Rating: 4.4/5
7. IBM Security (QRadar Suite)

IBM Security’s QRadar Suite is a long-established SIEM platform that has evolved into a broader XDR offering, backed by decades of enterprise security operations experience. Positioned within IBM’s wider security portfolio, QRadar emphasizes large-scale log analysis, compliance reporting, and AI-assisted threat detection.
Key Features
- Log analysis at scale: Designed to handle extremely high log volumes, reflecting IBM’s decades of experience operating SIEMs in large enterprises.
- Watson AI integration: Uses AI-driven analytics for anomaly detection and automated triage.
- Unified analyst experience: The QRadar Suite consolidates SIEM, SOAR, and XDR capabilities into a single workflow.
- Threat intelligence: Integrates IBM X-Force threat intelligence feeds directly into detection and investigation.
Pros
- Effectively handles massive log ingestion and retention requirements
- Strong compliance, auditing, and reporting capabilities
- An extensive ecosystem of third-party integrations
Cons
- Operationally heavy and often requires dedicated personnel to maintain
- Complexity can overwhelm smaller security teams
- On-premises deployments demand significant infrastructure investment
- Detection rule updates and tuning can be slow
- The licensing model is complex and difficult to forecast
- Cloud-based QRadar offerings have a different and sometimes reduced feature set
Best For
Large enterprises with heterogeneous environments and dedicated security operations teams, particularly those with existing IBM relationships or significant mainframe and hybrid infrastructure.
Pricing: contact sales
Gartner Rating: 4.3/5
8. Cisco (XDR / Security Cloud)
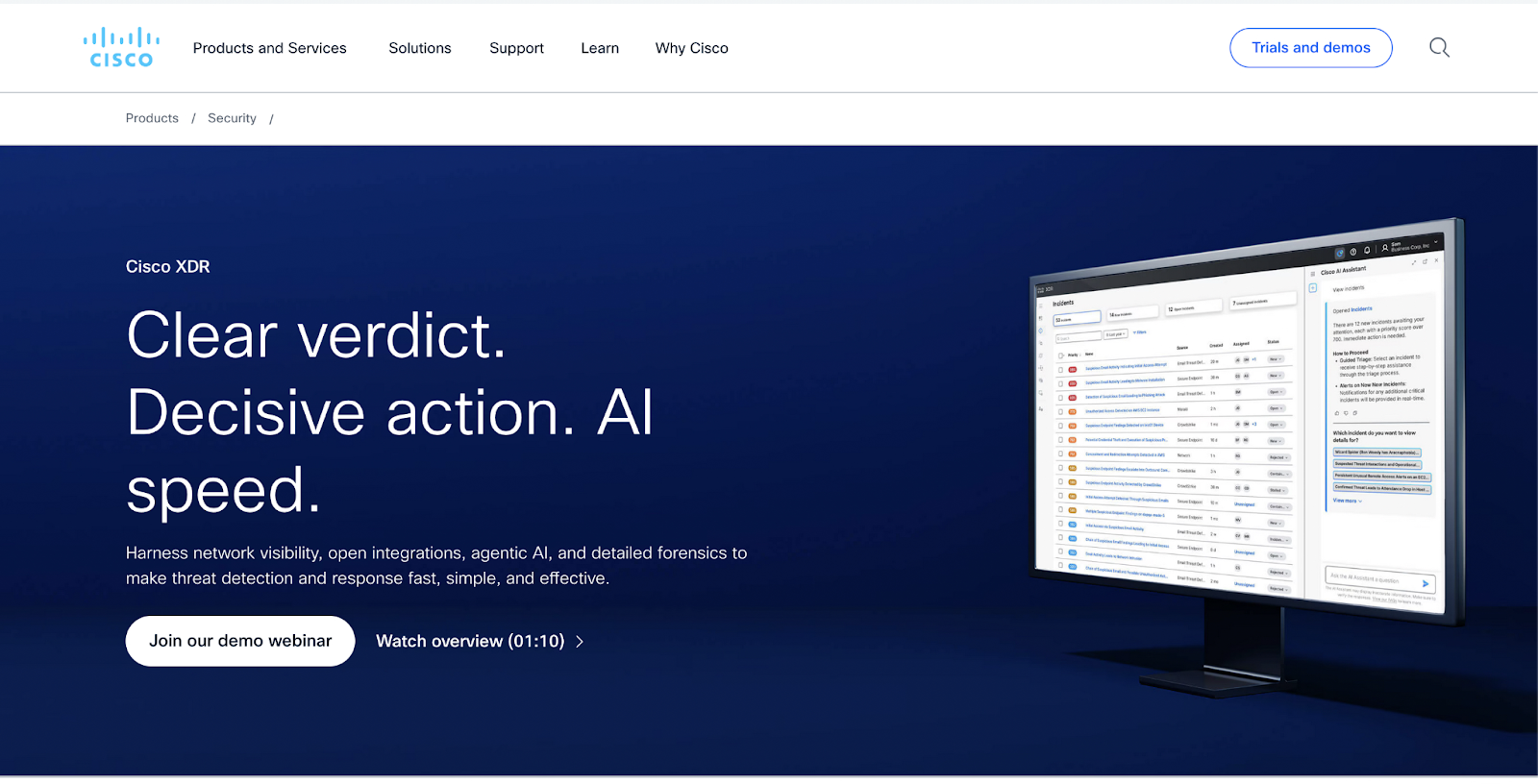
Cisco’s XDR, delivered through the Cisco Security Cloud, aims to unify detection and response by correlating telemetry across Cisco’s extensive portfolio, including networking, email, endpoint, and cloud security products. The platform’s strength lies in deep network visibility and threat intelligence, particularly for organizations already heavily invested in Cisco infrastructure.
Key Features
- Network visibility: Enriches detections with network flow data when running Cisco networking infrastructure.
- SecureX integration: Acts as an orchestration layer connecting multiple Cisco security products into a unified workflow.
- Talos intelligence: Leverages threat intelligence from one of the largest commercial threat research teams in the industry.
- Email security: Provides integrated email threat detection through Cisco Secure Email.
Pros
- Unmatched network-level visibility for Cisco-centric environments
- High-quality threat intelligence from Cisco Talos
- Strong leverage of existing Cisco infrastructure investments
Cons
- XDR capabilities are still maturing following the Splunk acquisition
- Ongoing integration and product roadmap uncertainty
- Endpoint detection is less mature than network-based visibility
- Deployment can be complex in hybrid and multi-cloud environments
- Full value requires deeper commitment to the Cisco ecosystem
- Some product overlap and consolidation efforts are still in progress
Best For
Organizations with significant Cisco networking investments that want to extend existing infrastructure telemetry into security detection and response. Buyers should closely evaluate how Splunk integration evolves.
Pricing
Custom pricing, often bundled through Cisco Enterprise Agreements. Standalone product pricing varies widely depending on deployment size and scope.
Gartner Rating: 4.7/5
9. Trend Micro (Vision One)

Trend Micro has been a staple in endpoint security for decades and has successfully transitioned into a full XDR platform with Vision One. The platform excels at correlating data across endpoints, servers, email, networks, and cloud workloads, with a particular strength in tracing attack chains that span multiple vectors.
Key Features
- Cross-layer detection: Traces attack chains across email-to-endpoint-to-server scenarios, connecting related activity into unified incidents.
- Risk insights: Quantifies organizational risk exposure across the attack surface with prioritized recommendations.
- Workbench investigation: Offers a unified console for alert triage and incident investigation across all telemetry sources.
- Cloud security integration: Extends coverage to containers, serverless functions, and cloud workloads.
Pros
- Strong correlation between email and endpoint attack vectors.
- Long track record and maturity in endpoint protection (a 20-time Gartner Magic Quadrant Leader).
- Competitive and flexible pricing models, often more cost-effective than other top-tier XDR competitors.
- Extensive support for legacy operating systems alongside modern cloud-native environments.
Cons
- Cloud-native and container security capabilities were later additions to the suite.
- Organizations heavily invested in Kubernetes may find the detection depth lacking compared to specialized tools.
- Some users report that false positive rates require ongoing manual tuning.
- Third-party integrations are less extensive than larger platform ecosystem vendors.
- The agent can be resource-intensive on older endpoint hardware.
Best For
Organizations where email and endpoint are the primary attack vectors, particularly those already using Trend Micro products, who want a consolidated, high-visibility XDR experience.
Pricing: Exact quotes require contacting sales.
Gartner Rating: 4.7/5
10. Fortinet (Security Fabric)
Best known for its FortiGate firewalls, Fortinet has expanded into a comprehensive security platform under the Security Fabric umbrella. The platform unifies network security, endpoint protection, and cloud workload visibility, offering a highly integrated ecosystem that excels in environments where network-level detection and OT (Operational Technology) security are top priorities.
Key Features
- FortiGuard Labs Intelligence: Processes over 100 billion security events daily to provide real-time, AI-driven threat intelligence across the entire Fabric.
- Network-Level Detection: Deep integration between FortiGate firewalls and the broader detection stack allows for correlated visibility across all network traffic.
- OT and Industrial Security: Purpose-built capabilities for securing industrial control systems (ICS) and SCADA environments, including ruggedized hardware.
- Unified SASE Integration: Combines on-premises network security with cloud-delivered Secure Access Service Edge functionality for hybrid workforces.
Pros
- Best-in-class performance for organizations already running Fortinet network infrastructure.
- One of the few platforms with deep, native support for industrial and manufacturing environments.
- Custom-built SPU (Security Processing Unit) chips offer superior throughput compared to software-only competitors.
- While proprietary, the "Fabric" covers more ground (WLAN, LAN, SD-WAN, and Endpoint) than almost any other single vendor.
Cons
- Vendor Lock-in: The platform’s value is highest when using an all-Fortinet stack; integration with non-Fortinet products often requires complex "Fabric Connectors."
- Interface Complexity: The management consoles (FortiManager/FortiAnalyzer) offer deep control but are known for a steeper learning curve and a more traditional UI.
- Endpoint Maturity: While improving, FortiClient and FortiEDR are often viewed as secondary to their network security powerhouses.
- Licensing Friction: Users frequently report that navigating the various support tiers and feature licenses can be cumbersome.
Best For
Organizations with significant Fortinet network infrastructure, particularly those in the manufacturing, energy, or utilities sectors, where OT security and network segmentation are critical.
Pricing: contact sales for a quote
Gartner Rating: 4.6/5
Conclusion
Choosing the right cybersecurity tools in 2026 is less about chasing the most features and more about matching detection capabilities to how your systems are actually built and operated.
As attack surfaces expand across endpoints, cloud infrastructure, identities, and application code, security teams need tools that surface real risk, reduce noise, and fit into existing workflows rather than slowing them down.
The platforms in this list each excel in different domains, from endpoint and network detection to vulnerability management and SIEM-driven visibility. Aikido Security stands out by focusing on where modern risk is introduced across code, dependencies, infrastructure, and runtime, and by making remediation practical through automated triage and clear fixes. If you are looking to improve security coverage without adding complexity or alert fatigue, Aikido offers a strong starting point.
Want to see how Aikido Security fits into your environment? Start for free or book a demo to explore how it helps teams find and fix real risks faster.

Secure your software now






