Introduction
Choosing the right application security tools can feel like a showdown between very different philosophies. SonarQube and Fortify are two popular options on opposite ends of the spectrum. This comparison breaks down how each fares in practice – and why a newer alternative might just steal the show.
TL;DR
SonarQube and Fortify are legacy tools built for static code analysis, but both come with trade-offs. SonarQube is easier to use but limited in depth, while Fortify offers enterprise-level coverage with a steep learning curve and heavyweight setup. Aikido Security offers a modern alternative: combining deep code analysis with fast setup, minimal false positives, and seamless CI/CD integration—making it a better fit for today’s engineering teams.
Overview of Each Tool
SonarQube
SonarQube is an open-core platform primarily known for static code analysis and code quality inspection. Developers love its slick UI and IDE plugins (SonarLint) that give instant feedback on bugs, code smells, and the occasional security issue. It supports dozens of languages and integrates into CI pipelines with ease. While SonarQube does include security rules (OWASP Top 10, CWE checks, etc.), its heritage is code quality – meaning advanced security testing isn’t its strong suit. Organizations often start with SonarQube for improving code maintainability and gradually “stretch” it into a light SAST tool. This works to a point, but serious AppSec teams often hit SonarQube’s ceiling in terms of deep vulnerability coverage.
Fortify
Fortify (OpenText Fortify, formerly HP/Micro Focus Fortify) is a veteran application security suite built squarely for finding vulnerabilities. Its flagship Static Code Analyzer combs through source code with a fine-toothed comb, using thousands of proprietary rules and dataflow analysis to catch OWASP Top 10 issues and more. Fortify’s approach is comprehensive: it offers not just SAST but also options for Software Composition Analysis (third-party library vulnerabilities) and even Dynamic testing (DAST) as part of its ecosystem. This tool was designed for enterprise security teams – and it shows. Fortify can uncover security problems that simpler tools miss, and it provides in-depth reports and dashboards for governance. However, all that power comes with baggage: Fortify is not trivial to deploy or use day-to-day. Expect a steep learning curve, heavy system requirements, and a workflow geared more toward security auditors than fast-moving dev teams. It’s the archetypal “big enterprise” security scanner – thorough and robust, but often cumbersome.
Feature-by-Feature Comparison
Security Scanning Capabilities
SonarQube performs Static Application Security Testing (SAST) as a subset of its code analysis. It flags common coding flaws and some security hotspots (e.g. SQL injection patterns, XSS) using rule sets mapped to OWASP and CWE. But its security ruleset is fairly basic – limited in depth and coverage compared to dedicated security tools. SonarQube does not natively include dynamic testing or comprehensive software composition analysis, though it may identify a few vulnerable dependencies in reports. Its focus remains on first-party code.
Fortify, on the other hand, is built for security from the ground up. Fortify’s SAST engine performs deep data flow analysis (tracking how data moves through the code) to catch complex vulnerabilities that SonarQube might overlook. It also offers Software Composition Analysis (SCA) to detect vulnerable open-source libraries, and Fortify’s product family includes DAST tools for runtime testing. In short, Fortify aims to cover the whole security scanning spectrum. The trade-off is that Fortify can be overzealous – it will identify every potential unsanitized input or insecure configuration, often flagging edge cases that end up not exploitable. (Yes, it even panics if it sees the word “password” anywhere in your code.) Neither SonarQube nor Fortify significantly tackles new areas like infrastructure-as-code templates or container image scanning – those remain blind spots for both. If you need those scanned, you’ll need an additional tool or a more unified platform (cue Aikido Security).
Integration & DevOps Workflow
When it comes to fitting into a modern DevOps toolchain, SonarQube shines. It was practically made for CI/CD integration – you can run SonarQube analysis as a step in your build pipeline (Jenkins, GitHub Actions, GitLab CI, you name it) with minimal fuss. There are official plugins and easy configs to automatically upload results. SonarQube also has features like Quality Gates to break the build if new code introduces critical issues. And because Sonar started life catering to developers, it offers niceties like branch-by-branch analysis and PR annotations. In short, SonarQube slips into a DevOps workflow almost as easily as a linter or test suite.
Fortify integration is more challenging. Historically, Fortify’s workflow often involved manually running scans and uploading results to its Security Center – not exactly “continuous”. In fact, an early Fortify limitation was the lack of easy pipeline automation (requiring manual file uploads or custom scripting). Nowadays, Fortify can integrate into CI pipelines, but it’s not as plug-and-play. You typically need to install the Fortify scanner, ensure the code is built (Fortify often requires a successful build with all dependencies to analyze properly), then invoke a scan which generates results for upload.
There are plugins for tools like Jenkins now, but expect to spend time configuring them. One user noted that Fortify “needs a build in order to scan” and takes more effort to wire into a pipeline. In summary, Fortify can fit in DevOps, but it doesn’t feel as native to the fast CI/CD cycle as SonarQube does. SonarQube is the easy-going team player here, whereas Fortify might make you jump through a few hoops.
Accuracy and Performance
Accuracy in static analysis has two sides: catching real issues (true positives) and avoiding false alarms. SonarQube tends to err on the side of silence – it finds the low-hanging fruit and avoids overly complex vulnerability analyses, which means it misses some real flaws (false negatives) but in turn doesn’t cry wolf too often. Many devs appreciate that “SonarQube…does a nice job of not throwing false positives”, sparing developers from chasing ghosts. Fortify is the polar opposite. It throws a wide net to catch every conceivable issue, resulting in a noisy output. It’s not unusual for Fortify to report thousands of findings in a large codebase, of which only a handful are truly critical problems. Teams often spend significant time triaging Fortify results, weeding out false positives or minor issues.
One experienced user bluntly noted that with Fortify “the tool is very noisy” and you must learn which findings to actually “trust”. This high false-positive rate can lead to alert fatigue – developers start ignoring Fortify or pushing the scanning to later in the release cycle.
In terms of performance, scan speed is another consideration. SonarQube is relatively lightweight; a scan is fast enough to run on every commit or pull request (often completing in a few minutes for moderate projects). Fortify scans, in contrast, are heavyweight. Large projects can take hours to scan with Fortify if not tuned properly. The Fortify SCA engine does deep analysis and can consume lots of memory and CPU, so you often have to allocate a beefy server for it. It’s telling that some organizations only run Fortify scans nightly or at the end of sprints, rather than with each commit – continuous scanning can be impractical if each run is slow. In summary, SonarQube is nimble and conservative (fewer but mostly relevant findings), whereas Fortify is thorough but heavy, generating a firehose of results that require horsepower (and discernment) to manage.
Coverage and Scope
Language and framework support: Both tools support a wide array of programming languages, but SonarQube holds an edge in breadth. SonarQube (especially in its commercial editions) covers ~30+ languages, including popular ones like Java, C#, Python, JavaScript/TypeScript, C/C++, and even more niche ones via plugins. Fortify’s language support is extensive for an enterprise SAST (Java, C/C++, C#, Python, JavaScript, Ruby, Go, PHP, and more, even IBM Mainframe languages in some editions), but users report that Fortify actually supports fewer languages than SonarQube in practice. For example, SonarQube has community or official analyzers for things like Swift, Kotlin, Apex, PL/SQL, etc., whereas Fortify might not cover all of those out of the box. If your tech stack is polyglot, check Fortify’s language compatibility closely – SonarQube could have the upper hand in eclectic environments.
Application scope: SonarQube’s scanning is scoped to source code and related test coverage/quality metrics. It doesn’t analyze your running apps or configs. Fortify’s scope is broader in the AppSec sense – Fortify can scan binaries and configuration files and, via its extended products, handle things like mobile app scanning or runtime tests. Still, both focus primarily on the application layer (code and dependencies). Neither SonarQube nor Fortify will scan your cloud infrastructure templates, Kubernetes manifests, container images, or API endpoints for you. That means gaps in cloud-native coverage – e.g., a hardcoded secret in a Terraform script or a CVE in your Docker base image won’t be caught by either tool. Covering those requires additional tools or a platform designed for unified coverage.
This is a key area where a platform like Aikido Security (which scans code, cloud configs, containers, and more) aims to fill the void. In terms of compliance standards coverage, both SonarQube and Fortify map findings to common frameworks (OWASP Top 10, CWE, PCI-DSS, etc.), with Fortify historically being used to satisfy corporate compliance mandates more often. But raw coverage of modern app surfaces (SaaS, serverless, cloud infra) is limited in both legacy tools.
Developer Experience (UX, Setup, Learning Curve)
Here’s where the philosophical differences really surface. SonarQube positions itself as a tool for developers. Its UI is clean and approachable: issues are shown in the context of code, with clear remediation guidance. Developers can click an issue and see the highlighted flawed code and a suggestion. The learning curve for SonarQube is shallow – if you understand your language’s coding standards, Sonar’s interface will feel intuitive. Setting up SonarQube (especially using SonarCloud or the Community Edition server) is straightforward, and there’s a huge community if you need help.
Crucially, SonarQube integrates into developer workflows: IDE plugins for on-the-fly analysis, PR decoration to point out new issues in code reviews, and so on. As a result, devs tend to embrace SonarQube rather than resent it. One team noted they “quite like the user experience” of SonarQube and how SonarLint gives instant feedback in the IDE. That instant, continuous feedback makes SonarQube feel like part of the dev toolkit, not an external auditor.
Fortify, conversely, feels more like a traditional security appliance. Its primary interface, Fortify SSC (Software Security Center), is powerful but complex. There’s also Fortify’s Audit Workbench, a desktop GUI for security auditors to review findings. New users often find these interfaces overwhelming – they’re packed with vulnerability data, filters, and terminologies that assume a security background. The learning curve is steep; as one Fortify user put it, “It will take a while to understand the tool… The tool is very noisy… You need a lot of patience to use the tool.”. Developers without security training might struggle to interpret Fortify’s results (e.g., understanding dataflow graphs or why something tagged “High Risk” truly is or isn’t a concern).
In many organizations, Fortify results are handled by a separate security team who then assigns issues to developers – an approach that can create friction. Moreover, setup and maintenance of Fortify is a project in itself. Installing the Fortify server, configuring authentication, updating rulepacks regularly, ensuring the scanning environment has all the build dependencies… it’s a lot. Indeed, Fortify’s own documentation and users echo that it “requires a lot of setup and a lot of thought to use… effectively”. In short, Fortify’s UX is geared toward the dedicated security specialist, whereas SonarQube’s UX is geared toward everyday developers. For a technical leader, this difference means Fortify might demand more training, more process changes, and perhaps dedicated personnel to manage, while SonarQube can be handed to dev teams with minimal fuss.
Pricing and Maintenance
The cost factor is often a deal-breaker. SonarQube offers a huge advantage here: it has a free Community Edition which, while limited in security rules and languages, is often enough to get started. The paid editions (Developer, Enterprise, Data Center) expand language support and security analysis capabilities, and pricing is generally based on lines of code analyzed. SonarSource publishes pricing openly (transparent tiers by LOC), which makes it easier to predict costs. For example, SonarQube Enterprise might cost in the low tens of thousands per year for a mid-sized codebase – not cheap, but often still less expensive than Fortify for similar scope. And if your team or budget is small, you can start with free SonarQube or the affordable Developer edition. Maintenance for SonarQube (self-hosted) is relatively low-effort: it’s a Java server that you update occasionally, and Sonar provides regular updates and LTS releases. If using SonarCloud (their SaaS), infrastructure maintenance is zero.
Fortify, in contrast, is known for its hefty price tag. As an enterprise solution, Fortify licenses can run into the high five or six figures annually for large organizations. There’s no free tier – you’re paying for the full package, even if you only need SAST. One source explicitly notes that Fortify is “expensive for enterprise-level usage”. Pricing isn’t public; it usually involves custom quotes and negotiations (so much for transparency). Beyond licensing, consider the total cost of ownership: Fortify may require dedicated hardware or VMs for the scan engine and Security Center, plus time from engineers to maintain it. Rulepack updates and new version upgrades must be applied a few times a year (often tied to your support contract). If you lapse on support, you might miss critical rule updates for new vulnerabilities.
All of this adds up to more $$$ and time. It’s telling that one reviewer quipped you need “a lot of money and a lot of patience” to effectively use Fortify. In short, SonarQube is cost-effective and straightforward to budget, while Fortify demands a serious financial commitment and ongoing investment in maintenance. (And if you’ve ever tried to ask “how much does Fortify cost?”, you’ve likely been met with a sales pitch rather than a number.)
Aikido offers a simpler, more transparent pricing model – flat and predictable – and is significantly more affordable at scale than either Snyk or SonarQube.
Compliance and Innovation
Fortify and SonarQube often appeal to different stakeholders. If you’re looking to satisfy a compliance checklist or impress an auditor, Fortify’s reports and certifications have clout. Fortify has been a staple in Gartner Magic Quadrants and is frequently used in industries with heavy regulations. It offers detailed compliance reporting (for example, mapping every finding to standards like OWASP, PCI DSS, CWE/SANS, etc.), which can help in audits. SonarQube, while it can map issues to OWASP Top 10 and other standards, is not traditionally seen as a “compliance tool” – it’s more about continuous improvement. That said, SonarQube Enterprise does include security reports for compliance purposes, and many companies use it to track OWASP Top 10 adherence over time.
In terms of innovation and staying current: SonarQube, backed by SonarSource and an open-source community, evolves rapidly with new language support, developer-centric features, and UI improvements. Fortify’s pace has been slower. In fact, some users have observed that Fortify hasn’t kept up with newer trends and developer expectations in recent years. After changing hands from HP to Micro Focus to OpenText, Fortify’s roadmap might prioritize stability for existing enterprise customers over cutting-edge features. For example, modern developer desires like a slick IDE integration or support for scanning IaC/containers came to Fortify very late or not at all.
SonarQube, meanwhile, introduced features like “Security Hotspots” (to involve developers in security review) and keeps refining its developer workflow integration. Neither tool is extremely “innovative” in 2025 by startup standards, but SonarQube feels more aligned with modern DevSecOps practices, whereas Fortify feels, well, a bit legacy in approach. The good news is both tools are mature and dependable; the bad news is neither will single-handedly address emerging security domains outside of code. This is where looking at newer solutions can pay off.
Pros and Cons of Each Tool
SonarQube – Pros:
- Developer-Friendly: Simple UI and workflow; easy for devs to adopt with minimal training.
- Easy Integration: Hooks seamlessly into CI pipelines and dev tools (IDE plugins, PR decoration) – fosters a true DevSecOps culture.
- Code Quality + Security: Combines code quality metrics with security analysis, giving a holistic view (one tool instead of two for quality and basic security).
- Cost-Effective: Open-source core with free tier; paid plans are transparent and generally cheaper than enterprise SAST suites.
SonarQube – Cons:
- Limited Security Depth: Not a dedicated security tool – misses many serious vulns that specialized SAST would catch (high false negatives).
- False Negatives over False Positives: Tends to quietly skip tricky vulnerabilities rather than flag them – you’ll need additional tools to catch what SonarQube doesn’t see.
- Advanced Features Require Paid Version: Key security features (taint analysis, injection detection) and more language support are only in Developer/Enterprise editions.
- Narrow Scope: Focuses on code and doesn’t cover app security beyond static analysis (no built-in dependency scanning or runtime testing).
Fortify – Pros:
- Thorough Security Scanning: Industry-leading depth in static analysis – catches complex vulnerabilities and covers OWASP Top 10, SANS 25, and more out-of-the-box.
- Extensive Rule Set: Decades of development have yielded a huge set of rules and checks (including custom rules capability) to find security issues in many languages and frameworks.
- Comprehensive AppSec Suite: Options to include SAST, DAST, SCA under one umbrella. Fortify can be a one-stop-shop for multiple AppSec activities (e.g. scan code and third-party libs together).
- Enterprise Reporting & Compliance: Detailed reports, dashboards, and compliance mappings suitable for management and auditors. Helps demonstrate due diligence and track risk over time.
Fortify – Cons:
- High False Positives (Noisy): Generates a ton of alerts – many are informational or not actually exploitable. Teams often struggle with the signal-to-noise ratio (time-consuming triage).
- Complex Setup & Use: Steep learning curve and configuration burden. Requires a dedicated effort to deploy, maintain, and tune (not plug-and-play).
- Developer Unfriendly: Feels like a heavyweight security tool – developers may find the interface and results overwhelming, leading to adoption friction. Lacks the “instant feedback” vibe that devs get from tools like SonarQube.
- Expensive: License and infrastructure costs are significant for Fortify. Often only large enterprises can afford it, and even then the ROI can be questioned if most findings are false positives.
Aikido Security: The Better Alternative
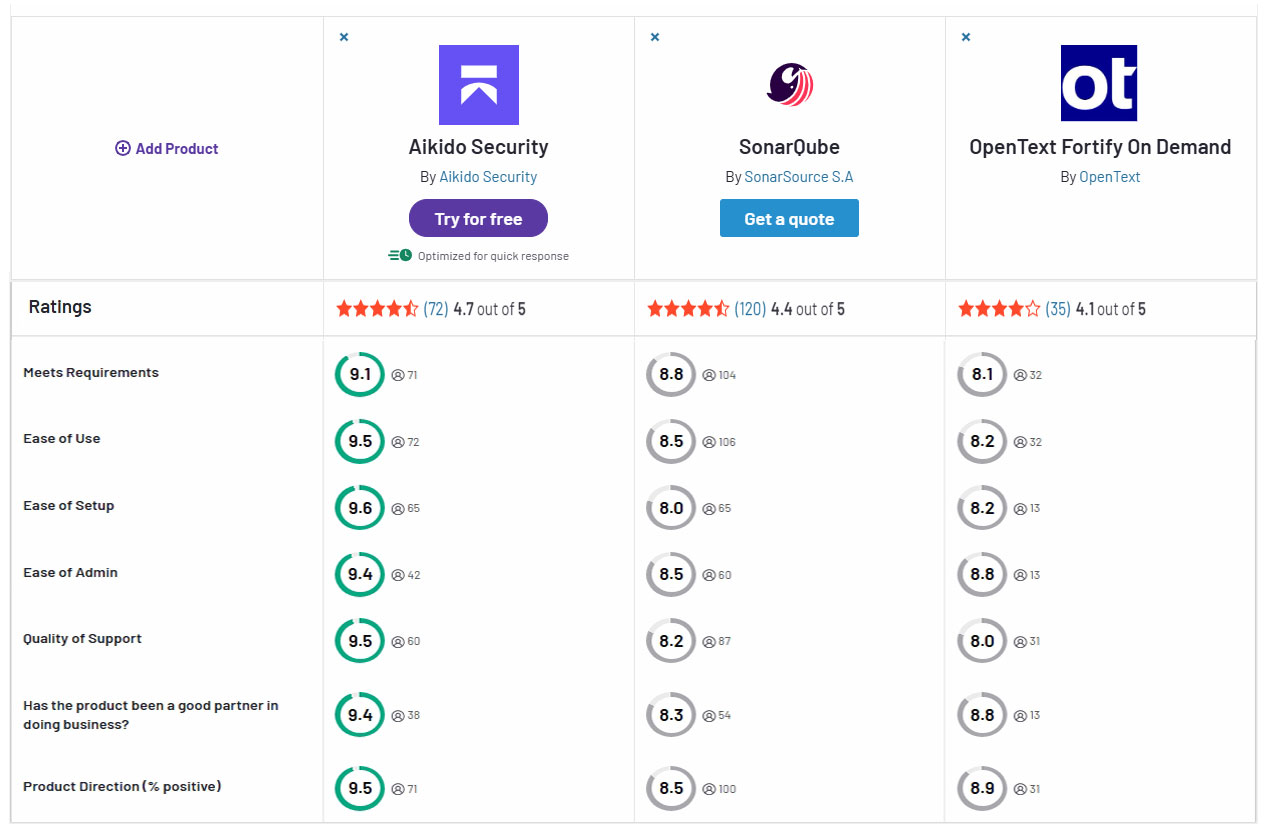
Aikido Security is a modern platform that emerged to address exactly the pain points noted above. Think of Aikido as taking the best of both worlds: it provides comprehensive coverage across your code, open-source dependencies, cloud configs, and more – yet it’s built in a developer-first way with simplicity in mind. Aikido’s static analysis uses smart algorithms to drastically reduce noise (up to 85% fewer false positives compared to legacy tools). This means developers trust the findings and don’t waste time on phantom issues. Integration-wise, Aikido plugs into CI/CD pipelines and developer workflows with minimal fuss (setup takes minutes, not weeks). No bulky installations or convoluted processes – it’s security that “just works” alongside your existing dev tools.
Aikido’s coverage is broader than SonarQube or Fortify alone, catching vulnerabilities in source code, dependencies, infrastructure-as-code, containers, and even secrets, all in one unified dashboard. Crucially, the pricing is transparent and flat – no per-project surprise fees or six-figure enterprise hurdles. In short, Aikido Security offers a no-nonsense approach to AppSec: robust protection with fewer false alarms, easy integration, and honest pricing. For a technical leader tired of the SonarQube vs Fortify trade-offs, Aikido might just be the “aikido move” that turns your AppSec program into a win-win for both security and development teams.
Start a free Trial or request a demo to explore the full solution.



