Introduction
As a technical leader responsible for software security, choosing the right code analysis tool is critical. SonarQube and Coverity are two popular platforms that help teams find bugs and vulnerabilities early. In this comparison, we’ll see how each tool impacts your development workflow and security outcomes – and why those differences matter for your team.
TL;DR – Different Focus, Common Blind Spots (and Why Aikido Wins)
SonarQube and Coverity both help secure your codebase, but they focus on different priorities – and each has blind spots. SonarQube shines in broad code quality scanning (covering many languages with easy pipeline integration) but its built-in security rules are limited. Coverity specializes in deep static analysis for critical code defects with fewer false alarms, yet it’s an on-premise heavyweight that can be costly and harder to integrate. Neither tool covers open-source dependencies or container vulnerabilities, leaving gaps in coverage.
Aikido Security brings both worlds together in one platform – covering your custom code and third-party components – with fewer false positives and simpler integration, making it the better choice for modern dev-security teams.
SonarQube Overview
SonarQube is an open-source (with paid tiers) platform for static code analysis and code quality management. Developers use SonarQube to continuously inspect code for bugs, code smells, and some security vulnerabilities across a wide range of languages. The tool emphasizes maintainability and overall code health: it highlights duplications, complexity, and test coverage alongside potential security issues. SonarQube integrates smoothly into build pipelines and version control workflows, giving teams a developer-friendly way to enforce coding standards and improve code quality. Its core strength is a broad rule set for clean code, although truly advanced security analysis often requires extending SonarQube or using its paid edition.
Coverity Overview
Coverity (by Synopsys) is a commercial static analysis tool geared towards finding critical software defects and security vulnerabilities. It performs a deep SAST analysis of source code, following execution paths to catch issues like memory leaks, null pointer dereferences, concurrency bugs, and other hard-to-find errors. Coverity’s focus is on accuracy and depth – it’s known to flag complex vulnerabilities with a low rate of false positives. This tool is favored in high-assurance and enterprise environments, offering compliance checks for industry standards and safety-critical code. However, Coverity supports a more limited set of programming languages compared to SonarQube (primarily C/C++, C#, Java and a handful of others). It’s also a proprietary on-premise solution, which means you get robust analysis and enterprise support at the cost of managing infrastructure and a higher price tag.
Security Scanning Capabilities
Core Approach: Both SonarQube and Coverity are primarily static application security testing (SAST) tools focused on analyzing source code for issues. SonarQube concentrates on code quality issues and certain security hotspots – for example, it might detect common injection flaws or weak cryptography usage in code. Its ruleset, especially in the free Community Edition, leans toward maintainability and style checks (code smells) with only basic security coverage.
You can extend SonarQube with additional plugins or custom rules for more security, but out-of-the-box it’s not a dedicated security scanner. Coverity, on the other hand, is designed from the ground up for finding defects and vulnerabilities. It performs interprocedural analysis (following code paths across functions) to catch issues that simpler linters or pattern-based tools might miss. Coverity comes with a large set of built-in checks covering both coding bugs and security flaws, and it maps findings to standards like OWASP Top 10 and CWE by default.
Blind Spots: Neither SonarQube nor Coverity extends beyond source code analysis. Open-source dependency scanning (SCA) is essentially absent in both – they won’t alert you if your project includes a library with known CVEs. Container or environment scanning is also outside their scope. This means if you rely on either tool alone, vulnerabilities in third-party packages or deployment configurations can slip through unnoticed.
Modern DevSecOps programs often need separate tools for SCA and container security to fill this gap. In short, SonarQube and Coverity each cover static code analysis in different flavors (general code health vs. in-depth security defects) but leave significant gaps when it comes to open-source and runtime security coverage.
Integration and DevOps Workflow
How well a tool fits into your development workflow is a make-or-break factor for adoption. SonarQube excels in integration flexibility. It offers official plugins for build systems (Maven, Gradle, MSBuild) and CI/CD platforms like Jenkins, GitHub Actions, GitLab CI, and Azure Pipelines. Setting up SonarQube scans is straightforward – a one-liner with the Sonar Scanner CLI can hook analysis into your pipeline. SonarQube also integrates with developer IDEs through SonarLint, giving instant feedback in VS Code, IntelliJ, Eclipse, etc.
The platform supports pull request decoration, so issues can show up directly in code reviews on GitHub/GitLab. This frictionless integration means developers see SonarQube as part of the normal development cycle, not a separate siloed process.
By contrast, Coverity tends to be more heavyweight to integrate. It’s primarily an on-premise tool (though Synopsys offers it as part of a platform in some cases), and it doesn’t have the same breadth of out-of-the-box integrations. Teams usually integrate Coverity by adding its analysis commands into the build process (using a Coverity build wrapper and analysis step), then uploading results to a Coverity server for viewing. It can connect with issue trackers like Jira for bug filing, and some CI systems can be scripted to fail builds on high-severity findings.
However, this setup requires more manual effort and maintenance compared to SonarQube’s plugin ecosystem. Coverity’s lack of a cloud-based offering means you manage the server, database, and updates yourself, which can be a hurdle for lean teams. In summary, SonarQube fits smoothly into modern DevOps workflows with minimal fuss, while Coverity may demand more custom integration and upkeep to achieve the same level of automation.
Accuracy and False Positives
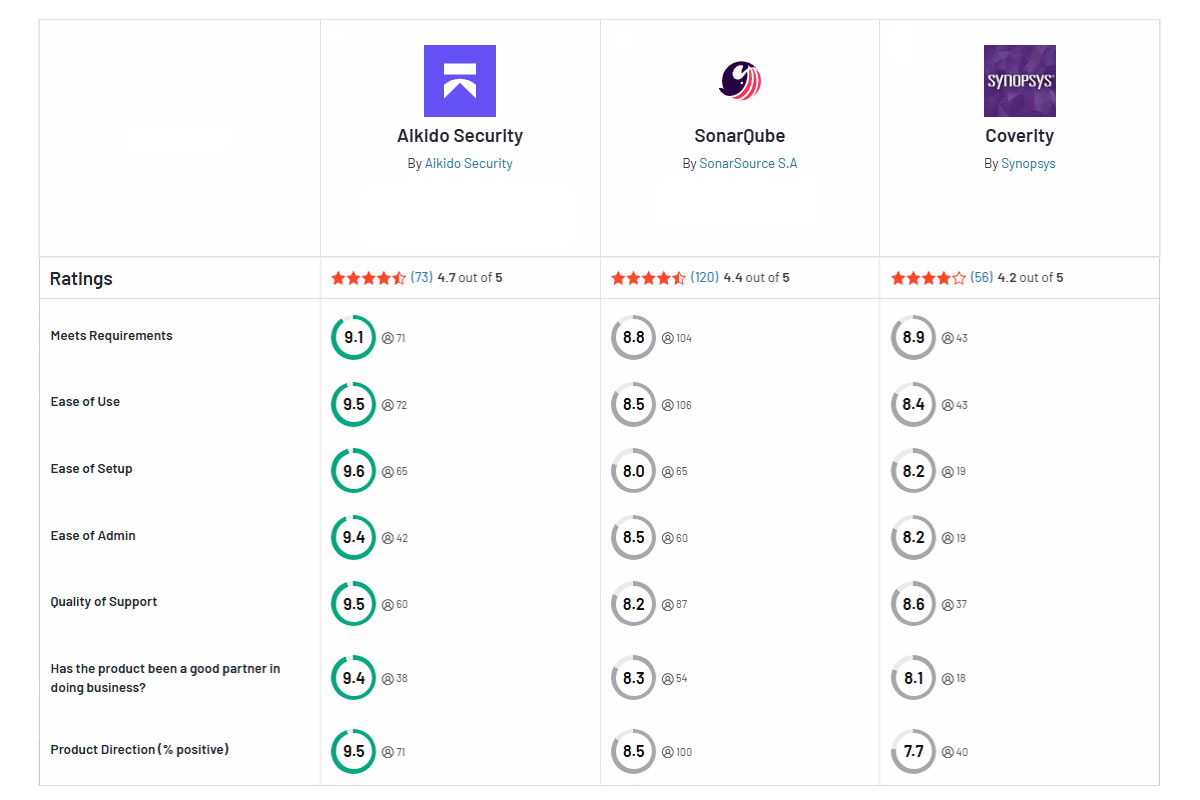
When it comes to alert accuracy, Coverity has a strong reputation. Users often praise Coverity for finding real, critical issues and minimizing noise. In practice, Coverity’s static analysis yields very few false positives – one user noted that “most vulnerabilities it identifies are genuine”. This high signal-to-noise ratio means developers and security teams can trust Coverity’s findings and spend less time wading through irrelevant alerts.
Coverity’s thorough analysis (e.g. tracking null pointer paths or buffer usage) is tuned to avoid reporting something unless it’s likely a real problem, which is a big plus in enterprise environments where false positives can waste significant developer time.
SonarQube, on the other hand, casts a wider net by design. It will flag a broad array of code issues – including minor maintainability concerns – so not everything it reports is a serious “vulnerability.” Many findings are low-priority code smells or style issues that, while useful for code quality, might be considered noise from a pure security standpoint.
SonarQube does allow marking issues as false positive or “won’t fix,” and its recent editions have improved the precision of security rules, but it still tends to over-report in the eyes of some developers. For example, if you enable all rules, SonarQube might raise dozens of styling or naming warnings that don’t truly affect security or function. The key is tuning Sonar’s rule set to your needs – but that tuning takes time, and until then developers might experience alert fatigue.
In terms of performance, SonarQube is generally fast enough to run on every build or pull request for most projects. Its analysis is optimized for incremental scanning (focusing on new/changed code on PRs), which means it can give near-real-time feedback. Coverity’s deep analysis can be more resource-intensive; initial scans of large codebases might take significantly longer. Coverity can be run incrementally as well, but teams sometimes opt to run it nightly or on a separate schedule due to the heavier workload. To Coverity’s credit, it’s built to handle enterprise-scale codebases and can be configured to distribute analysis tasks – but expect to allocate server horsepower for it.
SonarQube is also capable of handling large projects, but its lighter-weight nature makes it a bit more CI-friendly out of the box. In summary, SonarQube provides quick feedback with a higher volume of trivial alerts, whereas Coverity delivers meticulous results with very few false positives (at the expense of more computing resources and setup).
Coverage and Scope of Issues
Language Support: One of SonarQube’s biggest advantages is its broad language coverage. It supports 25+ languages (over 30 if you count community plugins), from mainstream ones like Java, C#, JavaScript, and Python to niche languages like Apex, PL/SQL, and COBOL. This makes SonarQube a versatile choice for polyglot environments or varied codebases. Coverity, in comparison, supports fewer languages out-of-the-box – traditionally focusing on C, C++, C#, and Java, with some support for others like JavaScript, Python, or Ruby in recent versions. (Coverity documentation cites support for around 22 languages, which is solid but still narrower than SonarQube.)
If your stack includes an uncommon language or a lot of front-end frameworks, SonarQube is more likely to handle it. Coverity sticks to what’s common in enterprise back-end and systems programming.
Types of Issues: The scope of what each tool checks also differs. SonarQube provides a holistic view of code quality. It doesn’t just find bugs; it also measures duplications, code complexity, coding style violations, and even tracks test coverage (when fed reports). This gives development leaders a broad picture of code health and technical debt. Sonar’s security rules (especially in paid versions) do include taint-analysis for things like SQL injection, XSS, and other OWASP Top 10 issues, but a large portion of Sonar’s default rules relate to maintainability and reliability rather than security alone.
Coverity is more laser-focused on catching defects and vulnerabilities. Its checkers cover CWE categories, buffer overflows, race conditions, API misuse, etc., and less about whether your code follows a naming convention or has high cyclomatic complexity. Notably, Coverity shines for compliance needs: it can enforce MISRA and other safety standards, and it’s used in industries where adhering to regulatory coding standards is a must. In fact, Coverity explicitly covers frameworks like OWASP Top 10 and CWE Top 25 and even maps to compliance regimes like HIPAA or GDPR for security/privacy best practices.
SonarQube does let you set up quality gates and can be configured for standards (and has some OWASP mapping for security rules), but it’s not as out-of-the-box compliance-oriented.
Beyond Code: As mentioned earlier, both tools largely stick to static code analysis. If you need Infrastructure as Code (IaC) checks (for Terraform, Kubernetes manifests, etc.) or secret detection, those would require separate tools or plugins. Similarly, neither SonarQube nor Coverity will natively check if your dependencies have known vulnerabilities – that’s the domain of SCA tools (though SonarQube can integrate with OWASP Dependency-Check or others as an additional step).
A technical leader should be aware that using SonarQube or Coverity alone won’t cover everything; you may need to augment them to achieve full coverage across the SDLC.
Developer Experience and Adoption
A security tool is only as good as its adoption by the dev team. SonarQube has an edge in being developer-friendly and accessible. Its UI is modern and straightforward – developers get a web dashboard showing issues with context, and they can drill down to see the highlighted problematic code snippet and remediation guidance. Thanks to SonarQube’s large community, there are plenty of guides, Stack Overflow answers, and community plugins to tailor it to your team’s needs.
The learning curve for SonarQube is relatively low: developers often grasp the interface and start fixing issues on day one. And because SonarQube flags maintainability issues too, devs might see it as a helpful assistant for code quality, not just a security nag.
Coverity is a more specialized tool and that shows in the developer experience. Its interface (Coverity Connect) provides detailed defect reports, including tracing the path in code where the issue occurs. This is great for an expert user who wants deep insight, but new developers might find the interface less intuitive or a bit dated. Some reviews note that Coverity’s UI could be improved for usability. Setting up Coverity analysis requires understanding your build system deeply (to make sure Coverity captures the correct compilation units), which can be a hurdle for developers during initial adoption.
On the flip side, once integrated, developers do benefit from the accuracy – they’re not chasing false alarms, so the issues Coverity does show are typically worth attention. Coverity also has features to mark false positives or filter results, and because it’s often used in strict environments, developers might have less leeway to ignore it (management will insist critical Coverity findings get fixed).
In terms of workflow, SonarQube’s presence in PRs and IDEs makes it a constant companion to coding. It nudges devs to clean up code as they write it. Coverity tends to function a bit more in the background – perhaps running nightly or as a separate step – with results that might be reviewed in batches. This could mean that unless there’s a champion on the team enforcing Coverity findings, devs might not look at them until just before a release or during a security review.
There’s also the matter of accessibility: anyone can download SonarQube Community Edition or use SonarCloud with a few clicks, which encourages experimentation and developer buy-in. Coverity, being enterprise software, usually involves procurement or at least a trial license and a heavier installation. That higher barrier can dampen organic adoption by developers.
In summary, for developer experience, SonarQube feels like a natural extension of the development process with a low barrier to entry and lots of community support. Coverity is powerful but more top-down – often introduced by mandate for its proven benefits, but requiring a bit more training and effort before developers are comfortable with it.
If your team is allergic to complicated tools or prone to ignore external feedback, SonarQube might see better uptake. If you have a mission-critical project where developers understand the need for thorough analysis (and have the patience for it), Coverity’s detailed feedback will be appreciated.
Pricing and Maintenance Considerations
Budget and maintenance effort are significant factors for any tech leader comparing tools. SonarQube offers a clear upside here, at least to start: it has a free Community Edition which many teams use without paying a dime. This free tier, however, lacks some security rules and support for certain languages (e.g., scanning C/C++ or Objective-C requires a paid Developer Edition). For full enterprise features (like portfolio management, advanced reporting, additional security hotpots, etc.), SonarQube’s pricing is typically based on the number of lines of code analyzed.
The cost can grow as your codebase grows, but it’s still often seen as cost-effective, especially for smaller teams. SonarQube can be self-hosted easily on a modest server for small projects, and SonarSource also offers SonarCloud (a cloud SaaS version) with subscription plans – this offloads the maintenance to SonarSource and charges by the code size and number of analyses.
Coverity, being a commercial enterprise tool, comes with a higher price tag. Its licensing is often quote-based, tailored to an organization’s size. Common models involve paying per user seat or per volume of code (e.g., per million lines of code analyzed), and it can become very expensive for large codebases. One PeerSpot reviewer rated Coverity’s price “a ten out of ten” on the expense scale – meaning it’s at the high end. There’s no free edition of Coverity for commercial use (Coverity Scan is a free service, but only for qualifying open-source projects).
Budget-conscious teams often find Coverity cost-prohibitive unless the need is critical. Maintenance-wise, using Coverity means you will likely maintain a dedicated server or cluster to run scans and host the results, and you’ll need to install updates from Synopsys periodically. That’s an ongoing operational overhead – whereas with SonarQube you have the choice to self-host (with similar maintenance effort) or go cloud (maintenance-free).
It’s worth noting that both tools can provide good ROI by preventing costly defects and security incidents. SonarQube’s value can often be realized even in its free form for many code quality improvements. Coverity’s value justifies itself for organizations that absolutely need its deep analysis (think aerospace, medical, or large enterprise software with millions of users). For a modern agile team, though, the combination of high cost and upkeep might tilt favor towards lighter solutions unless the risk landscape demands Coverity’s level of scrutiny.
Aikido Security offers a simpler alternative on this front as well – with a transparent, flat pricing model that doesn’t penalize you for growing. Unlike SonarQube or Coverity which can become pricier as you add code or users, Aikido’s pricing is predictable and often significantly more affordable at scale. This means you can cover all your repositories and developers without tough decisions about which code to scan to stay under a limit. In terms of maintenance, Aikido is provided as a cloud-native platform, so your team spends zero time on server upkeep or manual updates. (We’ll dive more into Aikido next.)
Pros and Cons of SonarQube and Coverity
SonarQube Pros:
- Broad language support and rule set: Works with dozens of languages and has a vast plugin ecosystem, making it useful across diverse projects.
- Easy integration: Simple to set up in CI/CD and available as a cloud service. Also offers IDE integration (SonarLint) for instant feedback.
- Developer-friendly UI: Clear web interface with actionable issue descriptions and a community of users for support.
- Quality beyond security: Helps enforce coding standards, reduce tech debt (bugs, duplicates, complexity), and improve overall code quality – not just find security flaws.
- Affordable (even free to start): Community Edition is free. Paid plans scale based on code size, which is cost-effective for many teams.
SonarQube Cons:
- Limited deep security analysis: Focuses on code quality; may miss certain vulnerability patterns that specialized security tools catch.
- Noise from minor issues: Tends to report many “code smell” warnings. Without tuning, teams can get flooded with low-priority alerts, which can distract from critical issues.
- Advanced features require paid tier: Key security rules (especially for C/C++ or advanced taint analysis) and enterprise features are behind a paywall.
- Self-hosting overhead: Running SonarQube on-premises means maintaining a server and database. Large-scale usage may require significant infrastructure, unless using SonarCloud.
- No native open-source scanning: Does not check your third-party dependencies or container images for vulnerabilities – you’ll need additional tools for full coverage.

Coverity Pros:
- High accuracy static analysis: Excellent at identifying real defects and security vulnerabilities with very few false positives. Engineers can trust that a Coverity finding is likely a legit issue.
- Deep vulnerability detection: Finds complex issues (e.g., concurrency bugs, memory corruptions) that simpler linters often overlook. Great for mission-critical, safety, or compliance-focused code.
- Compliance and standards support: Coverity covers OWASP Top 10 and CWE and can enforce industry coding standards (MISRA, DISA STIG, etc.), helping with regulatory compliance.
- Scalable for enterprise: Built to handle large codebases and enterprise workflows, with features like incremental analysis and integration into issue trackers and DevOps pipelines.
- Enterprise support: As a commercial tool, it comes with vendor support, detailed documentation, and assistance options – important for organizations that need guaranteed help.
Coverity Cons:
- Very expensive for teams at scale: Licensing costs (often per lines of code or user) are high. This can put it out of reach for smaller companies or force tough choices on what to scan.
- Setup and maintenance burden: Requires installing and maintaining an on-premise server (or using Synopsys’s managed services). Integration into builds is manual and can be time-consuming to configure.
- Less flexible integration: Lacks the out-of-the-box plugins and cloud integrations that tools like SonarQube have. Adapting Coverity to your workflow might need custom scripts or adjustments.
- Limited language support: Not as broad in language and framework coverage as SonarQube. Teams using niche or newer languages/technologies might find Coverity doesn’t support them.
- Narrow focus: Concentrates on code issues only – no built-in open source dependency scanning, container analysis, or dynamic testing capabilities. You’ll still need other tools to cover those areas.
Aikido Security: The Better Alternative
Aikido Security is a modern solution that combines the strengths of both SonarQube and Coverity without their drawbacks. It’s a unified platform that performs static code analysis and scans your open-source dependencies and containers, all in one go. In practice, this means Aikido catches vulnerabilities in your custom code and in the libraries you use – covering the blind spots that SonarQube and Coverity leave. The platform is built with a developer-first mindset: integration is straightforward (just a few clicks to connect to your repo or CI, no heavy setup), and the results are presented with clear, no-nonsense guidance.
Aikido’s smart risk engine prioritizes findings so you deal with the truly important issues, minimizing security-conscious engineering teams who refuse to trade agility for security. And unlike traditional enterprise tools, Aikido doesn’t believe in gatekeeping features behind complex pay models – it offers transparent, flat pricing that’s predictable as you scale, with significantly lower total cost at large team sizes. In short, Aikido brings both worlds together in one powerful yet easy-to-use platform, making it a superior choice for today’s security-conscious engineering teams who refuse to trade agility for security.
Start a free Trial or request a demo to explore the full solution.



