Introduction
SonarQube and Codacy are popular tools for ensuring code quality and security, but they take different approaches. For a technical leader, choosing between them can impact development speed and security outcomes. This comparison looks at SonarQube vs Codacy from a software security perspective – highlighting the differences that matter for keeping your code safe and your developers productive.
TL;DR
SonarQube and Codacy both help improve code security and quality, but each has blind spots. SonarQube shines in static code analysis but lacks broader vulnerability coverage. Aikido Security is the better alternative. Codacy adds open-source risk scanning, but can still fall short on runtime security. Aikido Security brings both worlds together in one platform – combining code analysis with open-source and container security – while delivering fewer false positives and smoother integration. In short, Aikido covers what SonarQube and Codacy miss, making it the superior choice for modern DevSecOps teams.
Overview of Each Tool
SonarQube: SonarQube is a longstanding static code analysis platform that provides an “overall health” check of your source code. It detects coding errors, bugs, and code smells to maintain quality, and flags some security vulnerabilities (e.g. SQL injection patterns or hard-coded secrets) as Security Hotspots. SonarQube also measures code duplication, complexity, and test coverage, enforcing quality gates on these metrics. While it includes OWASP Top 10 and CWE issue mapping for code vulnerabilities, SonarQube focuses primarily on your own source code. Using it usually requires setting up a server or using SonarCloud SaaS to analyze code in your CI pipeline.
Codacy: Codacy is a developer-friendly code quality platform that automates code reviews for both quality issues and security concerns. It supports over 40 languages and frameworks, detecting everything from style violations and code smells to known vulnerability patterns (OWASP Top 10) in code. In addition to static analysis (SAST), Codacy’s offering includes Supply Chain Security (SCA) for open-source library vulnerabilities, secret detection, and even Infrastructure-as-Code scanning for misconfigurations.
Recently, Codacy integrated dynamic analysis (DAST) via OWASP ZAP to catch runtime web app issues. The platform is designed for easy integration into development workflows – it’s cloud-based with minimal setup, provides results on pull requests, and even offers IDE plugins for developers. Overall, Codacy’s strength is offering comprehensive code scanning out-of-the-box with little configuration, aiming to improve code security without slowing developers down.
Feature-by-Feature Comparison
Core Security Capabilities
- SonarQube: Focuses on Static Application Security Testing (SAST) of your custom code. It will catch issues like SQL injection vulnerabilities, hard-coded passwords, or insecure configs in code, using pattern rules and taint analysis. However, SonarQube does not scan third-party libraries for known CVEs (no built-in SCA for dependency vulnerabilities). It also doesn’t include runtime security testing – there’s no container image scanning or dynamic testing in SonarQube. In summary: SonarQube helps clean up your code’s security flaws, but it won’t tell you if your application dependencies or containers have known risks. (Note: Sonar’s paid editions have added SCA for dependencies and IaC/security scanning, but these are not part of the core Community feature set.)
- Codacy: Takes a more holistic approach to application security. It includes SAST rules (spotting vulnerable code patterns and mistakes) and also integrates Supply Chain Security scanning – monitoring your open-source packages for known vulnerabilities. Codacy will alert you if a dependency has a CVE, which SonarQube by itself would miss. It also performs Secrets detection (e.g. API keys in code) and IaC configuration checks (scanning Terraform, CloudFormation, Kubernetes manifests for insecure settings). Uniquely, Codacy can incorporate DAST results by integrating with OWASP ZAP, so you can view dynamic test findings in the same dashboard. Neither SonarQube nor Codacy handle container image scanning (that remains a gap to fill with other tools). Overall, Codacy covers a broader security surface area out-of-the-box than SonarQube, giving you a more 360° view of risks in code and dependencies.
Integration & CI/CD
- SonarQube: Designed to integrate into your build pipelines and DevOps tools, but it requires some elbow grease. You need to host a SonarQube server (or use the SonarCloud service) and wire it into your CI/CD process to run scans on each commit or pull request. Initial setup and config can be complex – a headache for new teams, involving database config, CI script changes, and managing credentials/APIs. Once up and running, SonarQube does integrate nicely: it can annotate pull requests with issues and show quality gate status in tools like GitHub or Jenkins. There’s also SonarLint IDE plugins for pre-commit scanning. Still, compared to Codacy, getting SonarQube fully integrated requires more maintenance and self-hosting effort.
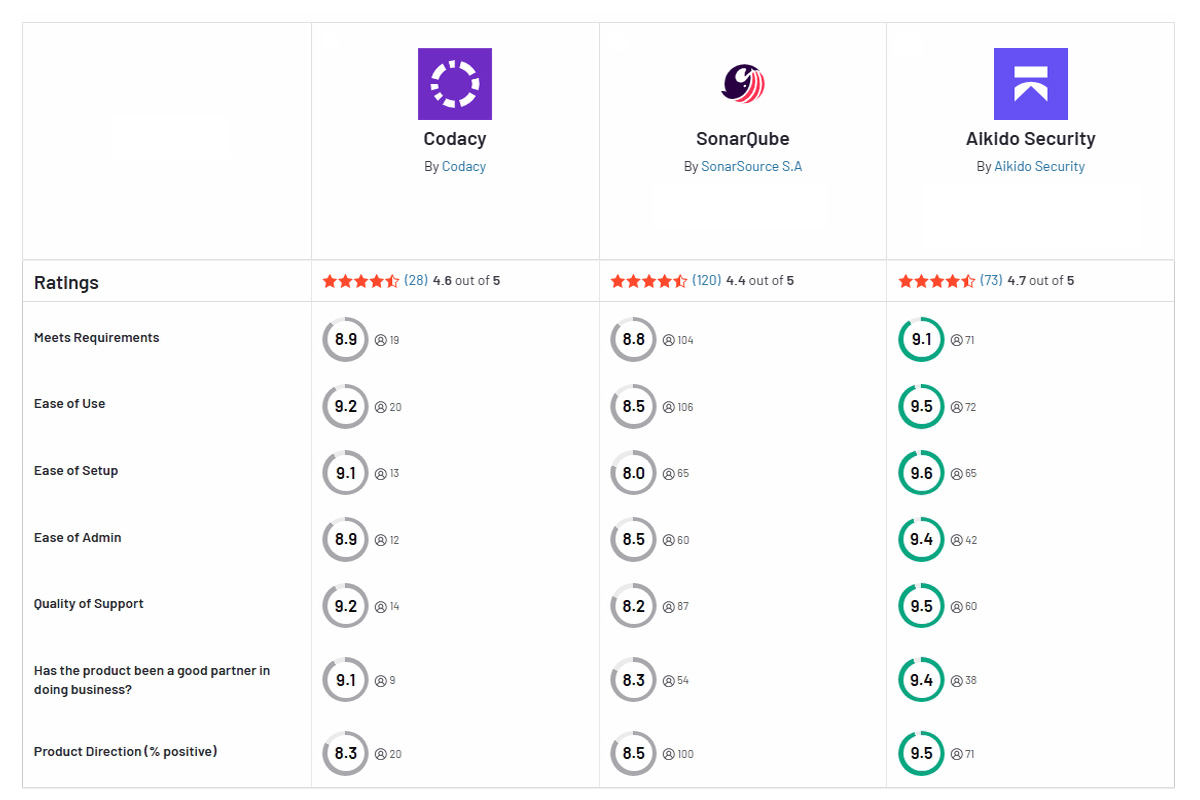
- Codacy: Emphasizes a frictionless integration experience. It’s a cloud service (with on-prem available) that you can connect to your code repo in minutes – no dedicated servers or build agents needed. Codacy’s scans run outside your CI/CD: when you open a pull request, Codacy automatically analyzes the code changes and reports issues, without making you add new pipeline steps. This “pipeline-less” approach means you get code feedback without slowing down your builds. Codacy provides one-click integrations with GitHub, GitLab, Bitbucket and can post comments on PRs with found issues. Developers can also use Codacy’s IDE extensions (VS Code, IntelliJ, etc.) to see analysis results right in their editor. The overall ease of use is reflected in user reviews – Codacy scores higher on integration and usability (9.6/10 integration vs SonarQube’s 7.8). In short, Codacy fits into workflows with minimal fuss, whereas SonarQube takes more upfront work to integrate into CI/CD.
Accuracy and Performance
- SonarQube: Static analysis isn’t foolproof, and SonarQube is no exception – it will occasionally flag false positives that aren’t real issues. Teams often need to fine-tune Sonar rules or mark certain findings as “Won’t Fix.” The good news is SonarQube’s mature ruleset has relatively decent precision; one reviewer noted its false positive rate is lower than some other SAST tools. SonarQube also provides context like dataflow traces for vulnerabilities, which makes it easier to triage findings. On performance, running SonarQube scans can add overhead to your pipeline. Scans are fairly quick for small projects, but on large codebases developers have seen long scan times – if you exceed a certain number of lines, the scan can take very long. You may need to allocate extra CI minutes or beefy servers for SonarQube to analyze huge monoliths. Essentially, SonarQube trades some build speed for thorough analysis.
- Codacy: Because Codacy often wraps multiple analysis engines (ESLint, PMD, SpotBugs, and even Semgrep patterns), it can initially report a lot of issues – not all of which are high priority. False positives can occur (especially if new security rules from Semgrep are too generic), so it’s important to configure your quality gate or ignore rules that aren’t relevant. Codacy provides the ability to customize rule sets and ignore specific false positives, which helps reduce noise. Some users note that Codacy’s vulnerability scanning alerts were “slightly better (less noisy) than other tools” they used. In terms of performance, Codacy’s analyses run on its cloud infrastructure asynchronously, so your developers aren’t left waiting on each build. You get results as soon as they’re ready in the PR. For very large repositories, Codacy’s unlimited scanning model ensures you’re not hitting LOC limits – though you’ll still notice that first scan on a big repo might take a bit of time. The key benefit is that this happens outside the dev’s machine or CI blocker, so it feels faster in practice. Overall, both tools require some tuning to maximize accuracy, but SonarQube is generally seen as reliable once configured, and Codacy offers flexibility to adjust any overly noisy rules.
Coverage and Scope
Both SonarQube and Codacy support a wide array of programming languages and integrate into the software development lifecycle, but there are differences in the breadth of security coverage each provides. SonarQube’s heritage is in code quality and static analysis of proprietary code, whereas Codacy aims for more full-stack code security coverage. The comparison table below highlights which features each tool covers:
As shown above, SonarQube delivers strong static analysis and code quality checks (covering ~30 programming languages), but its security scope is mostly limited to your own code. It lacks native open-source dependency scanning, container security, and DAST. Codacy covers nearly all the same static analysis capabilities (supporting 40+ languages) and extends into areas like dependency security, secrets, and IaC scanning. However, neither tool handles container image scanning or cloud configuration security – gaps that may require additional tools. For a technical leader, this means SonarQube and Codacy both leave certain risk areas (like vulnerabilities in Docker images or cloud environments) unaddressed.
A platform like Aikido is built to fill those gaps, as we’ll discuss, but with SonarQube or Codacy alone you’d need to plan for those additional coverage areas.
Developer Experience
- SonarQube: Developers generally appreciate the insights SonarQube provides, but the experience can vary. On the plus side, SonarQube’s UI gives a rich dashboard of code health and trends, which can instill a culture of quality. Its Quality Gate mechanism clearly tells devs when code doesn’t meet standards (e.g., new code has too many issues or insufficient tests). And with SonarLint IDE plugins, devs can get immediate feedback as they code, catching issues before they even commit. However, SonarQube has a steep learning curve for newcomers – there are a lot of rules and metrics, which can feel overwhelming or nitpicky until the team gets used to them. If imposed rigidly, some developers see SonarQube as a “policing tool” rather than a helper, especially if management uses it to block merges on minor issues. Tuning is key: teams that customize SonarQube to their needs (disabling irrelevant rules, adjusting thresholds) report a much better dev experience. In summary, SonarQube can improve code quality habits, but only after an initial hump of configuration and learning. It’s powerful, but not always lovable out of the box.
- Codacy: Codacy’s developer experience philosophy is to be as seamless and “shift-left” as possible. Because it sits in the background of PRs, developers get automated code review comments without having to run a tool locally or navigate to a separate dashboard (though a web UI and dashboards are available too). Teams often highlight Codacy’s ease of use – it scores higher in usability than SonarQube according to G2 reviews. From a dev’s perspective, Codacy feels like an assistant that quietly checks your code against standards and security guidelines, then tells you what to fix. The initial setup is minimal, so developers aren’t burdened with configuring scanners. The results are presented in-line with the code (on GitHub/GitLab diffs), which tends to be more actionable than a separate report. Codacy also offers an IDE plugin so developers can pull analysis results into VS Code or IntelliJ, similar to SonarLint integration. Another developer-friendly feature is Codacy’s AI-assisted fixes – it can suggest automatic fixes for certain issues right from the PR interface, saving time in remediation. Overall, Codacy is seen as more “plug and play” – developers can start benefiting from it on day one. The trade-off is that Codacy is less customizable than SonarQube’s do-it-yourself approach; but for many teams, not having to fiddle with configurations is a big plus in developer experience.
Pricing and Maintenance
- SonarQube: The core SonarQube Community Edition is free and open-source, which makes it attractive for budget-conscious teams. However, the free tier only goes so far – it supports many languages and basic static analysis, but advanced features (security rules like deeper taint analysis, additional language plugins, portfolio governance, etc.) are reserved for paid editions. The Enterprise and Data Center editions of SonarQube can get expensive (licenses often scale by lines of code or instances). Moreover, if you self-host SonarQube, you incur maintenance overhead: you need to run the server (and possibly a database), perform upgrades, and ensure high availability if it’s critical to your pipeline. Some small teams opt for SonarCloud (the SaaS offering) which has subscription pricing based on lines of code – easier than managing your own server, but costs can grow with your codebase size. In terms of transparency, SonarQube’s pricing can require some calculation (especially LOC-based plans). Maintenance-wise, expect to allocate effort for an admin to keep SonarQube running smoothly (monitoring resources, cleaning up old scan data, etc.). In short, SonarQube can be free to start, but scaling it with full features is a significant investment – either in licensing or in engineering time to maintain the service.
- Codacy: Codacy offers a straightforward SaaS pricing model. It is free for unlimited public/open-source repositories, which is great for community projects. For private repositories, Codacy uses a flat per-user subscription (seat-based pricing) rather than charging by lines of code. This means you can scan all your code (no LOC limits) at a predictable rate – e.g., a team of 10 developers pays for 10 seats, regardless of whether they have 100K or 10M lines of code. According to Codacy, this flat pricing often ends up more affordable at scale than SonarQube’s enterprise LOC-based fees. Codacy’s paid plans also include enterprise options (with support and on-premise deployment if needed). From a maintenance perspective, using Codacy cloud means zero infrastructure for your team to manage. You don’t need to configure build agents or maintain servers – the heavy lifting is on Codacy’s side. This is a big relief for lean teams that don’t want to babysit yet another tool. One thing to consider is data security: since code is analyzed by Codacy’s service, some organizations with strict compliance might require the self-hosted version. Codacy Self-Hosted gives you similar benefits but deployed in your environment (which then introduces maintenance overhead more akin to SonarQube). Overall, Codacy’s pricing is transparent and predictable, and maintenance is minimal when using the cloud. It’s essentially outsourcing the tooling overhead, which for many technical leaders is worth the cost.
Aikido offers a simpler, more transparent pricing model – flat and predictable – and is significantly more affordable at scale than either Snyk or Codacy.
Innovation and Community Support
- SonarQube: SonarQube has been around for over a decade, and it’s backed by an enormous community of users and open-source contributors. This means if you encounter an issue or need a custom rule, there’s likely a community plugin or someone on the forums who can help. SonarQube’s long history also means it’s stable – but it can be slower to adopt cutting-edge features. Innovation tends to be incremental. For example, support for new languages or frameworks appears over time, but SonarQube wasn’t the first to tackle container or supply-chain security (it’s only recently adding those via partnerships). SonarQube does excel at compliance-focused features for enterprise (e.g., rules mapping to MISRA, CERT standards for those in regulated industries). In terms of support, SonarQube offers official support for paid users, and community support for the free tier via its forums. The community is active, but some users on G2 have noted that SonarQube’s vendor support can be a bit less responsive (scoring 8.0/10) compared to Codacy’s more hands-on support.
- Codacy: As a newer player, Codacy has shown an appetite for innovation. In the last couple of years, they expanded beyond basic static analysis to include SCA, IaC scanning, and even integrated an open-source DAST tool – moves that blur the line between code quality and full AppSec platform. Codacy is also leveraging AI in its product, using AI to suggest code fixes automatically and even to guide code standards (“AI guardrails”). This indicates Codacy is keeping up with modern trends like AI-assisted development. The trade-off of being newer is a smaller community – Codacy’s user base isn’t as huge as Sonar’s, so community forums or third-party plugins are fewer. However, Codacy’s team is active in publishing updates (for example, integrating thousands of new rules via Semgrep shows a commitment to improve accuracy). On support, Codacy has earned a reputation for being responsive and helpful – its support quality is rated higher than Sonar’s (9.2 vs 8.0) by users. They also have documentation and an active blog to help users get the most out of the tool. In summary, Codacy seems to be innovating faster in the code security space, adding features that align with DevSecOps trends, while also keeping users happy with strong support. If being on the cutting edge (AI suggestions, unified DevSecOps scans) is important, Codacy has an edge over the more old-school SonarQube.
Pros and Cons of Each Tool
SonarQube – Pros:
- Robust Static Analysis Engine: Catches bugs, code smells, and vulnerabilities with a comprehensive ruleset refined over years.
- Broad Language Support: Supports 30+ languages and frameworks out-of-the-box, making it suitable for polyglot teams.
- Rich Metrics & Dashboards: Provides code quality metrics (coverage, duplication, complexity) and enforces quality gates to keep standards high.
- Active Community & Ecosystem: Large user community, plenty of plugins, and an open-source edition for extendability.
SonarQube – Cons:
- Setup and Maintenance Burden: Requires hosting a server and integrating it into CI – setup can be complex and time-consuming. Ongoing maintenance (upgrades, monitoring) is needed for self-hosted instances.
- False Positives & Tuning: Like many static tools, SonarQube can flag false positives that teams must manually mark or filter out. Initial rule tuning is often necessary to avoid alert fatigue.
- Limited Security Scope: Focuses mainly on in-house code. Lacks native open-source dependency scanning or container security, leaving blind spots in coverage. No built-in DAST or runtime testing features.
- Cost for Full Features: The free version is feature-limited (e.g., one branch analysis, basic rules). Advanced security rules, multi-branch reporting, and enterprise features come with high licensing costs.
Codacy – Pros:
- Easy Cloud Integration: Very little setup – one-click connect to your repo and get automated code reviews on every PR. No CI pipeline modifications or servers to manage.
- Comprehensive Coverage: Combines code quality and security scanning in one platform. Covers 40+ languages and checks for OWASP Top 10 issues, code style, complexity, duplicates, etc., all in one dashboard.
- Broader AppSec Features: Includes SCA for dependencies, secret detection, and IaC config scans out-of-the-box. Even offers DAST integration – giving you more security coverage without extra tools.
- Developer-Friendly Workflow: Integrates with PRs and IDEs to provide immediate, in-context feedback. Clean UI and even AI auto-fix suggestions make it popular with dev teams.
Codacy – Cons:
- Cloud Code Access: Using the SaaS means sending your code to Codacy’s servers, which may be a compliance concern for some organizations (though self-hosted is an option, it loses the zero-maintenance benefit).
- Noise from Many Rules: With thousands of checks, Codacy can report a lot of issues initially, including some low-priority or false positives. Requires configuration to tailor rule sets and reduce noise.
- No Container Scanning: Codacy still doesn’t scan container images for vulnerabilities, and it doesn’t cover live runtime/production security – you might need additional tools to fill those gaps.
- Paid for Private Repos: For internal codebases, you’ll need a paid plan. While pricing is flat per user (unlimited repos/LOC), teams on a tight budget must factor in this cost once you move beyond the free OSS usage.
Aikido Security: The Better Alternative
Aikido Security is a modern platform that positions itself as the “no-bullshit” alternative to tools like SonarQube and Codacy. It combines the key capabilities of both into one solution, delivering a broader security net with less hassle. With Aikido, you get full SAST coverage for code (like SonarQube, but with fewer false alarms thanks to smart automation) and built-in SCA, container image scanning, IaC and DAST – essentially all the AppSec tools you need under one roof. The platform is designed for quick setup and smooth integration: it plugs into your CI/CD and IDEs in minutes and provides immediate, actionable results without the noise.
Aikido’s focus on automation means it drastically cuts down on false positives, highlighting only real risks that developers should fix. In short, Aikido offers a one-stop, developer-friendly approach to security that eliminates the gaps left by SonarQube and Codacy. You get comprehensive coverage (from code quality to open-source and container security) without the deployment headaches – allowing your team to ship secure software faster and with confidence.
Start a free Trial or request a demo to explore the full solution.



