Introduction
Snyk and Veracode are both popular tools for improving software security. Each helps development teams catch vulnerabilities in code, but in different ways. For a technical leader responsible for secure software, choosing the right tool can significantly impact development speed and risk management. In this comparison, we’ll look at how Snyk and Veracode differ in coverage, integration, and team impact.
TL;DR
Snyk and Veracode both help secure your codebase, but they focus on different layers – and both have blind spots. Snyk is strong on open-source dependency and container security, while Veracode focuses on static code analysis and policy compliance. Aikido Security brings both worlds together in one platform, with fewer false positives and simpler integration – making it the better choice for modern security teams.
Overview of Each Tool
Snyk
Snyk is a developer-first security platform that scans for vulnerabilities in code and the software supply chain. It started by focusing on open-source dependencies (SCA) and container image security, helping teams find known vulnerabilities in libraries and Docker images. Snyk has since added Snyk Code for static application security testing (SAST) and Snyk IaC for infrastructure-as-code checks. The platform integrates directly into developer workflows (IDE plugins, CLI, CI/CD) so that security issues are caught early. Snyk’s key strength is quick, actionable scanning with fix suggestions, aimed at minimizing disruption for developers.
Veracode
Veracode is a veteran application security testing platform known for its comprehensive static and dynamic analysis capabilities. It provides static code analysis (SAST) as a cloud service – developers upload (or compile and upload) their code to Veracode, which then scans it on Veracode’s servers. Veracode also offers dynamic application security testing (DAST) to find runtime vulnerabilities, plus a software composition analysis feature from a past acquisition. The platform is geared towards enterprise use: it emphasizes thorough scanning, compliance reporting, and governance features for security programs. Veracode’s core focus is identifying code-level security flaws with depth and rigor, making it popular in organizations with strict security requirements and dedicated AppSec teams.
Feature-by-Feature Comparison
Security Scanning Capabilities
Snyk offers broad security coverage across the software stack. It includes a native SAST engine (Snyk Code) for finding code vulnerabilities, a software composition analysis tool for open-source library vulns, container image scanning, and IaC configuration checks. This means Snyk can flag insecure code as well as issues in the libraries and infrastructure files developers use, all in one unified platform. In contrast, Veracode has traditionally focused on SAST and DAST. Veracode scans compiled applications for code weaknesses and can test running web apps for vulnerabilities, but it has very limited container or cloud config scanning capabilities. Veracode does include an SCA module to detect vulnerable open-source components, though it’s not as developer-centric as Snyk’s approach.
Essentially, Snyk covers the newer “shift-left” use cases (dependencies, containers, config) out-of-the-box, whereas Veracode concentrates on deep analysis of the custom code itself. Both tools cover static analysis, but Snyk’s scope extends further into supply chain security. Veracode’s advantage is a one-stop AppSec platform for SAST and DAST at scale, even offering binary scanning (you can scan code without source by uploading compiled binaries). However, that strength comes at the cost of blind spots in areas like container security and infrastructure scanning, which Snyk handles by design.
Integration & DevOps Workflow
A big difference between Snyk and Veracode is how they integrate into development. Snyk was built to plug directly into the dev workflow – it has plugins for IDEs like VS Code and IntelliJ, Git hooks for repos, and CI/CD integrations so that checks happen automatically on each commit or pull request. Developers using Snyk can see vulnerability alerts and even one-click fix pull requests without leaving their normal tools. In practice, Snyk can scan uncompiled code in real time (no separate build step required) and provide instant feedback. Veracode, on the other hand, fits a more traditional model. It provides IDE plugins (Veracode Greenlight) and CI pipeline integrations, but using them often means sending code artifacts to the Veracode platform for analysis.
Typically, a developer or build server must compile the application and upload it to Veracode’s cloud scanner, then wait for results. This extra step introduces friction – it’s not as seamless as Snyk’s in-editor scanning. Many organizations treat Veracode as a gating step in the pipeline or a scheduled scan (for example, a nightly build) rather than something that runs on every code change. Veracode’s integrations are robust in an enterprise sense (e.g. it has Jenkins plugins, API access, and can integrate with ticketing systems), but from a DevOps perspective Snyk tends to feel more “plug-and-play.” Developers are more likely to actually use Snyk routinely, because it’s embedded in their tools and provides quick, actionable results. Veracode’s workflow often involves a separate portal for viewing results and can require more coordination with a security team.
In summary, Snyk better meets teams “where they work” with minimal ceremony, whereas integrating Veracode can feel like bolting an external security step onto the pipeline. Both can be automated, but Snyk’s automation is simpler and more developer-friendly.
Accuracy and Performance
Accuracy and scan speed are critical for adoption. Snyk is known for its fast scanning. It can analyze code continuously as you write it, with average scan speeds about 2.4× faster than many legacy tools. Because Snyk doesn’t require a full build, it can surface issues within seconds or a few minutes at most for typical projects. This real-time aspect means developers get quick feedback and aren’t stuck waiting. Veracode scans, in contrast, tend to be slower and more heavyweight. Scanning a large application with Veracode might take anywhere from 30 minutes to multiple hours, especially if using its deep scan modes.
Many teams end up running Veracode scans overnight or only on certain builds because of this duration. That delay can discourage developers from running scans frequently. On accuracy, each tool has its trade-offs. Snyk’s static analysis (Snyk Code) uses a modern AI-based engine (from their DeepCode acquisition) to prioritize real vulnerabilities and reduce false alarms. In practice, Snyk tends to have a relatively low false-positive rate for a SAST tool, and it provides context to help devs decide if an issue is real or not. Veracode, with its long history in SAST, also strives for accuracy and has matured rules that catch a wide range of issues.
Veracode claims to have one of the lowest false positive rates out-of-the-box, but experiences vary. Some engineers report that Veracode’s thoroughness can surface a lot of findings that aren’t always relevant, requiring time to filter and tune the rules. On the flip side, Snyk has been criticized (often by competitors) for occasionally flagging issues that might not be true vulnerabilities. In short, both tools will generate some noise, as any automated scanner will. Snyk’s approach tries to minimize wasted effort by using machine learning and developer feedback to weed out trivial or non-exploitable findings.
Veracode’s approach leans on its policy engine and scanning depth to focus on significant issues, but the initial scan results can be overwhelming until you implement ignore lists or adjust severity thresholds. For performance and dev productivity, Snyk clearly has the edge – it’s built for speed and quick iteration. Veracode is built for thorough coverage, at the cost of speed. This means in terms of practical accuracy (signal-to-noise ratio in a daily dev workflow), Snyk might actually surface fewer but more pertinent alerts, whereas Veracode might find more potential issues overall (including edge cases) but needs more human triage.
Coverage and Scope
When it comes to technology coverage, the two tools differ in both breadth and depth. Veracode supports an extensive range of programming languages (over 30 languages and 100+ frameworks) for static analysis. It’s well-suited for enterprise stacks – from Java and C# to C/C++, JavaScript, Python, Ruby, and more – including older or less common languages. Veracode’s static scanner can even analyze binaries for certain languages (like scanning .NET DLLs or Java bytecode), which means it can handle cases where you can’t provide source code. This broad language support and the ability to scan mixed-language apps or legacy code is a strong point.
Snyk, meanwhile, covers all the major languages that modern development teams use, especially for web and cloud apps (Java, JavaScript/TypeScript, Python, C#, PHP, Go, etc.). For those, Snyk offers both SAST and SCA coverage. However, Snyk might not support some very niche or legacy languages in its SAST engine (for example, if you have a lot of C/C++ or old-school languages, Veracode would likely have more mature support there). In terms of vulnerability coverage: Snyk has a massive open-source vulnerability database powering its SCA, so it’s extremely good at catching known issues in dependencies (one of the best in class for open-source intel). Veracode’s SCA database is solid but not as community-driven as Snyk’s, so teams relying heavily on open-source might find Snyk’s coverage more up-to-date.
When comparing overall scope across the SDLC, Snyk offers a more unified view – you can see code flaws, library vulns, container issues, and IaC problems all in one place. Veracode provides a wide view on application risk too, but primarily around code (SAST/DAST findings). It does not natively scan your Kubernetes configs or Terraform scripts, for example, whereas Snyk will. In summary, if your stack is very diverse or includes some older tech, Veracode’s static analysis might cover more ground. If your focus is modern development (cloud-native apps, containers, lots of open-source libraries), Snyk’s coverage is extremely comprehensive in those areas. Many organizations actually use a combination: Snyk for open-source and dev-first scans, and Veracode for that extra mile on certain languages or compliance checks.
(Feature Coverage Quick Glance: Snyk natively covers SAST, SCA, container, and IaC security; Veracode covers SAST, DAST, and SCA. Snyk recently even added DAST for APIs/web, but it’s newer. Veracode does not have a container or IaC scanner. Both integrate with major dev tools (IDEs, CI), but Snyk’s coverage of dev ecosystem integrations is broader.)
Developer Experience
For a technical leader, an important consideration is how the tool will be received by developers and integrated into their day-to-day work. Snyk prides itself on a clean, developer-friendly experience. The UI is straightforward, and the results are presented with developer context (including references to the exact lines of code or dependency versions that are problematic, along with guidance on how to fix). Snyk’s integrations (IDE plugin, GitHub/GitLab integration, etc.) mean a developer might get a security alert as a comment on their pull request or a red underline in their code editor – which feels like a natural extension of coding, rather than a separate security process.
The learning curve for Snyk is relatively low; developers can often self-serve and start fixing issues on day one. Veracode, being more of an enterprise tool, can feel less intuitive for developers. Its web portal is powerful but somewhat dated and complex, aimed at central AppSec teams as much as developers. Devs may need training to interpret some of Veracode’s findings (the vulnerability descriptions can be very detailed and occasionally overwhelming). Veracode has made improvements – their IDE plugin (Greenlight) gives quick feedback in the editor, which is great.
However, Greenlight only supports a few IDEs and performs a lightweight scan, not the full analysis. So developers still eventually have to deal with the main Veracode scan results in the portal. One common pain point cited is noise: if a developer runs a Veracode scan on a big project, they might get hundreds of issues listed, not all of which are critical. Snyk tends to highlight fewer, more relevant issues (and even ranks them by severity and exploitability to help prioritize). Another aspect is remediation support.
Snyk often provides one-click fix pull requests (for example, it can automatically bump a library version to fix a known flaw) and suggests code changes using its AI engine. Veracode provides detailed info on each finding and sometimes suggests safe functions or configurations, but it doesn’t auto-fix your code for you. Culturally, many devs see Snyk as a tool for developers, whereas Veracode is seen as a tool for security teams that developers have to interface with. If your development culture is DevOps/DevSecOps, Snyk will likely drive higher adoption because it feels like an enabler rather than a checkpoint.
In summary, from a developer’s UX perspective, Snyk is simpler to set up, produces results that are easier to understand, and fits into existing workflows more naturally. Veracode can absolutely be used by developers (and should be), but it may be viewed as more of a mandate (“we must run a Veracode scan for compliance”) than an everyday coding assistant. That difference often translates to better engineering buy-in with Snyk.
Pricing and Maintenance
Both Snyk and Veracode are commercial products, but their pricing models differ. Snyk is offered as a cloud-based SaaS with tiered plans. It has a free tier (useful for open-source projects or small teams to try out, with limits on number of tests) and then paid plans that typically charge per developer seat or per project. As you scale Snyk to an entire engineering org, costs can climb quickly since it’s often priced per user. Large enterprises may negotiate custom plans, but generally Snyk’s pricing can become a significant line item if you have hundreds of developers.
The flip side is that Snyk’s cloud service requires minimal maintenance – there’s no server to manage (unless you use their broker for on-prem code), and updates to vulnerability databases and scanning engines happen automatically. Veracode is also delivered as a cloud service (it was one of the pioneers of SaaS in AppSec), and it’s known to be on the higher end of pricing. Veracode typically licenses based on the number of applications scanned, or sometimes based on scan frequency and the depth of services. For example, you might buy a package that allows static scanning for X applications and a certain number of dynamic scans or hours of manual penetration testing as a bundle.
There’s no “freemium” tier for Veracode – it’s an enterprise sales process with trials or pilot programs if you want to evaluate. So for startups or smaller companies, Veracode likely won’t fit the budget or effort. Maintenance-wise, since Veracode is also SaaS, you don’t host the scanning engine yourself (unless you opt for their on-prem agent for special cases). However, using Veracode does involve some operational overhead: someone needs to manage the scan scheduling, handle the onboarding of new apps into the platform, and review the results for false positives or waivers. Veracode provides robust features for these (policy management, user roles, etc.), but those features are really aimed at a dedicated security team overseeing the program.
In contrast, Snyk’s maintenance feels more like managing any developer tool – ensure the plugins are installed and developers are onboarded, and then much of the work is self-service as developers fix issues. One more consideration is scalability of cost: Snyk’s per-seat cost can become expensive if you roll it out to a giant dev team, whereas Veracode’s per-app model can be expensive if you have many small microservices (each counted as an app). Neither is cheap at enterprise scale, to be frank.
This is where alternatives like Aikido often pitch their value – Aikido offers a simpler, flat pricing model that doesn’t penalize you for having more developers or more projects, making it more predictable and often more affordable as you grow. In terms of getting the best value, Snyk might win for small-to-mid teams that can even use the free tier and then incrementally pay as needed, while Veracode is a serious investment generally justified for large orgs with big security budgets.
Pros and Cons of Each Tool

Snyk Pros:
- Developer-centric and easy to integrate: Plugs into IDEs, repos, and CI pipelines for seamless “shift-left” security. Devs get quick feedback and one-click fixes.
- Broad security coverage: One platform covers code vulnerabilities (SAST), open-source risks (SCA), container issues, and more – providing a holistic view.
- Fast scanning: Snyk’s scans are lightweight and incremental (no full build needed), so they run quickly (often under a couple minutes).
- Actionable guidance: Clear remediation advice and automated fix pull requests help developers actually resolve issues rather than just flagging them.
- Vast vuln database: Snyk’s open-source vuln database is one of the most comprehensive, meaning it can catch issues in dependencies that others might miss.
Snyk Cons:
- Noise in certain cases: While generally tuned for fewer false positives, Snyk’s static analysis is younger and can sometimes flag benign patterns as issues. In some languages, teams have reported needing to triage out a number of “false alarms.”
- Limited legacy coverage: Snyk supports many modern languages, but it’s not as deep in older platforms (e.g. legacy languages or binary-only workflows). Veracode’s long history gives it an edge for some legacy tech stacks.
- Complex pricing at scale: Snyk’s per-developer pricing can become expensive for large teams, especially if you need multiple Snyk products (Code, Open Source, Container, etc.). Budget-conscious organizations might find it hard to justify the cost for enterprise-wide use.
- No native DAST for web apps (until recently): Snyk’s focus has been on code and supply chain. It only recently added a dynamic scanner, which is not yet as established. If you need extensive runtime testing, Snyk alone might not suffice.
- Reliance on developer adoption: Snyk works best when developers actively use it. Organizations without a strong DevSecOps culture may find that vulnerabilities linger if developers ignore Snyk’s alerts (since there’s less of a central gating mechanism by default).
Veracode Pros:
- Thorough analysis: Veracode provides very in-depth static analysis that can uncover complex vulnerabilities in code (e.g. multi-step data flow issues) across a wide range of languages. It tends to catch a broad array of security issues, including ones that newer tools might overlook.
- Enterprise-grade governance: It excels in policy management and compliance reporting. You can enforce security gates (e.g. “no high-severity flaws before release”) and get detailed reports/audits, which is valuable for meeting regulatory or customer requirements. It’s a platform built with security teams and risk oversight in mind.
- Dynamic testing capability: Beyond static analysis, Veracode’s DAST option can scan running applications for vulnerabilities like SQL injection or XSS in a black-box fashion. This is something many code-only tools don’t offer in the same platform.
- Wide technology support: Over 30 languages and numerous frameworks are supported in scanning. It’s battle-tested on everything from Java and .NET enterprise apps to C/C++ projects. It also supports scanning compiled binaries, which is useful for cases where source isn’t available.
- Low false-positive tuning: Over the years, Veracode has refined its engine to reduce trivial or false findings (e.g. it recognizes common frameworks to avoid flagging safe patterns). Out-of-the-box, its results are relatively precise for a large-scale SAST, according to many enterprise users and Veracode’s own claims.
Veracode Cons:
- Slow feedback loop: Scan times are long. Developers might wait hours for results on a big codebase, which discourages frequent use. It’s not ideal for rapid CI/CD environments where you want instant validation.
- Integration friction: Setting up and running Veracode scans can be cumbersome. Requiring code to compile and be uploaded means it doesn’t fit as neatly into the save-and-check cycle of development. The need to use an external portal or carry out separate steps can reduce developer engagement.
- Limited DevOps flexibility: Veracode is a cloud service with a traditional enterprise vibe – less flexible for custom workflows. For example, its IDE plugin (Greenlight) only covers a subset of use-cases and IDEs, and full scans can’t run on every commit due to time. Fast-moving teams often need an additional lightweight tool because Veracode alone feels too heavy.
- Higher cost: Veracode is one of the pricier options in AppSec testing. The pricing model (usually by application and scan type) can lead to big bills for organizations with many microservices or frequent scanning needs. There’s also no free tier, so even initial evaluation has a barrier.
- Narrower scope of coverage: Veracode lacks first-class support for container scanning, infrastructure-as-code, and other newer areas. It focuses on code and web app tests. If you want a single solution for “code to cloud” security, Veracode by itself won’t cover everything. You might still need additional tools (which increases complexity and cost).
Aikido Security: The Better Alternative
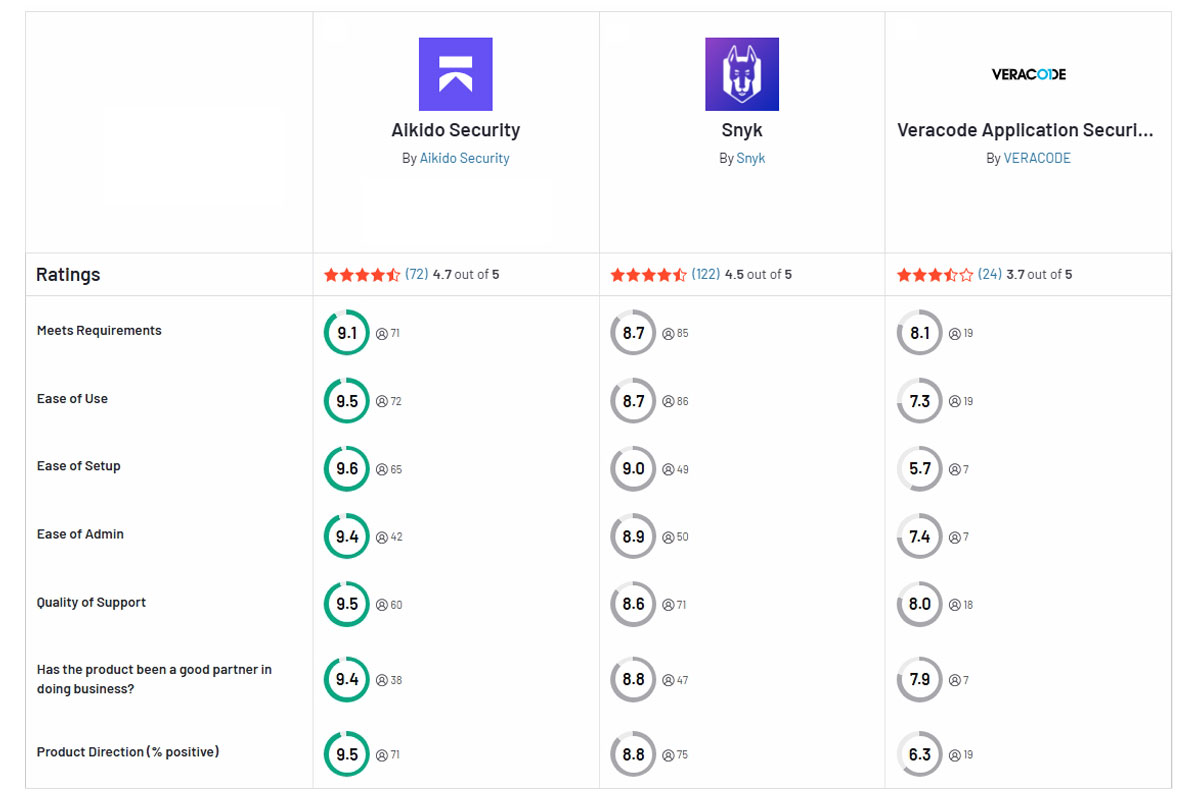
Aikido Security combines the strengths of both Snyk and Veracode while avoiding their pitfalls. It delivers a unified AppSec platform that covers code, open-source dependencies, cloud configs, and more in one place – without the usual headaches. With minimal false positives by design (thanks to intelligent noise filtering), Aikido gives developers high-signal results they can trust. Integration is a no-brainer: Aikido slips into your IDE and CI/CD pipeline, so security checks feel seamless and automated. Unlike legacy tools, there’s no waiting around or wrestling with complex UIs.
You get comprehensive coverage akin to Veracode’s thoroughness, but with developer-first UX on par with Snyk (and dare we say, even slicker). Plus, Aikido’s pricing is flat and predictable, making it significantly more affordable at scale. In short, if you’re tired of juggling Snyk’s and Veracode’s trade-offs, Aikido offers a modern, no-nonsense solution – secure code, minus the extra noise and BS.
Start a free Trial or request a demo to explore the full solution.



