If you work in DevSecOps or AppSec, you’ve probably heard of Snyk and Trivy, and probably compared them at least once. They both scan source code, dependencies, containers, and other artifacts for known vulnerabilities, but once you actually use them, the differences become impossible to ignore. Notably in their developer experience, accuracy, and maintenance.
One prioritizes polished workflows, deep integrations, and structured guidance for development teams, while the other focuses on transparency, speed, and simplicity through a fully open-source, CLI-first approach.
In this article, we’ll break down their core features and provide a clear side-by-side comparison to help you choose the tool that best fits your workflow and security needs.
TL;DR:
Aikido Security brings together the strengths of both Snyk and Trivy, offering a single platform with full-stack security and developer-friendly workflows. It combines Snyk’s coverage of dependencies, containers, and license risk with Trivy’s speed and simplicity, while offering AI-powered analysis and automated remediation features.
Aikido Security contributes actively to the open-source community through several initiatives. Its Intel feed is often first to identify new CVEs and malware campaigns including the recent npm security outbreak and Shai Hulud 2.0 Since these compromises, organizations have turned to Aikido’s SafeChain to protect npm packages on install, enabling them to avoid encountering many of these issues in the first instance.
Aikido Security is also the lead initiator of the Opengrep Project, an open-source alternative to Semgrep following its recent license change. Opengrep provides the open-source community with a more advanced static code analysis engine, access to previously paid Semgrep features, faster performance, and broader language and platform support.
It also offers an open-source version of its proprietary Zen firewall.
These initiatives make Aikido Security the combination of a powerful off-the-shelf security platform and a driver of community-driven security improvements.
Comparing Snyk vs Trivy vs Aikido Security
What is Snyk?
Snyk is an application security platform that scans code, open-source libraries , containers, and infrastructure-as-code (Iac) for vulnerabilities. It integrates directly into development environments and CI/CD pipelines (GitHub, GitLab) so developers get security feedback early. Snyk’s origin is in open-source dependency scanning (SCA), but has expanded to include Snyk Container for image scans, Snyk IaC for Terraform/Kubernetes checks, and Snyk Code for static application security testing (SAST).
Pros:
- Comprehensive coverage across SCA, containers, IaC, and code scanning.
- Deep integration with development tools and workflows (IDE plugins, CI/CD gating).
- Offers actionable remediation (fix suggestions, pull requests).
- Continuously monitors for new vulnerabilities and alerts you, improving long-term security.
Cons:
- Pricing can be expensive.
- The platform is known to produce false positives
- Snyk’s cloud-based approach may raise data governance concerns
- Steep learning curve
- It has a 1 MB file-size limit for static analysis.
- Scan times can be slow on large repositories
- Its remediation recommendations can feel generic or not tailored.
- It may struggle with proprietary or highly specialized codebases.
What is Trivy?
Trivy is an open-source vulnerability scanner from Aqua Security. It is known for being simple, fast, and thorough. It started as a container image scanning tool and has evolved into a versatile tool that also scans file systems, code repositories, Dockerfiles, Kubernetes manifests, and much more. Trivy detects vulnerabilities in OS packages (Alpine, Ubuntu) and application dependencies such as npm, Pip, Maven by pulling data from various security databases.
Pros:
- Free and open source
- Fast scans and simple setup
- Broad support for scanning different targets (containers, file systems, code repositories, IaC configs).
- Generally accurate results with minimal false positives.
- Integrates easily into CI/CD pipelines and can be run locally by teams without special infrastructure.
Cons:
- Limited scope beyond known vulnerabilities).
- Lacks a native UI or reporting interface; results are CLI-based..
- No automatic fix suggestions or patch management .
- While Trivy covers containers and code dependencies, you might need additional tools for comprehensive AppSec.
- Enterprise support and features (like RBAC, central dashboards) are only available by moving to Aqua Security’s paid solutions.
Feature-by-Feature Comparison
Core Security Capabilities
- Snyk: Snyk offers a broad suite of application security features under one platform. Its core strength is its Software Composition Analysis (SCA) engine which it uses to find vulnerabilities in third-party libraries and open-source dependencies. Snyk Open Source draws on an extensive vulnerability database to flag risky packages and license issues. It can also suggest safer versions or patches. Snyk also provides a dedicated container scanning tool (Snyk Container) that checks both OS packages and app libraries in images for known CVEs.
For infrastructure-as-code, Snyk IaC scans configuration files (Terraform, Helm charts, Kubernetes) for security misconfigurations such as. open security groups or hardcoded credentials. Additionally, Snyk offers static analysis (SAST) via Snyk Code to catch code-level issues like SQL injection or insecure code patterns in proprietary code..
- Trivy: Trivy in comparison, provides broad coverage, with a focus on vulnerability scanning. Trivy performs SCA out-of-the-box on container images and file systems to identify vulnerable OS packages (base images) and language dependencies in applications (similar to Snyk for container’s) .
Trivy also offers IaC scanning rules to catch misconfigurations in Dockerfiles, Kubernetes manifests, and cloud configuration files. It can even scan for hard-coded secrets (API keys, passwords) in code or images.However, Trivy does not perform static code analysis for vulnerabilities, it won’t find an XSS or business logic flaw in your application code since it lacks a SAST engine.
Both tools address the “pre-production” layers of security. They both leverage vulnerability feeds to identify risks: Trivy uses public databases such as the Linux distro advisories and GitHub Security Advisories, while Snyk uses its proprietary vulnerability database and public data.Neither tool provides runtime attack detection on its own..
Integration and DevOps Workflow
- Snyk: Snyk is designed to plug into the tools developers and DevOps engineers already use. It offers integrations with popular IDEs (VS Code, IntelliJ), source control platforms (GitHub, GitLab, Bitbucket), and CI/CD systems (Jenkins, CircleCI) so that security scans happen automatically during development and build processes. For example, Snyk can scan every pull request for vulnerable dependencies,open and fix PRs or add a step in your CI pipeline to break the build on high-severity issues.
- Trivy: on the other hand, is a lightweight binary that you invoke on demand, which makes it extremely easy to integrate in scripts and pipelines. You don’t need to create accounts or upload your code to a service,you simply run Trivy as part of your CI jobs (or locally) and inspect the output. This local-first approach appeals to many DevOps teams: for example, you can add a Trivy GitHub Action to scan each container image build, or run Trivy in a Jenkins pipeline to fail a build if critical vulns are found. Trivy doesn’t have a centralized cloud dashboard by default; the results appear in the console (or as JSON, JUnit, etc.) which you can feed into other systems.
In summary, Snyk deeply embeds into the SDLC with lots of official integrations (but requires adopting Snyk’s platform), while Trivy integrates wherever you can run a CLI.
Accuracy and Performance
When it comes to scan accuracy and noise, there are notable differences between Snyk and Trivy.
- Snyk: Snyk’s vulnerability scanning (SCA) is generally accurate. It uses curated data and context analysis to prioritize issues.. However, its static code analysis has been reported to produce false positives that overwhelm developers. In large codebases, users have reported performance problems, with Snyk missing issues and timing out. On the other side, Snyk’s continuous monitoring means after the initial scan, you get alerts on new issues without rerunning manually
- Trivy: Trivy is known for being fast and efficient. This is thanks to its ability to scan medium-sized container images in seconds, compact vulnerability database and low false positive rate. Since Trivy identifies only known vulnerabilities and misconfigurations, its results are mostly precise. However its misconfiguration scanning and secrets scanning may generate some noise.
Overall, in terms of performance Snyk might generate more noise in some areas such as code scanning but also provides richer insights, whereas Trivy is fast and precise on what it checks, but requires more user interpretation and rerunning to stay current.
Coverage and Scope
- Snyk: Snyk is designed to handle polyglot codebases and provides support for a broad range of programming languages (Java, JavaScript/TypeScript, Python, C#, Ruby, Go,), package managers (npm, Maven, RubyGems, NuGet), container operating systems, frameworks, and IaC formats. Generally, Snyk focuses on the development stage through the build process; for runtime or network-layer coverage, additional tools are required. Snyk also provides license compliance checking as part of its open-source scanning, which is important for managing legal risk.
- Trivy: Trivy has broad coverage in the types of artifacts it scans, source code, container images, configuration files, and more, but its depth of analysis is narrower. It supports a wide range of operating systems (Alpine, Debian, Red Hat) and languages (JavaScript, Java, Python, Ruby, .NET, Rust). And also handles Docker/OCI container images and can scan tar archives or local directories. For Infrastructure-as-Code (IaC), it includes checks for Kubernetes manifests, Helm charts, Terraform, and CloudFormation, similar to Snyk IaC. It can also generate SBOMs (Software Bill of Materials) in CycloneDX or SPDX formats and scan them for vulnerabilities, making it useful for modern supply-chain security workflows.
One limitation is that Trivy does not perform static code analysis for custom application logic and does not provide full cloud account configuration auditing
In summary, Snyk and Trivy both support a wide range of languages and development environments, but Snyk extends deeper into the application layer while Trivy excels at fast, precise detection of known vulnerabilities across many artifact types. However, Both leave certain gaps such as runtime protection and dynamic testing
Platforms like Aikido Security help cover those gaps by offering code scanning, dependency scanning, container, IaC analysis, and much more in a single integrated solution.
Developer Experience
- Snyk: Snyk delivers a strong developer experience with a clean, intuitive UI and dashboards that make it easy to track, assign, and remediate issues directly in developer workflows such as GitHub pull requests and IDE annotations. Its Onboarding is straightforward, especially for open-source projects, and Snyk’s extensive documentation further supports developers. However, users have reported its interface as slow on large projects, and Snyk’s findings can generate high alert volumes, requiring teams to spend time triaging
- Trivy: Trivy takes an opposite approach with a CLI-based workflow that prioritizes speed and simplicity. It outputs raw vulnerability lists without guidance or prioritization, which works well for DevOps users but can be less accessible to developers who prefer UI-driven workflows.
Overall, Snyk provides a more guided experience (with more automation in fixing and reporting), whereas Trivy provides a more flexible, do-it-yourself experience that teams can tailor.
Pricing and Maintenance
The cost and maintenance model of Snyk versus Trivy is a classic commercial vs open-source story.
- Snyk: Snyk is a commercial product that typically charges per developer seat or per project. Snyk’s pricing has been noted to scale aggressively with team size and features, with medium and large businesses finding it expensive. For example, Snyk might charge a set fee per developer per year, and additional fees for add-on capabilities like Snyk Container or for CI integration beyond a certain number of tests. This can lead to six-figure annual costs for larger teams, and some features (like reporting or additional language support) may only be in higher tiers.
Maintenance of Snyk on your end is relatively low ,– you will need to upgrade the CLI occasionally and manage integration, but the heavy lifting (updating vuln databases, improving scanners) is handled by Snyk’s team.
- Trivy: Trivy is completely free and open source (MIT licensed), which makes it ideal for budget-conscious teams, startups, or organizations that prefer. There are no limits on users or scans, and it automatically updates its vulnerability database, so minimal maintenance is required beyond keeping the Trivy binary or Docker image up to date.
However, Trivy’s support comes mainly from the community, and enterprise-scale management such as correlating scan results across multiple projects requires additional effort, since it has no central portal or guaranteed SLA.
Platforms like Aikido Security offer the best of both tools for teams that want the speed, flexibility, and broad coverage of Trivy while also benefiting from enterprise support, structured workflows, and contributing back to the open-source community, all at flat, transparent fees.
Community and Innovation
Snyk and Trivy have very different communities and development philosophies.
- Snyk: Snyk is a venture-backed company (now a decacorn) with a large user base among developers and enterprises. It has an active community in terms of usage, and contributes to open source projects like its vulnerability database and some CLI tooling, but its core products are proprietary. Snyk’s innovation often comes via acquisitions and partnerships: they integrated an AI engine (through their acquisition of DeepCode) to power Snyk Code’s analysis, and have partnered with companies like GitGuardian for secrets detection and Fugue for cloud security. The Snyk community tends to be users sharing best practices, plus Snyk’s own evangelism through blogs and events.
- Trivy: Trivy owes its popularity largely to the open-source community. It’s part of the Cloud Native Computing Foundation (CNCF) landscape of tools, and hundreds contributors help keep its vulnerability data and checks up to date. Being open source, Trivy’s development is transparent on GitHub, and it often adds features that users request (like new configuration checks or support for new artifact types). For instance, secret scanning and SBOM support (CycloneDX)were added as the ecosystem evolved.
In terms of AI/ML, Snyk is already using AI to help with code fixes and prioritization, and we can expect more of that in its platform. Trivy itself doesn’t have AI features (it doesn’t try to predict vulnerabilities or automatically fix them), but it can be combined with other tools that do. ).
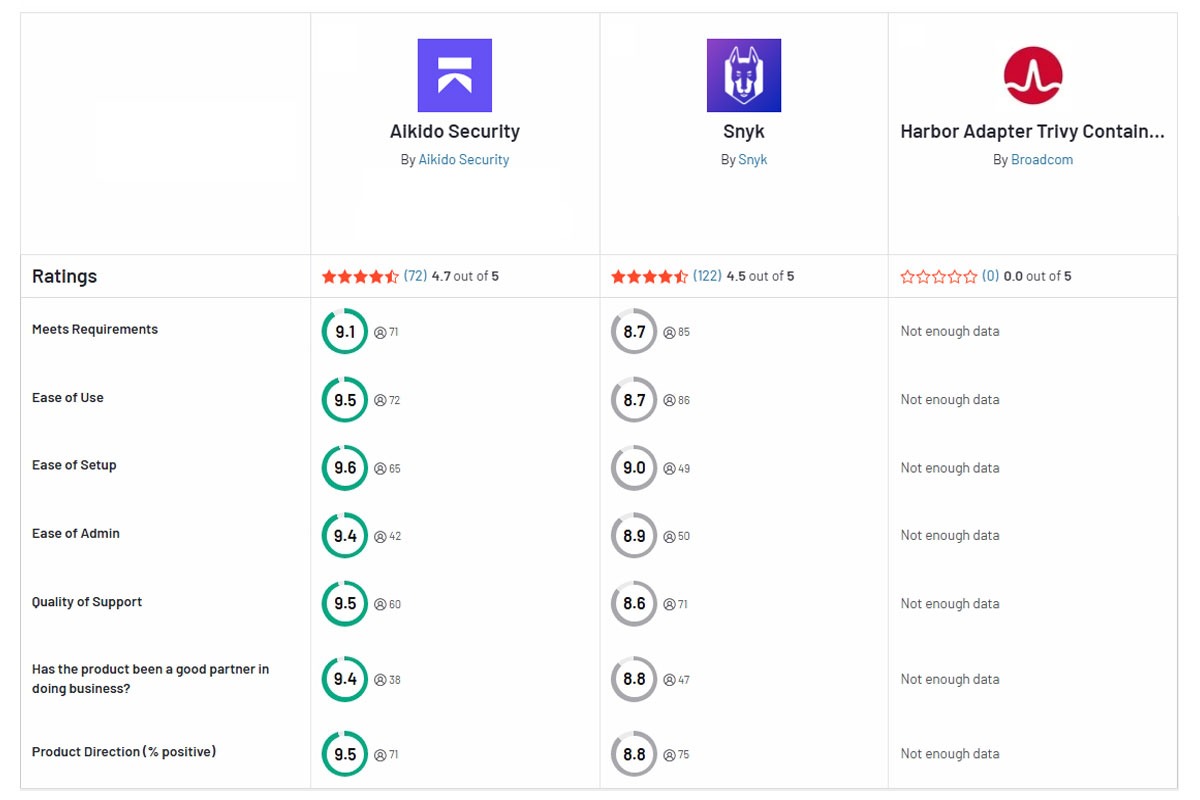
To help you compare the features of both tools, the table below summarizes it for you.
Aikido Security: The Better Alternative
Aikido Security is an AI-driven application security platform that merges the strengths of Snyk and Trivy into a single solution. It provides coverage across source code, dependencies, containers, IaC, cloud infrastructure, and APIs, all within a developer-friendly workflow.
Its AI engine correlates vulnerabilities across multiple layers of the SDLC and performs reachability analysis to identify truly exploitable vulnerabilities. It also provides developers with automated remediation, including pull requests and one-click fixes.
Beyond commercial capabilities, Aikido Security leads in open-source contributions: its Intel feed alerts teams to critical vulnerabilities early, SafeChain protects codebases against malicious packages during installation, Opengrep offers an advanced static analysis engine, and it provides an open-source version of its Zen firewall.
With a flat-rate pricing and a free forever tier, Aikido Security delivers broad, actionable security without the noise, cost, or complexity of juggling Snyk and Trivy.
Want to improve your application’s security? Start your free trial or book a demo with Aikido Security today.
FAQ
What are the main differences between Snyk and Trivy?
Snyk is a commercial, UI-driven platform with deep SAST, contextual prioritization, license checks, secrets detection, and workflow integrations. While Trivy is an MIT-licensed, Command-line interface scanner that’s fast, lightweight, and excels at finding known CVEs in images, packages, and IaC templates. Platforms like Aikido Security combine the usability and breadth of Snyk with Trivy-style speed.
Which tool is better for container vulnerability scanning: Snyk or Trivy?
For quick, local scans with zero cost, Trivy is the go-to, thanks to its open-source nature, speed, ease, and ability to flag known image CVEs. For enterprise workflows that need contextual reachability, remediation guidance, license checks, and integrated reporting, Snyk is stronger.Platforms like Aikido Security offer both speed and enterprise features without tool sprawl tools.
How do vulnerability scanners like Snyk and Trivy improve DevSecOps practices?
They shift security left by automating detection in development workflows, produce SBOMs, and enforce policy gates so issues are found and fixed earlier. Snyk adds contextual prioritization and managed alerts; while, Trivy offers fast, scriptable scans that fit CI pipelines and local testing.
Which tool offers better support for scanning Infrastructure as Code (IaC) templates: Snyk or Trivy?
Both perform IaC scans (Terraform, Helm, Kubernetes manifests, CloudFormation), but Snyk provides richer policy management, guided remediation, and a UI for triage. Trivy’s IaC checks are effective and CLI-friendly but produce raw results that often require custom aggregation or policy tooling for enterprise-scale governance. If you want built-in policy enforcement plus developer ergonomics, consider platforms that combine both approaches, such as Aikido Security.
Can Snyk and Trivy be integrated with CI/CD pipelines, and how do their integrations differ?
Yes. Trivy integrates via a single binary/CLI and is easy to embed in pipelines and build containers, it runs locally and scales with your CI runners. While Snyk integrates more deeply (IDE plugins, PR comments, automated fixes, centralized dashboards) and offers managed scanning, alerts, and role-based controls.
You Might Also Like:

Secure your software now





