Introduction
Snyk and Mend (formerly WhiteSource) are both popular tools for improving software security. They help development teams find vulnerabilities early, but they take different approaches. In this comparison, we’ll cut through the hype and look at what each tool really offers, where they fall short, and why technical leaders are exploring better alternatives.
TL;DR
Snyk and Mend both help secure your codebase, but they focus on different layers – and each has blind spots. Snyk shines in developer-friendly open-source and container security, while Mend emphasizes open source governance and code analysis. Aikido Security brings both worlds together in one platform, with fewer false positives and simpler integration – making it the better choice for modern teams.
Overview of Each Tool
Snyk: Snyk is a developer-first security platform that automatically finds and fixes vulnerabilities in code, open-source dependencies, containers, and infrastructure as code. It’s known for easy integration into development workflows and providing actionable fix suggestions (like automated pull requests to update a vulnerable library). Snyk’s focus is on empowering developers to secure components throughout the SDLC with minimal friction.
Mend: Mend.io (formerly WhiteSource) is an application security tool focused on managing open-source risks and license compliance. Teams use Mend primarily for software composition analysis (SCA) – scanning dependency libraries for known vulnerabilities and license issues. It has expanded into static code analysis (Mend SAST) and other areas, but Mend’s core strength remains open-source governance and detailed reporting for risk management. It’s often favored by security and compliance teams for its policy enforcement capabilities.
Feature-by-Feature Comparison
Core Security Capabilities
Snyk: Offers broad application security coverage in one suite. It includes SAST for custom code, SCA for open-source libraries, container image scanning, and IaC (Terraform/K8s) checks. Snyk’s vulnerability database is extensive, and it prioritizes known issues with suggestions for quick remediation – for example, it can automatically open fix PRs to bump a dependency version when a new CVE is found.
Snyk’s static code analysis does introduce some noise with false positives, which can require devs to spend time filtering out non-issues. The upside is that Snyk rarely misses real, critical vulnerabilities thanks to its rich vulnerability intel.
Mend: Primarily excels at SCA and license compliance. Mend continuously monitors your third-party dependencies against a broad vulnerability database and alerts on outdated or risky packages. It provides comprehensive dashboards and reports on open-source risk and can enforce policies (for example, blocking a build if a critical flaw is detected).
Mend has a static analysis component (Mend SAST) for custom code, but that capability is newer and less emphasized than its SCA. Unlike Snyk, Mend doesn’t cover areas like container or IaC scanning out of the box, focusing mainly on known vulnerabilities in your code and its libraries.
Integration & DevOps Workflow
Snyk: Designed for seamless integration into modern DevOps. It plugs into repositories (GitHub, GitLab, Bitbucket), CI/CD pipelines, and IDEs with minimal fuss. Developers can see security issues in pull requests or get immediate feedback in their editor. Because Snyk is cloud-based, setup is straightforward – you add it to your Git workflow or pipeline and it starts scanning. Snyk also supports additional platforms like Azure DevOps and Bitbucket, so it’s quite flexible. This developer-centric approach means teams adopt Snyk quickly without interrupting existing processes.
Mend: Integrations are more limited and often require extra effort. Mend can run via CLI in CI pipelines and has plugins for certain build tools, but users have reported challenges integrating it smoothly into some workflows (especially in on-prem environments). Initial setup might involve manual configuration – setting up API tokens, webhooks, and custom integration scripts for each project.
On the plus side, Mend offers on-premises deployment options, giving companies control over data and the scanning environment. However, maintaining those servers is extra work. Overall, Mend works once set up, but it’s not as plug-and-play for developers compared to Snyk.
Accuracy and Performance
Snyk: Snyk is known for a strong vulnerability database – it rarely misses known CVEs in dependencies. Its scans are generally fast (thanks to checking against a cloud database) and can even run in pull requests without much lag. That said, Snyk’s breadth can lead to noise. Users have reported it flags some issues that turn out benign or irrelevant, which creates extra work to review.
For example, Snyk Code (its SAST) might highlight a potential SQL injection that isn’t actually exploitable. They have been improving their filtering, but teams still sometimes need to tune rules or mark false alarms as ignored to manage alert fatigue.
Mend: Mend takes an automation-heavy approach aimed at reducing manual triage by highlighting the most important issues. Even so, many users complain about high false-positive rates in Mend’s findings, which can erode trust in the results.
Performance is another concern. Mend’s SCA scans on large projects can be slow, and the UI can feel laggy when navigating results. This means your team might spend extra time waiting for scans to complete and sifting through the noise to find real problems.
Coverage and Scope
Snyk: Supports a wide range of programming languages and package managers for scanning open-source components (from JavaScript and Python to Go and .NET). It continually adds ecosystem support, including frameworks and config files. Snyk’s addition of container and IaC scanning broadens its scope beyond just code – covering Docker images and Terraform/Kubernetes configurations for security issues.
In practice, Snyk gives you one tool to check your application code, its dependencies, container setup, and cloud configs for misconfigurations. One notable gap is that Snyk isn’t focused on general code quality or style; it sticks to security vulnerabilities and license risks, not things like code formatting or maintainability.
Mend: Offers broad language support as well, especially for open-source scanning, covering most major languages and package ecosystems. Mend particularly shines in license compliance: it can generate SBOMs (software bills of materials) and alert on license conflicts, which is valuable for enterprises in audit mode. This is an area where Mend historically outshines Snyk’s more basic license checks.
However, Mend’s overall coverage is narrower. It mainly concerns code and dependency vulnerabilities. If you need container image scanning, cloud configuration security, or dynamic application testing (DAST), those features are absent in Mend or require pairing it with additional tools.
Developer Experience
Snyk: Prioritizes developer experience. The interface is modern and relatively easy to navigate, with issues grouped in a developer-friendly way. Results come with clear remediation guidance (like exactly which version to upgrade to). Snyk’s IDE plugins and Git hooks give developers immediate feedback and even one-click fix pull requests for some issues.
The focus is on keeping noise low and integration tight, so using Snyk feels like a natural part of coding. There is still the occasional need to tweak settings or suppress an alert, but engineers generally appreciate that Snyk isn’t a heavy, bureaucratic tool that slows them down.
Mend: Caters more to security managers than to day-to-day developers. Its UI has a reputation for being clunky and outdated, which frustrates devs who just want to quickly address issues. Simply put, it’s not as intuitive or clean as modern dev tools.
Mend’s findings aren’t always immediately actionable for developers – for example, it might flag a vulnerable library without providing a suggested fix or automated PR. They have made some strides (Mend now owns Renovate, which helps automate dependency updates), but the overall experience still isn’t as developer-friendly. Setting up and mastering Mend often means digging through documentation and tuning configurations. In short, developers tend to find Mend cumbersome and will avoid using it unless required by the security team.
Pricing and Maintenance
Snyk: Many consider Snyk expensive. There is a free tier for small projects, but costs climb steeply for larger teams and for unlocking advanced features. Snyk’s pricing is typically per user or project, which can lead to large bills at scale. On the bright side, because Snyk is a SaaS solution, you don’t have to maintain any infrastructure – everything runs in the cloud under Snyk’s management.
Mend: Mend’s pricing tends to be enterprise-oriented and can be steep for smaller teams, especially given that you might also need to manage the tool’s infrastructure. Mend does offer an on-premise option (useful if you have strict data control requirements), but that means you’re responsible for running and updating the servers.
On a positive note, Mend’s customer support is well-regarded as responsive and helpful, which can be a lifesaver when dealing with tricky vulnerabilities or tuning false positives. Still, many organizations find Mend’s value hard to justify unless they heavily leverage its compliance and reporting features to get a solid return on investment.
Aikido: Notably, Aikido Security offers a simpler, more transparent pricing model – flat and predictable – and it’s significantly more affordable at scale than either Snyk or Mend. This predictable cost structure (plus a generous free tier) can be a breath of fresh air for budget-conscious teams.
Pros and Cons of Each Tool

Snyk Pros:
- Broad security coverage: One platform for code scanning, open-source vulns, containers, and more.
- Developer-friendly: Easy integrations with Git, CI pipelines, and IDEs; minimal setup overhead.
- Actionable fixes: Provides suggested fixes or even auto-fix PRs for many issues, accelerating remediation.
- Vulnerability intel: Backed by a comprehensive database of vulns, so it finds even the latest threats.
Snyk Cons:
- High cost at scale: Pricing becomes steep for large teams as you expand usage.
- False positives noise: Some scans report non-issues that have to be filtered out.
- Limited license tracking: Only basic license conflict alerts; not as in-depth as dedicated license compliance tools.
- Support hiccups: Support is generally good but some users have found response times inconsistent at the enterprise level.

Mend Pros:
- Excellent OSS governance: Detailed dependency and license reports help manage open-source risk.
- Policy enforcement: Can enforce security policies (e.g. block builds on critical vulns) to ensure compliance.
- Wide language coverage: Supports numerous languages/package managers for SCA, suitable for diverse tech stacks.
- Strong support: Known for responsive customer service and guidance during deployments.
Mend Cons:
- Clunky interface: Outdated UI and UX make it less pleasant to use, especially for developers.
- Integration friction: Lacks easy out-of-the-box integrations into dev workflows; setup and maintenance can be a pain.
- Alert fatigue: Tends to flag too many issues (high false positive rate), which can overwhelm teams.
- Limited scope: Focused mainly on SCA; lacks built-in container scanning, IaC security, or DAST capabilities.
Aikido Security: The Better Alternative
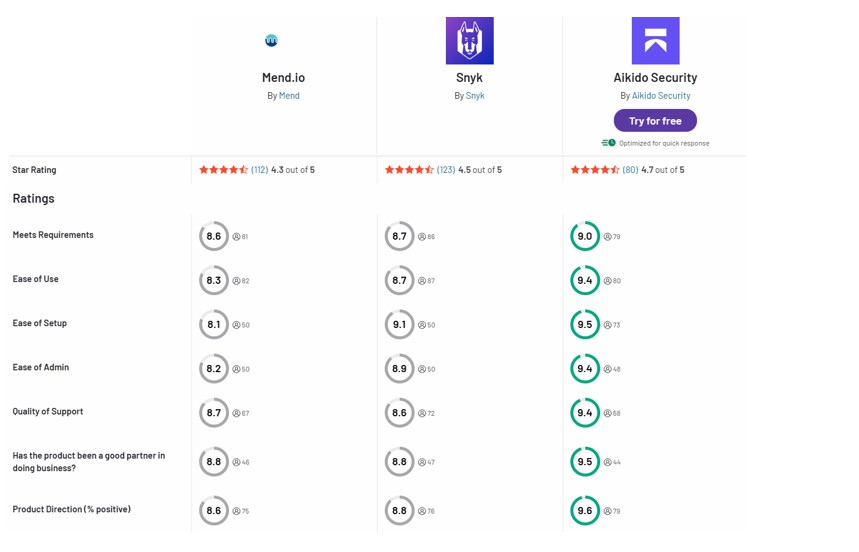
Aikido Security combines the strengths of both Snyk and Mend into one platform. It covers code, open source, containers, cloud, and more in a unified solution – so you’re not juggling multiple tools. Built with developers in mind, it offers in-IDE scanning, one-click fixes, and smart risk prioritization to cut out the noise. It delivers far fewer false positives by auto-triaging findings and slots into CI/CD pipelines seamlessly. With transparent flat pricing and an all-in-one approach, Aikido gives teams a no-nonsense way to ship secure code faster.
Start a free Trial or request a demo to explore the full solution.



