Introduction
Technical leaders know that choosing the right code security tool can make or break development velocity and risk management. In this post, we compare Snyk and Checkmarx – two leading application security (AppSec) platforms – to see how their different focuses (open-source vs. code quality) impact coverage, integration, and team workflow.
TL;DR
Snyk and Checkmarx both help secure your codebase, but they focus on different layers – and both have blind spots. Snyk excels in open-source dependency and container security, while Checkmarx specializes in static code analysis. Aikido Security brings both worlds together in one platform, with fewer false positives and simpler integration – making it the better choice for modern security teams.
Overview of Snyk and Checkmarx
Snyk – Snyk is a developer-first security platform designed to integrate into coding workflows. It initially focused on Software Composition Analysis (SCA) to find vulnerabilities in open-source dependencies, and later expanded into scanning proprietary code (SAST), container images, and infrastructure-as-code. Snyk emphasizes quick, in-IDE or CI/CD feedback to help developers fix issues early (“shift-left” security).
Checkmarx – Checkmarx is an enterprise-focused AppSec suite that started with Static Application Security Testing (SAST) for custom code and broadened its platform to cover open-source libraries, cloud infrastructure, and supply chain security. Its roots in static code analysis give it a reputation for deep code inspection and governance features. Checkmarx caters to security teams with strong policy enforcement and compliance tools during development.
Security Scanning Capabilities
Both Snyk and Checkmarx offer multiple types of security scanning, but their strengths differ. Snyk made its name in open-source vulnerability scanning – it quickly identifies known CVEs in third-party libraries (SCA) and monitors container image risks. It also includes SAST for your own code via Snyk Code, plus checks for infrastructure-as-code misconfigurations. However, Snyk does not offer any dynamic runtime testing (no DAST) or interactive testing (IAST) at this time.
Checkmarx, on the other hand, built its foundation on SAST and is known for thorough static code analysis. Over time, Checkmarx added its own SCA tool and even container and IaC scanning as part of the Checkmarx One platform. In theory, this means Checkmarx can scan source code, open-source packages, Dockerfiles, and cloud configuration all under one roof. In practice, its strongest area remains finding code vulnerabilities with SAST. Neither tool includes a full dynamic analysis module, so runtime vulnerability testing is a gap for both. If you need DAST, you’ll be using a separate tool regardless.
Key difference: Snyk shines at securing the software supply chain (open-source deps, containers) whereas Checkmarx focuses on the custom code itself. Checkmarx’s static analysis might catch security bugs in your application logic that Snyk’s SAST (still relatively new) could miss. Conversely, Snyk’s database of known vulns and misconfigurations gives it an edge in coverage of open-source risks out-of-the-box.
Integration & DevOps Workflow
Snyk is built to slot directly into a developer’s workflow with minimal friction. It offers plugins for popular IDEs and alerts in source control (pull requests) and CI/CD pipelines. Developers can get security feedback in real time as they code or commit changes. This seamless integration is often praised by engineering teams – Snyk’s API and integration options make it easy to connect with GitHub, GitLab, Jenkins, and other dev tools. The onboarding is straightforward (Snyk even has a free tier), so teams can start scanning quickly without extensive configuration.
Checkmarx integration is more heavyweight. It supports CI pipeline hooks and even IDE plugins, but the setup and maintenance are more involved. Many companies deploy Checkmarx in a centralized way – for example, a security engineer runs scans and shares results – rather than having every developer run it continuously. Checkmarx can be run on-premises or as a cloud service, which adds flexibility for enterprises with strict data requirements. However, on-prem deployments mean you’ll need to manage servers, updates, and scaling yourself. In fact, getting Checkmarx fully integrated into a modern DevOps environment can take considerable time and fine-tuning.
The platform is powerful but not as plug-and-play for developers. As a result, developers might only see Checkmarx scan reports after code is merged or on a schedule, rather than instant feedback in their IDE. This lag can reduce its usefulness in fast CI/CD loops.
In summary, Snyk is generally seen as the more DevOps-friendly tool – it fits into existing developer tools and cloud workflows with little fuss. Checkmarx can certainly integrate, but it often feels built for the security team first and developers second. If your goal is to empower engineers to fix issues early, Snyk has the advantage of approachability. If you require an on-prem solution with strict controls, Checkmarx provides that option (while Snyk is predominantly a cloud SaaS service).
Accuracy and Performance
When it comes to scan accuracy (true positives vs false positives) and performance, the two tools have trade-offs. Checkmarx has a reputation for very thorough static analysis – it will find subtle issues in code – but historically it can overwhelm you with a lot of findings, some of which may not be critical or are hard to validate. In other words, it can be noisy. Tuning Checkmarx (writing custom rules or suppressing certain patterns) is often required to reduce false positives and make results actionable. Checkmarx’s own marketing highlights improved accuracy, claiming their engine produces fewer false positives than Snyk’s and catches more real vulnerabilities.
There is evidence that Checkmarx SAST does catch issues that simpler scanners might miss – one analysis found Checkmarx identified 3.4× more true positives in code than Snyk. This suggests Snyk’s newer SAST engine might still be maturing in depth.
On the flip side, Snyk tends to optimize for signal-to-noise ratio. Its vulnerability scanning prioritizes actionable results and tries to minimize the “firehose” of alerts common to legacy SAST tools. In fact, many users report that Snyk’s false-positive rate is quite manageable, letting teams focus on real issues. Snyk’s static analysis uses an AI-based engine (from their DeepCode acquisition) that learns from developer feedback, and Snyk claims high accuracy scores on industry benchmarks. However, some developers have still encountered “false flags” with Snyk Code scanning (e.g. it flagging safe code as vulnerable).
No SAST tool is immune to noise – one AppSec practitioner noted that false positives plague every SAST, and without tuning you’ll face a flood of distracting alerts. Snyk’s approach is to reduce this noise by default (possibly at the cost of missing a few issues), whereas Checkmarx might err on the side of reporting more and leaves it to you to filter out the noise.
Performance is another differentiator. Snyk is generally fast – its cloud scanners and lightweight plugins can give results in seconds or minutes. Snyk advertises scan speeds 2.4× faster than traditional solutions. Because it scans incrementally (especially in IDE), it can provide near real-time feedback as code is written. In contrast, Checkmarx scans (especially full SAST scans on a large codebase) are known to be slow. It’s not uncommon for Checkmarx to take hours to scan a big project with millions of lines of code, especially if using thorough settings. This slower feedback cycle can frustrate agile teams. If developers have to wait overnight or longer for results, security fixes slow down. Checkmarx has been improving performance and even offers incremental scanning, but in practice Snyk’s more modern architecture tends to be quicker out-of-the-box.
To put it simply: Snyk is speedy and fairly accurate, but might miss some deeper issues; Checkmarx is deep but noisy and slow without careful tuning. Many teams will use these tools in complement – or look for a unified solution that balances depth with developer-friendly signal, as we’ll discuss with Aikido.
Coverage and Scope
Coverage refers to the breadth of languages, frameworks, and security issue types each tool can handle. Checkmarx positions itself as an enterprise-grade solution with very broad language support. It advertises support for 35+ programming languages and 70+ frameworks, covering everything from popular languages like Java, C#, and JavaScript to legacy or niche languages that large organizations use. Checkmarx’s SAST can analyze desktop, web, mobile, and even some low-level code. For example, it supports older languages like C/C++ and PHP, mobile languages like Swift and Kotlin, and more – making it suitable if your codebase is polyglot.
Its SCA component similarly covers a wide range of package ecosystems (Maven, NPM, PyPI, NuGet, etc.), and Checkmarx claims it even outperforms Snyk in open-source vulnerability coverage by identifying ~11% more issues in third-party libraries. Additionally, Checkmarx includes an “Exploitable Path” analysis to prioritize reachable vulnerabilities, which works across major repo platforms and languages (whereas Snyk’s similar feature was limited to GitHub/Java at one point).
Snyk, while comprehensive for most modern development needs, supports fewer languages in its SAST tool compared to Checkmarx. As of recent data, Snyk Code covered around 20+ languages (all the common ones, but perhaps not as many legacy languages). Snyk’s strength is in open-source scanning: it has an extensive vulnerability database and monitors open-source projects for new disclosures, which means you get alerts for dependency issues in real time. Snyk Open Source covers all major package managers and has detailed remediation guidance (like recommended upgraded versions).
In container security, Snyk integrates with container registries to scan images for known CVEs in OS packages or language packages – this is an area it excels. Checkmarx’s container scanning (as part of their SCA product) also identifies vulnerable packages in Docker images, but Snyk’s product might be more polished for developers in DevOps pipelines. Both tools scan Infrastructure-as-Code files (Terraform, CloudFormation, Kubernetes manifests) for misconfigurations to prevent cloud security mistakes – Snyk through its IaC tool, and Checkmarx via its open-source KICS engine integrated into the platform.
In terms of vulnerability types, both will catch the OWASP Top 10 web app risks (SQL injection, XSS, etc.) in code. Checkmarx, with its deeper static analysis, can find complex logical flaws or insecure coding patterns in proprietary code. Snyk’s SAST might not have as extensive a rule set yet, but it’s improving and does cover many common issues. One gap to note: neither Snyk nor Checkmarx performs penetration testing or live application testing, so things like business logic flaws or runtime-only vulnerabilities won’t be flagged by these tools alone. For compliance needs, both provide reporting on security posture (e.g. adherence to standards like OWASP, PCI, etc.), but Checkmarx offers more robust compliance reporting suitable for auditors.
Overall, Checkmarx covers a broader technology stack (especially if you have legacy apps or a diverse portfolio), while Snyk covers the modern cloud-native stack extremely well (cloud infra, containers, plus code and dependencies). If your team mainly works with modern languages and frameworks, Snyk’s support is more than sufficient; but if you have some obscure language in the mix, Checkmarx might be the only option. Both aim to provide “360-degree” coverage across the SDLC, but each still has holes that may require supplementary tools (like DAST or secret scanning tools).
Developer Experience
In the battle of developer experience, Snyk has an edge by design. It’s frequently lauded for its ease of use – the interface is clean and geared towards developers rather than security analysts. Setting up a Snyk scan is as easy as a few clicks or commands, and the results are presented with actionable fix advice. For instance, if Snyk finds a vulnerable dependency, it will suggest a specific version to upgrade to; if it finds a code issue, it often provides a code snippet and guidance on how to remediate. Snyk even offers automated fix pull requests for some issues, saving developer time. This focus on quick, actionable remediation means developers can take ownership of security findings without needing deep AppSec expertise. It’s a “no-nonsense” tool in that it tries to surface only what matters, with minimal jargon, so devs aren’t scared off by walls of cryptic vulnerabilities.
Checkmarx, by contrast, is often seen as a tool for the security team. Its interface and outputs can be overwhelming or overly verbose for developers. Many devs find the need to sift through lengthy PDF reports or complex dashboards to find the few issues they actually need to fix. Without customization, Checkmarx might dump hundreds of findings labeled with CWE IDs and internal codes – not exactly developer-friendly. As a result, teams sometimes treat Checkmarx as a compliance gate: run it in the background and have security triage the results, shielding developers from the noise. This dynamic isn’t ideal for fostering a security ownership mindset among engineers.
The learning curve for Checkmarx is steep. Developers may need training to use the tool effectively (ironic, though Checkmarx does include its Codebashing training to help educate developers).
Additionally, Checkmarx often requires manual tuning to fit a team’s coding patterns. Writing custom queries or adjusting rule packs is powerful for AppSec specialists, but average developers won’t spend time doing that. Snyk, on the other hand, opts for sane defaults and simplicity – less configuration, more immediate value. This difference is reflected in user feedback: Snyk scores higher in ease of setup and use according to peer reviews, whereas Checkmarx is described as “reliable but requires some babysitting” by users.
One more aspect of developer experience is how well the tools integrate into daily tools. Here again Snyk wins points for its native IDE plugins and Git workflow integration – devs can get security feedback without leaving their coding context. Checkmarx is improving in this area (they’ve added VS Code and JetBrains plugins, and even AI-assisted fix suggestions in the IDE), but those features are relatively new. Historically, developers would interact with Checkmarx mainly through a web dashboard or emailed reports, which feels disconnected from their workflow.
In summary, developers tend to actually use Snyk because it’s straightforward and reduces friction. Checkmarx, if imposed without care, can feel like a chore or “security tax” on development – something that might be avoided or run only when mandated. For technical leaders, this matters: a security tool that engineers quietly ignore is a waste of investment. The slightly “check-the-box” nature of Checkmarx in some devs’ eyes is a real downside. Snyk’s dev-centric approach stands out as a major positive. Of course, if your developers are security-savvy and willing to engage with a more complex tool, Checkmarx’s depth can be harnessed – it just takes more effort to get to that sweet spot where devs and AppSec are in sync.
Pricing and Maintenance
Pricing and maintenance considerations can heavily influence which tool makes sense for your organization. Snyk uses a subscription model and offers a transparent pricing structure (including a free tier for small-scale use). Teams are often charged per developer seat or per project, which can become expensive as you scale up. Many startups start with Snyk’s free or affordable plans, but as they grow, the costs can ramp up significantly – there are reports of mid-sized companies paying tens of thousands of dollars annually for Snyk.
The upside is that Snyk being SaaS means zero infrastructure to maintain. You don’t need to provision servers or worry about updating the scanning engine; Snyk handles all that in the cloud. The platform’s updates (new vulnerability data, rule improvements) roll out continuously to all users. So, the operational overhead on your end is minimal.
Checkmarx typically is a larger investment. It’s sold as an enterprise product (no public pricing, usually custom quotes), and the cost can be justified for large organizations with big security budgets. If you’re a smaller company or startup, Checkmarx’s price tag will likely be prohibitive (think enterprise license $$$). Moreover, if you choose an on-premise deployment, you’ll incur maintenance costs: you need hardware or VMs for the scanning engine and database, an admin to apply updates/patches, and potentially support contracts.
Checkmarx does offer a cloud-hosted option now (Checkmarx One SaaS), which offloads some maintenance, but many enterprise customers still opt for self-hosting due to data security concerns. Feature-wise, note that some advanced capabilities in Checkmarx might cost extra or only be available in higher-tier packages (for example, their Codebashing training or advanced analytics might be add-ons). This modular pricing can drive up the total cost if you want the full suite.
In terms of maintenance, Snyk clearly wins for ease – as mentioned, it’s mostly hands-off for your team. Checkmarx requires care and feeding, from customizing rules to managing false positive workflow and updates. One must factor in those personnel hours. As a rough guide, organizations often have a dedicated AppSec engineer or two managing a Checkmarx deployment, while Snyk can often be run with less dedicated overhead (developers themselves operate it). This is in line with the earlier note on complexity: Checkmarx’s power comes with complexity, and complexity has a cost.
Finally, consider the scalability of pricing. Snyk’s cost grows linearly with the number of developers or projects – which can get expensive if you have hundreds of devs, but at least it’s somewhat predictable. Checkmarx, being enterprise software, might actually scale better per-user in large volumes (big enterprises negotiate site licenses), but the entry barrier is high. Also, Aikido’s approach to pricing is worth mentioning: Aikido offers a simpler, flat pricing model that stays predictable and is significantly more affordable at scale than either Snyk or Checkmarx – avoiding the “surprise” bills as you add more projects or users.
Bottom line: Snyk is easier to start with and budget for incremental growth (especially with its free tier and SaaS model), whereas Checkmarx is a heavier upfront investment that makes sense if you’re a big shop needing its breadth. Don’t forget to account for the hidden cost of managing the tool – Checkmarx’s total cost of ownership includes maintenance effort that Snyk’s does not.
Aikido offers a simpler, more transparent pricing model – flat and predictable – and is significantly more affordable at scale than either Snyk or SonarQube.
Pros and Cons of Each Tool

Snyk – Pros
- Seamless dev workflow integration: Embeds into IDEs, Git repos, and CI/CD pipelines, so developers get security feedback without leaving their tools.
- Immediate, actionable results: Provides real-time vulnerability alerts with clear fix guidance (e.g. recommended version upgrades or code patches) to remediate issues quickly.
- Easy to adopt: Intuitive UI and one-click setup means teams can onboard in minutes, with no steep learning curve or complex configuration.
- Strong open-source & cloud coverage: Excels at scanning open-source dependencies, containers, and IaC for known flaws, leveraging a vast vulnerability database.
Snyk – Cons
- Limited enterprise controls: Lacks some advanced policy management and compliance reporting that large enterprises and security auditors may require out-of-the-box.
- Narrower testing scope: Focuses on SAST and SCA, with no offerings in dynamic testing (DAST) or IAST – leaving certain vulnerability types (e.g. runtime issues) unaddressed.
- Can get pricey at scale: Per-developer pricing and add-ons can become expensive for large teams or org-wide usage, potentially straining budgets as you grow.
- SAST still maturing: Its static code analysis, while improving, may miss some deep issues that legacy tools catch – third-party tests show a higher miss rate compared to Checkmarx.

Checkmarx – Pros
- Comprehensive AST suite: Provides a broad range of application security tests (SAST, SCA, IaC scanning, etc.) in one platform, covering vulnerabilities across code, open source, and cloud configs.
- Enterprise-grade governance: Robust enforcement of security policies, role-based access, and detailed compliance reporting meet the needs of security teams in regulated industries.
- Highly scalable: Built to handle large codebases and many projects simultaneously, with options for clustering and tuning – suitable for complex, multi-team enterprise environments.
- Developer education built-in: Includes Codebashing training modules to help upskill developers in secure coding, directly linking learning to identified vulnerabilities.
Checkmarx – Cons
- Complex setup & usage: Deployment and integration require significant time and expertise. The tool has a steep learning curve, and advanced features demand careful tuning and maintenance.
- Slow scan feedback: Static analysis scans can be time-consuming (especially on big projects), delaying results and potentially hindering agile development cycles with long waits.
- High cost for entry: As an enterprise solution, it comes with a premium price tag. Licensing and infrastructure costs make it less viable for smaller teams, who may be priced out.
- Integration gaps: Despite broad coverage, it lacks some capabilities (no built-in DAST or secrets scanning) and has limited third-party integrations – organizations often need additional tools to fill these gaps.
Aikido Security: The Better Alternative
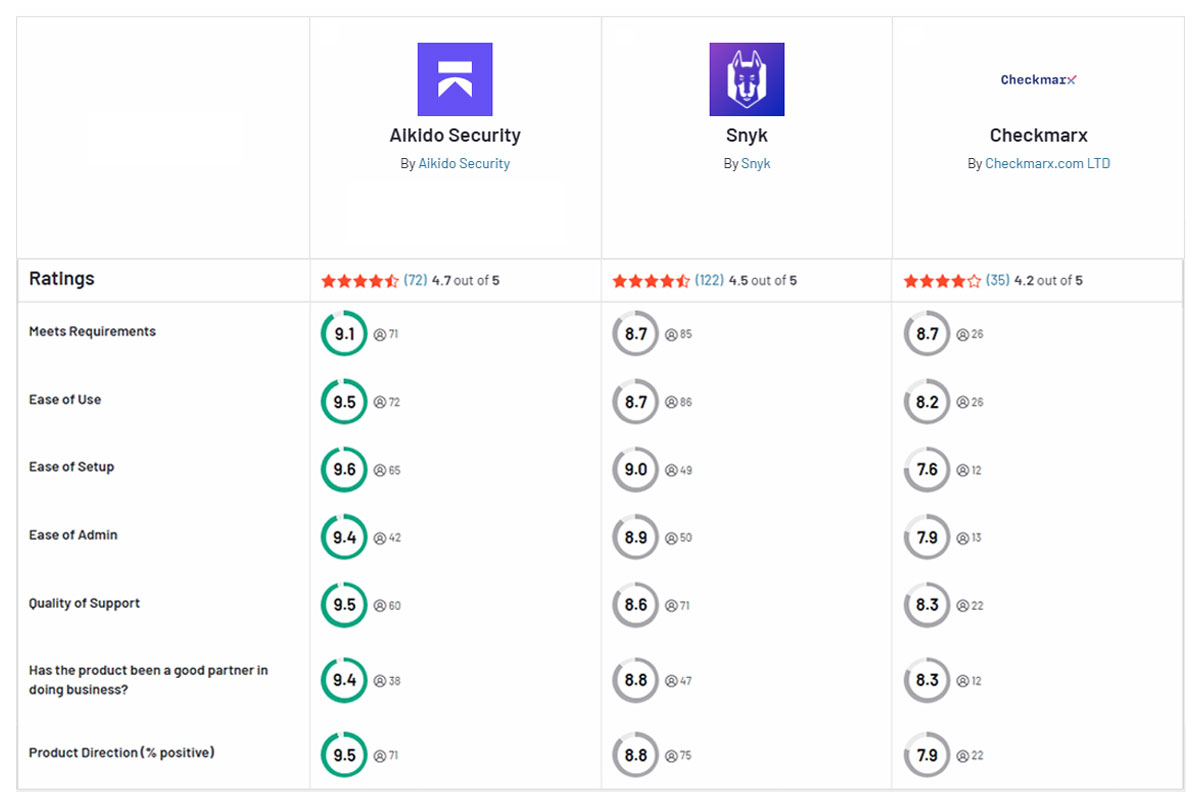
Aikido Security combines the strengths of Snyk and Checkmarx into one no-nonsense platform without their downsides. It delivers both deep code scanning and open-source supply chain security in a unified solution, so you aren’t forced to juggle multiple tools. Importantly, Aikido is engineered to produce far fewer false positives – cutting out the noise that plagues other scanners. The result is a tool developers actually trust and use. Integration is frictionless (plugging into repos, pipelines, and IDEs just like Snyk) and the developer experience is front-and-center, but with the robust coverage and governance that security leaders expect.
Aikido also offers flat, predictable pricing that undercuts legacy vendors. In short, it’s an all-in-one AppSec solution that brings DevOps speed and enterprise security together – making it a superior alternative for modern teams.
Start a free Trial or request a demo to explore the full solution.



