Introduction
For technical leaders responsible for software security, choosing the right tools is critical. Snyk and Black Duck are two prominent application security platforms, each with a different focus. This Snyk vs Black Duck comparison examines their strengths, weaknesses, and impact on development workflows to help you make an informed choice.
TL;DR
Snyk focuses on developer-friendly scanning of open-source dependencies and containers, whereas Black Duck centers won open source code quality and compliance. Each has advantages but also pain points (from false positives to complex setup). Aikido Security emerges as a superior alternative, combining the strengths of both with minimal noise and seamless integration.
Snyk Overview
Snyk is a cloud-based, developer-first security platform that helps find and fix vulnerabilities in code and dependencies. It initially gained popularity for its open-source dependency scanning and container image security, and has expanded to cover static application security testing (SAST) and infrastructure-as-code checks. Snyk integrates directly into development workflows (CLI, IDE plugins, VCS, CI/CD), providing real-time results and even automated fix pull requests. Its focus on ease of use and actionable remediation advice makes it a go-to for teams looking to embed security early without slowing developers down.
Black Duck Overview
Black Duck (now part of Synopsys) is a software composition analysis tool focused on open source risk management and code governance. It identifies open source components in applications, flags known vulnerabilities, and highlights license compliance issues. The platform generates a comprehensive software bill of materials (SBOM) and enforces open source license policies to ensure compliance. Typically deployed as an on-premises enterprise solution, Black Duck is used by security and compliance teams to monitor third-party code usage. It integrates with development pipelines, but its approach is heavyweight and often requires additional tools for full application security coverage.
Core Security Capabilities
Snyk and Black Duck differ in the core security areas they cover and how they detect issues. Snyk provides a broad suite of application security scanning in one platform. It performs software composition analysis (SCA) to find vulnerabilities in open source dependencies, scans container images for known vulnerable packages, checks infrastructure-as-code configurations for security issues, and even includes static application security testing (SAST) for proprietary code (through Snyk Code). By covering code, dependencies, container layers, and configurations, Snyk aims to catch vulnerabilities across the stack during development.
Black Duck, on the other hand, focuses mainly on open source component analysis. It scours your codebase to identify third-party libraries or snippets and matches them against a comprehensive database of known vulnerabilities and licenses. Black Duck excels at generating an inventory of all open source in your application and flagging any known security issues or license violations in those components. However, it does not natively scan your custom code for bugs (no built-in SAST) or your cloud/IaC setups for misconfigurations.
Its strength is depth in open source risk detection and compliance, but that comes at the cost of a narrower scope: vulnerabilities in proprietary code or environment configurations can go unnoticed unless you add other tools to fill those gaps.
Bottom line: Snyk offers more all-in-one coverage (code, open source, container, IaC) whereas Black Duck delivers deep open source insight but requires supplementary products to address areas like code flaw detection or cloud security. Neither tool performs dynamic application testing (DAST) by default, so runtime vulnerabilities remain out of scope for both.
Integration & DevOps Workflow
A key difference between Snyk and Black Duck is how they fit into modern DevOps workflows. Snyk is delivered as a cloud service (with an optional self-hosted flavor) that easily plugs into continuous integration/continuous delivery (CI/CD) pipelines and developer tools. Teams can connect Snyk to source code repositories (GitHub, GitLab, Bitbucket, etc.) to automatically scan pull requests, or add Snyk steps in build pipelines to fail builds on high-severity issues. Snyk’s IDE plugins allow developers to find vulnerabilities as they code and even auto-suggest fixes. The platform requires minimal setup—no dedicated servers to manage—and updates are handled by Snyk in the cloud. This makes rolling out Snyk relatively quick, and developers can start seeing results (and fixing issues) within minutes of integration.
Black Duck historically runs as a local server within the organization (though Synopsys now also offers a Polaris SaaS option). Integrating Black Duck into DevOps requires more effort: you need to install and maintain the Black Duck scanning engine, its database, and possibly additional components for reporting. CI/CD integration is achieved via plugins or scripts that invoke Black Duck scans during builds or deployments. It supports common build systems and can create tickets or reports (e.g. in Jira) for discovered issues. However, the feedback loop is slower.
Scans can be time-consuming, so teams might run them nightly or at a dedicated pipeline stage rather than on every code change. Black Duck also has IDE integrations available, but they are not as seamless or widely adopted as Snyk’s plugins.
Workflow limitations: Snyk’s cloud-based approach means it’s very easy to deploy, but organizations with strict data restrictions may balk at sending code or dependency data to a SaaS platform. Black Duck’s on-prem model suits those who need everything in-house, yet it introduces significant maintenance overhead and complexity. Black Duck often ends up being used by a central security team as a gating check (with developers addressing findings after the fact), whereas Snyk empowers developers to catch and fix issues continuously as part of their normal workflow.
Accuracy and Performance
When it comes to scan quality and speed, Snyk generally outperforms Black Duck for day-to-day use. Snyk’s scans are optimized for quick feedback – developers can run scans on each commit or pull request without significant slowdowns. Its cloud architecture offloads heavy processing, and incremental scanning means you’re not rescanning the entire codebase every time. Snyk’s static code analysis is also relatively fast thanks to its modern engine. In terms of accuracy, Snyk tends to produce fewer irrelevant alerts.
It incorporates prioritization logic (for example, highlighting vulnerabilities that are actually exploitable in your app) to help reduce noise. False positives can still occur (especially in SAST results), but Snyk’s noise level is lower and more manageable for developers.
Black Duck scans are more heavyweight. An initial scan can be quite slow (often hours for a large codebase) as it combs through every file to fingerprint open source components. Subsequent scans may leverage some caching, but performance remains a concern – many teams avoid running Black Duck on every commit due to the time it takes. Accuracy-wise, Black Duck casts a wide net, which finds lots of potential issues but also leads to more false positives or at least “informational” alerts that developers must sift through. It might flag vulnerabilities in libraries that your application never actually calls, or list dozens of low-risk license notices alongside the critical issues.
Without strong built-in prioritization, the output requires significant triage. Teams often have to define custom filters or spend time whitelisting benign findings to cut down the noise. In short, Black Duck’s thoroughness comes with a cost in scan speed and result volume, whereas Snyk aims for a more targeted, developer-friendly signal-to-noise ratio.
Coverage and Scope
Both tools support a wide array of languages and platforms, but their emphases differ. Language & ecosystem support: Black Duck is language-agnostic in identifying open source components – from web apps to IoT firmware, it can scan virtually any codebase (C/C++, Java, .NET, JavaScript, Python, and more) for known components. Snyk also supports all major programming languages and package managers (JavaScript/Node.js, Java/Maven, Python/Pip, Ruby, Go, .NET, PHP, etc.), but it shines particularly in modern web and cloud-native ecosystems. Essentially, if your project uses common languages and dependency files, Snyk can scan it; Black Duck can handle those plus more obscure or mixed-code projects by using signature-based detection.
Issue types covered: Snyk’s scope has expanded beyond just open source dependency vulnerabilities. It now covers container image vulnerabilities (scanning OS packages and libraries in container builds), infrastructure-as-code security issues (for Kubernetes configs, Terraform, etc.), and even hardcoded secrets in code. Black Duck’s scope is more focused: its core strength is SCA for open source security and license compliance. Out-of-the-box, Black Duck does not check your Terraform scripts for misconfigurations or your code for secret keys – it leaves those areas to other specialized tools.
However, in its specialty of open source and third-party components, Black Duck provides richer detail like license obligations, component age/stability, and comprehensive SBOM exports, whereas Snyk offers those only at a basic level.
To summarize the feature coverage, here is a side-by-side comparison of Snyk vs Black Duck capabilities:
CapabilitySnykBlack Duck: Delivery modelCloud (with hybrid option)Primarily on-premises (SaaS available)Open source vulnerability scanning (SCA)✔ Yes✔ YesStatic code analysis (SAST)✔ Yes (via Snyk Code)✘ No (separate tool required)Container image scanning✔ Yes✔ Yes (for OSS packages in images)Infrastructure as Code scanning✔ Yes✘ NoSecret detection✔ Yes✘ NoLicense compliance✔ Yes (basic info)✔ Yes (extensive features)SBOM support✔ Basic export✔ Full SBOM generationIDE plugins✔ Extensive (many IDEs)✔ Available (limited use)CI/CD integration✔ Wide support✔ Wide supportOn-premise deploymentLimited (only via hybrid broker)✔ Yes (fully self-hosted)
*Note: “Limited” indicates that Snyk is primarily cloud-based, with only hybrid or self-managed options for on-prem use.*
Developer Experience
Adoption by the development team is a key factor in a security tool’s success. Snyk is designed with developers in mind, offering an intuitive interface and tight IDE/VC integration. Developers get immediate feedback on issues in their own environment (IDE pop-ups or GitHub pull request checks), which encourages fixing problems early. The Snyk UI is clean and consolidates all issue types in one place. It provides clear descriptions of vulnerabilities, links to advisories or upgrade recommendations, and even one-click fix pull requests in some cases. The learning curve is low – an engineer can start using Snyk’s CLI or IDE plugin with minimal training.
Noise levels are also manageable; Snyk highlights the most critical issues first so developers aren’t drowning in alerts. Overall, it feels like a tool made to fit into developers’ daily workflow, not a gate to work around.
Black Duck offers a very powerful but less developer-friendly experience. Its interface exposes a lot of data (component names, versions, license texts, etc.), which can be overwhelming for an engineer who just wants to remediate a vulnerability. Many developers encounter Black Duck only via lengthy PDF reports or auto-generated tickets rather than through an interactive UI. Setting up Black Duck isn’t as simple as running a quick scan; it often involves onboarding projects into a server, configuring policies, then interpreting the scan results. The UI, while capable, is geared more toward security analysts who need to audit open source usage and drill down into details.
As a result, the average developer might find it cumbersome to navigate, or they rely on the security team to filter and relay issues. The high volume of findings (including minor license warnings or duplicate vulnerability entries across components) can lead to alert fatigue. In short, Black Duck tends to be a heavyweight tool that may require training or a dedicated specialist to use effectively, whereas Snyk is plug-and-play for most developers.
Pricing and Maintenance
Cost is an important consideration for any enterprise tool. Snyk offers subscription-based pricing with tiered plans (including a free tier for small projects). Enterprise pricing is typically based on the number of developers, projects, and product modules (Snyk Code, Snyk Open Source, etc.) in use. This can be cost-effective to start, but as usage grows there can be surprises – for example, hitting a limit on projects or scan frequency might require moving to a higher tier or purchasing add-ons. Some organizations have reported that heavy usage incurs additional charges. In general, Snyk’s pricing is transparent but not cheap for large-scale deployments.
On the plus side, Snyk being SaaS means near-zero infrastructure overhead: no servers to maintain or databases to update (Snyk handles all updates to its vulnerability database). Your team’s maintenance effort is basically just managing integrations and reviewing results, rather than babysitting the tool itself.
Black Duck is usually sold as a high-end enterprise solution and comes with a correspondingly high price tag. Licensing is often annual and may be based on number of applications, code bases, or even total lines of code audited. There’s no free tier; using Black Duck is a significant commitment. Beyond the licensing cost, companies need to factor in infrastructure (e.g. provisioning and running the Black Duck server, database, and any additional components) and personnel time. It’s not uncommon to allocate a dedicated admin or engineer to manage Black Duck, handle upgrades to its vulnerability database, and tune the system (for performance and for filtering out irrelevant results).
These hidden labor costs mean the total cost of ownership for Black Duck can be quite high. Moreover, if you need additional Synopsys products (like a separate static code analyzer or Risk Management module) to complement Black Duck, those come with their own costs and upkeep.
At scale, Snyk tends to have lower maintenance overhead but can become pricey as you add more developers or projects, while Black Duck has a large upfront cost and ongoing operational overhead. Notably, newer solutions like Aikido Security aim to address these pain points by offering flat, predictable pricing and a fully-managed platform (no infrastructure to maintain), ensuring that security costs don’t balloon as your development team grows.
Snyk vs Black Duck: Pros and Cons
Below is a quick summary of each tool’s pros and cons:

Snyk Pros:
- Developer-centric – Integrates seamlessly into dev tools (CLI, IDE, SCM) and workflows
- Comprehensive coverage – SCA, SAST, containers, IaC, etc., in one unified platform
- Fast, actionable scans – Quick results with minimal slowdown; provides guided fixes (even auto PRs)
- Low maintenance – Cloud-hosted with automatic updates and very little setup effort
Snyk Cons:
- Costly at scale – Subscription costs can rise quickly for large teams or extensive use
- False positives exist – Some noise in results (especially in SAST) still requires tuning and review
- Limited compliance features – Not as strong in license audit and compliance reporting as Black Duck
- Cloud dependency – Relies on SaaS infrastructure; fully on-prem use is limited for sensitive environments

Black Duck Pros:
- Deep open source analysis – Thorough identification of all OSS components and vulnerabilities (rich knowledgebase)
- Strong compliance & SBOM – Excellent license risk management and automated SBOM generation for regulations
- Broad language support – Works with virtually any codebase or language (can even scan binaries for known components)
- On-premise option – Can be self-hosted on your infrastructure for full data control and custom integration
Black Duck Cons:
- Complex setup – Deployment and integration are time-consuming, requiring dedicated infrastructure and admin effort
- Slow feedback – Scans are relatively slow, meaning security issues may be reported late in the development cycle
- High noise level – Large volume of findings (including false positives and low-priority issues) can overwhelm developers
- Developer unfriendly – Less intuitive UI and workflow for engineers; often used primarily by security/compliance teams
- Expensive – High licensing costs and significant maintenance overhead increase the overall TCO
Aikido Security: The Better Alternative
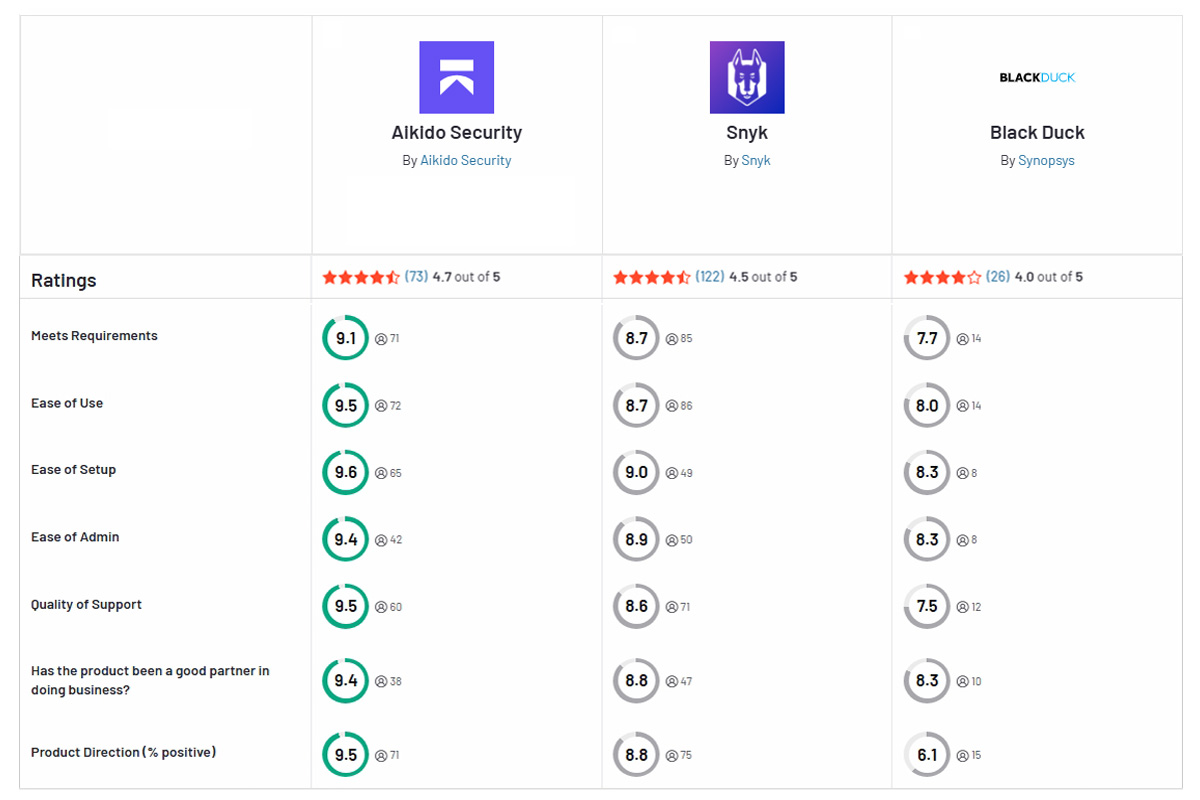
Aikido Security is a unified AppSec platform that combines Snyk’s developer-first approach with Black Duck’s comprehensive open-source coverage—without their downsides. It scans proprietary code and open source components (even container images) together, yielding broad coverage with minimal noise thanks to smart false-positive filtering.
Aikido integrates effortlessly into CI/CD and developer tools, ensuring security is continuous and frictionless. With flat-rate pricing and no infrastructure to maintain, it delivers enterprise-grade security without surprise costs or complexity. For technical leaders, Aikido represents the best of Snyk and Black Duck in one trustworthy, efficient solution.
Start a free Trial or request a demo to explore the full solution.



