When the first cryptographically relevant quantum computer (CRQC) arrives, it won’t come with a press release. One day in the not too distant future, a nation-state, organized crime group or unhinged megalomaniac billionaire will quietly spin up the capability, and in eight hours or less, your TLS (Transport Layer Security) RSA-2048 encryption is gone. Like a hot knife through butter.
And here’s the kicker: there’s no such thing as quantum incident response. You won’t see a red light flashing in your SOC (Security Operations Center) or NOC (Network Operations Center). You won’t get an alert about someone ordering a tap on an encrypted TCP API connection. The breach won’t look like a breach until it’s far too late. We can “see” a DDoS attack and we can mitigate its effects with packet scrubbing and clever routing rules. But the “silent boom” that occurs with a quantum attack is like a lot of other cybersecurity events. It takes place with no real observable indicators. It’s not like someone is forgetting to set “quantum-tracking=true” in some environment variable or Windows registry setting.
As a member of the World Economic Forum Quantum Security Working Group for the last couple of years, we have been meeting periodically to discuss what we can do to promote readiness and awareness of the risks that accompany the innovations in quantum computing (not all of which are centered around breaking asymmetric encryption used in PKI and modern day web applications and services). What can we do now to prepare for then?


Our working group published a readiness toolkit in 2023 that is still a good starting point for many organizations who want to understand the capabilities needed for a post-quantum world. More recently there is also a whitepaper with guidance for the financial services industry on opportunities and challenges that was published in July of this year. Both have the obligatory TL;DR executive summaries and both are over 13 pages for those who don’t mind spending a few minutes reading something interesting about the subject.
Unfortunately there is also a lot of FUD and snake oil being published around this topic, so it’s best to not believe those click-bait articles and posts that impugn the experts and declare that RSA (Rivest–Shamir–Adleman, a family of public-key cryptosystems that is one of the oldest widely used for secure data transmission) is already dead and (cryptographically) broken. For certain key lengths, yes. But for RSA 2048 there is no reason to believe that your communications are currently being spied upon with the aid of quantum computers.
Keep in mind that it’s much easier to get at the sensitive cleartext data in other ways. This XKCD comic was one of the first items shared on one of our working group meetings, for example, and captures the spirit of hacking and technology quite nicely: https://www.explainxkcd.com/wiki/index.php/538:_Security

Why You Won’t See It Coming
Today’s monitoring tools detect suspicious logins, malware signatures, DDoS spikes. They don’t detect “quantum decryption in progress.” Once a CRQC exists, any encrypted data intercepted (in real time or from years of stored traffic from BGP hijacking events, first demonstrated at a DEF CON 16 session in 2008) can be silently decrypted without your knowledge.
Your Only Defense: Preparation
You can’t respond to what you can’t detect. The only winning move is to migrate away from ciphers and algorithms susceptible to quantum attacks before the threat materializes (experts continually place this at anywhere from within 5 to 10 years from now). That starts with a complete cryptographic inventory in order to support what is referred to as “crypto agility” or the ability to introduce NIST-approved PQC (Post-Quantum Cryptography) algos when they are made available:
- Discover – Map every cipher, algorithm, key length, and protocol in use. You need to be able to support TLSv1.3 if you want to use quantum-resilient algos.
- Classify – Identify quantum-vulnerable components and data that will need to be protected by PQC. This will vary from business to business and industry to industry.
- Prioritize – Tackle high-value, long-lived data first. Not all sensitive data remains sensitive. The casting announcement for the latest Marvel movie is uber super secret squirrel kind of stuff (I know, because I was the CISO for Marvel previously). Until it isn’t and the announcement is made and the information is reclassified as public information.
- Migrate – Begin a shift to post-quantum cryptography (PQC) such as CRYSTALS-Kyber and Dilithium. Some situations might best be addressed with a mitigation plan instead of remediation plan. You can, for example, put a PQC proxy in front of some of your website applications, services and APIs in order to reduce the threat exposure.
The Quantum Breach Window
When CRQC day comes, the “quantum breach window” opens silently and globally. Those without an inventory will scramble blindly with their hair on fire (figuratively speaking); and those with one will execute or accelerate a migration plan they’ve already written and tested. Maybe you think your communications are not worthy of having a “quantum tap” purchased from the owner of the CRQC. Maybe you don’t have secrets that need to stay secret for more than a few hours, so you rotate your passwords every 7 hours if the CRQC can crack the encryption and learn your password in 8 hours. But know for sure that this milestone will be a disruption of geological proportions. A veritable plate tectonic shift in global intelligence and the management of anything sensitive or secret.
Who knows, maybe we’ll see a revival of the passenger carrier pigeon for “quantum safe” communications channels. Or a return to having bicycle couriers speeding around downtown NYC with USB thumb drives in their bags (we actually saw this when ICBC was disrupted by a cyber attack in 2023 in order to close open trades and orders).
By the time you realize quantum decryption has happened, it will be ancient history. Your data will already be in someone else’s hands. Quantum incident response isn’t real. Quantum readiness is. Start now.
Quantum Readiness
There are some easy things that you can do now in the direction of inventorying your data and understanding which assets and applications are candidates for PQC. One of which is to simply figure out how many of your internet-facing assets are using PQC algos. A simple website has been created by Aikido to help with this step: https://quantum.aikido.io
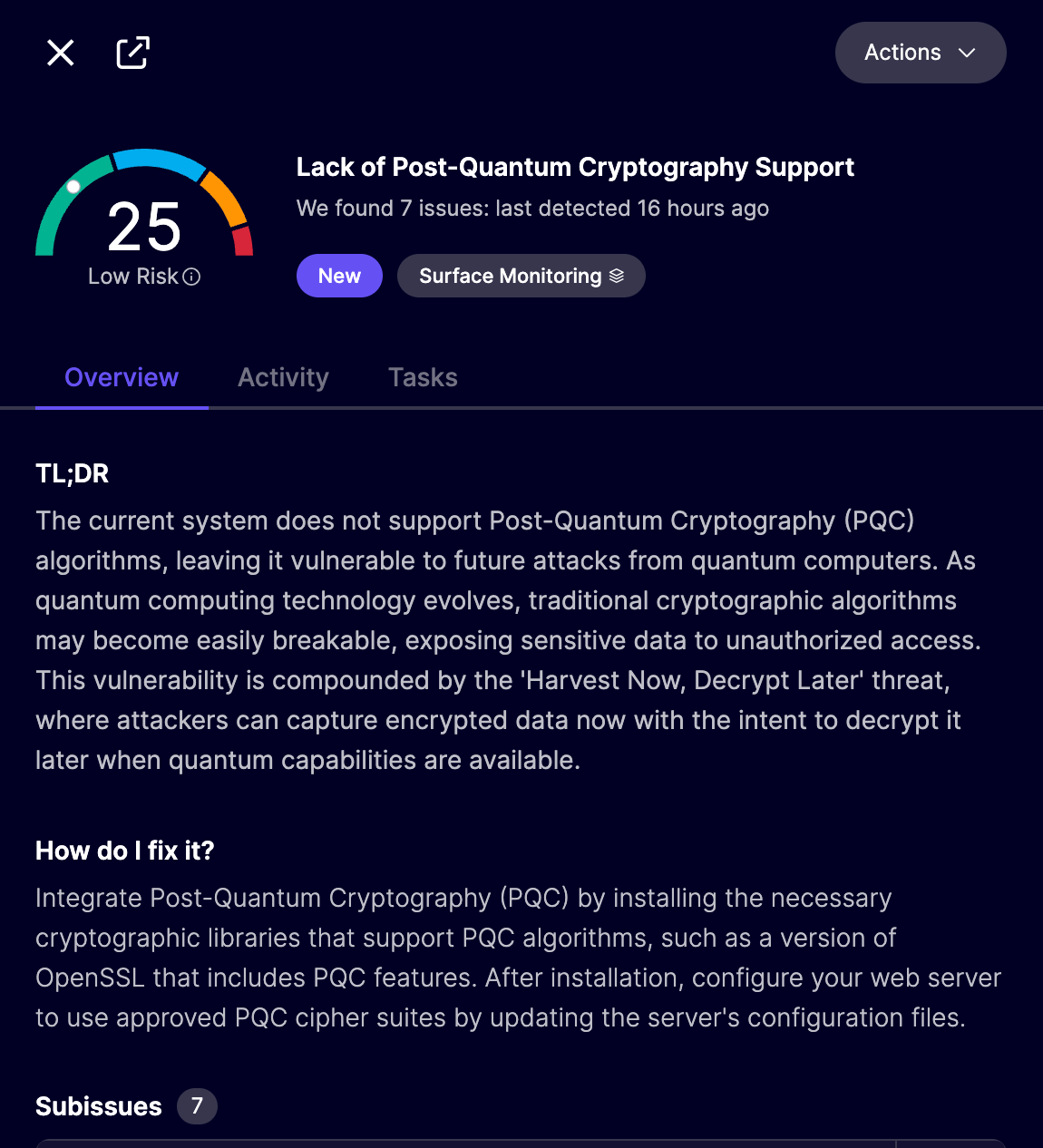
Aikido Security has added a check for Post-Quantum Cryptography to their Attack Surface Monitoring module. After you sign up and add the domain(s) that you would like to monitor, if you are not yet using Post-Quantum Cryptography you should see an issue in your issues feed like this one:

When clicking on that issue, details similar to the following will be shown:
Make it so
As with many Star Trek captains, we wish it were as simple as uttering the command “Make it so…” but of course this is not our current reality or timeline (maybe ChatGPT v5 can do this before too long??). So your question will naturally be: “How do I upgrade my site to be Post-Quantum Safe?” and there are a couple of different directions to take with the answer:
- Proxy it. Cloudflare offers quantum-resistant encryption using TLSv1.3 with ML-KEM that protects websites and APIs against future quantum threats without configuration changes. More information here: https://www.cloudflare.com/pqc/
- Compile it. Most web servers (and applications and APIs too of course) rely on OpenSSL for their implementation of TLS algorithms and ciphers. Using the Open Quantum Safe provider for OpenSSL (3.x) is a path to serving quantum-safe cryptography. More information here: https://github.com/open-quantum-safe/oqs-provider and here: https://medium.com/be-tech-with-santander/how-to-configure-post-quantum-cryptography-in-your-web-server-fcf79e05e526
The quantum future isn’t waiting. Neither should you.
Data Point
Chrome added ML-KEM as default for TLSv1.3 in version 124 (May of 2024). Earlier than that was just experimentation and not real PQC in my view.
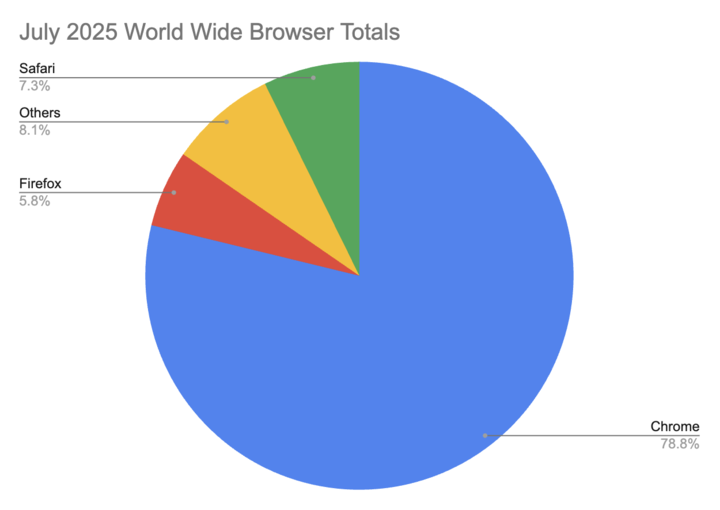
According to StatsCounter, the aggregated percentage for Chrome versions 124 or higher in July 2025 is 43.30%. Given that MS Edge is also Chromium-based, the aggregated percentage for Edge versions 124 or higher in July 2025 is 11.29%. So we have some reasonable movement on the client side of things, but where do we sit with providing PQC on the server side of things?
Notes:
Safari does not currently support Post-Quantum Cryptography (PQC) for general web browsing (TLS connections). While Apple has implemented PQC in iMessage (PQ3 protocol) and is likely working on it for Safari, broad default support in Safari for all TLS traffic wasn't explicitly confirmed as of early 2025.
Firefox does support post-quantum cryptography (PQC), but it's not enabled by default. You need to manually enable it through Firefox's settings. Specifically, Firefox supports the hybrid PQC key exchange algorithm X25519MLKEM768.
References:
https://help.aikido.dev/dast-surface-monitoring/attack-surface-monitoring
https://gs.statcounter.com/browser-version-market-share/desktop/worldwide/
https://github.com/open-quantum-safe/oqs-provider
https://www.cloudflare.com/pqc/
https://www3.weforum.org/docs/WEF_Quantum_Readiness_Toolkit_2023.pdf
https://media.defense.gov/2021/Aug/04/2002821837/-1/-1/1/Quantum_FAQs_20210804.PDF



