Whether you’re teaching computer science, software engineering, or cybersecurity, Aikido equips your students with enterprise-grade security tools, at no cost.
Aikido for Education brings the same platform trusted by professional teams into the classroom, helping students learn by doing. Teachers can integrate it into their courses to give students hands-on experience with real-world security challenges, without adding complexity or cost.
Curious about the “why” behind this program? Read our story here → Why We Launched Aikido for Education.
Why Teachers Use Aikido
Aikido helps professors bring theory to life by demonstrating real vulnerabilities instead of static slides. It enables them to design hands-on assignments where students work with real code, cloud configurations, and runtime security. It also allows tracking of learning outcomes and progress while preparing students with practical, job-ready experience.
For Educators
Step 1 – Set up a workspace and teams
Start by creating a workspace and grouping students into teams, just as security teams do in industry. For example, a class of fifty can be split into five teams of ten or ten teams of five. Connect repositories such as course apps, forks of open-source projects, or dedicated teaching repos to give students a sandbox where they can discover and remediate issues.
Screenshot: one-click sign-up screen showing how professors can create an account and connect repositories securely with read-only access.
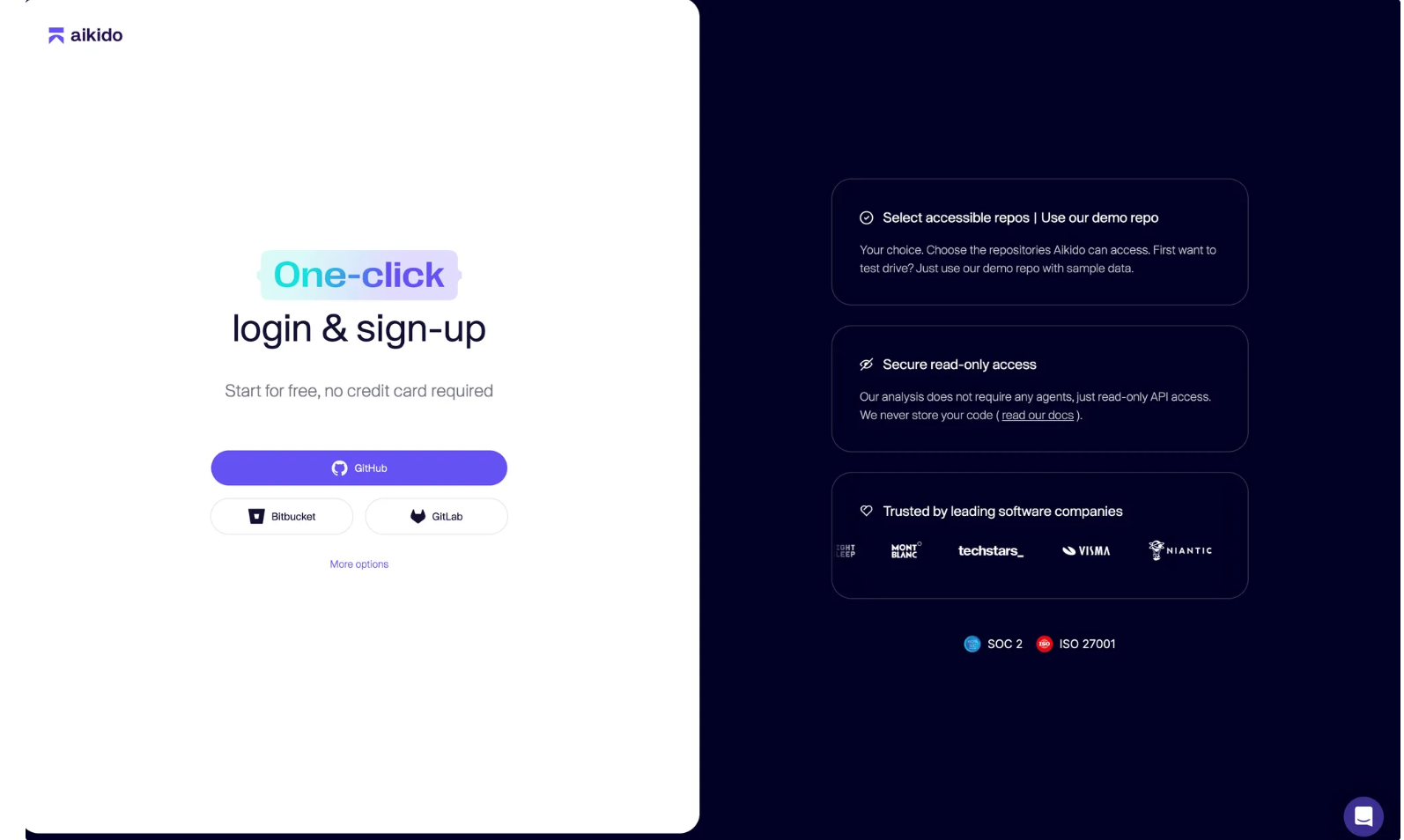
Step 2 – Invite students
Invite students into the workspace and assign roles that define what they can access. This gives them experience with the access controls and accountability practices used in professional environments while keeping the classroom organized.
Screenshot: invite user flow showing how professors can assign students to specific teams and responsibilities across repositories, clouds, and containers.
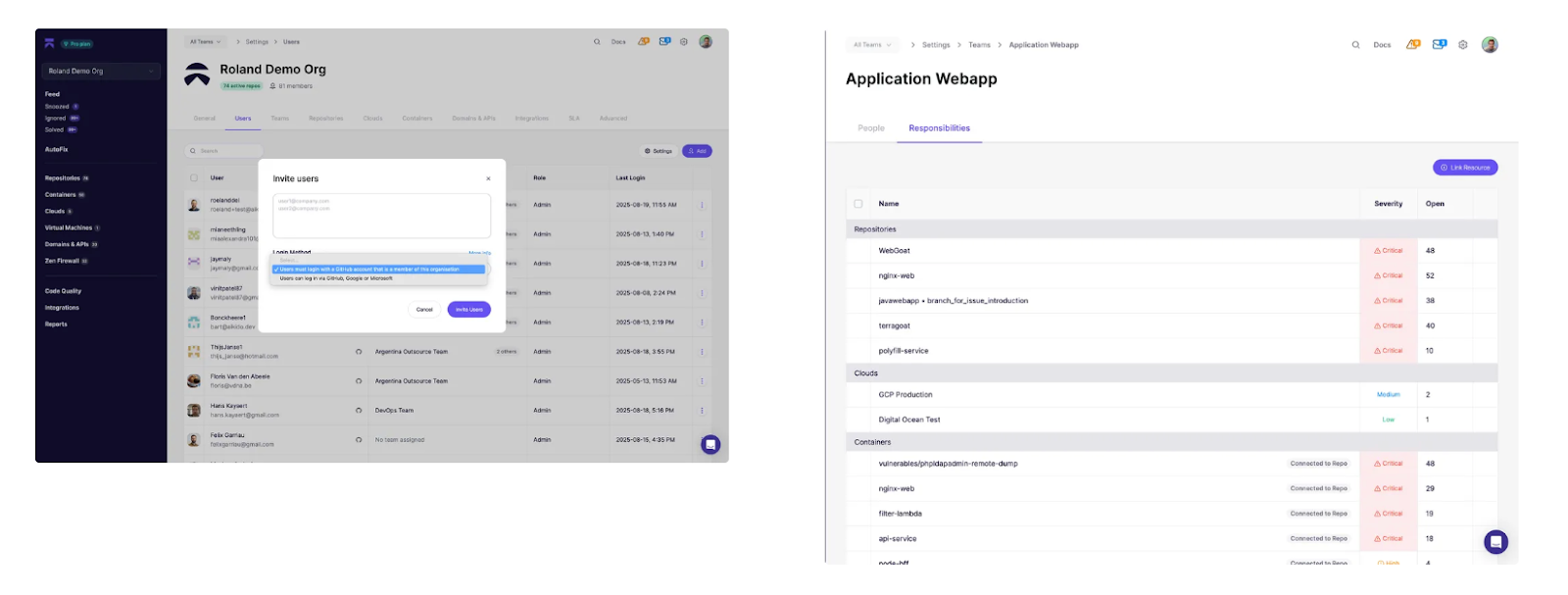
Step 3 – Run the first scan
Once repositories are connected, Aikido automatically scans them and populates the main feed within minutes. Use this in class to show students a professional security dashboard and walk through the categories of findings together, turning abstract concepts into visible results.
Screenshot: the Aikido main feed after the first scan, showing a range of issues across categories with severity levels, fix time estimates, and status filters.
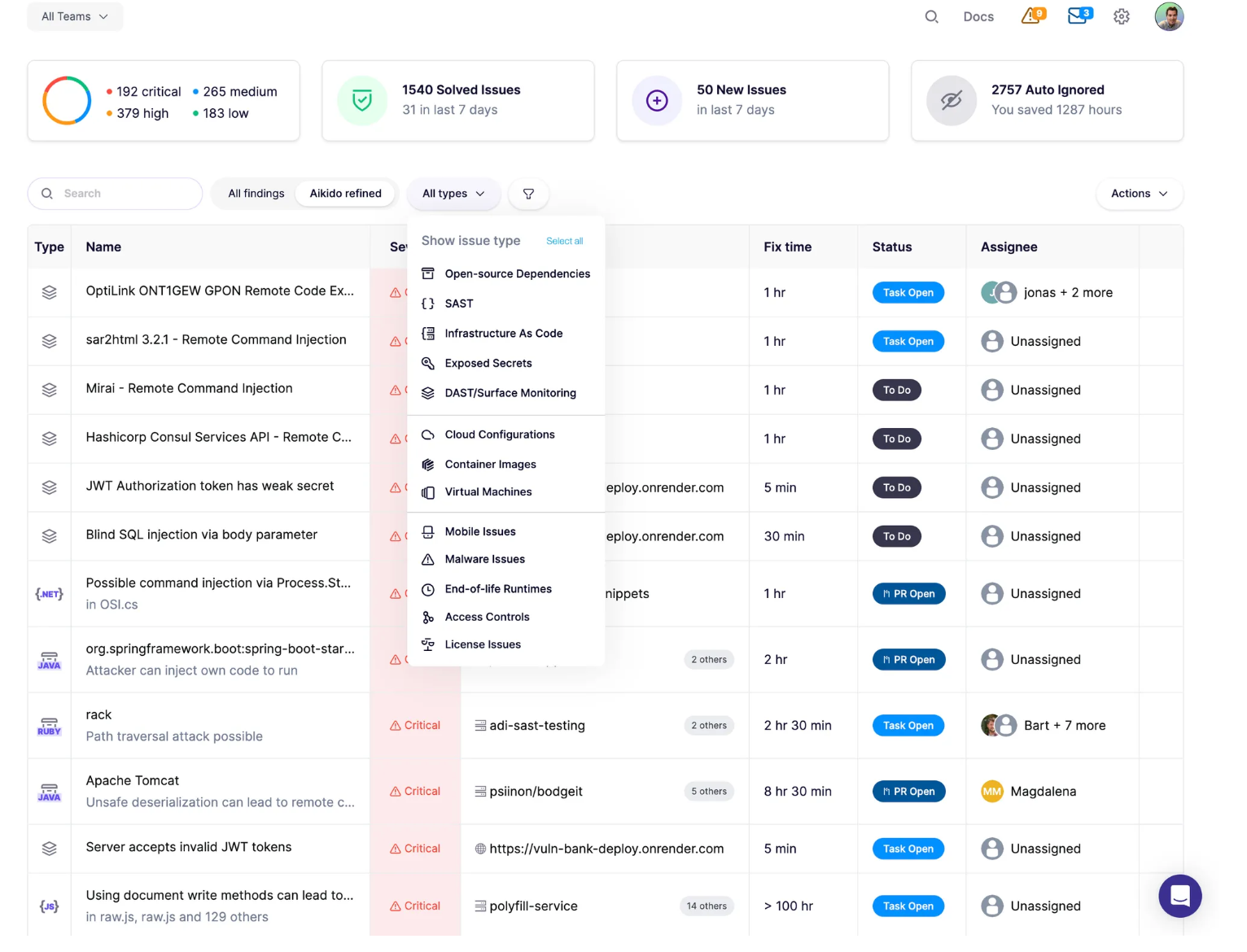
Step 4 – Explore open-source dependencies
Open-source dependencies form the backbone of most modern software, but they also introduce inherited risks. Students learn how CVEs affect supply chains and why patching matters. A simple exercise is to assign each team a vulnerable package, have them patch it, and rerun the scan to confirm the fix.
Screenshot: vulnerable open-source dependencies highlighted in the dashboard, with detailed CVE information

Reduce false positives
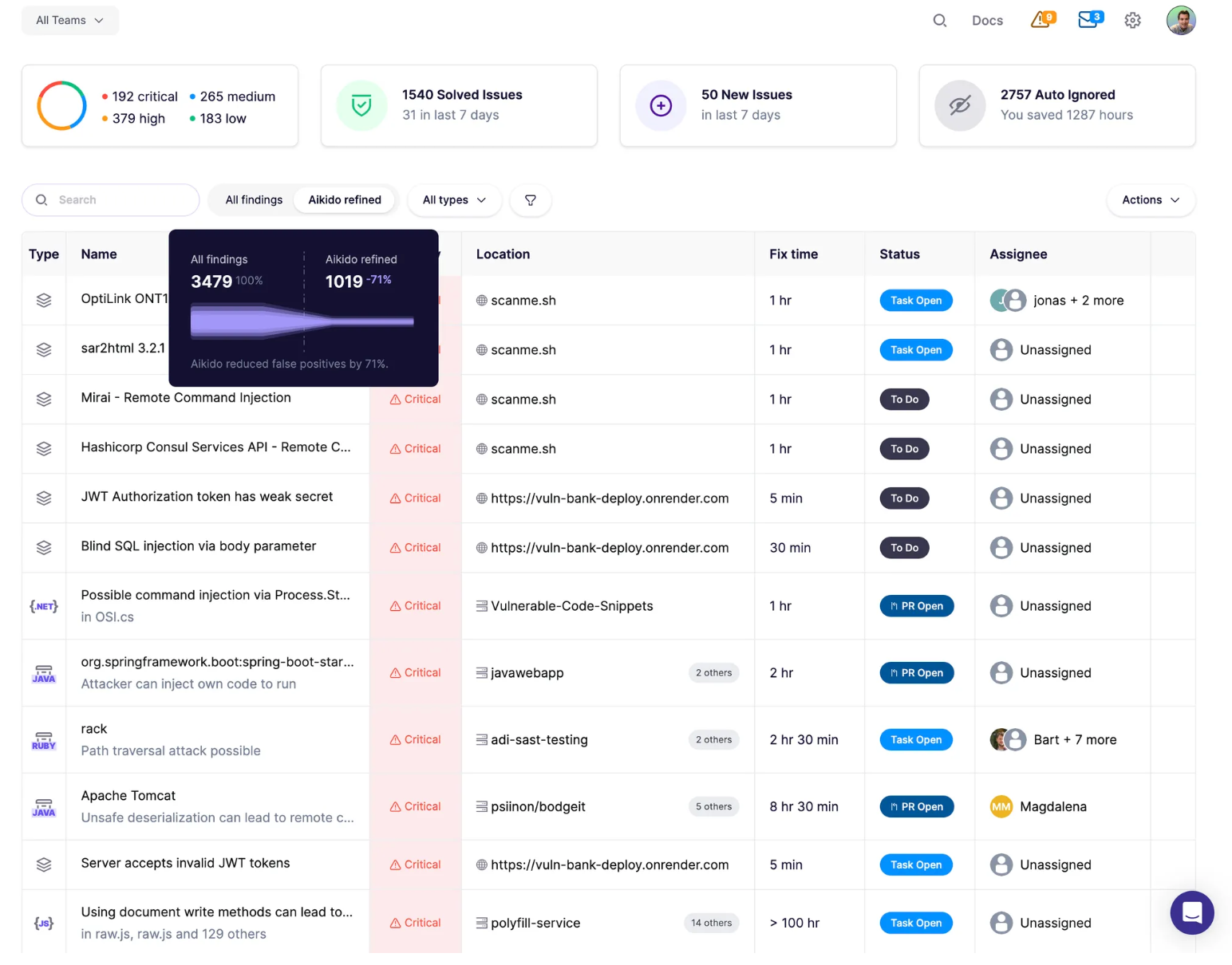
Security alerts can be overwhelming, and many are false positives. Students learn how to focus on actionable issues by comparing the “All Findings” view with the “Aikido Refined” results.
Screenshot: comparison between all findings and Aikido’s refined results, showing how false positives are reduced by 71% to highlight actionable vulnerabilities.
Reachability Analysis
Not all vulnerabilities are exploitable. By reviewing dependency paths, students see which CVEs are actually reachable in their code and learn how to prioritize fixes based on real risk.
Screenshot: reachability analysis graph showing dependency chains for CVE-2019-10746 and whether the vulnerable package is actually used in production.
Step 5 – Analyze cloud configurations and compliance
Cloud misconfigurations like open buckets or overly permissive IAM roles are among the most common causes of breaches. Students learn how technical mistakes map directly to frameworks such as SOC2, ISO 27001, and OWASP Top 10. Use a demo cloud environment to show misconfigs, then let students remediate issues until compliance scores improve.
Screenshot: cloud misconfiguration results showing connected accounts across AWS, Azure, GCP, and DigitalOcean, with detailed findings for an Azure demo environment including disabled security logging and remediation guidance.

Asset Graph + Cloud Search
By being able to see how misconfigurations connect to each other, students can better understand how better visibility and context can help to mitigate risks. Aikido enables natural language queries across the entire cloud inventory so that students can simply describe what they want to find, and the system translates that into a series of logical steps. For example, if a student asks “show me EC2 instances with access to S3 buckets,” Aikido maps out the relationships between instances, IAM roles, bucket policies, and permissions, then presents the results step by step.
Screenshot: Cloud Search results showing natural language query “data touching US IPs” translated into step-by-step checks across EC2 instances, load balancers, RDS databases, S3 buckets, and Lambda functions.
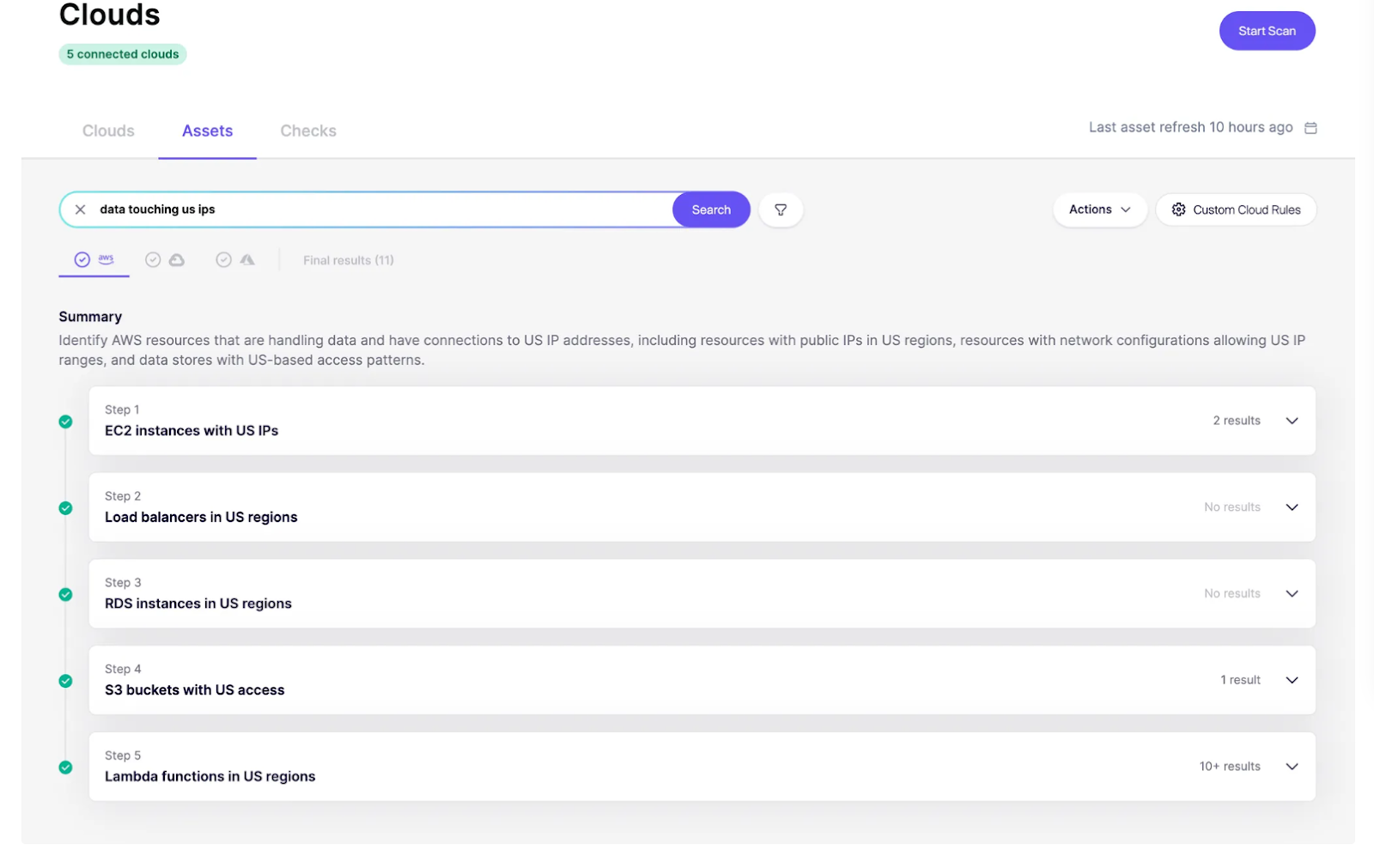
Step 6 – Review Domains & APIs
External-facing apps and APIs are often the first place attackers look. Students can learn how DNS misconfigs, weak headers, and exposed endpoints create risk. Run a scan on a small web app, then ask students to apply mitigations such as authentication or stricter CSP headers. Rescan to compare improvements.
Screenshot: list of connected domains and APIs, categorized by type, with severity levels and open issues. Examples include REST APIs missing authentication, front-end apps with high or critical risks, and domains marked safe with “No risk.”
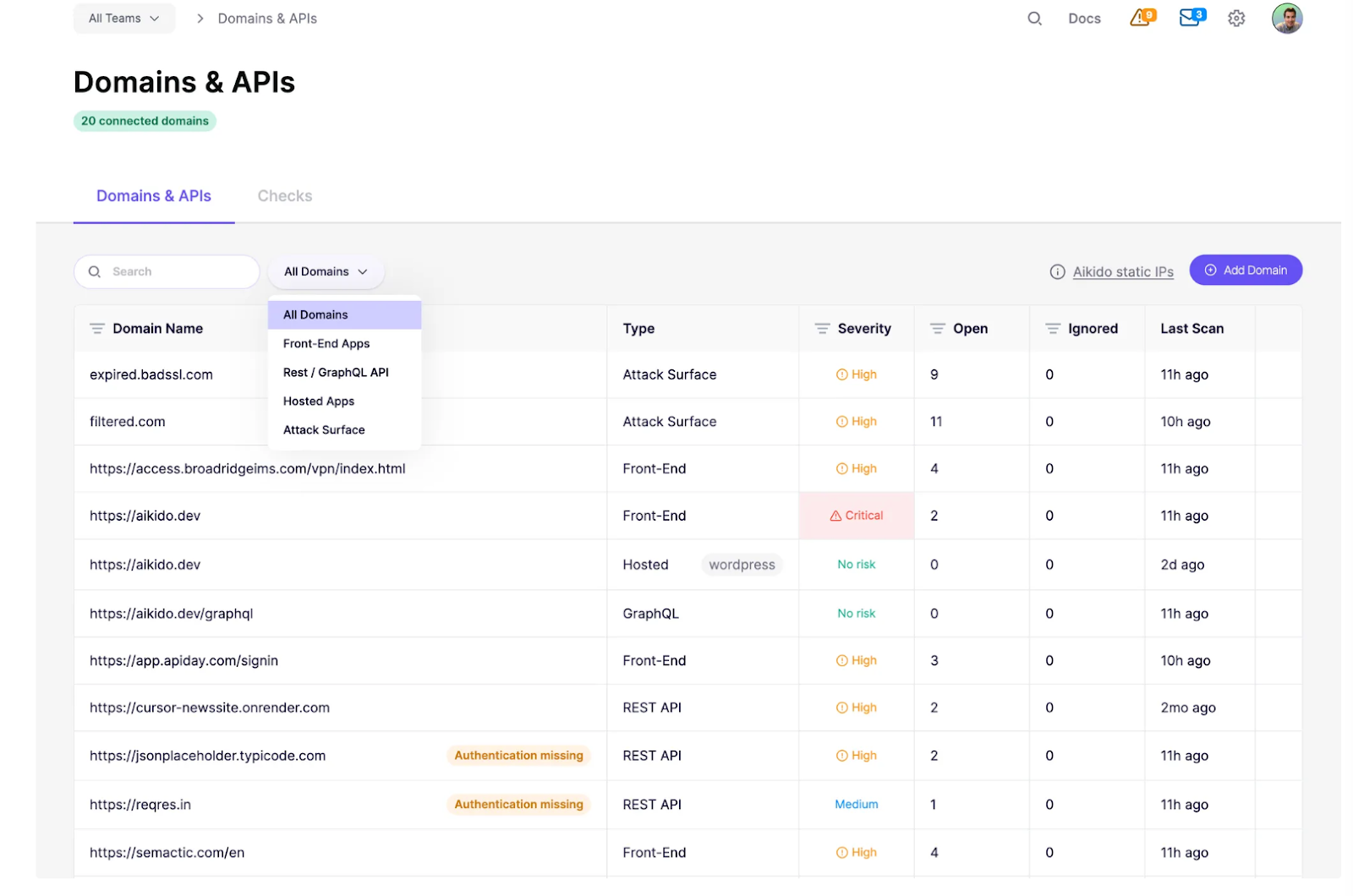
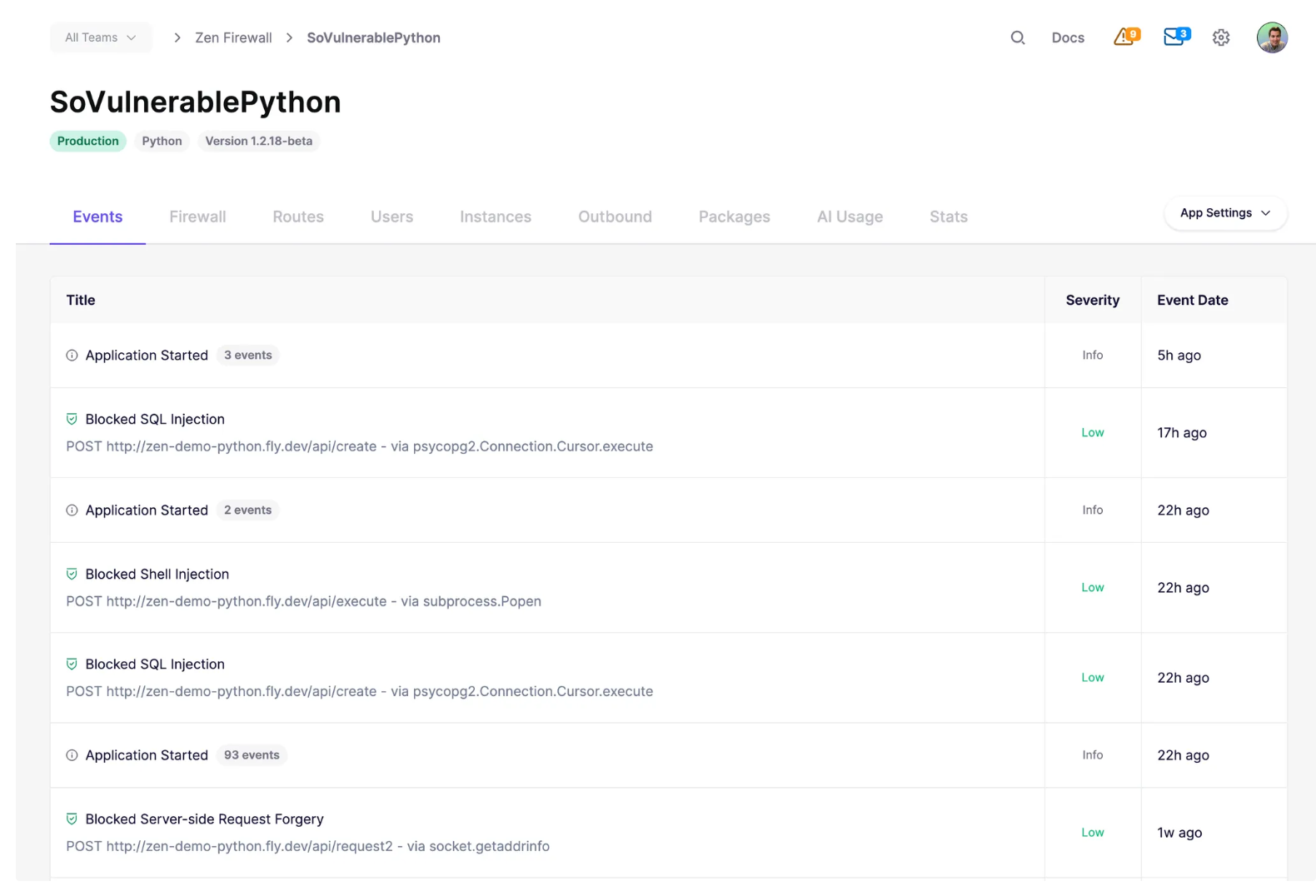
Step 7 – Enable runtime protection
Static scans highlight potential issues, but runtime protection shows what happens when attacks are attempted in real time. With Zen Firewall enabled, students can see SQL injection or SSRF attempts blocked instantly. Running the same attack without protection provides a striking contrast.
Screenshot: Zen Firewall dashboard showing real-time logs of blocked SQL injections, shell injections, and SSRF attempts against a vulnerable Python application.
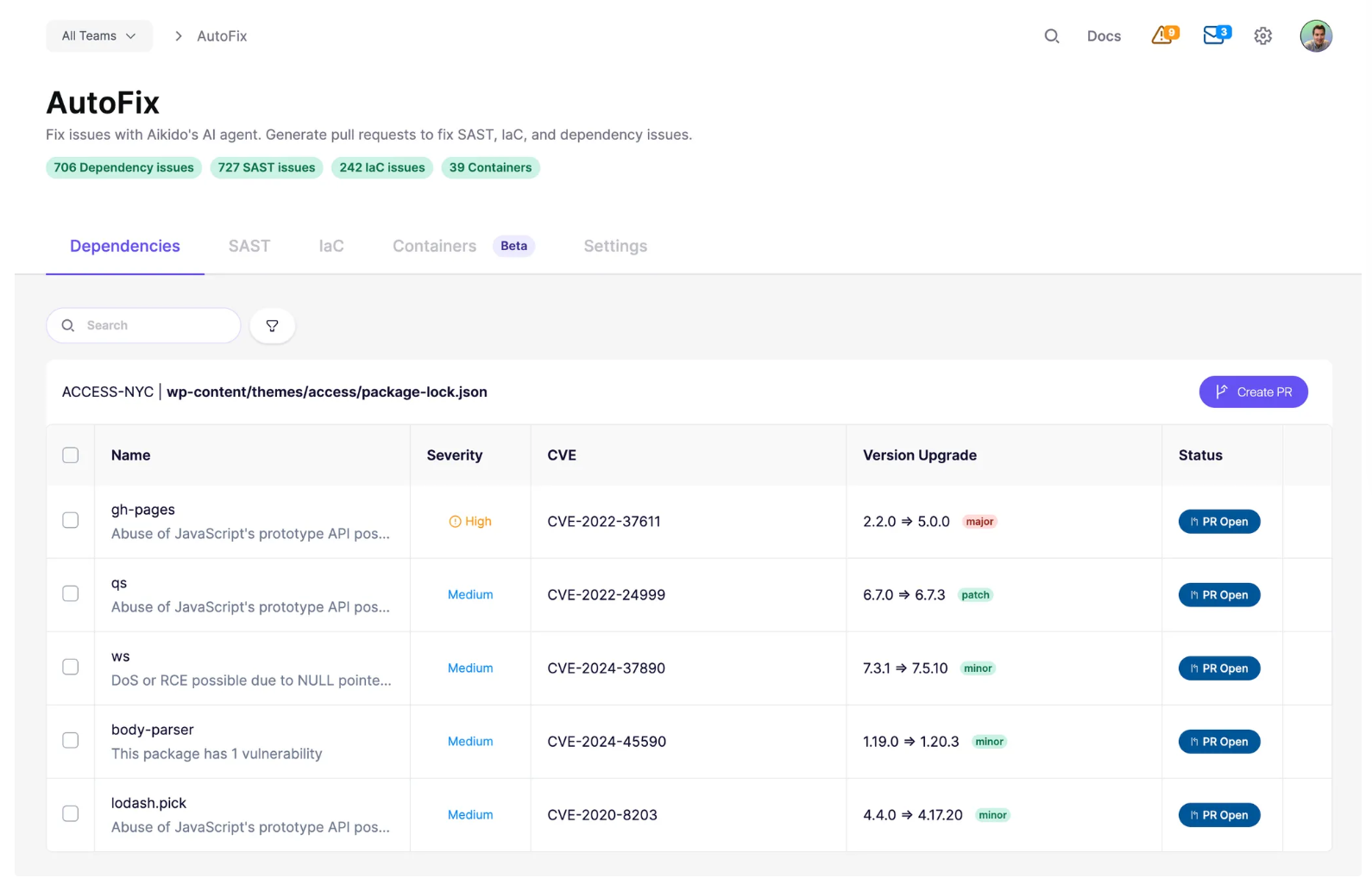
Step 8 – Practice remediation with AI AutoFix
Fixing vulnerabilities is as important as finding them. AutoFix generates AI pull requests across dependencies, SAST, IaC, and containers. Students can attempt their own fixes first, then compare with AutoFix to discuss trade-offs and when to trust automation.
Screenshot: AutoFix dashboard showing dependency vulnerabilities with CVEs, recommended version upgrades, and automatically generated pull requests ready for review.
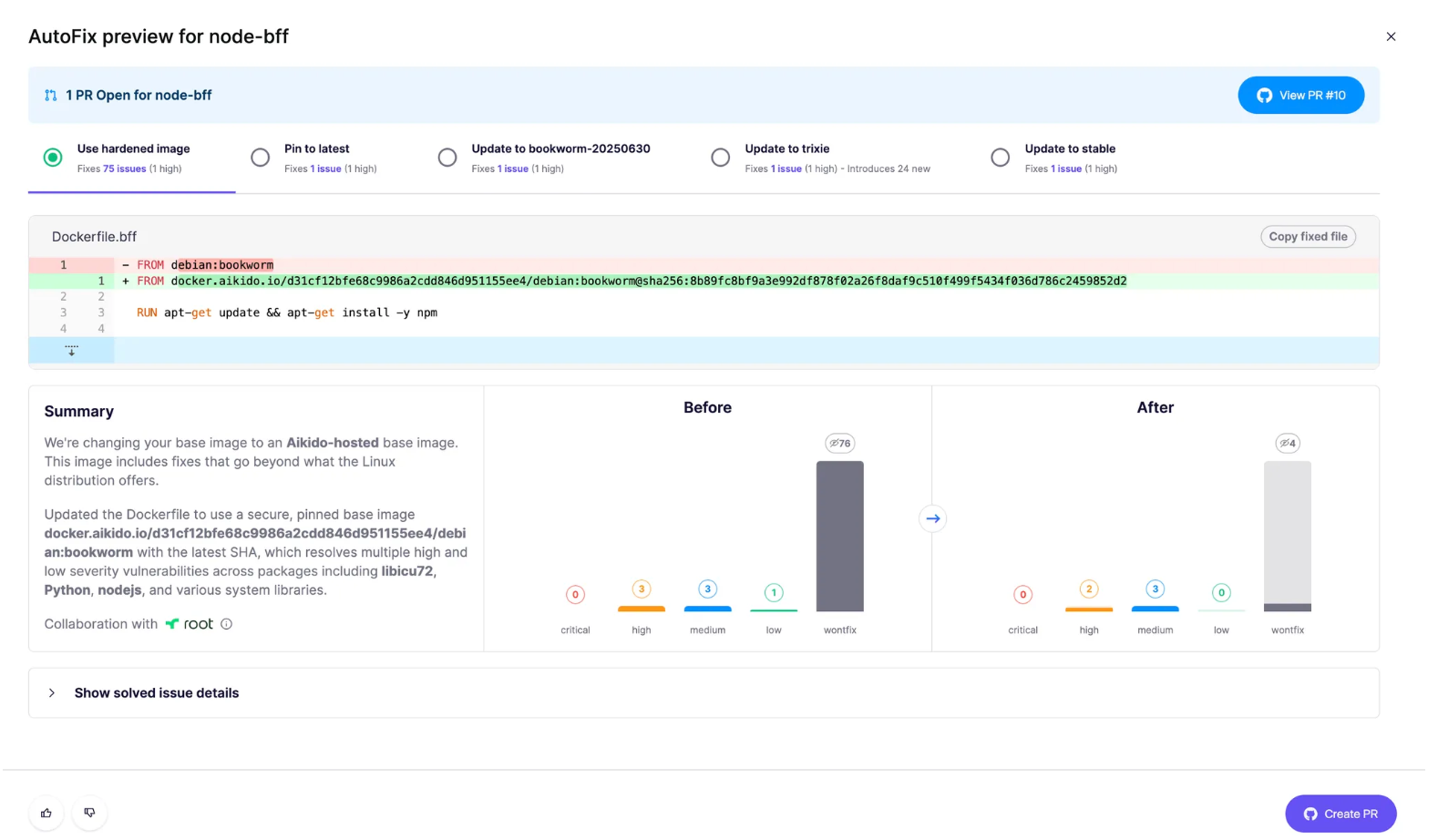
Example: Hardened Docker images
Screenshot: AutoFix replacing a vulnerable base image with a secure, hardened alternative, reducing issues automatically.
Step 9 – Monitor progress
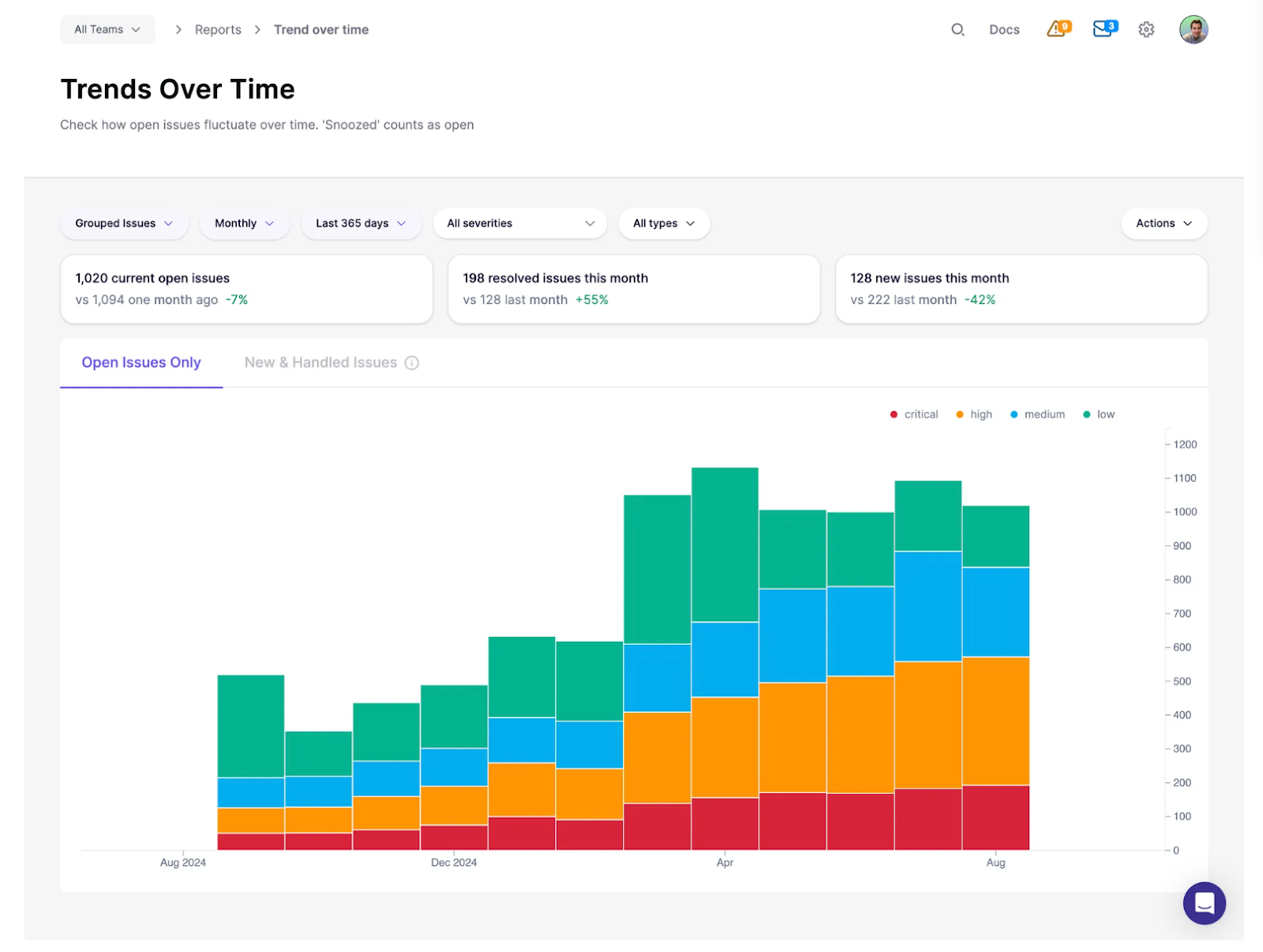
Security is about long-term patterns, not one-off fixes. Aikido’s “Trends Over Time” report shows how unresolved issues accumulate, while team comparisons highlight performance across groups. Use these reports to spark classroom competition and discussions on continuous improvement.
Screenshot: Trends Over Time report showing how open issues fluctuate across severity levels, making it clear when vulnerabilities are accumulating versus being remediated.
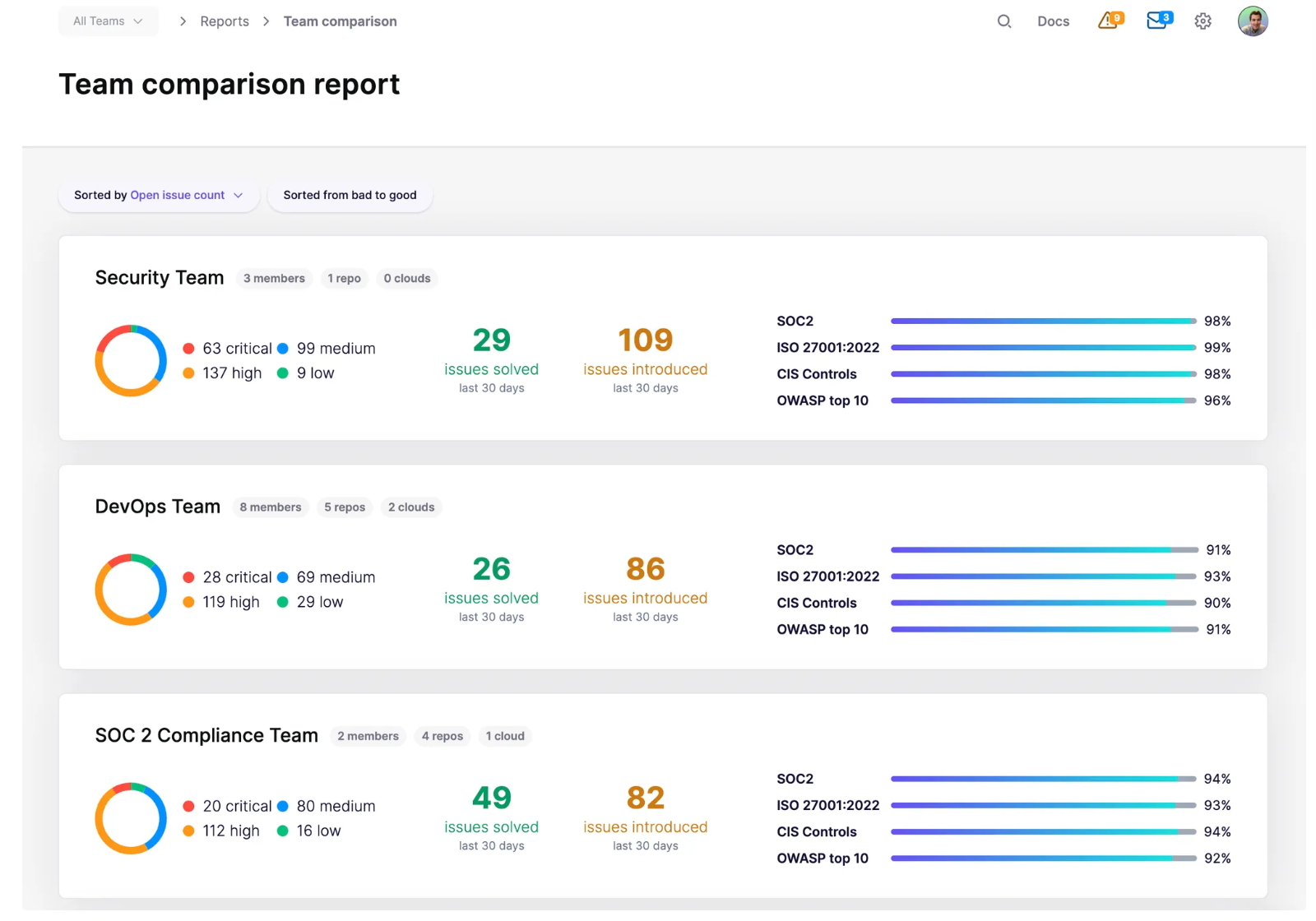
Screenshot: Team comparison report displaying solved versus introduced issues across groups, alongside compliance alignment scores, allowing professors to benchmark progress and create classroom competitions.
Step 10 – Advanced modules
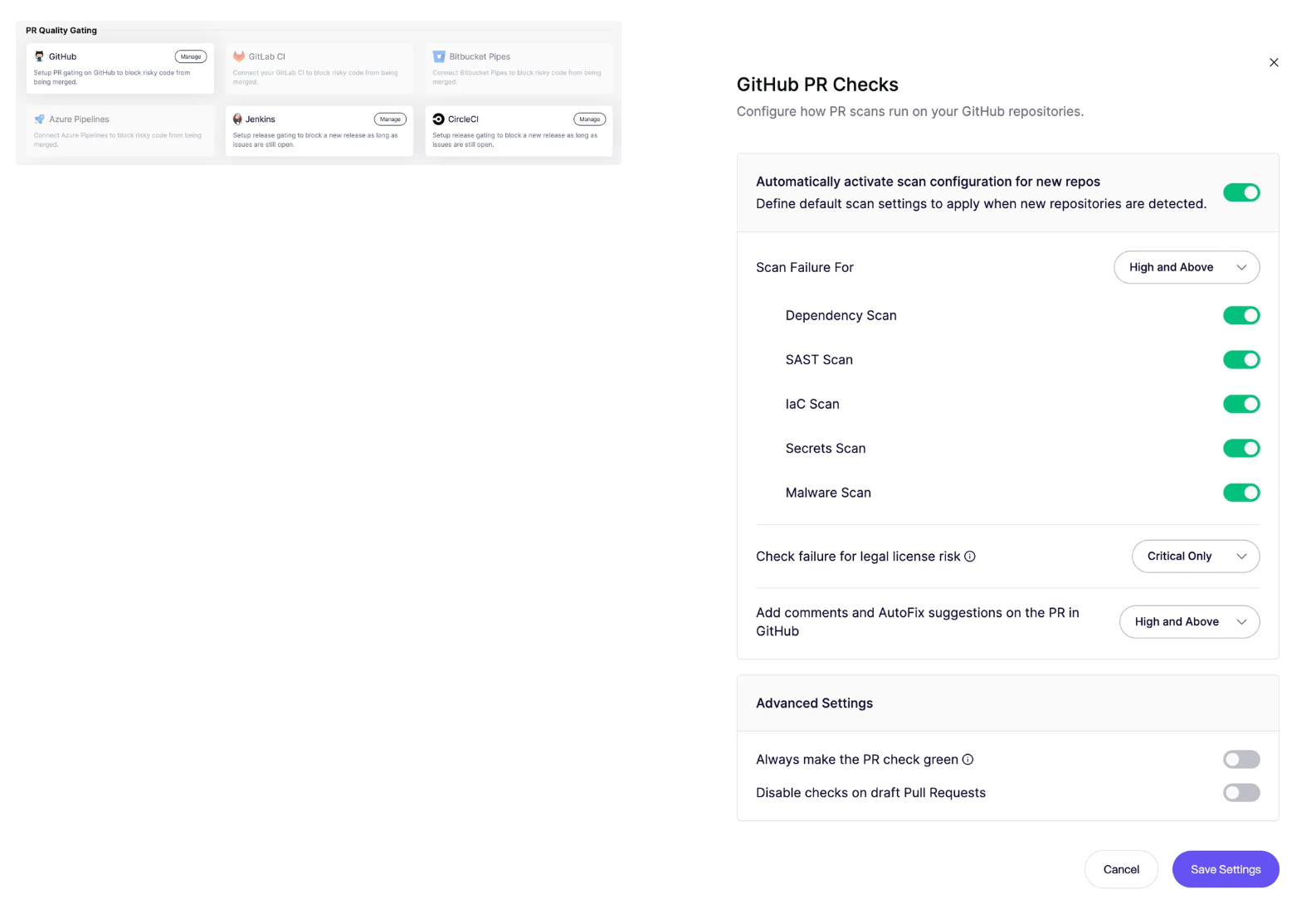
PR Gating
In professional teams, insecure code is blocked before it reaches production using PR gating. Students can learn how to use PR gating, preventing merges that introduce vulnerabilities above a chosen severity threshold.
Screenshot: PR gating configuration screen showing how pull requests can be blocked if they introduce vulnerabilities, with detailed controls for scan types, severity thresholds, and CI/CD integrations.
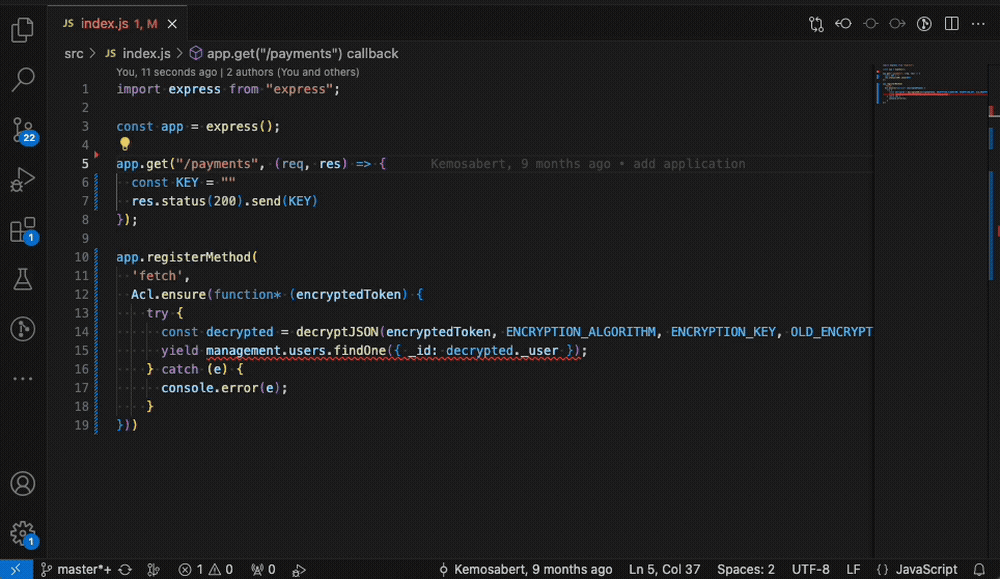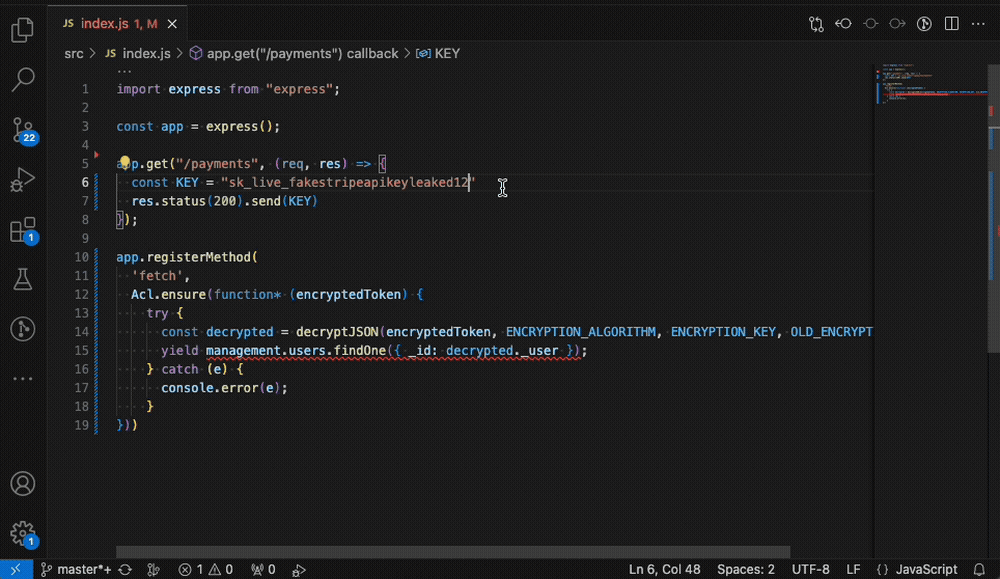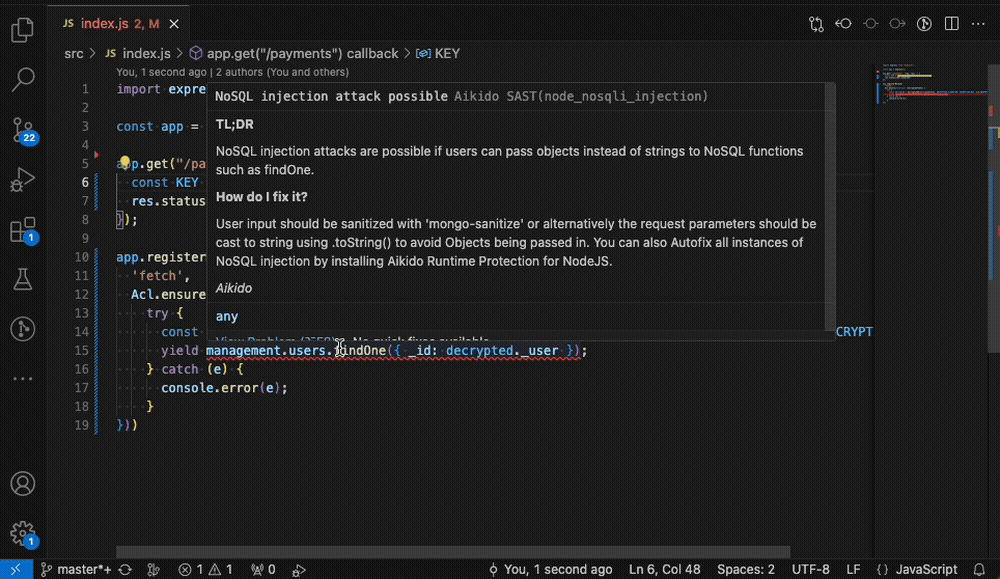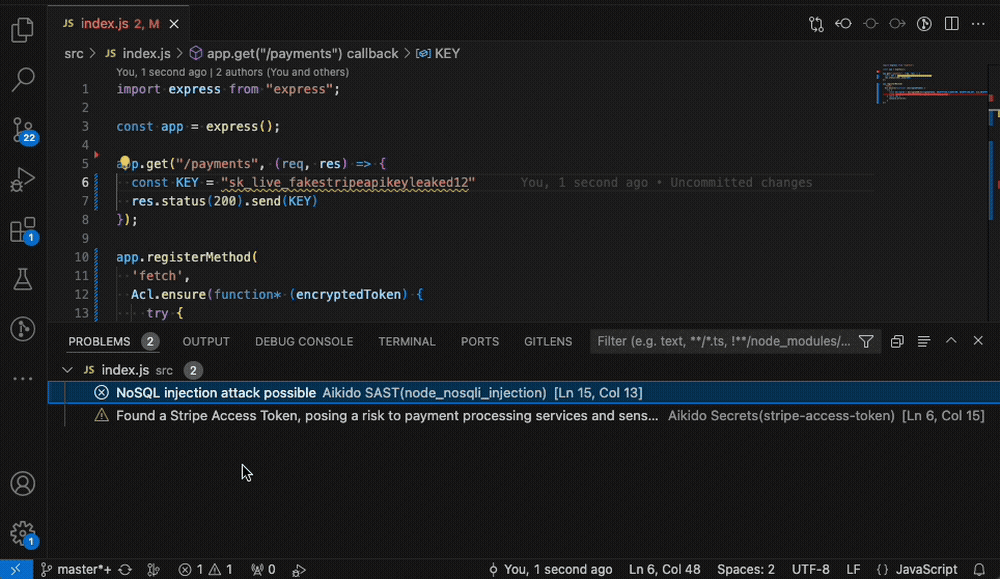
IDE Plugins
Security can also be shifted earlier, into the coding stage. With IDE plugins, students see issues flagged directly in their editor before committing code. An assignment could be to trigger a finding in VS Code, fix it, and confirm resolution in Aikido.
Screenshot: IDE plugin highlighting an issue in VS Code
What a First Month Can Look Like
- In the first week, connect repos and run the initial scan to introduce categories of findings.
- In the second week, explore dependencies and noise reduction.
- In the third week, teach prioritization with reachability.
- In the fourth week, assign remediation exercises using AutoFix comparisons.
- In the fifth week, review progress with reports to highlight long-term risk patterns.
Next Steps for Professors
Connect a demo repository, invite students, and run your first scan. Use core lessons like noise reduction, reachability, runtime protection, and AutoFix, and layer in advanced modules such as PR gating or IDE plugins for capstones.
With Aikido, students gain real-world, job-ready security skills, at no cost and without added complexity.



