Over night, starting at 01:16 UTC on September 9th, we were alerted to more packages being compromised, these included:
- duckdb (148.000 weekly downloads)
- @duckdb/node-api (87.000 weekly downloads)
- @duckdb/node-bindings (87.000 weekly downloads)
- @duckdb/duckdb-wasm (64.000 weekly downloads)
These packages all had a new version 1.3.3 released (In the case of the wasm version, it was version 1.29.2), which contained the same malicious code as we saw in the compromise of packages with 2 billion+ downloads.
Malicious payload
The payload observed in this attack is virtually identical to the one previously documented, trying to drain crypto wallets. It's an interesting choice to deploy this payload inside a package like duckdb, given that this will primarily run on a backend. It suggests that the attackers may not be very aware of what they are actually doing.
Vendor response
At the time of writing, the only indication that something has occured is the fact that the vendor has marked the latest release as deprecated:
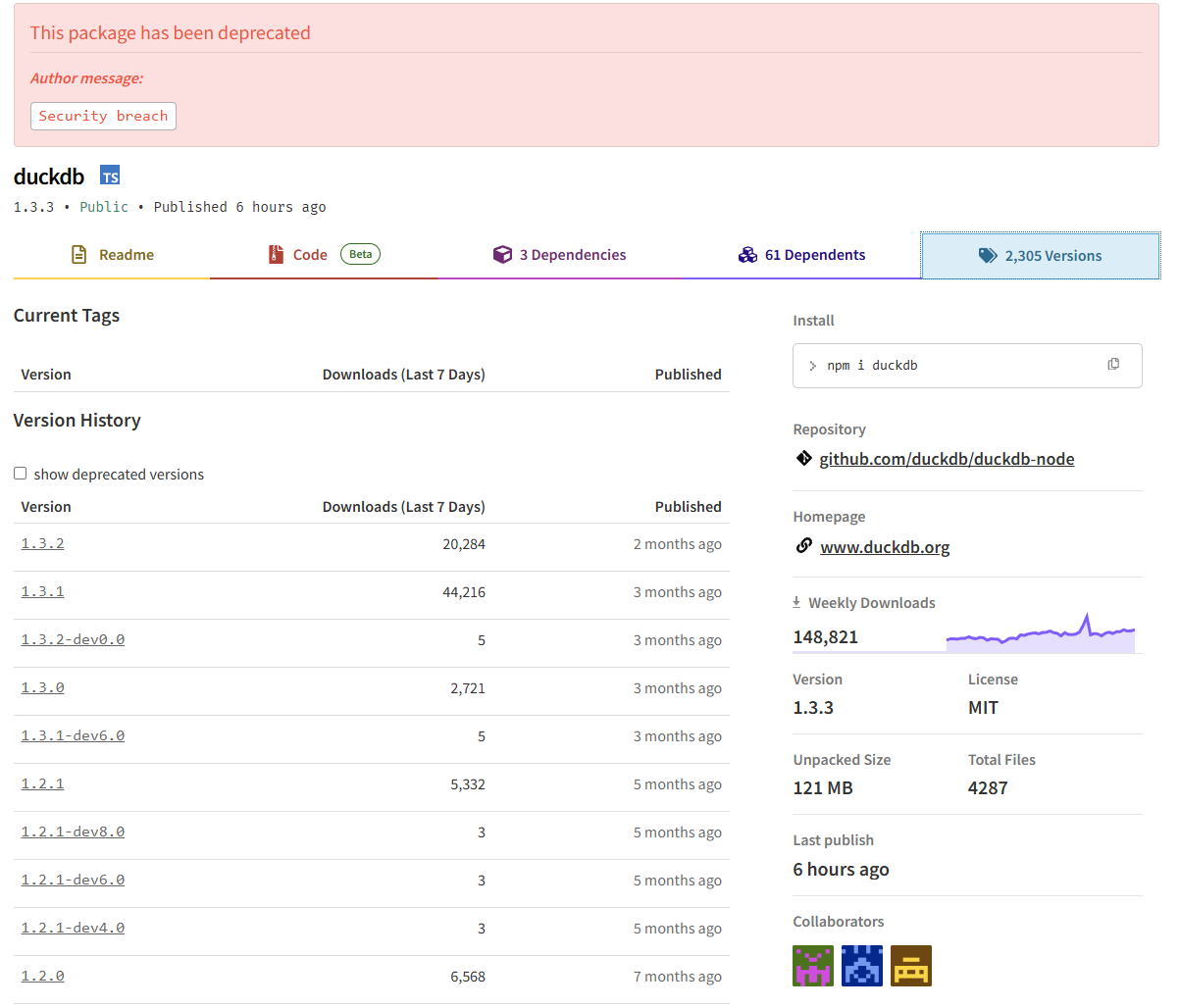
The vendor also released an advisory on GitHub about the incident:

How to phish a duck?
Based on the registry data from npm, the malicious package was submitted by the user duckdb_admin, which has the email quack [at] duckdb.org . Given that the other compromises were achieved through phishing, it appears that this time the duck itself got phished, hook, line, and sinker. The hunter became the hunted, and the poor duck waddled straight into the net (It’s been a long night).

Secure your software now





.avif)
