Introduction
In modern application security, leaders must address both code vulnerabilities and open-source risks. Checkmarx and Black Duck are popular tools that tackle these areas: Checkmarx is known for static application security testing (SAST) on source code, while Black Duck focuses on open-source dependency and container security through software composition analysis (SCA). Comparing them highlights coverage gaps and helps inform a more holistic security strategy.
TL;DR
Bottom line: Checkmarx and Black Duck each excel at their layer (custom code vs. open source) but leave blind spots. Aikido Security combines both SAST and SCA strengths in one platform – covering code, open-source components, and containers – with far fewer false positives and smoother integrations. The result is broader protection with less noise and complexity. For software security leaders, Aikido offers a more complete and efficient alternative.
Overview of Each Tool
- Checkmarx: A leading SAST tool designed to scan proprietary source code for security flaws. It supports a wide range of programming languages and uses static analysis to catch issues (like SQL injection or XSS) before code runs. Checkmarx emphasizes a developer-first approach, integrating into development pipelines and IDEs to provide early feedback on vulnerabilities.
- Black Duck: A top SCA solution focused on open-source and container security. It identifies all open-source libraries, frameworks, and OS components in your applications (or container images) and flags known vulnerabilities or license risks. Black Duck excels at generating a comprehensive software Bill of Materials and enforcing open-source policies, though it does not analyze your custom code for new weaknesses.
Feature-by-Feature Comparison
Security Scanning Capabilities
- Checkmarx (SAST): Performs deep static analysis of proprietary code to find vulnerabilities in the application’s source. It can detect code issues like injection flaws, insecure configurations, and hardcoded secrets without running the program. Checkmarx’s engine covers dozens of languages and performs data flow and taint analysis to trace exploitable paths in code. However, by itself Checkmarx focuses on custom code and does not inherently scan open-source libraries for known CVEs (its legacy model required pairing with a separate SCA tool). This means if you rely on Checkmarx alone, third-party dependency risks could go unnoticed.
- Black Duck (SCA): Performs comprehensive open-source scanning rather than code analysis. It inventories all third-party components (e.g. libraries, frameworks, OS packages) in your codebase or container, then cross-references them against a vast vulnerability database and license index. Black Duck can generate an SBOM and pinpoint known vulnerabilities (CVEs) in dependencies, and even scans container image layers for outdated or risky packages. Its forte is open-source risk management – including license compliance (e.g. flagging GPL or unacceptable licenses) and vulnerability alerts. The trade-off is that Black Duck does not examine your proprietary source code’s logic; it won’t find a security bug in your custom algorithm or configuration unless it ties back to a known vulnerable component. In practice, many organizations use both: Checkmarx to catch coding flaws and Black Duck to cover open-source exposures. (Notably, Aikido combines both approaches, doing static code analysis and dependency/container checks in one unified scan.)
Integration & CI/CD Compatibility
- Checkmarx: Offers robust integration across the development lifecycle. It provides plugins for major IDEs (VS Code, IntelliJ, Visual Studio, etc.) so developers can scan code and see findings in their editor. In CI/CD, Checkmarx integrates with platforms like GitHub, GitLab, Azure DevOps, and Jenkins – you can configure scans on each pull request or build, with the ability to break the build if severe issues are found. This shift-left approach catches issues early. Checkmarx can run on-premises or as a cloud service (the Checkmarx One SaaS platform), giving flexibility in deployment. The unified dashboard in Checkmarx One aggregates SAST (and if licensed, SCA) results in one place. Overall, integration is a strong point: security checks can be automated in pipelines and woven into developer workflows with relatively deep tooling support.
- Black Duck: Integrates primarily at the CI/CD and repository level for scanning artifacts and builds. Developers usually don’t run Black Duck scans inside their IDE; instead, teams use the Synopsys Detect CLI or plugins to trigger scans during build or release pipelines. For example, a Jenkins pipeline might invoke Black Duck to scan a built application or container image, and then fail the build if any high-severity vulnerability or policy violation is detected. Black Duck outputs results to a centralized portal (Black Duck Hub) where security or compliance teams review and triage findings. It supports integration with issue trackers (like Jira) to create tickets for developers, and can even open pull requests to update vulnerable libraries. Deployment: Black Duck is often run on-premises as a server (or cluster) that stores your project BOMs and vulnerability data. A managed SaaS option exists, but many enterprises host it themselves for compliance reasons. This means integration involves setting up that infrastructure and connecting your CI pipelines to it. In summary, Black Duck fits into DevOps by adding a post-build audit step – it’s effective for governance, but not as tightly woven into the real-time coding process as Checkmarx’s IDE integrations.
Accuracy and Performance
- Checkmarx: The tool performs thorough static analysis, which can be computationally heavy. Scanning a large codebase may take minutes to hours, especially on initial runs. Checkmarx mitigates this with incremental scanning (only analyzing new or changed code on subsequent runs) to improve speed on ongoing integration scans. In terms of accuracy, Checkmarx is known to flag a high volume of potential issues out-of-the-box – some critical, others informational. This thoroughness means it often uncovers vulnerabilities, but it also results in false positives (benign code flagged as risky) or low-priority warnings that can overwhelm developers. In fact, legacy Checkmarx users sometimes joke that it can be a “false positive generator,” noting cases where only ~1% of reported issues turn out to be real problems. With tuning – e.g. customizing rules or marking certain patterns as not exploitable – teams can greatly improve the signal-to-noise ratio. Checkmarx’s rule engine allows fine-grained adjustments, and its newer versions use more contextual analysis to reduce noise. Still, the initial learning curve in separating wheat from chaff is non-trivial. Performance-wise, for a mid-sized codebase integrated in CI, Checkmarx can usually complete a scan in a reasonable time (a few minutes), but very large monolithic projects might need careful configuration (or segmentation) to avoid slowing the pipeline. Accuracy against true positives is considered strong – it finds a wide range of issues – but expect to invest effort in triaging results to filter out the trivial or false alarms.
- Black Duck: Accuracy for Black Duck means identifying known vulnerable components correctly. In that regard, it leverages an extensive vulnerability knowledge base and typically has few false positives – if Black Duck says a library version has CVEs, it’s usually a factual statement. The challenge is more about relevance: not every vulnerability in a dependency is exploitable or high-impact for your application. By default, Black Duck will list all known issues, which can be a long list for a large app with many dependencies. Unlike some newer SCA tools, it doesn’t deeply analyze whether your code actually calls the vulnerable function (except in limited cases like a Java “exploitable path” analysis). Thus, you might see alerts for a library vulnerability that exists in a part of the code you never use in production – technically a true positive, but not a true risk. This can create noise, requiring security teams to manually prioritize which vulns are critical. Black Duck does offer policy features to auto-ignore or waive certain findings (e.g. ignore dev/test dependencies or vulnerabilities below a certain severity).
Performance: Scanning with Black Duck involves either analyzing dependency manifests or conducting a full binary scan (for containers or compiled apps). This process, especially the first full scan of a project, can be time-consuming. Users have noted that Black Duck is “not the leanest tool for quick scans” – a comprehensive scan of a large codebase’s open-source components might take many minutes, as it constructs the BOM and checks each component. Scanning container images (layer by layer) is similarly intensive. In CI/CD, this can slow down build pipelines if not configured to run in parallel or asynchronously. There have been improvements over the years, but some users still desire faster scanning and a more responsive UI while results load. In summary, Black Duck’s vulnerability data is trustworthy, but the sheer volume of findings and the scan duration mean you need a process in place to handle the output efficiently. It’s thorough and enterprise-grade, but not lightweight.
Coverage and Scope
- Checkmarx: One of Checkmarx’s strengths is its breadth of language support. It can scan code written in dozens of languages and frameworks – from Java, C#, and JavaScript/TypeScript, to Python, C/C++, PHP, Ruby, Go, and more. This makes it suitable for organizations with polyglot stacks (you don’t need a separate SAST tool for each language). Checkmarx covers web apps, microservices, mobile app code (e.g. Swift for iOS, Kotlin for Android, if source is available), and even checks Infrastructure-as-Code templates for security misconfigurations. Its newer platform modules extend into API security testing and IaC scanning, aiming to give more holistic coverage of code risks beyond just application source code. However, Checkmarx’s scope is essentially code you write. It finds vulnerabilities in proprietary application logic and configuration. For third-party components, Checkmarx introduced its own SCA capabilities (as part of Checkmarx One), but traditionally this wasn’t its core focus. Organizations relying on Checkmarx alone for open-source risk might find its SCA database less mature compared to Black Duck’s, or they might have had to integrate another tool. In terms of SDLC coverage, Checkmarx is used predominantly in development and testing phases – it’s a “shift-left” tool to catch issues pre-production. It doesn’t, for instance, monitor running applications in production (that’s the domain of runtime tools), and it doesn’t natively scan compiled binaries or container images for OS package issues. So its coverage is broad across source code and early-phase artifacts, but not across binary or runtime artifacts.
- Black Duck: The scope of Black Duck is agnostic to programming language – it cares about what open-source or third-party components are present, whether they come from a Maven pom.xml, an NPM package.json, a Python requirements.txt, a container base image, or even a checked-in binary JAR. It will enumerate components and find their known vulnerabilities regardless of how they’re brought in. This means Black Duck can cover virtually any environment: enterprise apps in Java/.NET, front-end projects in JavaScript, C/C++ projects using open-source libs, mobile apps (it will scan the Gradle/Maven dependencies or CocoaPods, for example), and container images (scanning Linux packages and libraries inside). Additionally, Black Duck is well-known for license compliance coverage. It not only flags security issues but also tracks open-source license obligations (e.g. if you’re using a library under GPL or AGPL, Black Duck will alert you so legal teams can review). This goes beyond what Checkmarx or many pure security tools do. Black Duck’s knowledge base includes legal risk information, which is important for organizations that need to avoid certain licenses or publish accurate attributions. In terms of SDLC, Black Duck is often used during the build/release phase or in continuous monitoring of released software (e.g. to alert if a new CVE affects an already deployed component). It’s not limited to just development: many use it to periodically rescan production software bills of materials for newly disclosed vulnerabilities. What it doesn’t cover: any vulnerabilities in the custom code that are not in a vulnerability database. Also, it doesn’t inherently cover configuration issues (unless a misconfiguration introduces a known vulnerable component). For example, Black Duck won’t warn you about an insecure use of crypto in your code – that’s something SAST (Checkmarx) would catch. It also doesn’t do dynamic testing. So, its coverage is wide in open-source, but narrow in focus (no runtime or custom code analysis). In practice, Black Duck is part of a larger toolchain: for full coverage, teams pair it with SAST, DAST, etc., or choose an all-in-one like Aikido that spans these areas.
Developer Experience
- Checkmarx: Integrates directly into developers’ workflows with IDE plugins and pull request checks, but the abundance of findings can overwhelm teams with false positives . Developer training and rule tuning are necessary to make it effective.
- Black Duck: Primarily used by security teams, Black Duck doesn’t offer the same hands-on experience for developers. It provides high-level reports and remediation suggestions, but developers may not interact directly with the tool regularly .
Pricing and Maintenance
- Checkmarx: Offers enterprise-level pricing, which can be costly for smaller teams. Maintenance involves tuning scans, managing infrastructure, and updating rules.
- Black Duck: Also a premium solution with complex pricing, often bundled with other Synopsys tools. It requires maintenance of an on-premises server or a managed SaaS, and the cost can be prohibitive for smaller organizations .
Pros and Cons of Each Tool

Checkmarx – Pros and Cons
- Checkmarx – Strengths: Very broad language and framework support for static analysis, capable of finding complex code vulnerabilities; rich integration with developer tools and CI/CD (IDE plugins, PR checks) facilitating shift-left security; offers customizable rules and detailed compliance reports (OWASP Top 10, PCI, etc.) suitable for enterprise governance.
- Checkmarx – Drawbacks: Tends to report a high volume of issues out-of-the-box, including many false positives that require tuning; initial setup and rule customization involve a steep learning curve for teams; scan durations and infrastructure requirements can be heavy on large projects; and the licensing is expensive and geared toward large enterprises (no easy pay-as-you-go option).

Black Duck – Pros and Cons
- Black Duck – Strengths: Best-in-class open source and container vulnerability tracking, with an extensive knowledge base of known risks and licenses; able to produce complete SBOMs and enforce open-source policies (e.g. license compliance, version bans) across all your applications; integrates into build pipelines to catch issues before release, and can automatically suggest or orchestrate dependency upgrades, saving manual effort.
- Black Duck - Drawbacks: Does not analyze proprietary source code, so it leaves custom code security gaps unless combined with SAST; can overwhelm teams with lengthy vulnerability lists that need prioritization (no contextual exploitability filtering by default); the solution is resource-intensive – from the on-prem server to the slow scan times on big images – and not very agile for fast-moving dev cycles; documentation and UI, while comprehensive, have a reputation for being clunky or confusing for newcomers; and like Checkmarx, it comes with a high price tag, which some reviewers consider too steep relative to the value.
Aikido Security: The Better Alternative
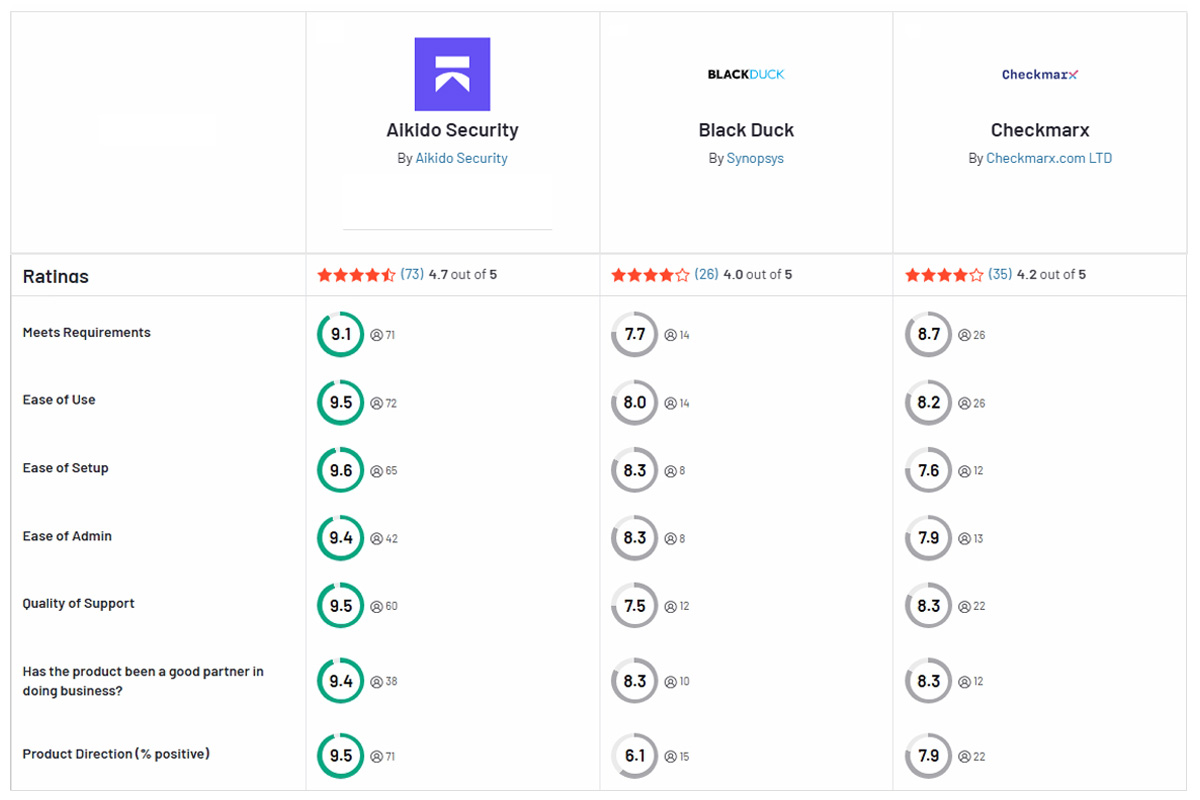
Aikido Security offers a modern approach that addresses many of Checkmarx’s and Black Duck’s shortcomings. It provides broader coverage by unifying static code analysis and open-source/container scanning in a single platform – no gaps between SAST and SCA. Thanks to intelligent filtering, Aikido yields fewer false positives (its “no noise” philosophy surfaces only actionable issues). The solution delivers a smoother developer experience, with fast scans, in-IDE results, and even AI-assisted fixes, all designed to fit DevOps workflows. Importantly for leadership, Aikido uses a simpler pricing model (all-in-one, no multi-tool contracts), making it easier to adopt and scale. In short, Aikido combines the strengths of Checkmarx and Black Duck – comprehensive code and dependency security – while avoiding their pain points, emerging as a more effective alternative for software security programs.
Start a free Trial or request a demo to explore the full solution.



